Posted
Query abuse.net for abuse contacts registered to a domain
ThreatConnect developed the Playbooks capability to help analysts automate time consuming and repetitive tasks so they can focus on what is most important. You can also communicate with third-party services to trigger events outside of ThreatConnect.
Why Was the Playbook Created?
With the massive amount of SPAM and phishing targeting organizations today, it can be a nightmare to report abuse to the proper teams. This PlayBook can save security teams from the tedium of finding abuse contacts. The folks at abuse.net provide an easy to use service to find this info with a simple DNS query, now you can leverage this in ThreatConnect.
*We also released the Abuse.net ThreatConnect Playbook app open source to give you an example of the power behind the Platform’s orchestration tool.
What are some use cases?
- Process abuse email in an automated way
- Send abuse reports in real time as abuse hits your network
How It Works
We have included a sample PlayBook in the GitHub repo called “Abuse.net PlayBook Demo.pbx” that you can import directly into your ThreatConnect instance.
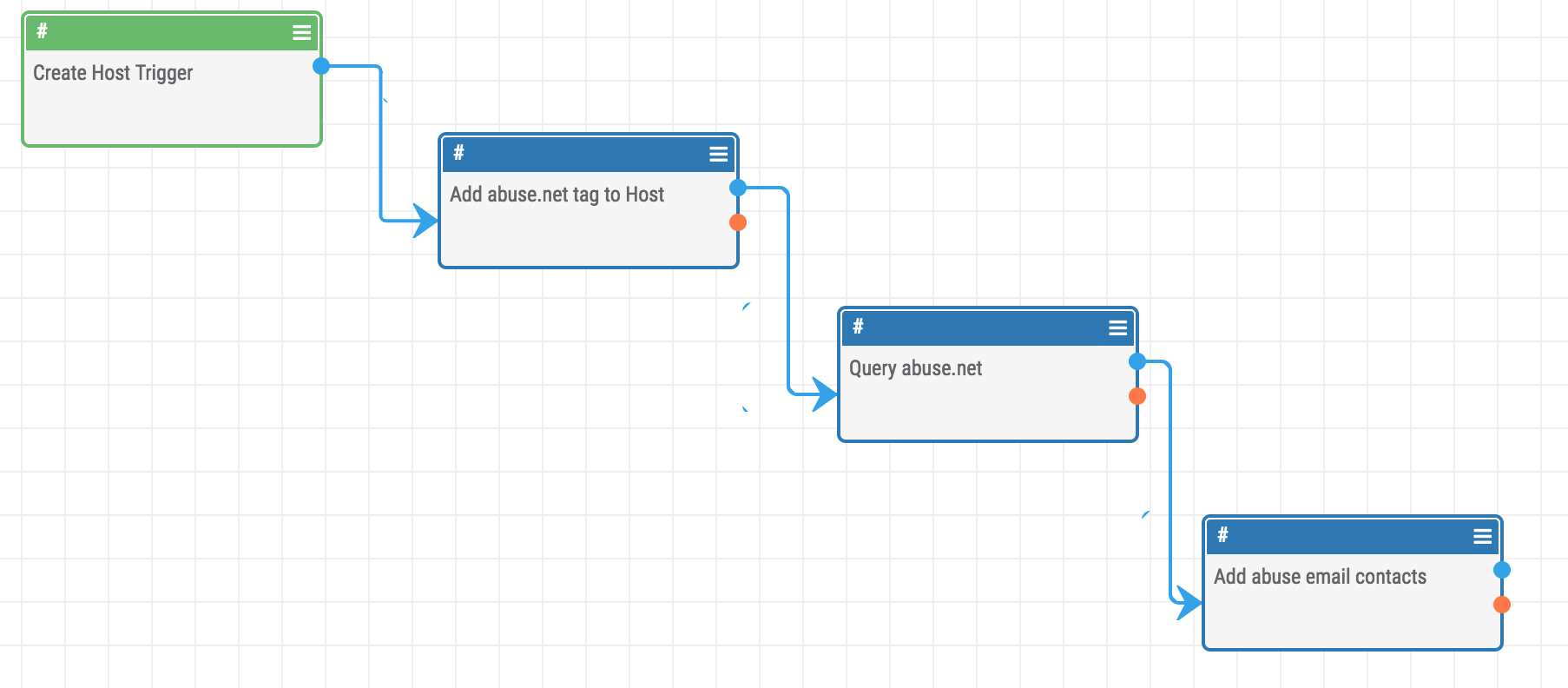
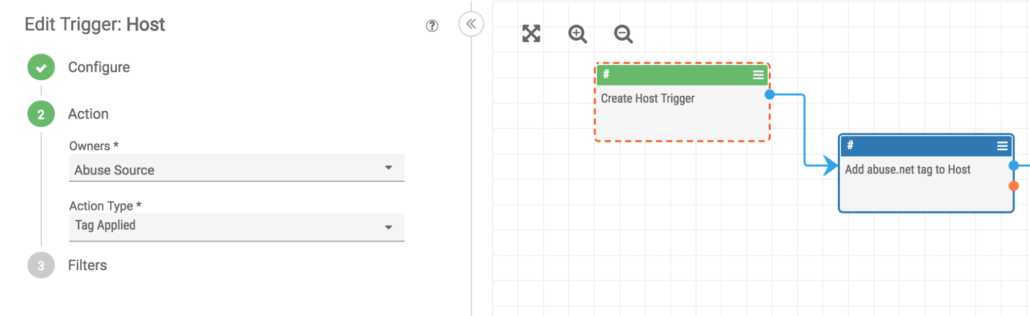
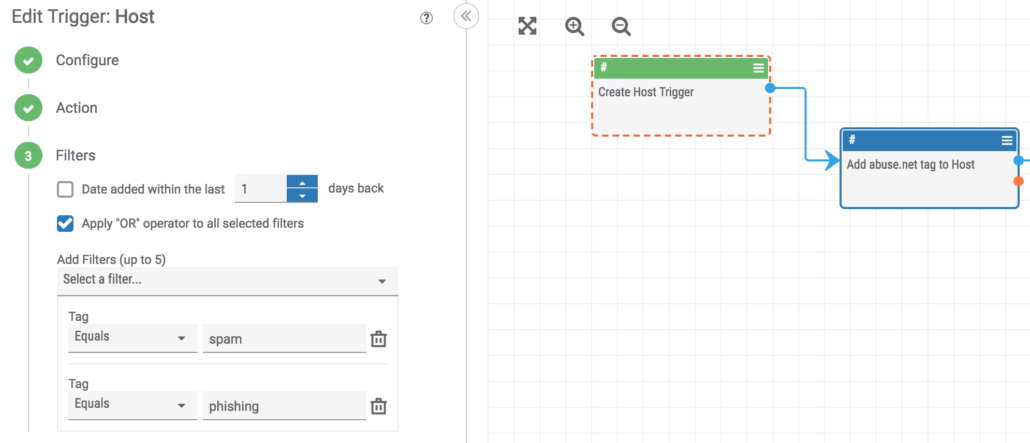
In this example we use a “Tag Applied” filter on a Host indicator to start the playbook when a tag of “spam” or “phishing” is applied to a Host.
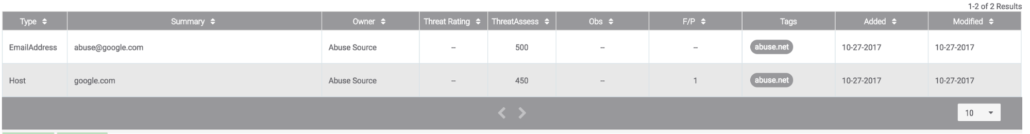
Once you start tagging your Hosts with one of the values defined in the previous step, ThreatConnect will begin querying abuse.net for any contacts that are listed for that domain.
After the trigger event happens we have access to the Host indicator’s properties and can use them in further steps. You can see here we configure the Abuse.net app to read the “host” property of the indicator and start running queries.
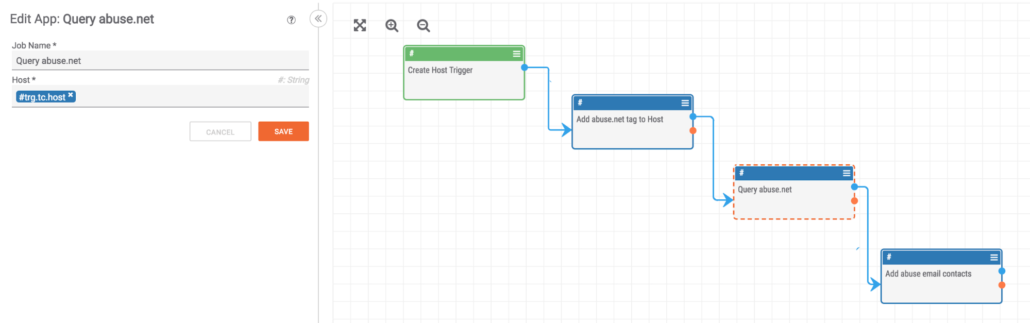
This PlayBook will do the following:
- Add the “abuse.net” tag to the Host
- Get all registered abuse contacts for the domain
Add the Email Addresses and tag them with “abuse.net”
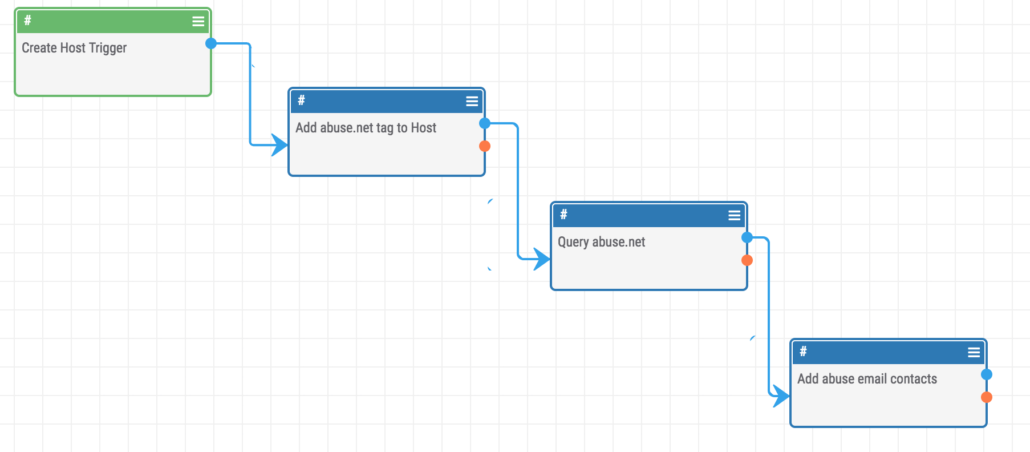
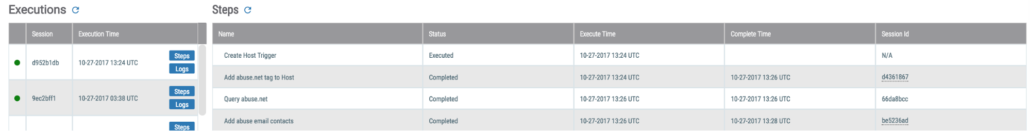
You can also easily check the steps of a playbook by looking in the bottom panel of the PlayBooks UI.
We hope this gives you inspiration to write your own PlayBooks and integrations. You can find more information on this project’s GitHub page or by looking at the ThreatConnect Developer Documentation.
Happy Protecting Your Network!
Read the rest of the Playbook Fridays blog series: