Posted
CTI analysts often face the challenge of managing an overwhelming volume of diverse threat intelligence data, making it difficult to effectively aggregate, correlate, and act on this information. The brain of ThreatConnect’s TI Ops Platform, CAL™, addresses this issue by leveraging AI, natural language processing (NLP), and machine learning (ML) to deliver advanced analytics and global intelligence.
The TI Ops Platform includes several open-source intelligence (OSINT), proprietary CAL analytics-powered intel feeds, and the ThreatConnect user community, tracking 271 billion data points and over 1.1 billion anonymized daily observations from ThreatConnect users worldwide to offer a collective perspective on threats, enhancing organizations’ ability to identify and respond to emerging risks.
In previous blogs, I provided a high-level understanding of CAL and the CAL Automated Threat Library (ATL). In this blog, let’s expand our view of CAL’s novel threat feeds in the Platform, the dozens of open-source intel feeds available for frictionless use, and assess intel feed performance with Report Cards.
OSINT and CAL Feeds
ThreatConnect TI Ops makes it frictionless to add the dozens of OSINT and proprietary CAL feeds that can be turned on with the click of a button in Feed Explorer. We eliminate the labor of finding, subscribing to, and configuring OSINT threat feeds. Our Platform integrates this process, allowing you to effortlessly add threat intelligence data to the Threat Library.
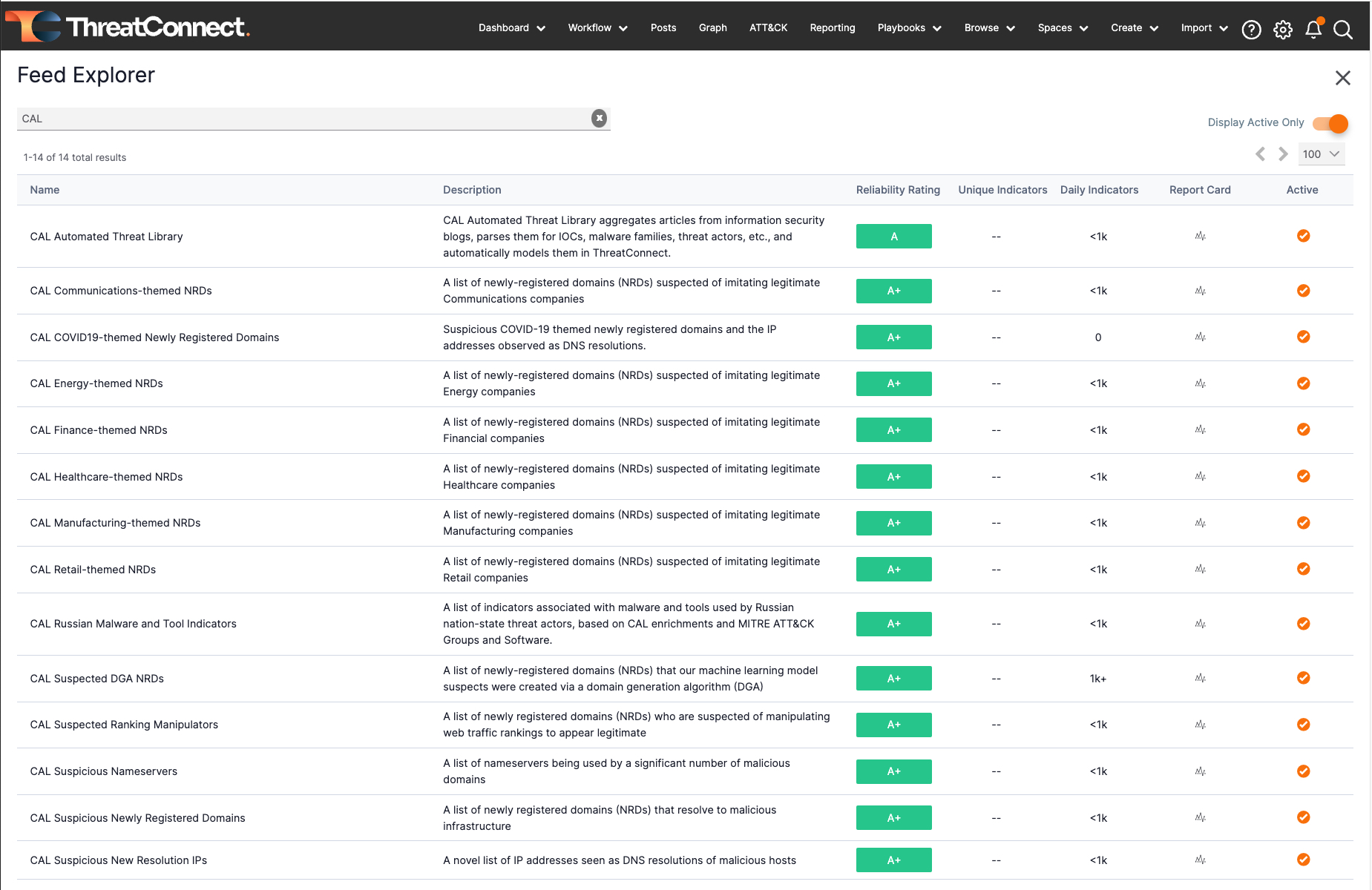
CAL Feeds
Powered by ThreatConnect’s AI-powered analytics, the CAL Feeds provides 15 novel threat intel feeds unique to ThreatConnect.
Not only do the CAL Feeds include CAL ATL, which automatically aggregates articles from information security news sites, industry sites (like CISA), and blogs ,and automatically identifies and extracts IOCs, malware families, threat actors, etc, but the CAL Feeds also provide sector-themed newly-registered domains (NRDs) feeds for energy, finance, and healthcare.
For example, let’s say that as a CTI analyst, you use the CAL ATL feed to keep track of the latest cybersecurity threats through its aggregation and quick parsing of information from a wide variety of trusted security news sources. This helps you quickly identify indicators of compromise (IOCs), malware families, and threat actors to save you valuable time.
Additionally, suppose you work in an industry with sector-specific threats, you may also want to leverage one of our NRD feeds to establish a tripwire in order to detect and respond to targeted threats. This enables analysts to focus on intel specific to your organization and intel requirements.
Feed Explorer and Report Cards
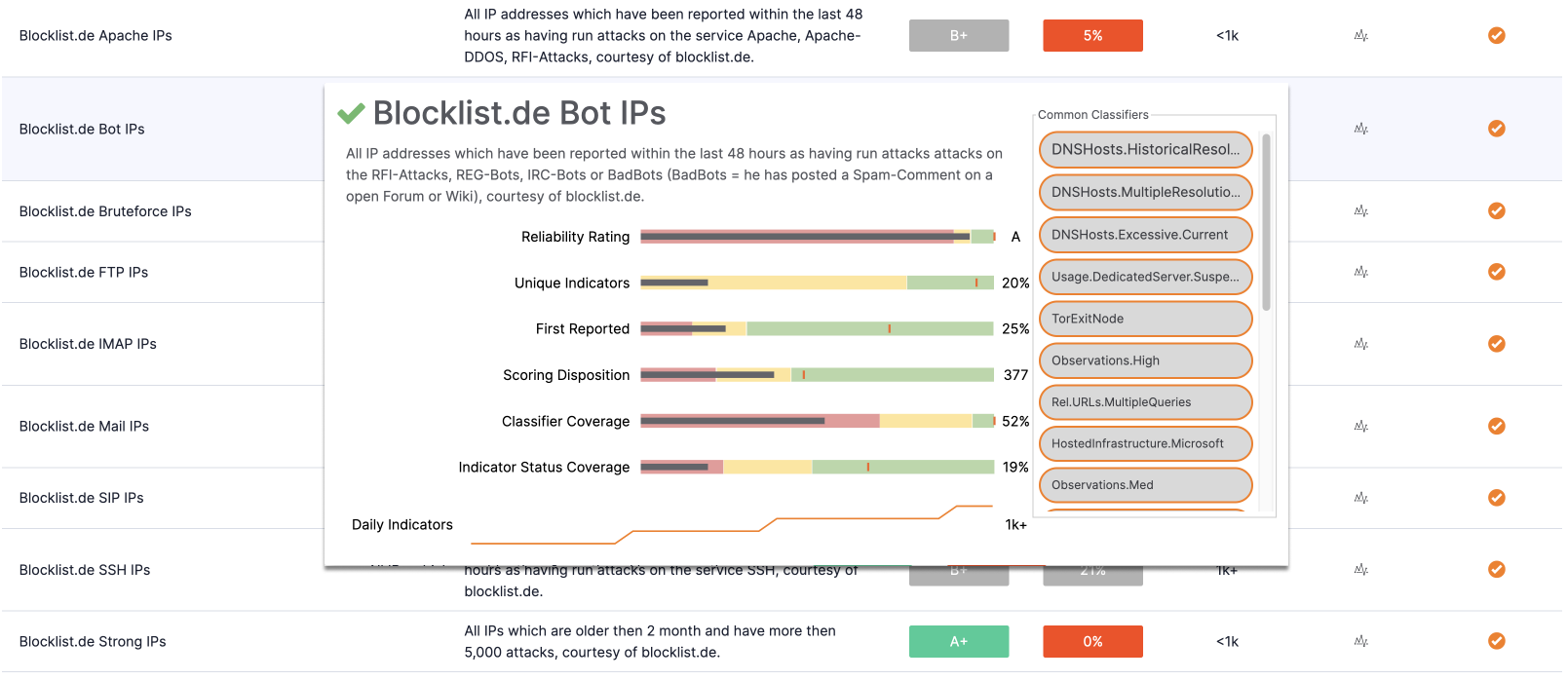
Analysts who want an up-to-date assessment and a comparison between various feeds will want to check out Feed Explorer and Report Cards. These features provide performance-related insights and Report Cards for all the intel feeds enabled in the Platform,.
Analysts can quickly assess feed performance and its value using a Report Card that provides a reliability rating, measures false positives, and performance scores based on multiple factors. Report Cards list Common Classifiers from CAL and analyses for key metrics like Unique Indicators, First Reported, Scoring Disposition, and Classifier Coverage. It’s a great feature to help optimize your intelligence sources (commercial/paid, OSINT, or industry partners), and intel feed budget.
Benefits of CAL Feeds, Feed Explorer, and Report Cards
OSINT and CAL Feeds allow for easy access to threat intel out-of-the-box. Feed Explorer and Report Cards offer analysts valuable insights and comparisons between various intel feeds, facilitating informed decision-making and optimization of intelligence sources.
Want to Learn More?
We offer various ways to learn more about the ThreatConnect TI Ops Platform. Take an interactive tour, check out our website, or request a demo to learn more about how ThreatConnect can help you operationalize your threat intel program.

