The industry’s leading modern threat intelligence operations platform
Join a Monthly Live Demo
Why ThreatConnect?
Operationalization
The value of threat intelligence is broadly understood among enterprise security program stakeholders. However, many security programs struggle to operationalize their threat intelligence.
Impact
Infusing threat intelligence into activities across the entirety of security operations makes it possible for security teams to apply their efforts where they’ll have the biggest impact against the most dangerous threats and the most prevalent attack tactics.
Effectiveness
The ThreatConnect Platform enables teams to align security operations and the critical risks to the business, enabling better security processes for higher efficiency and greater effectiveness and creating measurable and demonstrable value for Threat Intelligence Operations and security tool investments.
What
makes us different
Built By Analysts
For Analysts
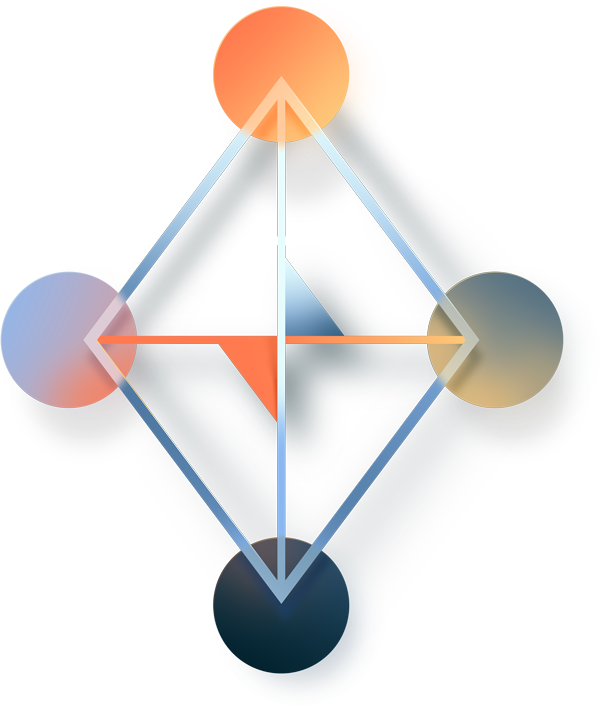
ThreatConnect’s founders come from various security backgrounds, from software engineers to threat analysts. ThreatConnect’s co-founder and current EVP of Product is a co-author of The Diamond Model for Intrusion Analysis, a methodology for analyzing and relating threat information. The Diamond Model is an approach to conducting intelligence on network intrusion events. The model gets its name from the four core interconnected elements of any threat event – adversary, infrastructure, capability, and victim.
Learn More About ThreatConnect

