Posted
Enriching Indicators with haveibeenpwned
ThreatConnect developed the Playbooks capability to help analysts automate time consuming and repetitive tasks so they can focus on what is most important. And in many cases, to ensure the analysis process can occur consistently and in real time, without human intervention.
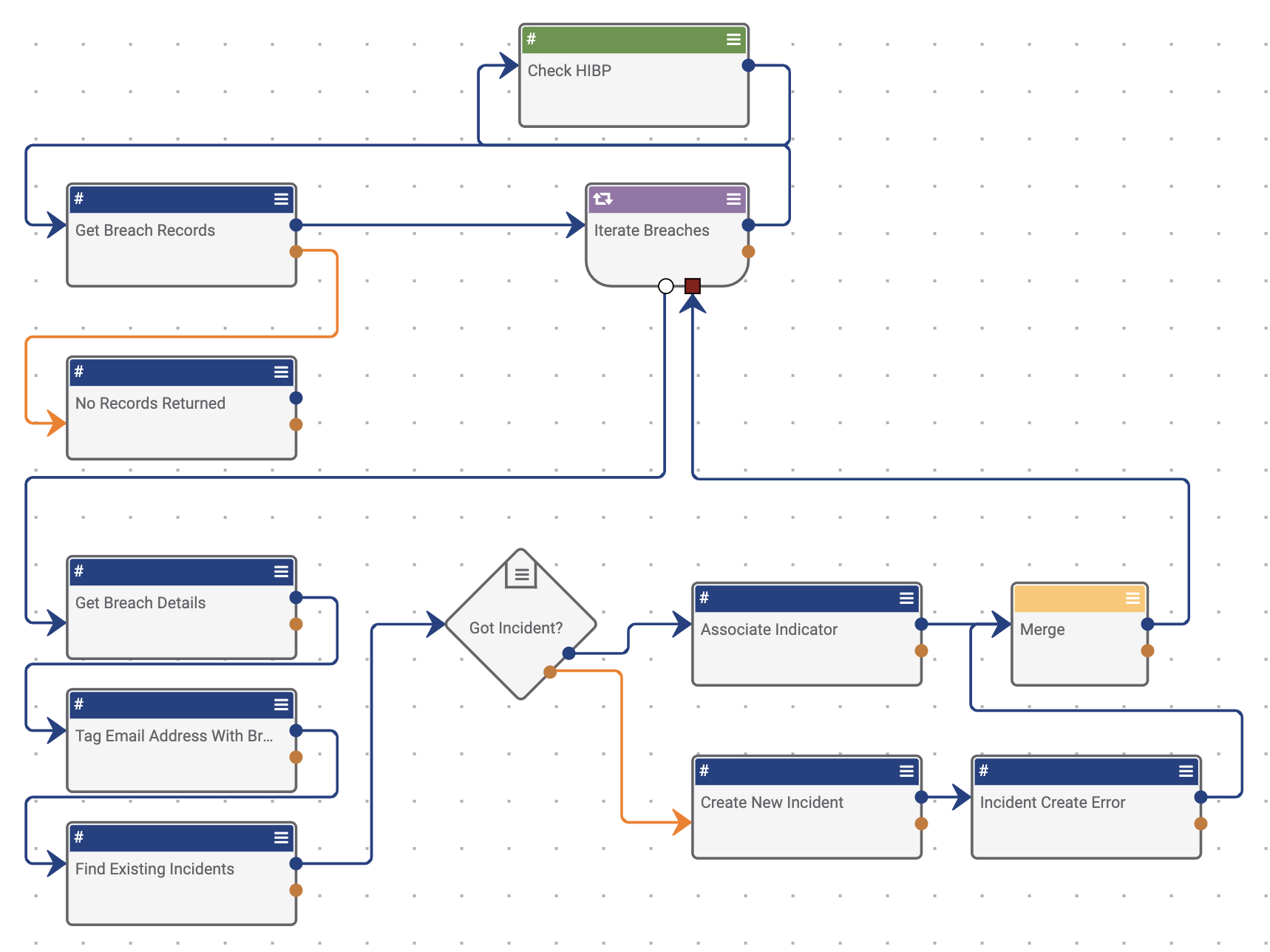
Why Was the Playbook Created?
Data breaches come and go and it is easy to forget who was breached and when. The team at Have I Been Pwned? has built a searchable database of 4.8 billion compromised accounts.
We have built a PlayBook app that allows you to query for breach information for a given email address as well as return additional context around a given breach.
How it Works:
- When looking at any EmailAddress indicator in the ThreatConnect platform simply click “Check HIBP”. That’s all that is needed.
- From here, the ThreatConnect PlayBooks engine takes over and performs the following steps:
a. Check HIBP for the email address
b. If found, perform some data transformations to extract the data needed
c. Tag the current Indicator with the name of the breach it was found in
d. Search for existing Incidents to associate the EmailAddress too, creating a new Incident if required
One step for the analyst
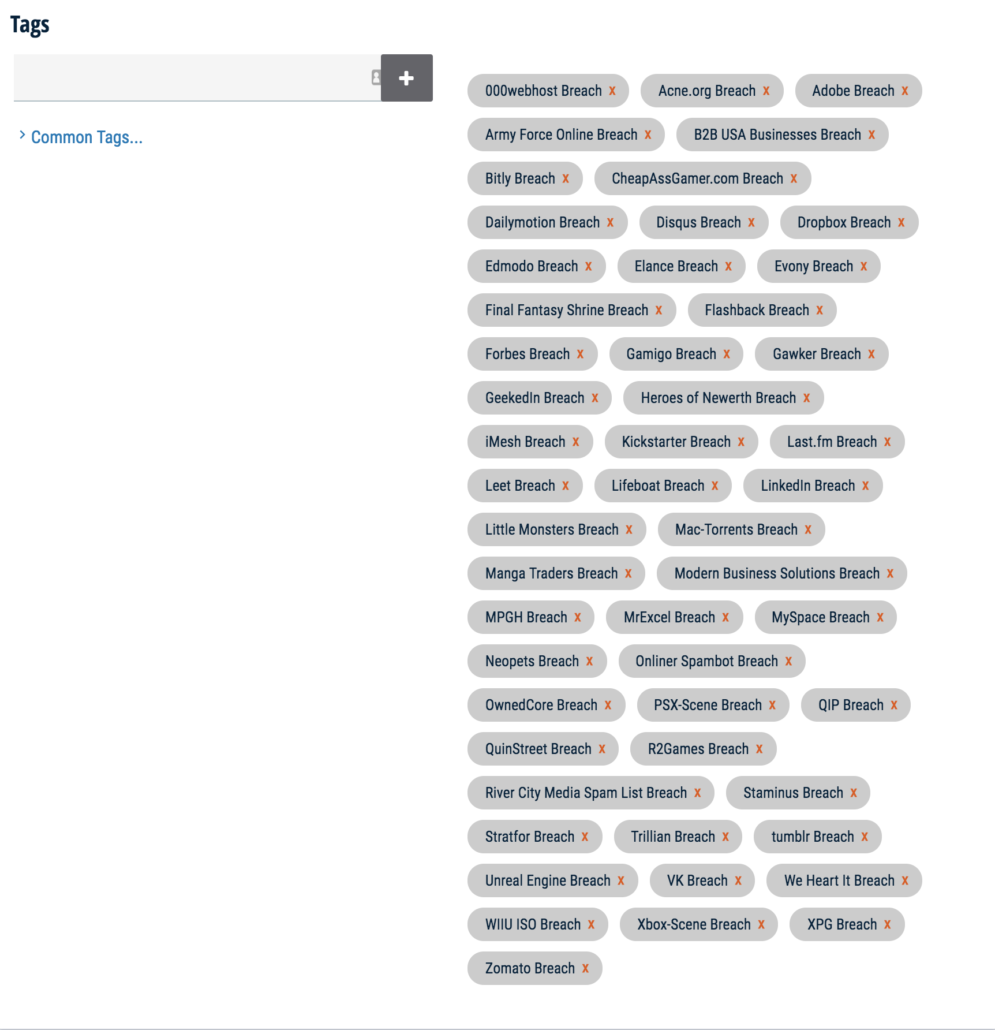
Here you can see that this unlucky user’s account was found in over 50 data breaches and we tagged the indicator with each breach.
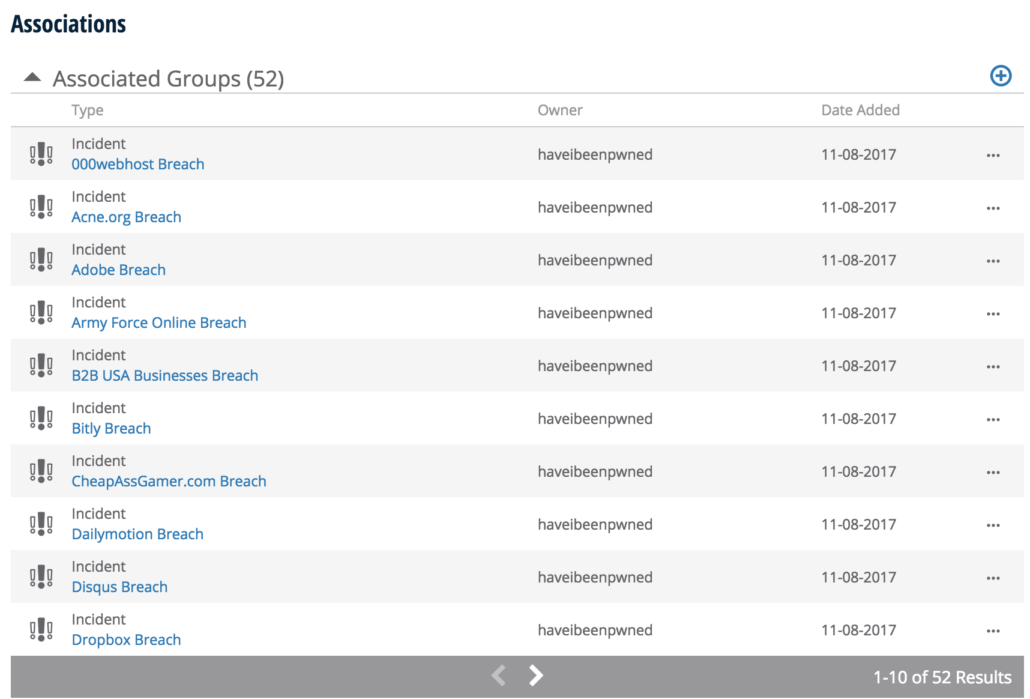
We also created and associated an incident for each data breach that contains the breach date as well as a brief description of the breach.
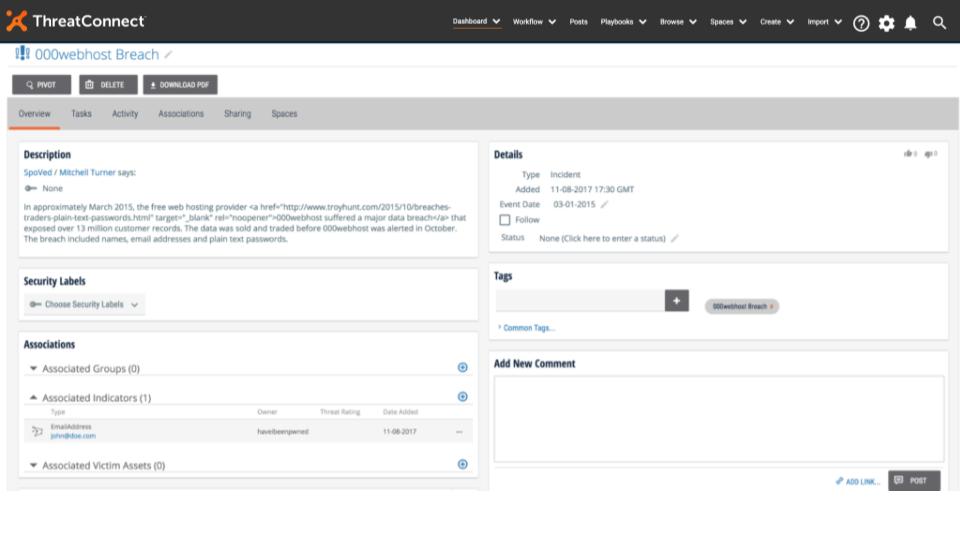
It’s important to note that we did not write a single line of code to build this playbook with HIBP, and relied entirely on utility apps provided in ThreatConnect Playbooks to “build the integration”. This showcases the power and extensibility of ThreatConnect as a true platform. If an integration doesn’t exist, you can easily create one using the built-in capabilities of ThreatConnect Playbooks.
How to Use It:
- Import the PlayBook, we have created a GitHub repository with the PlayBook file
- Click “Check HIBP”