No Results Match Your Search
Please try again or contact marketing@threatconnect.com for more information on our resources.

Smarter Security Series – How Do Companies Manage The Risk For Low-frequency And High-Severity Events?
As issues related to cybersecurity evolve, the potential financial impact of ransomware attacks has come to the forefront of every conversation. Organizations are particularly concerned about this risk, especially since significant resources are already committed to bolstering defenses. Despite these investments, the risk can’t entirely be eliminated. Jerry Caponera, the General Manager of Risk Products […]

ThreatConnect Customers Share Their Improved Security Outcomes
ThreatConnect surveyed its customers on the benefits they’ve realized, and in this e-book, you’ll see real-world results achieved by some of the most sophisticated cyber threat intelligence and security operations teams in the industry. These teams rely on ThreatConnect every day to help them protect and defend their enterprises. See how else ThreatConnect helps our customer improve their security outcomes.

Smarter Security Series – How Has The Increase In Ransomware Attacks Changed The Risk Posture For Companies?
In the current digital landscape, one of the significant concerns at the forefront of every conversation is ransomware – a trending topic of discussion, given its potential for severe losses and the consistent increase in frequency. Jerry Caponera, the General Manager of Risk Products at ThreatConnect, is joined by Yousef Ghazi-Tabatabai, Director, Risk at PwC, […]

Smarter Security Series – What Are The Challenges With Risk Quantification?
Jerry Caponera, the General Manager of Risk Products at ThreatConnect, was joined by Yousef Ghazi-Tabatabai, Director, Risk at PwC to discuss the impediments to measuring cyber risk in an organization. The field of cybersecurity has been witnessing a significant paradigm shift, with organizations beginning to see the value of cyber risk qualification. Despite the […]

Smarter Security Series – Introducing Colin
Introducing ThreatConnect’s Smarter Security Expert Series! We’re interviewing the brightest minds in the cyber industry and getting their expertise on current trends and tips and tricks for a successful modern security team. For our first guest, we’re joined by Colin Anderson, CISO at Ceridian and ThreatConnect’s newest Board Advisor! Colin sat down with our VP […]

Smarter Security Series – How Companies Approach Cyber Risk Quantification
Jerry Caponera, the General Manager of Risk Products at ThreatConnect, was joined by Yousef Ghazi-Tabatabai, Director of Cyber Risk at PWC, in this video interview to discuss how companies are approaching Cyber Risk Quantification today. They shared viewpoints on evolving trends in risk management, focusing particularly on risk quantification and reporting. Yousef provided an overview […]

Use Cases and Quick Wins for Offensive Security & Vulnerability Management
Join our webinar to explore offensive security and vulnerability management with Joe Rivela. Learn practical applications, vulnerability triage, exposure assessments, and asset awareness to elevate your security operations.

ThreatConnect Low-Code Automation
ThreatConnect’s Low-Code Automation gives you the flexibility, consistency, and rapid speed implementation your security team needs.
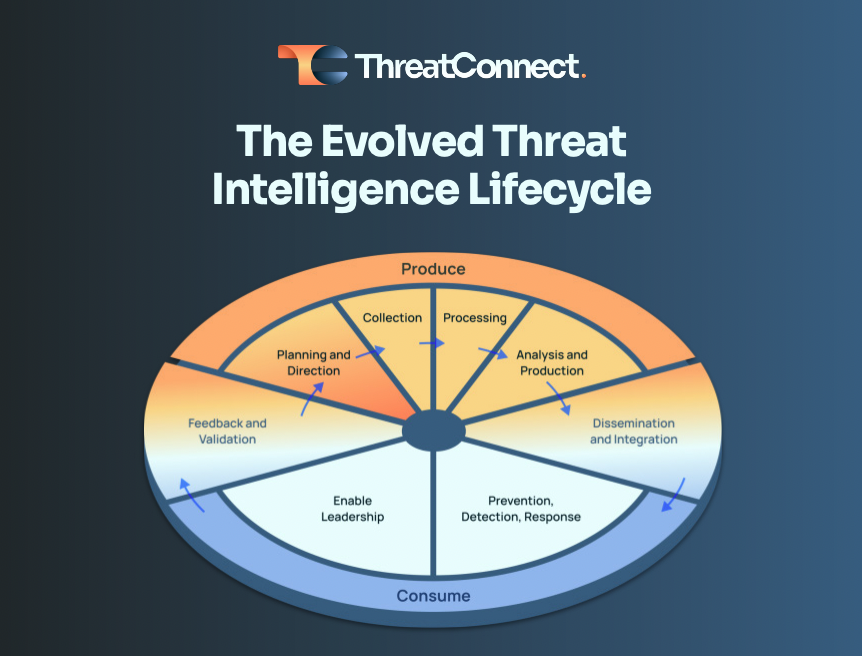
The Need for an Evolved Threat Intel Lifecycle Webinar
In order to evolve a threat intelligence function from a nice-to-have to an essential component of a security team, we need to unpack two key weaknesses of the threat intel lifecycle. Join us in this on-demand webinar were we explain why TI Ops requires an Evolved Threat Intelligence Lifecycle, one that emphasizes the planning and […]

Smarter Security Series – The Importance of Cyber Risk Quantification
Introducing ThreatConnect’s Smarter Security Expert Series! We’re interviewing the brightest minds in the cyber industry and getting their expertise on current trends and tips and tricks for a successful modern security team. For our first guest, we’re joined by Colin Anderson, CISO at Ceridian and ThreatConnect’s newest Board Advisor! Colin sat down with our GM […]

Webinar: Smarter Security Series – How To Move Your CTI Team From A Reactive To Proactive Posture
Introducing ThreatConnect’s Smarter Security Expert Series! We’re interviewing the brightest minds in the cyber industry and getting their expertise on current trends and tips and tricks for a successful modern security team. For our first guest, we’re joined by Colin Anderson, CISO at Ceridian and ThreatConnect’s newest Board Advisor! Colin sat down with our VP […]

Smarter Security Series – How To Move Your CTI Team From A Reactive To Proactive Posture
World-renowned Cybersecurity Executive Colin Anderson, recently sat down with Toby Bussa, VP of Product Marketing at ThreatConnect. Anderson is the Senior Vice President and CISO at Ceridian, a top HR Management Software company. With a vast and impressive career, Anderson has also held high-ranking roles at Levi Strauss and Safeway. Besides actively working in […]



