Posted
Last October, MITRE released ATT&CK v16. In a blog post, the organization described its latest updates as a mission in balance, with the goal of “striking that perfect chord between familiar and pioneering to keep things real and actionable.”
While MITRE’s ATT&CK framework is a well-known and popular tool in cybersecurity circles, many teams still struggle with the “actionable” part of the equation. Consider this: The ATT&CK matrix for enterprise alone lists 236 techniques across the attack lifecycle. Each technique includes robust data on sub-techniques, procedures, and more.
In other words, integrating updates to ATT&CK across teams and workflows can quickly turn into a tedious and time-consuming task, especially for teams relying on manual methods and spreadsheets.
That’s where our ATT&CK Visualizer tool comes in. At ThreatConnect, we wanted a way to make ATT&CK’s wealth of information easy to take action on. With ATT&CK Visualizer, teams can quickly integrate ATT&CK v16 updates into their workflows to better understand and defend against adversaries. Read on to learn how.
What’s New In ATT&CK v16?
MITRE ATT&CK is a well-known knowledge base that documents adversary tactics, techniques, and procedures based on evolving cyber threats and intelligence. Many cybersecurity teams use the ATT&CK framework for threat detection, defense, and response.
MITRE updates ATT&CK based on publicly available threat intelligence and incident reporting to make sure security teams are equipped with the latest information on adversarial techniques.
In ATT&CK v16, which was released in October 2024, MITRE restructured cloud platforms to better mirror real-world adversary activities. The release also significantly expanded the number of techniques featuring detection notes and analytics and improved coverage of criminal threat actors.
In particular, cybersecurity teams should look out for these three big changes:
- Restructured cloud platforms: MITRE reorganized its cloud platforms into identity provider and Office Suite categories (merging Office 365 and Google Workspace) to more accurately represent how adversaries target cloud services. This is important as adversaries increasingly target cloud-based infrastructure and services.
- More detection notes and analytics: Additional detection notes and analytics help threat intelligence teams better identify adversary tactics, techniques, and procedures. With more granular detection data, teams can improve threat-hunting efforts and mitigate the potential impact of an attack.
- Enhanced criminal threat actor coverage: Expanded criminal threat actor coverage provides threat intelligence teams with deeper context on emerging threat groups and their tactics. This helps teams understand the evolving threat landscape, prioritize responses, and develop targeted threat intelligence that can disrupt criminal activities before they cause significant harm.
Security teams should review ATT&CK v16 in more detail to determine if they need to make any updates to defense mechanisms, to ensure the accurate mapping of threats to enterprise security controls, and to align with the latest intel for proactive threat management.
How To Align Your Security Operations with ThreatConnect’s ATT&CK Visualizer
For some cybersecurity teams, these updates may feel like both a blessing and a curse. While updated information on bad actor behaviors can fuel a more proactive security posture, operationalizing ATT&CK is often easier said than done.
For example, at ThreatConnect we often hear customers struggle with the following:
- Manual tracking (such as in spreadsheets), which is error-prone and time-consuming.
- Limited solutions, which lack the context and automation needed for real-time updates.
As a result, integrating ATT&CK updates into workflows becomes time-consuming, ineffective, or even incomplete.
At ThreatConnect, we knew there had to be a better way to leverage ATT&CK and its regular updates. That’s why we developed the ATT&CK Visualizer.
What Is ATT&CK Visualizer and How Does It Work?
ATT&CK Visualizer is a tool within ThreatConnect’s threat intelligence operations (TI Ops) platform that visually shows the MITRE ATT&CK matrix of tactics, techniques, and sub-techniques. ATT&CK Visualizer automates the interpretation of ATT&CK data associated with threat intel and renders it in a user-friendly interface. In other words, ATT&CK Visualizer makes it easier to see the relationships between threats, techniques, and adversaries.
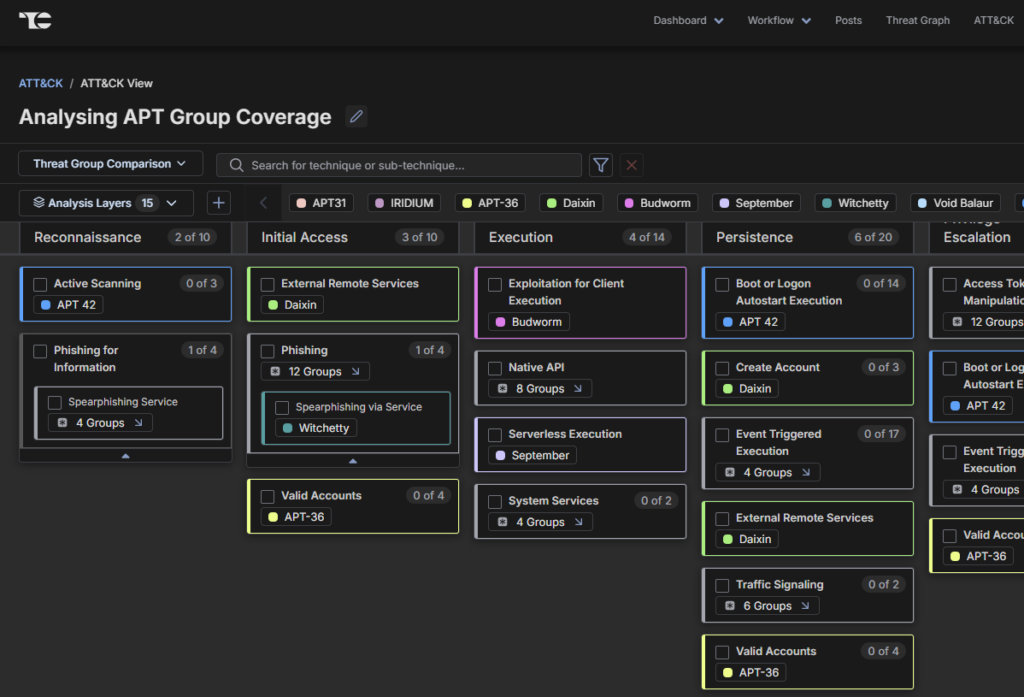
ATT&CK Visualizer automatically maps new ATT&CK techniques within your existing workflows. You can also add intel and contextual data to ATT&CK Visualizer to see any specific tactics, techniques, and sub-techniques associated with specific intel reports. By layering multiple intel data points, you can identify new insights.
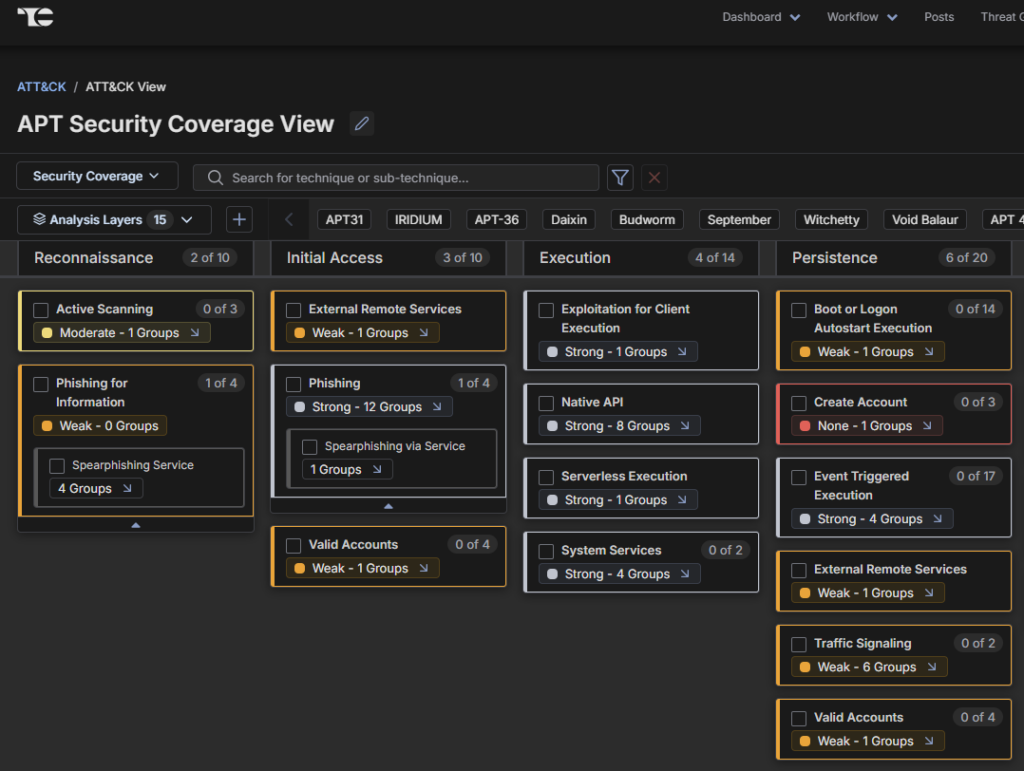
ATT&CK Visualizer also lets you map security control coverage, so you can identify security gaps and assess your defenses down to the technique and sub-technique level.
With ATT&CK Visualizer, you can leverage an interactive interface for easier threat investigation, security gap identification, defense prioritization, and collaboration.
How Does ATT&CK Visualizer Compare to Alternatives?
ThreatConnect’s ATT&CK Visualizer takes the manual effort out of operationalizing the ATT&CK framework so you can better understand and act on threat intelligence. Since it’s part of ThreatConnect’s TI Ops platform, ATT&CK Visualizer also allows for a more holistic view of adversarial tactics tied to your organization’s defenses.
For example, with ATT&CK Visualizer, users can:
- Adapt to ATT&CK updates with minimal effort: Automated updates to ATT&CK-based models that integrate across playbooks and intelligence workflows mean more time for proactive threat-hunting and incident response.
- Increase visibility and accuracy in threat mapping: By integrating ATT&CK updates with contextual intelligence in a centralized platform, you can better spot security gaps, investigate threats, and make informed decisions.
- Enhance collaboration between teams: Use the common language of ATT&CK to foster stronger collaboration among security and management teams.
- Shift from reactive responses to prescriptive defense: ATT&CK Visualizer facilitates continuous improvement and defense maturity. By quickly identifying adversary behaviors and tactics, you can better determine where to focus cyber defenses to stay ahead of threats.
Make ATT&CK Actually Actionable with ThreatConnect
MITRE updates the ATT&CK knowledge base biannually, which means new data on adversary behaviors and tactics are on the horizon. To get the most out of these regular updates, consider leveraging ThreatConnect’s ATT&CK Visualizer.
How are others using ATT&CK Visualizer? Read about top use cases here. Or, take a free tour.

