ThreatConnect Intelligence Anywhere
Instantaneously scan and identify relevant pieces of information from web-based resources with a simple click of a button. Quickly understand what you currently know about an Indicator or threat and add it to your threat library to aid in future analysis and investigation efforts.

From dispersed data to a single source of truth
Gain insights on threats and threat actors and memorialize threat intelligence through real-time access to a diverse range of sources from data feeds to ThreatConnect CAL™ Automated Threat Library (ATL), which includes unique insights not available anywhere else.
From manual lookups to simplified threat analysis
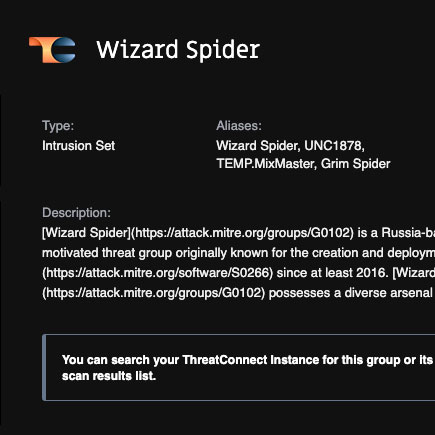
Instantly match known threat actor aliases so you get more context to make fast and informed decisions.
From working
in silos to operationalizing threat intelligence
Increase the value of your threat intelligence program by giving everyone on the security team a handy tool that automatically shares rich, contextualized threat intelligence on web pages or web-based SaaS tools.
ThreatConnect Advantages
Natural Language Processing (NLP)
Detect language indicative of specific MITRE ATT&CK techniques when scanning web-based resources to learn more about a threat.
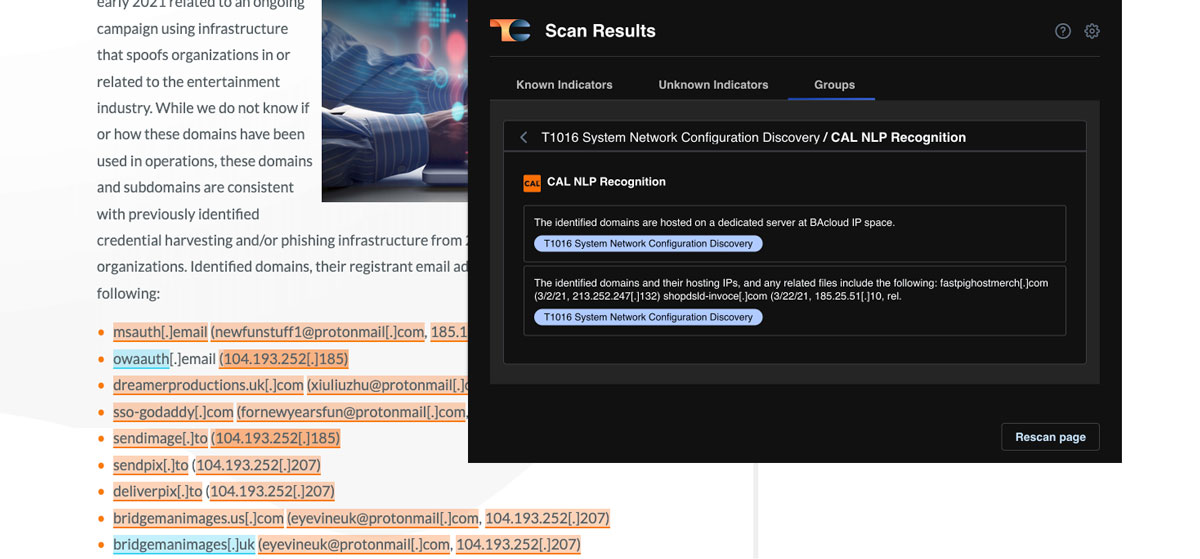
CAL aliases
Automatically translate the aliases of threat actor groups used across the threat intel landscape and stop using spreadsheets.
CAL insights
Leverage the global context from CAL, including classifiers from our analytics, global trends on observed indicators, and analyst insights from the ThreatConnect ecosystem.
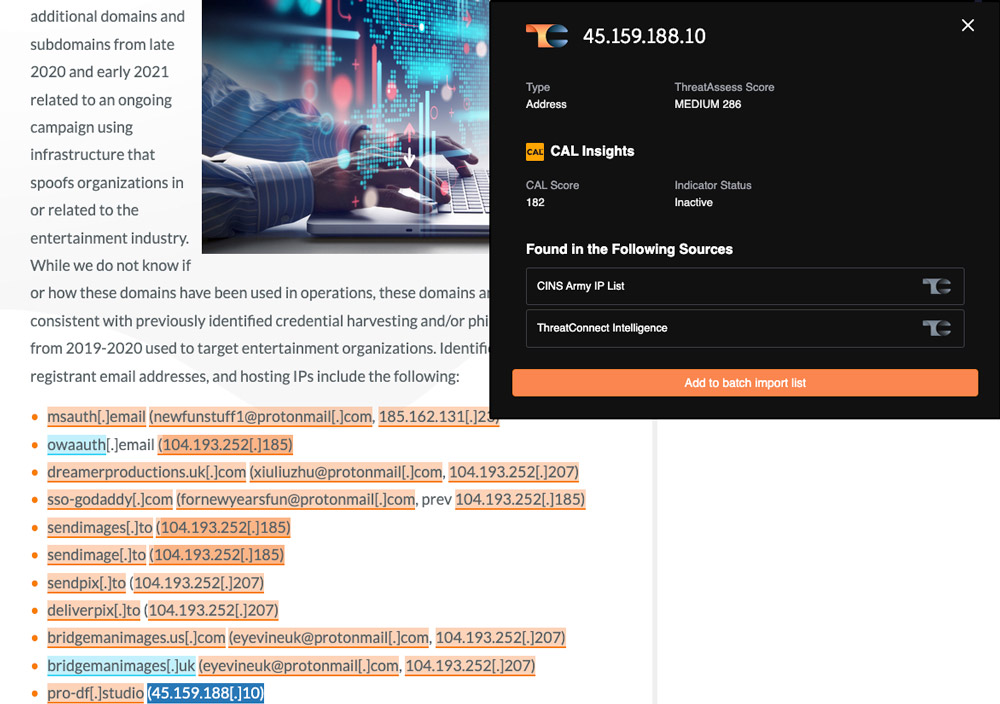
Fewer clicks. Quicker results. Instantly access insights directly from a web browser.