Posted
In the complex game of geopolitics, the digitized world has to contend with cyber threats that don’t conform to conventional rules. Nowhere is this shift more significant than in the sanctity of electoral processes. With many physical and digital elements involved across federal, regional, state, and local elections, ensuring the integrity of the voting process and results is vitally important.
Cybersecurity has become an increasingly important component as nation-states seek to influence and potentially disrupt elections. Getting ahead of adversaries before they can impact an election is vital to the overall security of electoral systems. To achieve these insights, agencies and their cybersecurity teams need high-fidelity cyber threat intelligence (CTI) that is relevant and actionable. CTI is one of the key tools in making election infrastructure and processes resilient to attacks.
There are excellent resources online from CISA and ENISA if you’d like to learn more about election cybersecurity.
Challenges in Election Security
The heart of election security is not only in the casting and counting of votes, but in the entire democratic process leading up to election day. This process is now tied to the new forms of digital communication; thus, it is inherently at risk. The rise of digital voting systems, the reliance on electronic communication for campaigns, and the pervasive spread of information online have created new points of vulnerability that malicious actors can exploit.
Vulnerabilities in the Electoral Process
While traditional voting mechanisms are not without risk, digital systems introduce new vulnerabilities. These may include:
- Data Integrity: Ensuring the accuracy of voter registration databases and election results against tampering.
- Destructive Malware and Ransomware: The potential for attacks that could disrupt critical election systems and processes.
- Phishing: Targeting election officials or political organizations to gain unauthorized access and steal sensitive information.
Targeted Cyberattacks and Disinformation Campaigns
Cyber threats during the electoral period are not just technical—they often intersect with the world of disinformation and propaganda and, most importantly, are not theoretical. They are happening:
- Social Engineering Attacks: Malicious attempts to sway voters by exploiting social media.
- Information Warfare: Coordinated campaigns to alter perceptions and influence the course of elections.
- Deep Fakes: The creation of misleading audio and video content to discredit candidates or parties.
An example of how the threat actors operate was detailed in the US Justice Department’s indictment of Iran-based actors trying to influence the 2020 Presidential Election. They “… obtained confidential U.S. voter information from at least one state election website; sent threatening email messages to intimidate and interfere with voters; created and disseminated a video containing disinformation about purported election infrastructure vulnerabilities; attempted to access, without authorization, several states’ voting-related websites; and successfully gained unauthorized access to a U.S. media company’s computer network…”
Role of Cyber Threat Intelligence for Threat Awareness and Prevention
CTI is an instrument of awareness in the battle for election security. It is the gathering and analysis of information about adversaries’ capabilities, their intent, and the opportunities they have for attacks across the electoral process. In the context of election security, CTI serves as both a shield and a spear:
- Proactive Monitoring: Utilizing human expertise and tools like threat intel platforms (TIPs) to monitor for potential threats before they materialize.
- Adaptive Response: Employing real-time indicators to tune defenses as situations change.
- Threat Actor Campaign Analysis: Examining previous tactics deployed in similar elections to predict and anticipate future attacks.
The Need for Operational, Tactical, and Strategic CTI
It’s important to reinforce the need for all types of threat intel in election security.
- Operational: Indicators can be used to proactively defend election infrastructure and systems, and tools like email are common threat vectors to compromise organizations through phishing attacks.
- Tactical: Understanding threat actor tactics, techniques, processes, tools and infrastructure, and behaviors can be used to identify defensive gaps and make improvements proactively. For example, MITRE ATT&CK can be used to gain more precise awareness of how adversaries operate and communicate that knowledge across cybersecurity teams.
- Strategic: Guides forward-looking strategic planning and decision-making with greater precision and effectiveness.
The Importance of Collaboration and Information Sharing
Sharing CTI across government agencies and private cybersecurity firms is vital for ensuring election security. In this domain, no entity is an island, and collective threat intelligence is strong currency against the range of cyber threats and actors. Intel sharing takes the form of:
- Public-Private Partnerships: Joint initiatives between government and private sectors to exchange threat information and best practices.
- International Cooperation: Engaging with global partners to create a united front against cross-border cybersecurity threats.
- Information Silos vs. Sharing Cultures: Breaking down barriers to information flow for a more dynamic and responsive collective defense.
How ThreatConnect Can Help
Operationalizing threat intelligence is crucial in ensuring your organization and those you share intel with through partnerships are tracking the most relevant threats and actor activities. The ThreatConnect TIOps Platform has various features and capabilities that make it easier to produce actionable, high-fidelity threat intel and disseminate it to stakeholders in the right format at the right time.
- Intelligence Requirements allows CTI teams to document and action requirements from stakeholders, whether high-level intel requirements (IRs), priority intel requirements (PIRs), ad-hoc requests, etc.
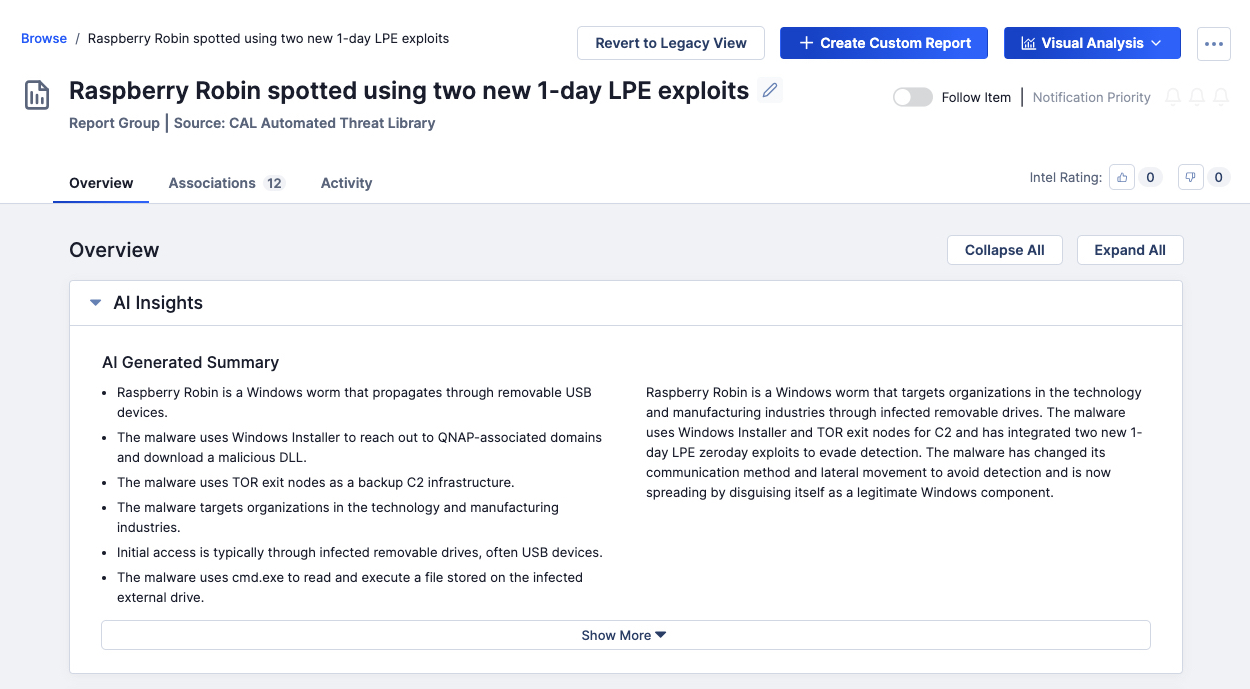
- CAL Automated Threat Library is the time-saving approach to monitoring over 60 definitive sources of open-source intel. The AI-powered analytics in CAL™ uses GenAI, natural language processing (NLP), and machine learning (ML) to automatically summarize the intel, and understand and ingest IOCs and ATT&CK tactics and techniques from those sources, removing hours of manual work from analysts.
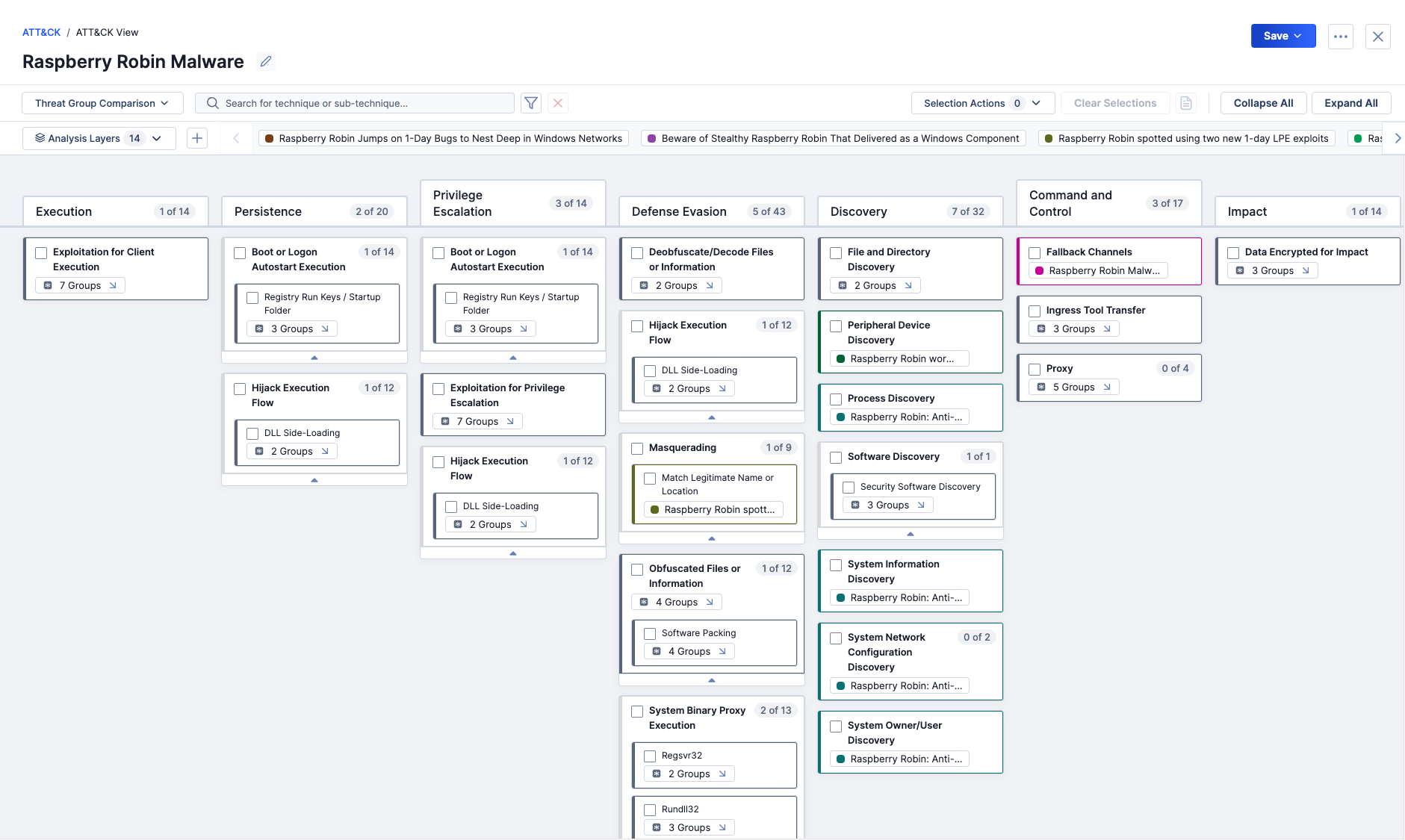
- ATT&CK Navigator enables the tactics, techniques, and sub-techniques tracked across multiple threat intel data points to be displayed visually, enabling analysts to get deep insights into threat actor behaviors and map that against current defensive control coverage.
- Native support for STIX and TAXII, and pre-built Apps for integrating with popular technologies make it easy to share intel with trusted partners through a variety of mechanisms, such as through MISP for example.
Conclusion
Election security in the digital age demands a robust approach to cybersecurity. Proactive, intel-driven defense is not just an option—it’s a necessity. The application of cyber threat intelligence helps assure the integrity of election processes.
For those in the trenches of election planning and execution, the message is clear—CTI is not just an abstract principle. It’s time to make CTI a mandatory component of electoral infrastructure, not just a nice-to-have.
Take the next step!
If you would like to learn more about how ThreatConnect enables threat intel and security operations teams to gain insights on threat actors and proactively improve defenses with high-fidelity threat intelligence, experience an interactive tour of our TI Ops Platform or reach out and chat with one of our experts.

