Polarity Intel Edition
Streamlining Distribution of Intel from CTI Teams to SecOps
Bring TI to the point of decision and action for SOC, incident response, threat hunting, and vulnerability management – without making them leave their pane of glass.
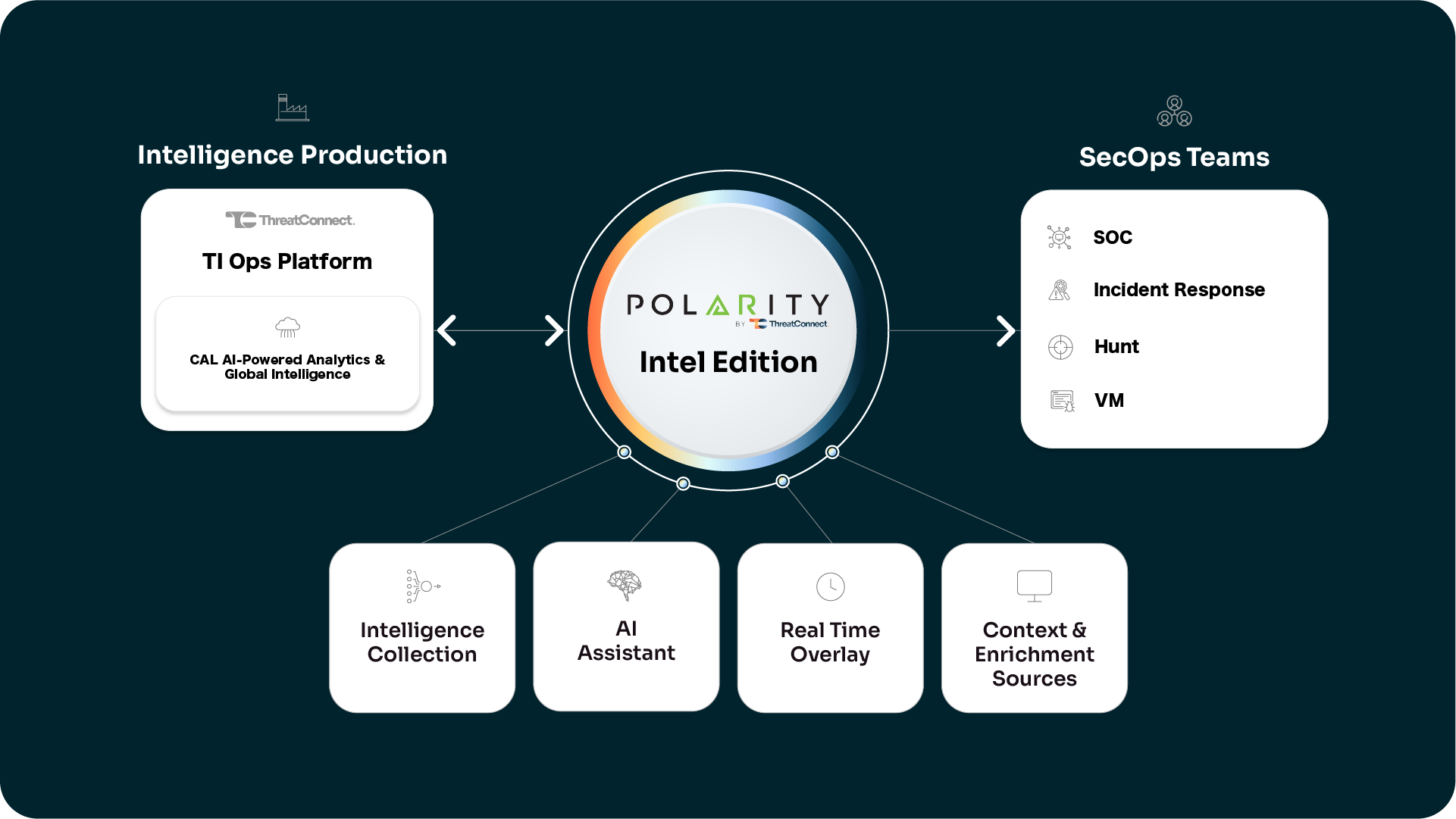
Key Capabilities of Polarity
Enabling both the CTI and SecOps Teams
CTI Teams
- Streamline collection and processing by gathering new intel from anywhere
- Uncover potential insights during analysis by correlating new information with existing intelligence
- Collect feedback and validation by getting real-time updates from your stakeholders on the intelligence you create and what they’re seeing on the ground
SecOps Teams
- Reduce the time it takes to triage an alert with real-time intelligence delivered to your preferred pane of glass
- Avoid burnout with tools that move you away from false positives quickly and confidently
- Make quick sense of intelligence with interactive AI summaries
Direct Access to Threat Intel in the TI Ops Platform
Unlock the value of your threat intel across security operations without adding “yet another pane-of-glass.” Enable intel to be updated and new intel to be easily memorized into the TI Ops Platform, ensuring everyone has access to the latest knowledge.

Quickly Triage Alerts
Reduce the time it takes to triage alerts with real-time access to the Threat Library in TI Ops, OSINT, and other essential contextual data sources to help triage and prioritize the most urgent information.
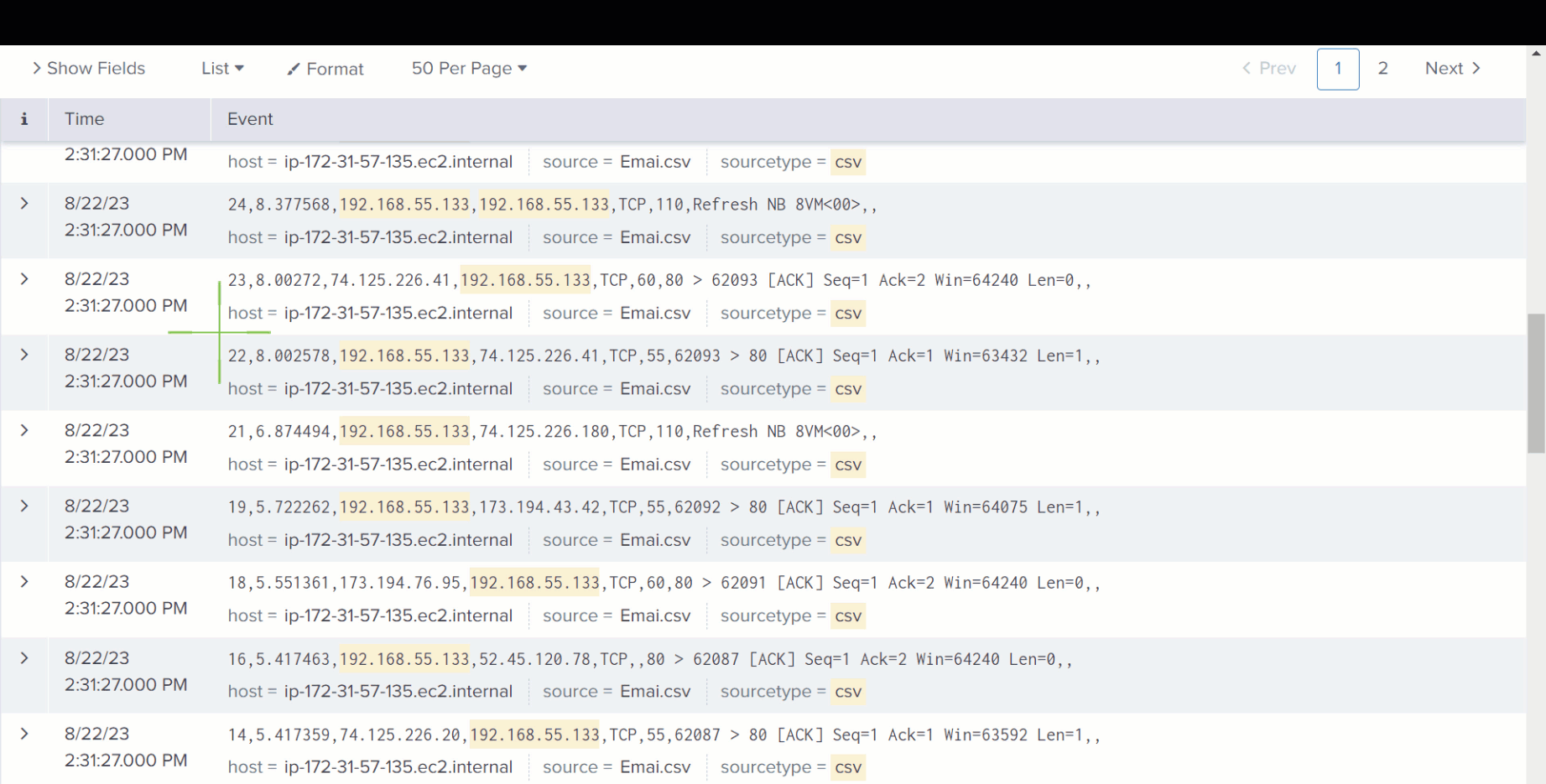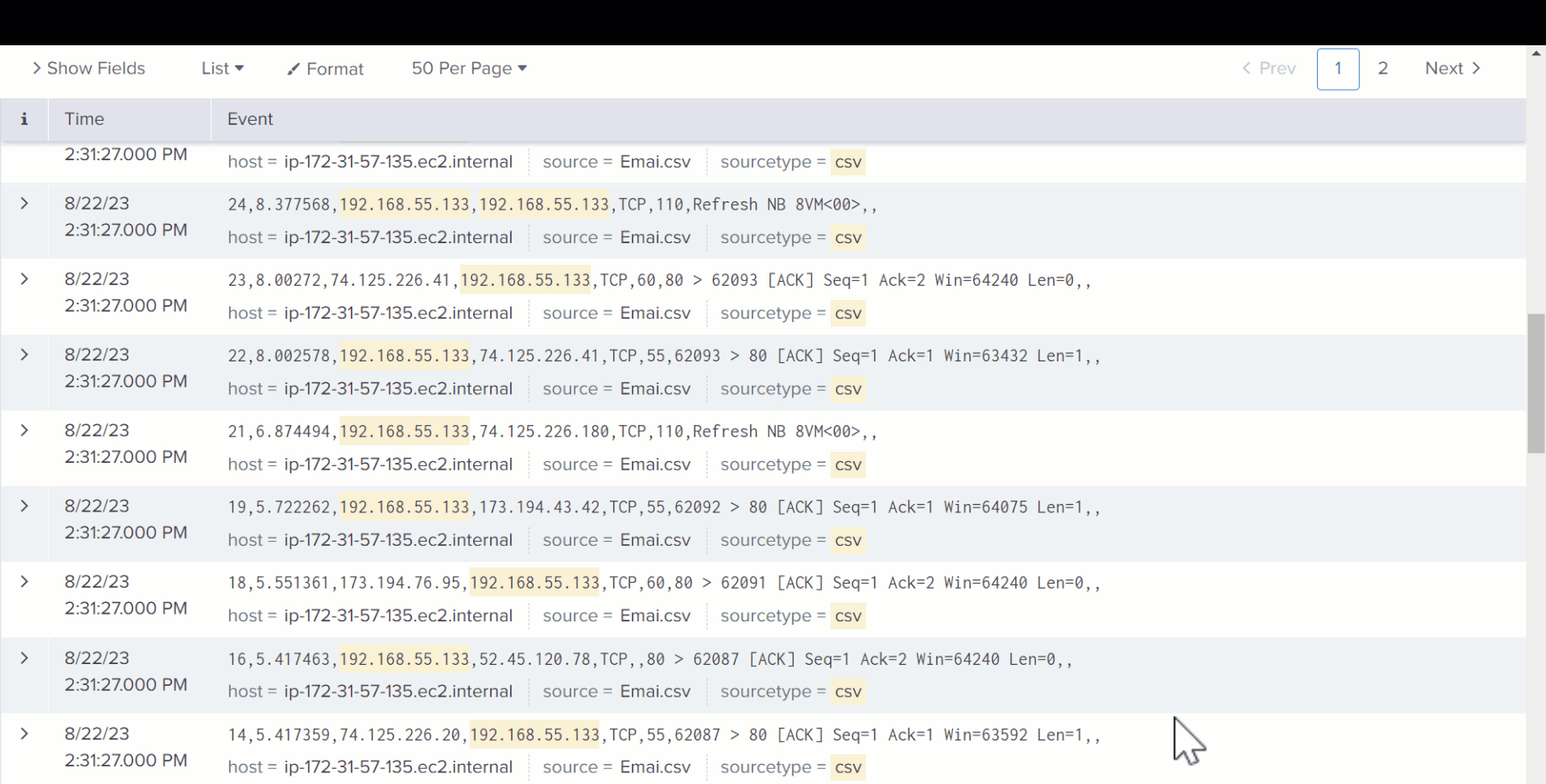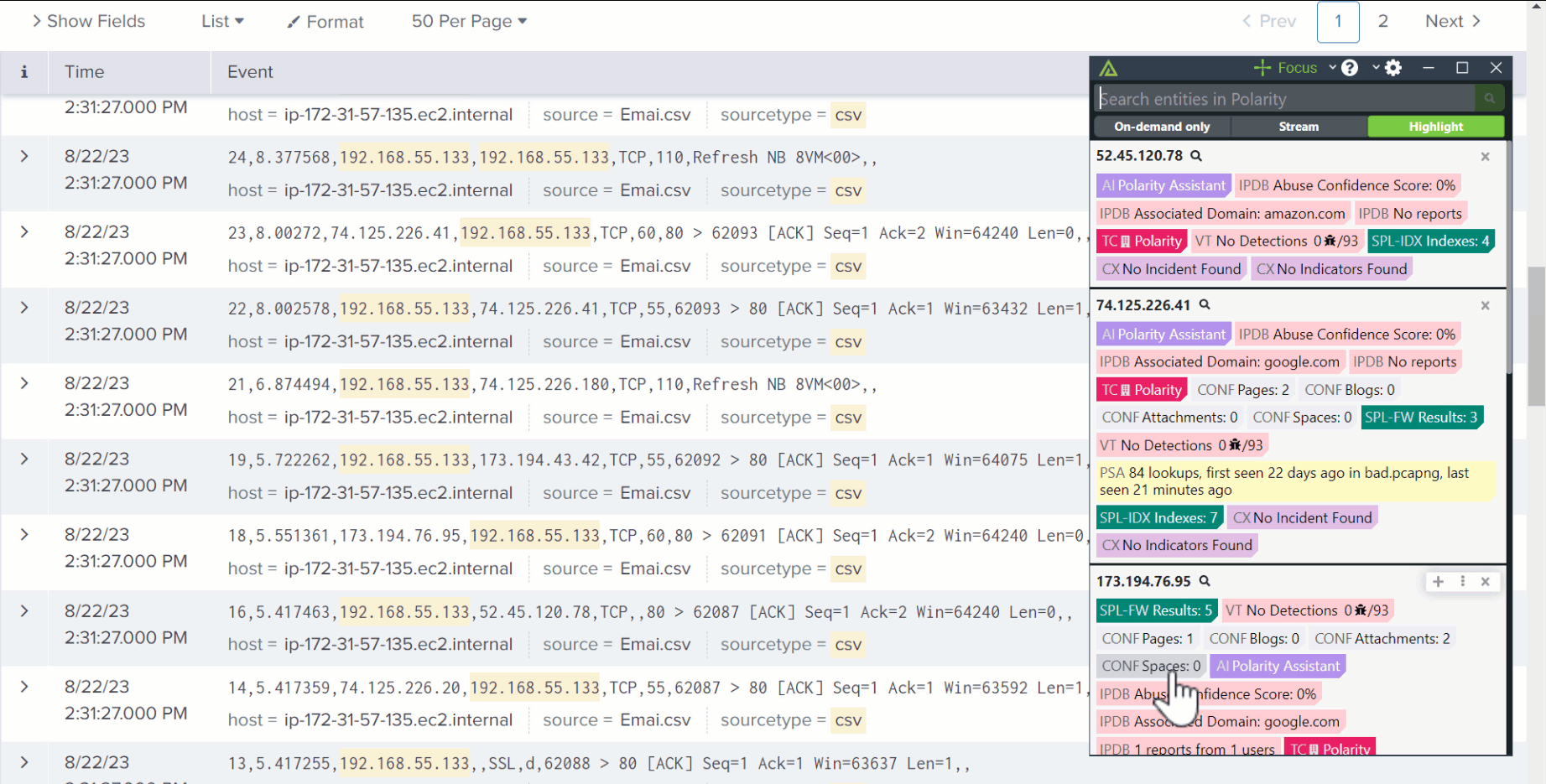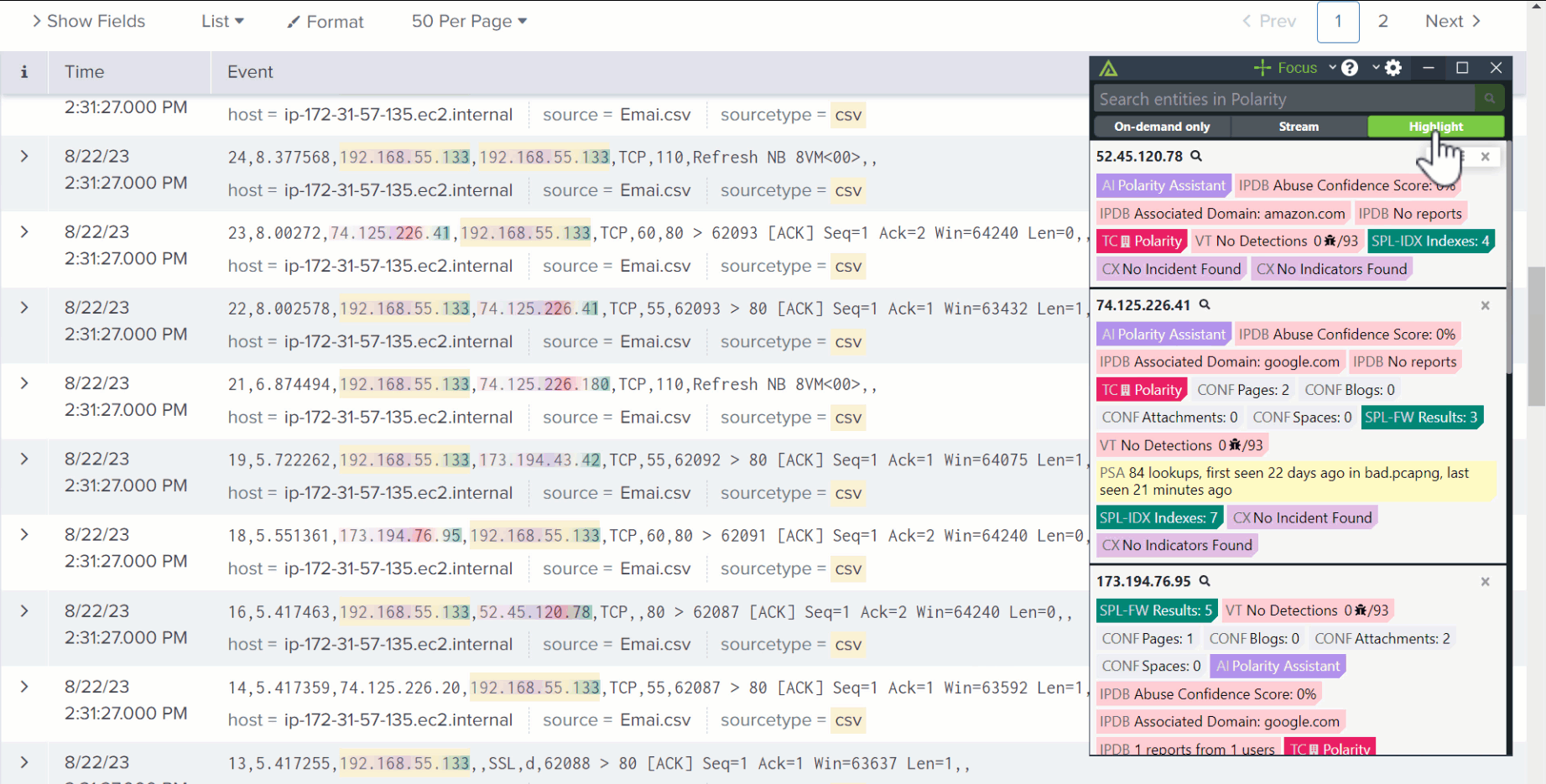
Hunt Threats Smarter
Enable threat hunters to quickly access threat intel and essential context to hunt faster and smarter. Help them find and expel attackers who sneak into their networks and systems, minimizing their ability to cause havoc.

Enhance Incident Response
Give analysts investigating and responding to incidents real-time insights on threat actors. Help analysts minimize disruptions, costs, and reputational impacts from attacks.

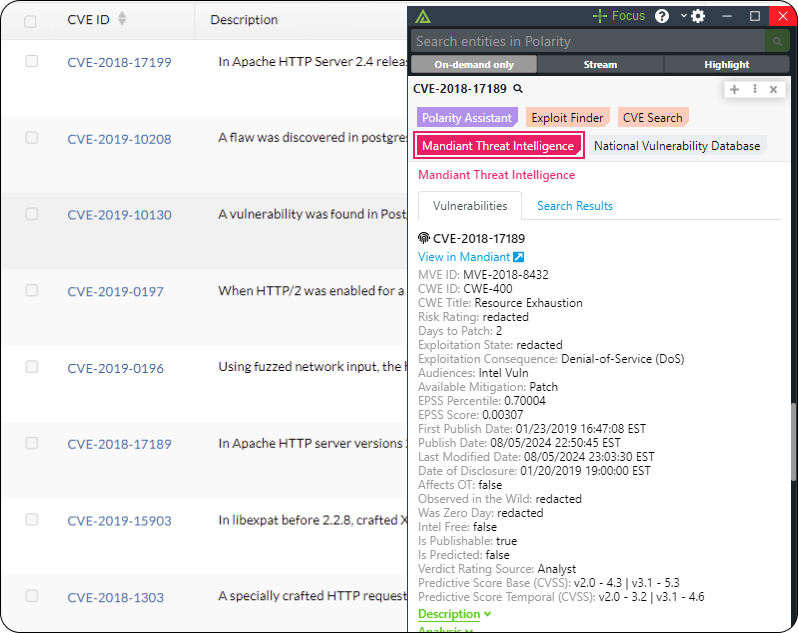
Prioritize Critical Vulnerabilities
Quickly determine which of the thousands of new vulnerabilities that come out each month need to be addressed. Polarity Intel Edition makes it easy to access the threat and vulnerability intel required to triage and prioritize vulnerabilities for remediation quickly.
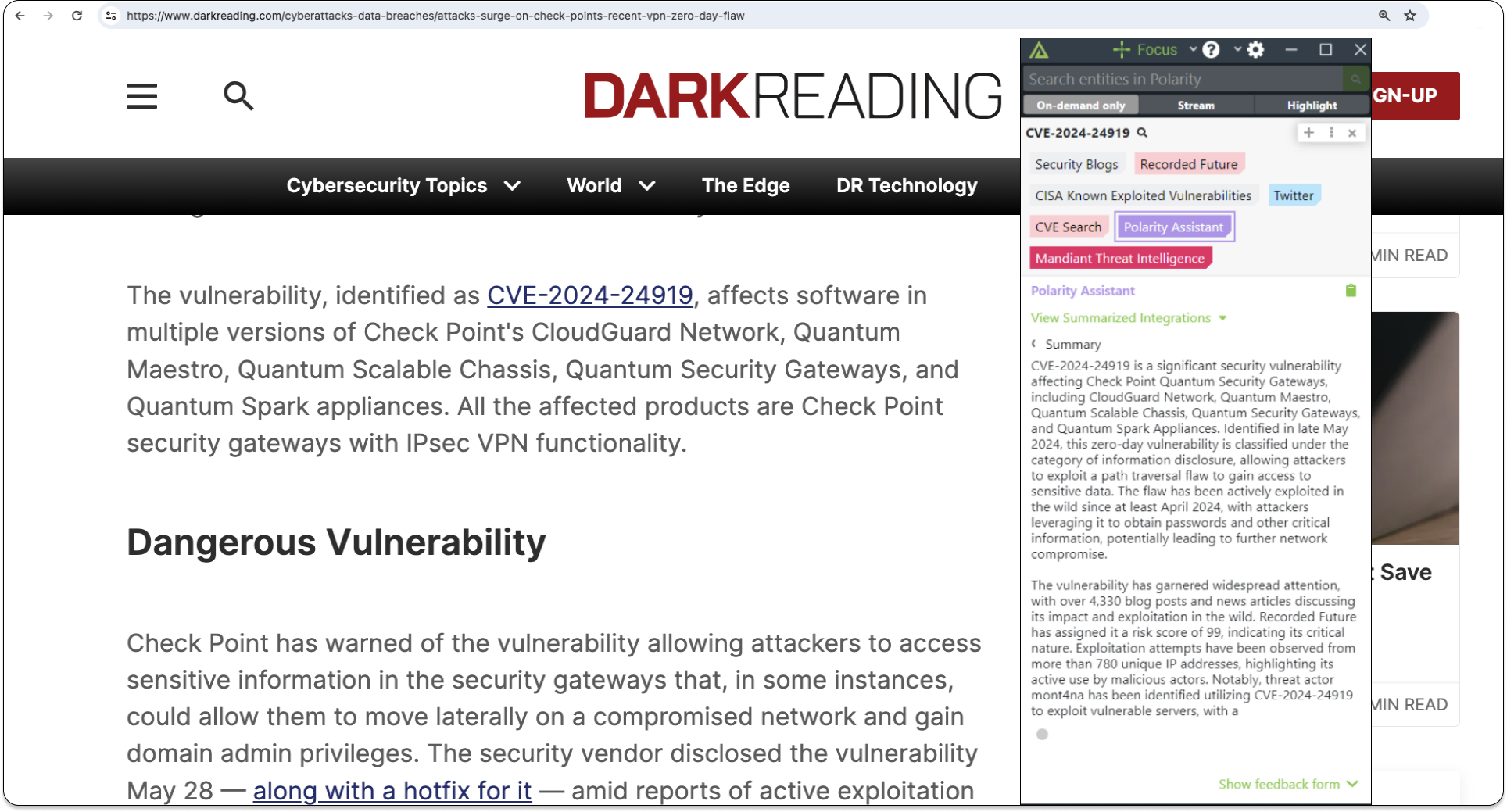
Leverage the Power of GenAI
Quickly understand the scope and nature of potential threats using GenAI tools like ChatGPT, Azure AI, and Gemini, while ensuring they are used safely, consistently, and within corporate policies.
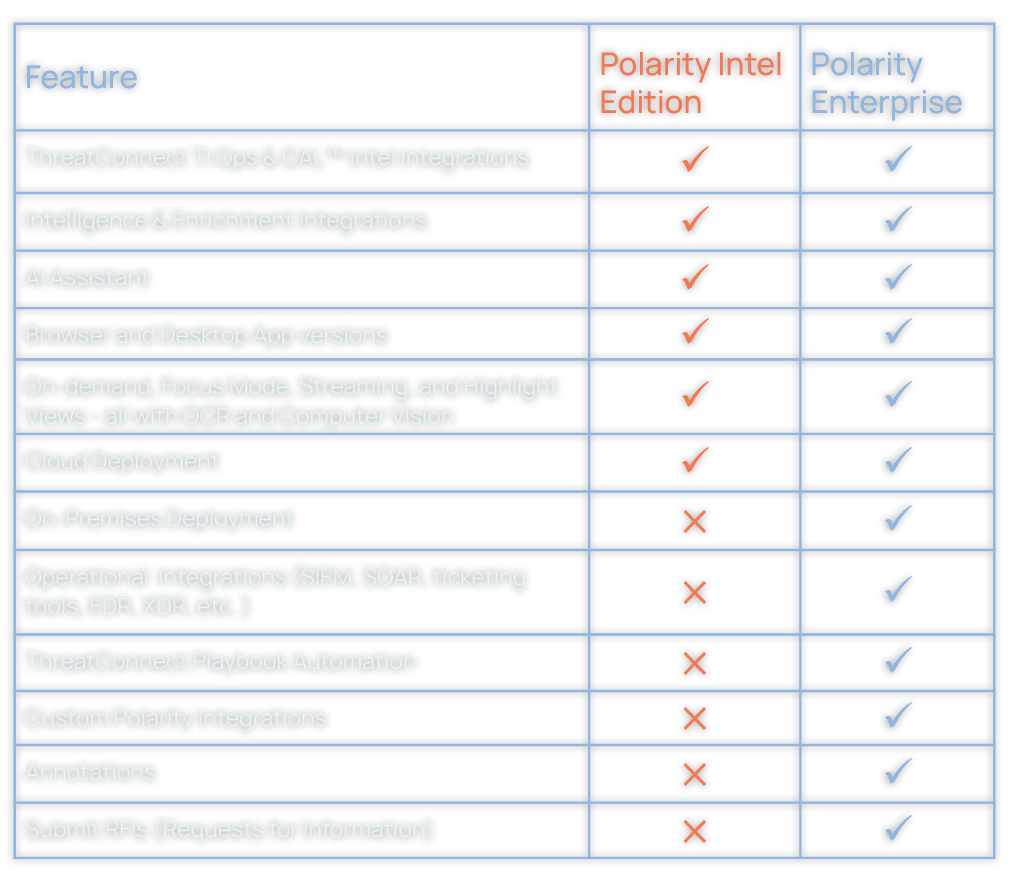
Comparing Polarity Intel Edition and
Polarity Enterprise
Polarity integrates with 50+ intelligence sources














Discover More About Polarity Intel Edition
A Potent Combination
Learn about the combined power of ThreatConnect TI Ops and Polarity Intel Edition.
Polarity Intel Edition by ThreatConnect Solution Brief
Learn how Polarity Intel Edition removes the friction to access and consume threat intel.
See Polarity Threat Intel Edition in Action
See Polarity Threat Intel Edition live and get your questions answered,
