Posted
This Playbook queries Cymon.io API, which tracks malware, phishing, botnets, spam, and more
ThreatConnect developed the Playbooks capability to help analysts automate time consuming and repetitive tasks so they can focus on what is most important. And in many cases, to ensure the analysis process can occur consistently and in real time, without human intervention.
Happy Friday! This Friday, we are featuring a Playbook which queries Cymon’s API. Cymon, run by eSentire, is an open service which tracks “malware, phishing, botnets, spam, and more” (from https://cymon.io/).
The Playbook is pretty simple:
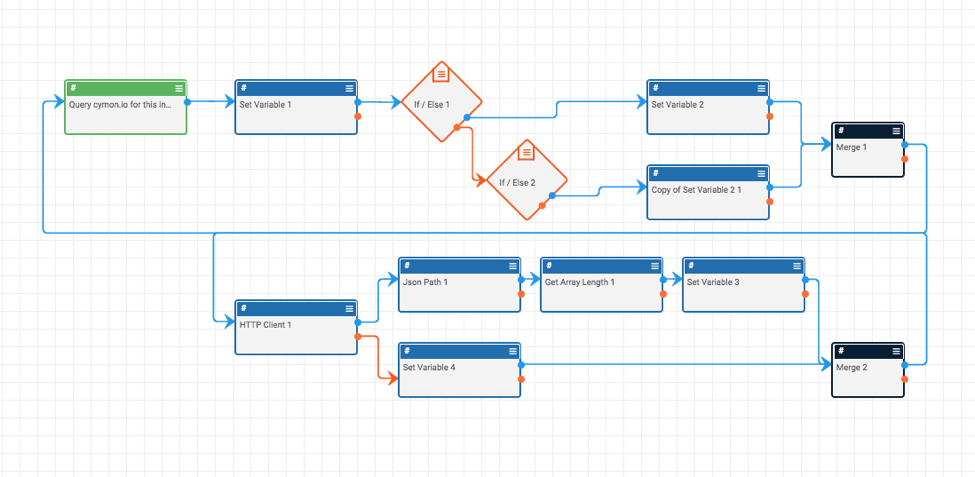
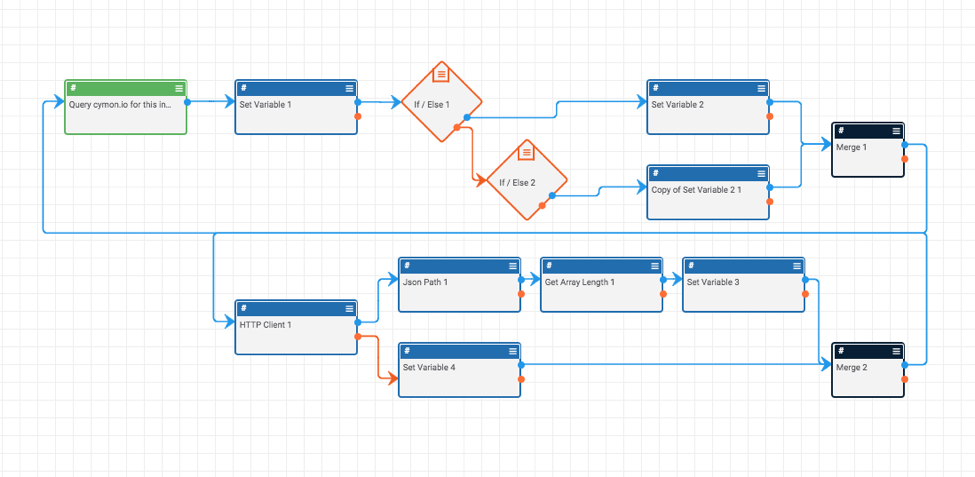
The Playbook starts with a user-action trigger (which means you can trigger this Playbook from an indicator’s page).
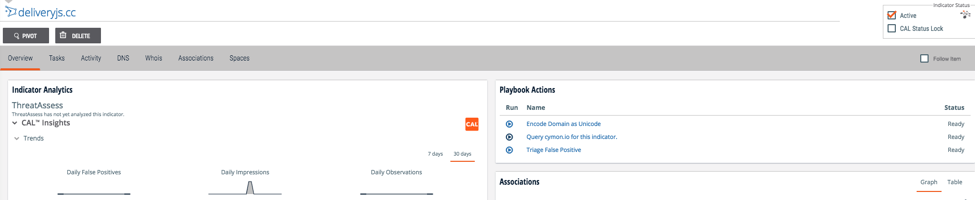
The Playbook then determines whether the given data is an IP Address indicator or a host indicator, queries Cymon’s API, and returns the response to the indicator’s page so you can see the results with one click and without leaving the page! This Playbook does require a Cymon API Token which is stored as a keychain variable. You can register for a Cymon API Token here.
You can download the playbook from our Playbooks repository: https://github.com/ThreatConnect-Inc/threatconnect-playbooks/tree/master/playbooks/TCPB-UA-Cymon%20Query%20IP%20and%20Host. If you have any questions, feedback, or run into any problems, feel free to raise an issue.
Happy hunting!