Posted
State, local, and tribal (SLT) governments are responsible for numerous critical services like educating children, providing safe drinking water, delivering safety and emergency services, managing airports, and administering elections. Yet, the threat landscape for SLT governments is getting even more hostile.
- Ransomware gangs are increasingly indiscriminate regarding who they target and impact. Sophos’ “The State of Ransomware in State and Local Government 2023” report found that ransomware attacks in state and local government increased between 2022 and 2023, up from 58% to 69%, where enterprises reported that ransomware attacks stayed level year over year.
- Nation-states target SLT for various reasons – information gathering, creating FUD and mistrust, pre-emptive planning for retaliation activities, etc. Nation-states are also involved in ransomware too!
In Q3 2022, the Department of Homeland Security announced the State and Local Cybersecurity Grant Program (SLCGP) aimed at improving state and local government cybersecurity. Territorial governments are being supported through the Tribal Cybersecurity Grant Program (TCGP).
- The SLGCP supports strengthening cyber resilience and improving detection, protection, and response to cyber threats.
- The Department of Homeland Security (DHS) announced the availability of $374.9 million in grant funding for the Fiscal Year (FY) 2023
- Established as part of a bipartisan infrastructure law, the SLCGP provides $1 billion in funding over four years.
- Award recipients are encouraged to use grant funding for cybersecurity improvements and capabilities such as cybersecurity planning/exercising, hiring cyber personnel, etc.
So, with this funding allocation to SLTs, what do they need to do to unlock these funds? Three Key Requirements are spelled out to receive funding.
- Assessments and Evaluations – Requires organizations to assess, baseline their security posture, and determine the areas for improvement.
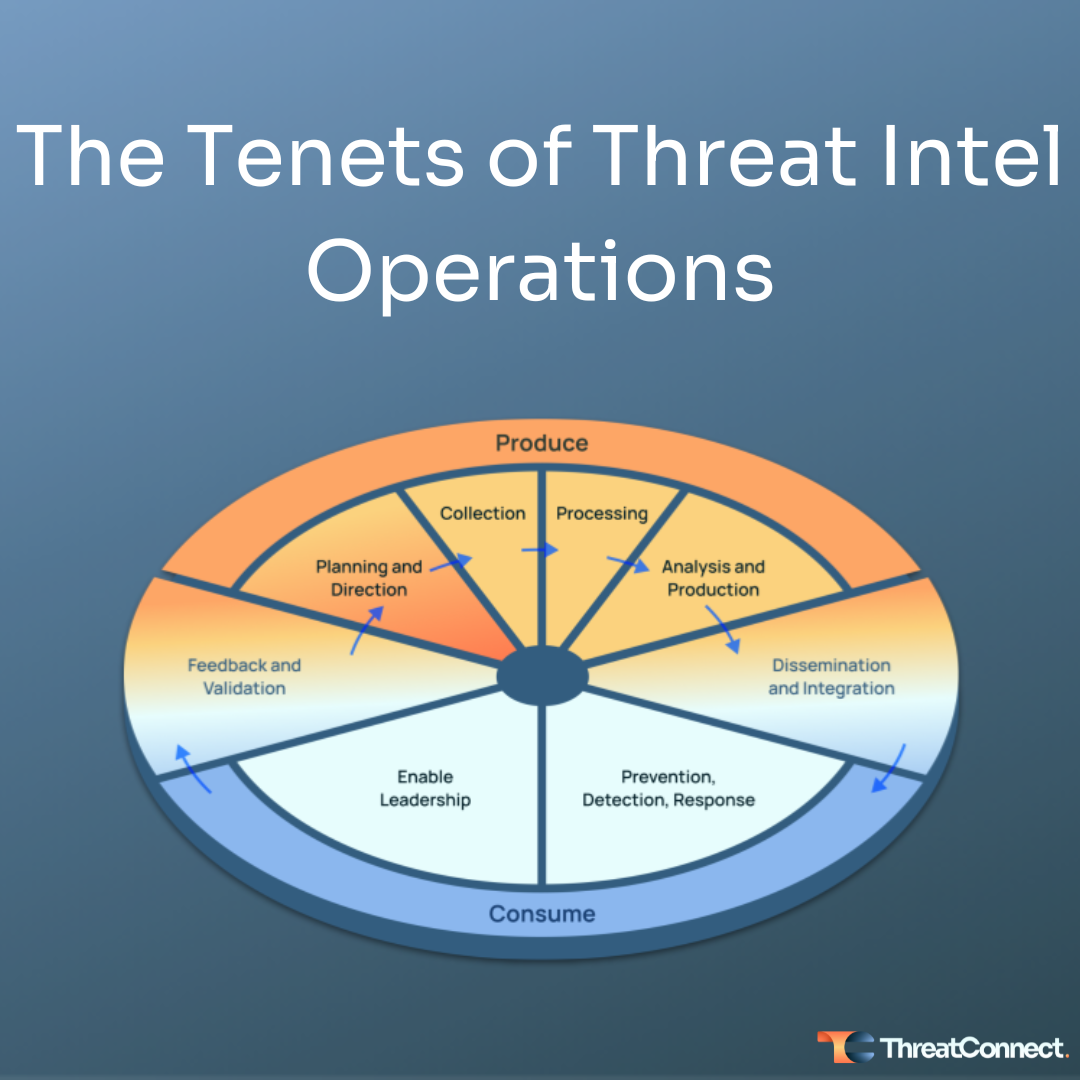
- Building a Cybersecurity Planning Committee – A set of recommended best practices to help SLTs. One is “Engage in rapid bidirectional sharing between CISA and SLT entities to drive down cyber risk.” This is where having a cyber threat intel capability is important as it supports bi-directional sharing of threat intelligence, like indicators of compromise and threat actor activity and behaviors.
- Create a Cybersecurity Plan – This is where the work to be done is agreed and documented.
The Cybersecurity Plan Template (available under “RELATED DOCUMENTS” on the grants.gov website) recommends using NIST CSF, organized around the Identify, Protect, Detect, Respond, and Recover framework. Threat intelligence plays a vital role across all of the phases of the NIST CSF, such as identifying and blocking indicators of compromise or helping incident responders contain, evict, and recover from an attack, leveraging the known behaviors and infrastructure used by a threat actor.
In the Plan Template, there are Best Practice requirements that need to be addressed:
- Monitor, Audit, and Track – Another example of where leveraging unified threat intelligence from a range of sources is needed to monitor and track threats.
- Enhance Preparedness – Having an awareness of the threat actors targeting agencies and departments helps with being prepared, as threat intelligence can act as an early warning signal to take additional actions to bolster defenses.
- Assessment and Mitigation – Being able to assess exposures, like unpatched vulnerabilities, is vital, and threat intelligence also helps here. Knowing which vulnerabilities are being actively exploited, by which threat actors, and for what purposes helps prioritize mitigations to reduce risks to agencies and departments.
Tools and Tactics is one of the additional items in the Plan along with Best Practices. Within Tools and Tactics are two items where a cyber threat intelligence capability and a fit-for-purpose tool are needed:
- Cyber Threat Indicator Information Sharing
- Cybersecurity Risk and Threat Strategies
To share threat indicator information, you need to have the means to benefit from threat intel being shared by the Federal government, a state government, or amongst trusted communities across agencies and departments. This is where having a threat intel platform (TIP) makes information sharing significantly easier, rather than relying on manual processes, spreadsheets, and emails. It helps you aggregate and analyze threat intel to inform threat mitigation strategies and provide input into a cyber risk management strategy, i.e., in the form of operational and strategic intel.
Learn how ThreatConnect can power your cyber threat intel
Cyber threat intel is not a luxury but is mandatory for state and local governments to mature their cybersecurity capabilities and move from being reactive to proactive. Contact us to learn how the ThreatConnect Platform is the optimal solution to manage and operationalize your cyber threat intel.
Other Resources