
Read insights, thought leadership, and platform updates.
No Blogs Match Your Results
Please try again or contact marketing@threatconnect.com for more information on our blogs.
Introducing ThreatConnect’s Version 5.8
Showcasing the Platform’s increased user flexibility for creating Playbooks and expanded options for in-Platform application (App) building It’s here! Version 5.8 is here: ThreatConnect’s newest Platform features and functionality that we (humbly) think will heighten your experience. With these “ ease-of-use” updates, we’re continuing to enhance your experience when it comes to the development, design, […]

Leveraging Channels – Reference Channels versus Collaborative Channels
The past few posts have discussed how Polarity’s 3rd party integration framework operates, so today we wanted to talk more about how you can take better advantage of Polarity’s Collective Memory by utilizing our Channel Framework. What is a Polarity Channel? Channels in Polarity provide a way to organize Entities and Annotations into logical groups. […]
Playbook Fridays: Indicator Defanging
To avoid indicators of compromise becoming links to malicious content, “defang” them. If you’ve worked in the computer security industry for a while, you have probably seen a website, email, Slack message, or spreadsheet with a malicious URL, email address, or domain name that has become a link. One of the ways to avoid indicators […]
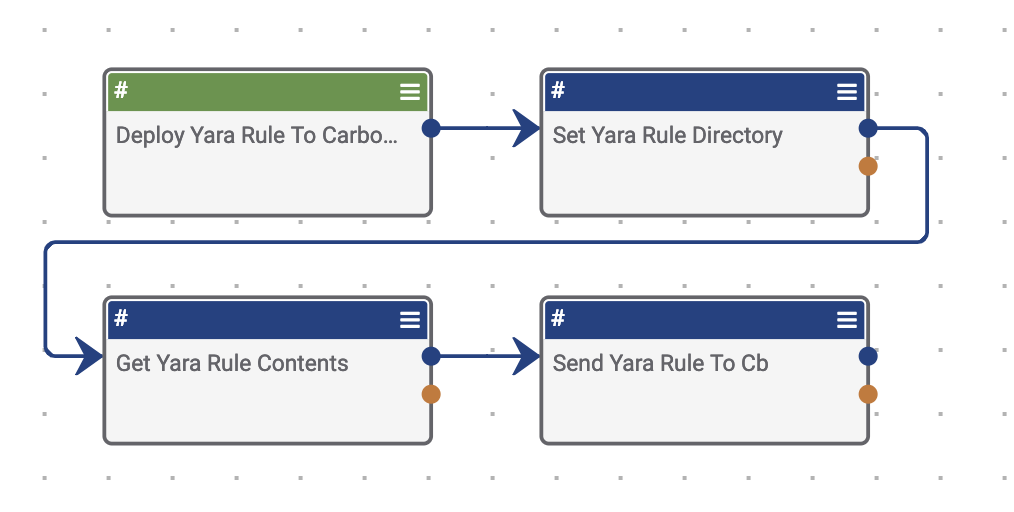
Playbook Fridays: Deploying Yara Signature to Carbon Black CB Response
Rapidly deploy Yara rules that are associated to intel products within ThreatConnect out to CarbonBlack’s CB Response via their Yara Connector This Playbook allows analysts that are performing an investigation or doing proactive threat hunting to quickly deploy signatures to Carbon Black’s CB Response. Normally this process is very manual as it requires the user […]
What Can CAL™ (Collective Analytics Layer) Do For You?
CAL™ has billions of data points that it can bring to bear to power its analytics—and we’re adding more every day It’s been two years since we announced CAL™ , our Collective Analytics Layer. Since then, we’ve made fantastic strides in leveraging some of the latest big data technology to make our users’ lives easier. […]
Playbook Fridays: New ThreatConnect App for Splunk 3.1
Splunk Users Can Now Launch Playbooks Directly from Splunk With ThreatConnect App Updates Earlier this week, the latest ThreatConnect App for Splunk (v3.1) was released to Splunkbase. This release for Splunk is all about taking action and enabling our customers to fully leverage the power of the ThreatConnect Platform while working directly inside Splunk or […]
Lights, Camera, Actionable Intelligence!
ThreatConnect Research builds out a network of domains and subdomains spoofing organizations related to the entertainment industry, most likely used in credential harvesting efforts. To be frank, if we were going to give out an award for this acting, we don’t know who it would go to. Following a partner tip identifying IP addresses hosting […]
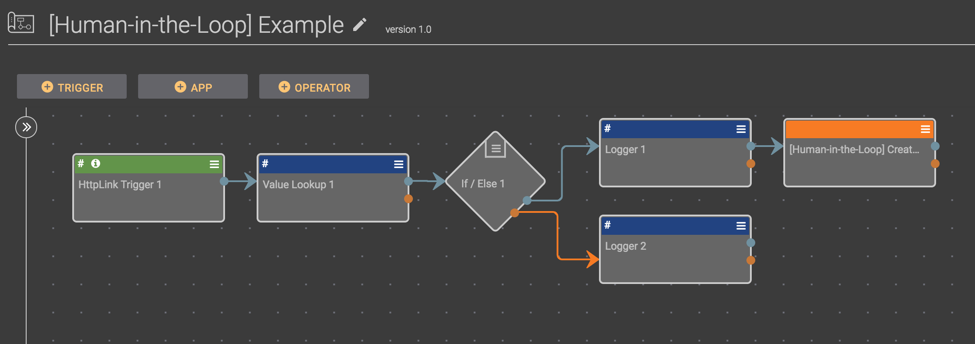
Playbook Fridays: Human in the Loop Playbook Systems
When automating processes, you may run into situations where you need a human to be part of an automated process The whole goal of Playbooks is to make it easy to automate tasks so you can be faster, more effective, and more secure. When automating processes, you may run into situations where you need a […]
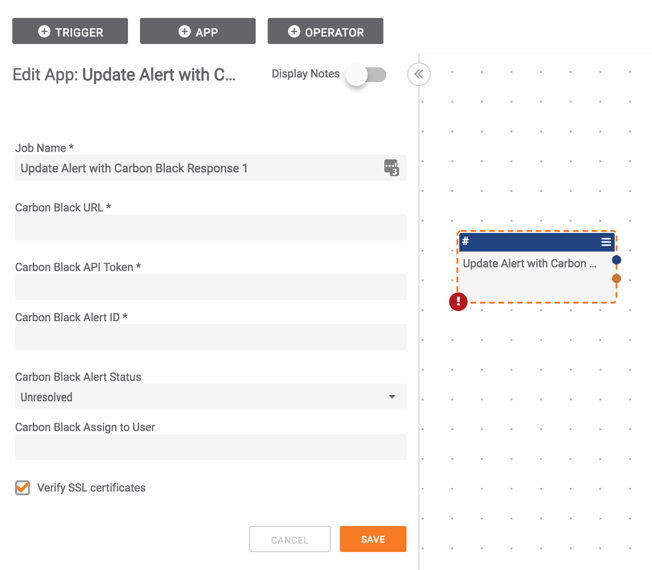
ThreatConnect Releases 20 New Carbon Black Playbook Apps for CB Response
Together, ThreatConnect and Carbon Black provide a complete solution for security teams We’re excited to announce the release of a large bundle of ThreatConnect Playbook Apps with Carbon Black Response (CB Response). This set of Apps greatly increases the ability to take investigative and response actions across enterprise endpoints from the ThreatConnect Platform. Integrating ThreatConnect […]

New Integration Framework Updates Increase Interactivity
We want to showcase some recent integration framework updates that allow users to take actions directly from within the Overlay Window. To do this, we’ll focus on user driven queries, and integration actions. User Driven Queries Polarity integrations now have the ability to retrieve additional data based on user actions. User driven queries improve performance, […]
5 Things to Do at RSA 2019
Headed to RSA? Here are some ideas of things to do! RSA Conference 2019 is just around the corner! Make the most of your time in San Francisco by filling your time with some classic San Francisco activities, and of course, making time for some show-related activities. 5. Ghirardelli Square Stop by for something sweet […]
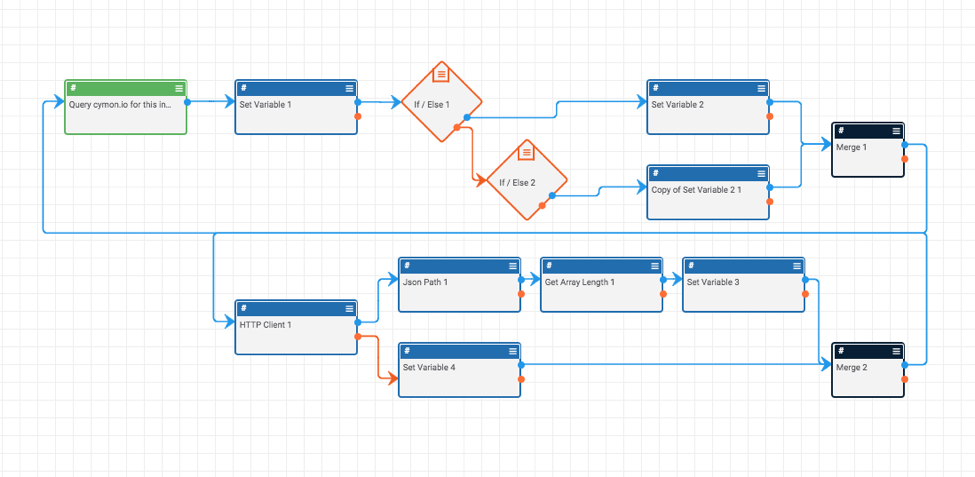
Playbook Fridays: Query Cymon.io API
This Playbook queries Cymon.io API, which tracks malware, phishing, botnets, spam, and more ThreatConnect developed the Playbooks capability to help analysts automate time consuming and repetitive tasks so they can focus on what is most important. And in many cases, to ensure the analysis process can occur consistently and in real time, without human intervention. […]
