Are Your Controls Actually Protecting You?
Security leaders often discover that the controls they thought were in place aren’t working as expected or aren’t configured to optimal defenses.
CISOs struggle to report on the effectiveness of controls with confidence.
GRC teams rely on quarterly audits that are quickly outdated.
Security architects and engineers lack visibility into which controls are actively protecting key assets.
From Stale Reports to Real Time Prioritization
Transform control assessment from a static checkbox exercise into a living, data-driven evaluation of real control effectiveness.
Contextualize
Map controls directly to business-critical assets, attack techniques, and security telemetry. Understand active controls and how they’re aligned to the threats that matter most.
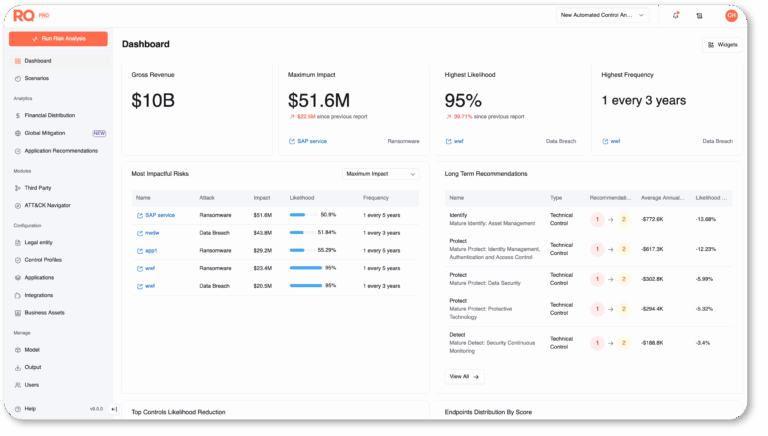
Prioritize
Surface control gaps with real financial consequences using ThreatConnect’s Risk Quantifier. Highlight which ineffective controls expose your most vital applications and which remediations yield the biggest risk reduction.
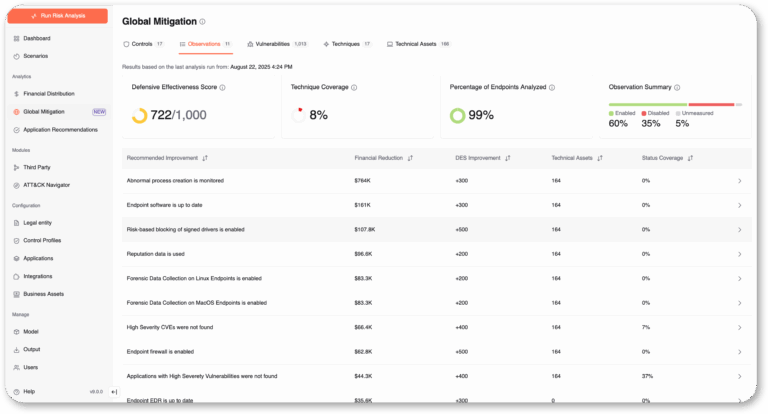
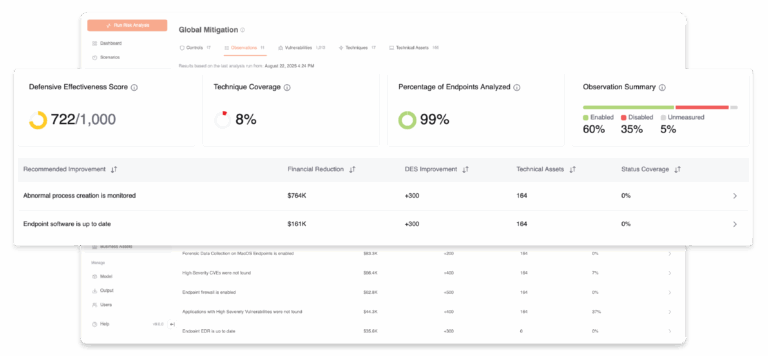
Act & Adapt
Move from manual checklists to continuous control monitoring. Leverage telemetry from CrowdStrike, Wiz, SentinelOne and other tools to validate control deployment and proper configuration, and effectiveness in near real time, not just during audits.
Start CCM Quickly and Scale Easily Across Your Enterprise
Getting Started
Instead of relying on static checklists or annual audits, use real-time data from your security stack to see what’s actually working and what’s not.
- Automatically assess controls using live telemetry from tools like Wiz, CrowdStrike, and SentinelOne
- Highlight missing or ineffective controls in critical applications with business risk context
- Identify and prioritize control weaknesses that pose the greatest financial exposure
- Generate remediation recommendations aligned with specific threat techniques and business needs
Grow With Us
ThreatConnect empowers you to shift from technical audits to continuous, risk-aligned governance across teams and workflows.
- Align detection, response, and vulnerability teams using shared control visibility and threat context
- Visualize coverage gaps across MITRE and evaluate compensating controls in one view
- Map controls directly to financial outcomes and strategic KPIs for executive reporting
- Establish a closed loop where control insights continuously inform detection engineering, policy, and procurement decisions
Outcomes That Matter
Reduce Audit Fatigue
Saved 200+ analyst hours per quarter across three audit cycles
Quantify Control Failures
Tie ineffective controls to actual financial exposure to drive executive urgency and budget alignment.
Surface Hidden Gaps
Identify misconfigurations that would’ve gone undetected for months in manual reviews.
Track Risk Reduction Over Time
Demonstrate measurable ROI from control remediation using before-and-after financial deltas.





