
Read insights, thought leadership, and platform updates.
No Blogs Match Your Results
Please try again or contact marketing@threatconnect.com for more information on our blogs.
How to Use Workflow to Conduct Phishing Analysis Part 2 – Automating Phase 1
While most organizations (88% in 2019 according to ProofPoint’s State of the Phish 2020 report) are targeted by spear phishing emails each year, the processes by which these messages are triaged and analyzed varies from company to company. In some cases, phishing analysis is the responsibility of the security operations center or incident response team. […]
Why Your SOAR Needs Threat Intel Management, Not Feed Management
When it comes to using threat intelligence to aid in the investigation of alerts or phishing, it’s essential to have the right feeds (whether OSINT or paid). We often get asked, “can I just dump feeds right into my SOAR platform?” This is an evolution of a question that’s been going on for some time: […]
Tracking Sunburst-Related Activity with ThreatConnect Dashboards
Recently FireEye discovered that the SolarWinds Orion IT monitoring platform was compromised earlier this year. The threat actor used SolarWinds cryptographic keys to sign multiple backdoored files posing as Orion IT updates. These files contained a hidden backdoor that would communicate via HTTP to external servers after remaining dormant for up to 2 weeks. The […]
Tactical Threat Hunting (Part 1): Providing the information that matters, when it matters.
This is part 1 of a 2 part series. In a previous article, “SOAR: An Incident Responder’s Best Friend,” we discussed the issues facing Incident Responders today and how Security Orchestration, Automation, and Response (SOAR) can help to reduce alert fatigue while providing faster, more timely responses. In this article we are going to expand […]
Infrastructure Research and Hunting: Boiling the Domain Ocean
The Diamond Model of Intrusion Analysis identifies two main nodes as actor assets that may ultimately interact with a target / victim’s own assets — capabilities and infrastructure. But while “exploitation” is usually considered something the adversary does, it works both ways as threat intelligence researchers and defenders in general can exploit the discoverable characteristics […]
ThreatConnect and Cisco Identity Services Engine (ISE): Streamline Security Policy Updates
ThreatConnect and Cisco have partnered to deliver a Playbook app for joint customers to leverage. With this Playbook app, you can control the network status of an endpoint in Cisco ISE. The Cisco Identity Services Engine (ISE) is your one-stop solution to streamline security policy management and reduce operating costs. With ISE, you can see […]
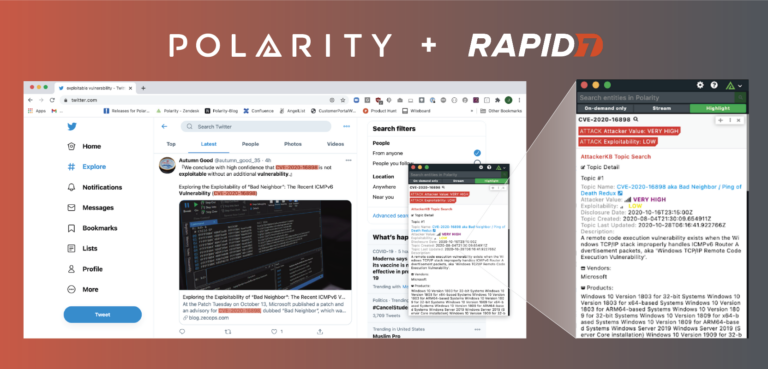
Always Know a Vulnerability’s Weak Point with the Polarity Rapid7 AttackerKB Integration
Today’s post continues an ongoing series on Polarity Integrations. Data tells a story, Polarity helps you see it with Augmented Reality overlaying contextual information from the applications you use every day, no glasses or goggles required. With over 100 powerful integrations, Polarity’s open-source Integrations Library arms you with the right data at the right time […]
RQ 5.0 Offers New Automation and Prioritization to Better Respond to and Communicate Cyber Risk
Latest RQ 5.0 release introduces support for multiple security control frameworks and is the industry’s first product to prioritize common vulnerabilities and exposures (CVEs) by the financial risk they bring to the business. Even with all the strife experienced in 2020, companies are accelerating their digital transformation initiatives. Believe it or not, most companies are […]
ThreatConnect and Zoom: Coordinated Communications as part of Incident Response
ThreatConnect has delivered a Playbook App for Zoom users to leverage within the Platform. The app will allow you to launch a Zoom meeting, invite attendees, and save the meeting as part of an automation or orchestration. This helps your Incident Responders save time and remain coordinated with others during an investigation. With this new […]
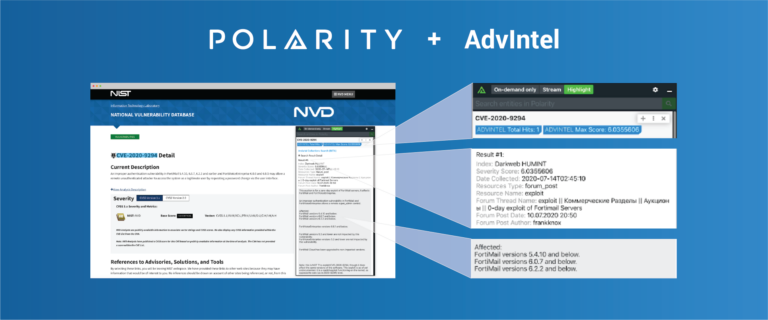
Instant Contextual Awareness of New and Emerging Threats with Polarity and AdvIntel
Today’s post continues an ongoing series on Polarity Integrations. Data tells a story, Polarity helps you see it with Augmented Reality overlaying contextual information from the applications you use every day, no glasses or goggles required. With over 100 powerful integrations, Polarity’s open-source Integrations Library arms you with the right data at the right time […]
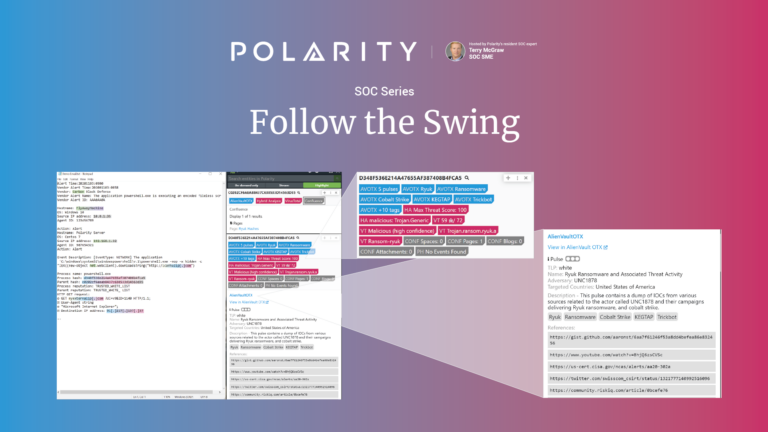
SOC Series: Follow the Swing
Today’s post continues an ongoing series on Polarity Security Operations Center (SOC) use cases; demonstrating how Polarity helps you to see the story in your data without sacrificing thoroughness or speed. Your analyst team lives a high stress and often painful life. They have to be right as close to 100% of the time as […]

SOC Series: Determining Asset Criticality During Event Triage
Today’s post continues an ongoing series on Polarity Security Operations Center (SOC) use cases; demonstrating how Polarity helps you to see the story in your data without sacrificing thoroughness or speed. Understanding asset criticality, function, and location are absolutely critical when triaging an event to determine whether or not it is an actual incident requiring […]
