Posted
As the risk of cybersecurity incidents increases, the need to be more proactive and increase organizational resilience to cyber attacks is needed. The U.S. Securities and Exchange Commission (SEC) recently released guidelines that publicly traded companies must follow for proper cybersecurity risk management, strategy, governance, and incident disclosure. This blog discusses – essential aspects of these rules and how they impact your company.
What’s in the new rules?
Public companies must prioritize the identification of cybersecurity risks. Every company must understand the nature of threats targeting their industry and organization, such as phishing, malware, data theft, and intellectual property theft. Companies need to assess their level of exposure and determine the potential risk of financial damage from an incident. Based on the outcome of the assessment, a cybersecurity strategy must be developed and tailored to the nature, scope, and severity of the potential risks.
The SEC rules mandate that cybersecurity programs must have governance. Every company must have a designated individual or team responsible for informing the company’s stakeholders about significant cybersecurity matters. This often falls to the CISO. Furthermore, board members or individuals must be aware of their responsibility to oversee and monitor cybersecurity risks and incidents.
There are new requirements mandating reporting incidents that have a material impact on the company. Companies must keep their customers, investors, and the public informed about any such incidents within four business days of determining materiality. The announcement must contain information about the nature of the attack(s), scope and severity, and a timeline of incident occurrence and response.
What is a “material” cybersecurity incident?
Material cybersecurity incidents refer to significant security breaches or events that substantially impact an organization’s information technology systems, data, or operations. These incidents, such as data breaches, ransomware and nation-state attacks, and insider threat activity, can result in severe consequences, including financial losses, damage to reputation, legal issues, and even potential harm to individuals or the public.
Material cybersecurity incidents can have a significant impact on the affected organization. This can manifest in several ways:
- Financial Loss: Organizations may incur direct costs related to investigating and mitigating the incident, as well as potential legal fines and compensation for affected parties.
- Reputation Damage: Public perception of the organization can be severely tarnished, leading to a loss of trust from customers, partners, and stakeholders.
- Operational Disruption: Cyberattacks can disrupt normal business operations, causing downtime and productivity losses.
- Legal and Regulatory Consequences: Organizations may face legal action and regulatory penalties for failing to protect sensitive data or not complying with cybersecurity regulations.
- Notification and Disclosure: In many jurisdictions, organizations are legally obligated to notify affected individuals and regulatory authorities when a cybersecurity incident occurs. Timely and transparent communication is crucial to managing the incident’s fallout.
- Incident Response: Organizations should have a well-defined incident response plan and an incident response retainer in place to address incidents promptly. This includes identifying the breach, containing the damage, recovering systems and data, and conducting a post-incident analysis to prevent future incidents.
The SEC rules place an emphasis on cybersecurity risk management, strategy, governance, and incident disclosure, which are all critical compliance requirements for public companies. The challenge is how do you meet these rules in a way that truly improves security posture, minimizes compliance risks, and does not create undue friction for strapped security teams, especially in a world where materiality is subjectively determined?
The role of cyber risk quantification in addressing materiality
The key challenge companies will have with the new SEC rules is the lack of guidance in defining and explaining material cyber risks for their organization. This means that defining materiality is left to the company’s leaders and directors and will likely be tested in court over time.
We believe that materiality must be delivered in financial terms, and unless a company has past loss information, they won’t be able to quantify their possible exposure easily or defensibly.
ThreatConnect’s Risk Quantifier (RQ) solution puts a financial value on cyber attacks and incidents like ransomware or data breaches. RQ breaks down losses by loss category (e.g., Legal, Settlement, Incident Response costs), enabling a company to evaluate and determine what losses they would tolerate and what would be considered a material impact. Additionally, RQ lets you compare your company’s potential losses ranked against peers to further help you define materiality.
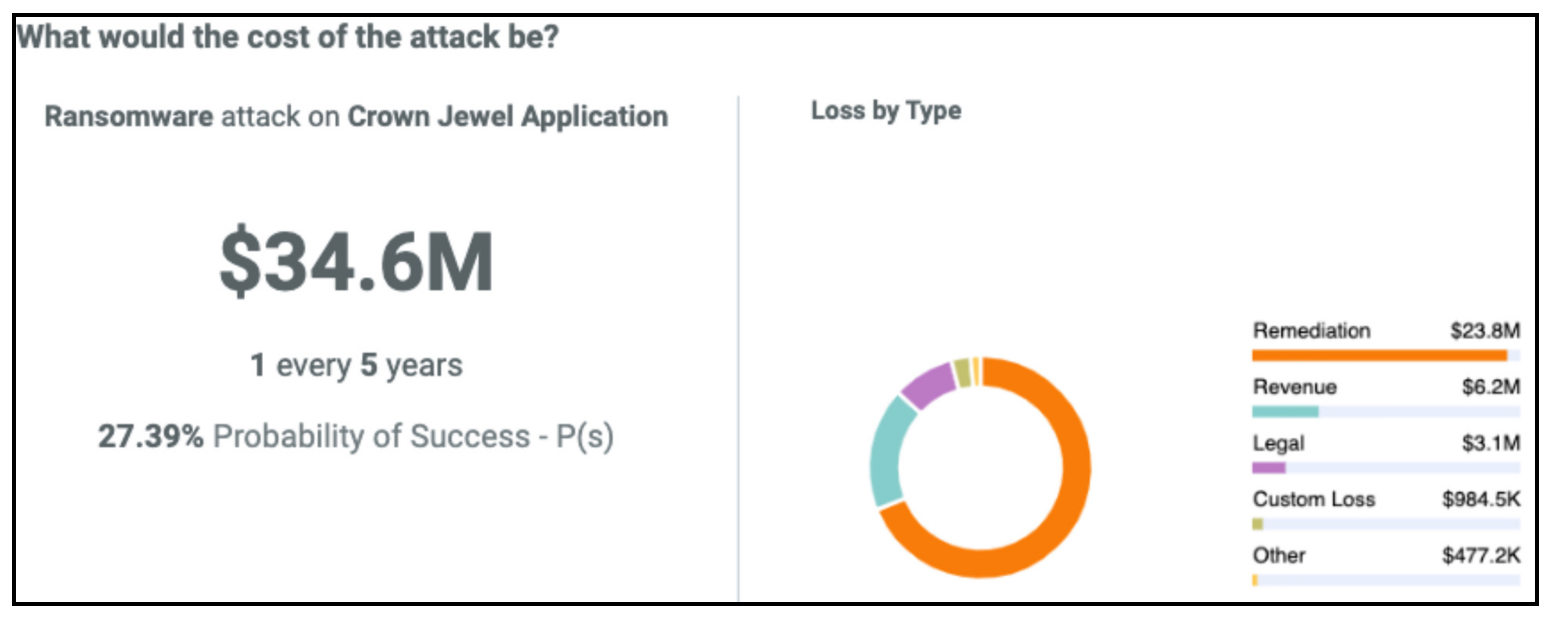
RQ combines those views with the ability to prioritize cyber security improvements by financial risk reduction, and you can cover your reporting and governance functions while working to lower your overall financial exposure in a cost-effective, data-driven manner.
What to Do Now
As with any new regulation, we can expect the requirements and compliance processes to evolve over time. However, it is clear that defining, measuring, and communicating materiality will remain a keystone element of these SEC rules and future regulatory requirements. Developing a consistent, scalable methodology for managing materiality over time is crucial. ThreatConnect meets this need with a unique, automated approach to quantifying cyber risk. To speak with a ThreatConnect cyber risk expert, please reach out.
Looking for more information? Read our joint whitepaper with IBM Consulting on how to operationalize risk quantification.

