Polarity Enterprise by ThreatConnect
Enhance your security operations with the Polarity Enterprise. Discover our solution for federated search, real-time contextual intelligence, and seamless integrations.
of analysts worry about missing threats in oceans of data
– Crowdstrike Global Security Attitude Survey
say alert volume is hurting their personal lives
– CISO Magazine
of teams miss critical alerts due to ineffective prioritization
– Mandiant – Global Perspectives on Threat Intelligence

Computer vision recognizes indicators and keywords in any window – no setup, no integration.
Polarity federated search returns intel, enrichment data, and team knowledge from across 150+ tools.
GenAI assistant explains threats, context, and actions – all summarized instantly.
Run playbooks, annotate, submit RFIs, or push updates to TI Ops – right from the overlay.
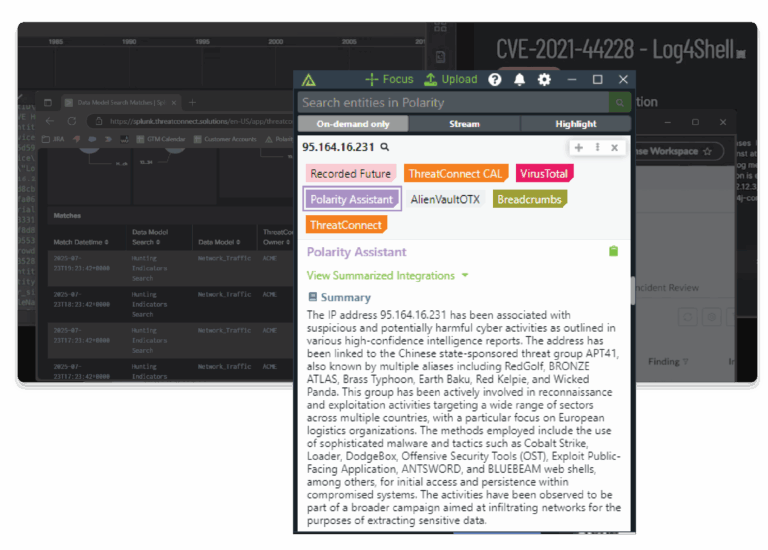
Start fast. Move from constant tool and context-switching to AI-assisted speed and clarity on day one.
Scale context and collaboration across all teams, and amplify the effectiveness of your existing tools.

Triage alerts faster by instantly surfacing threat context next to matching IOCs
Correlate logs to known threats using real-time overlays from intelligence sources
Reduce alert fatigue by filtering low-priority events using enrichment scoring

Trigger automated playbooks directly from the overlay – no console hopping
View enrichment and confidence scores on indicators before deciding to escalate
Capture analyst decisions to improve future automation logic

Correlate endpoint alerts with threat actor TTPs from TI Ops
See whether a process, domain, or hash has been previously analyzed or suppressed
Investigate faster by overlaying intelligence from previous incidents

Prioritize CVEs based on active threat campaigns and financial risk (via RQ)
See CAL enrichment showing whether a vuln is being exploited in the wild
Reduce ticket noise by filtering out low-priority findings

Auto-enrich tickets with threat intel and business risk scores
Submit RFIs or annotate key insights from the overlay
Route tickets based on criticality, intel confidence, or team feedback

Federated search across all sources – no query language required
AI summaries explain the relevance of any domain, IP, file, or email
Push new intel or annotations directly into TI Ops from any screen
No context switching. No integrations needed to start.
Understand threats fast with no query language required.
Curated intel, global analyst feedback, and real-time enrichment.
Collaborate across teams and trigger response actions without leaving your screen.
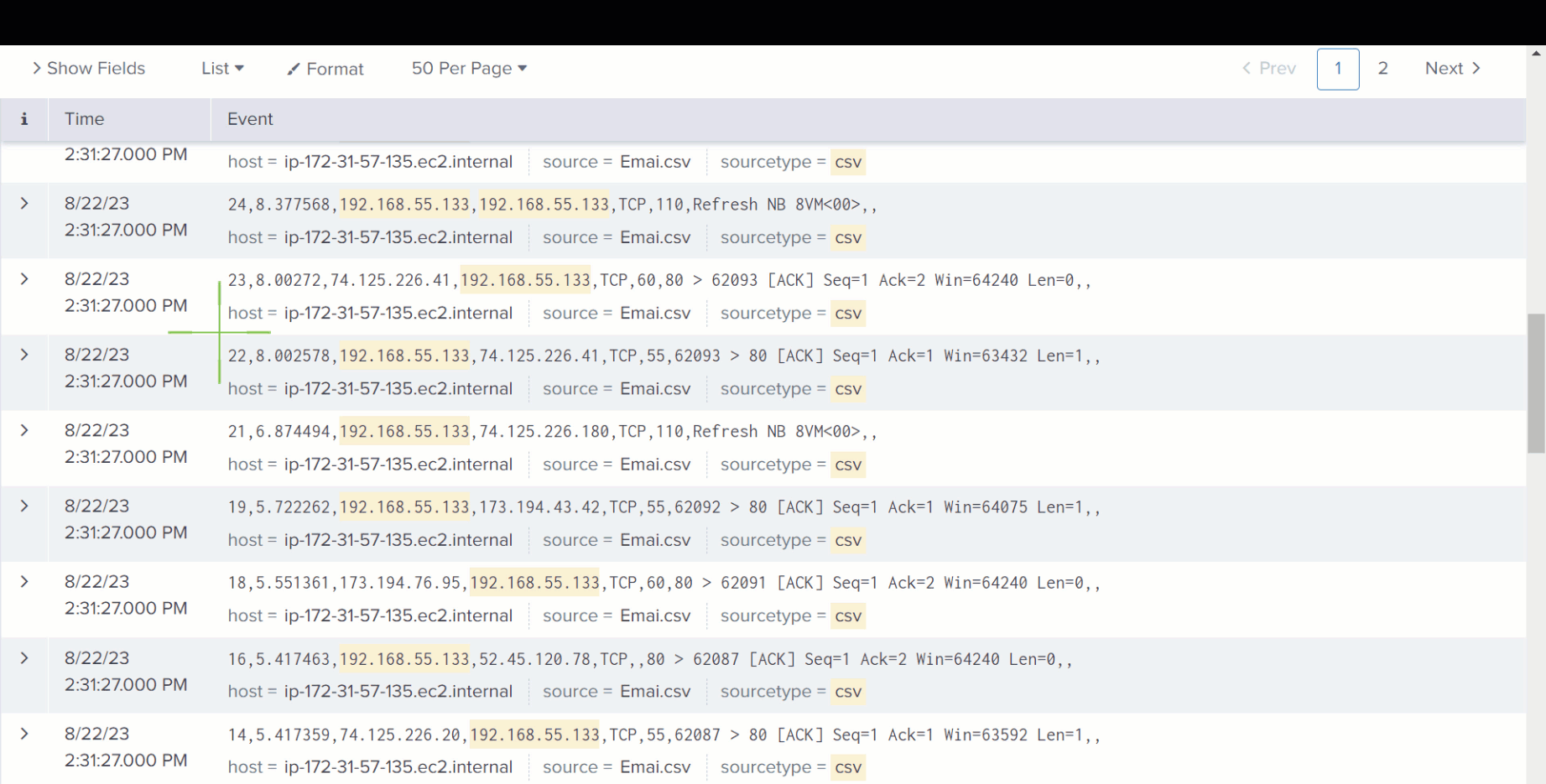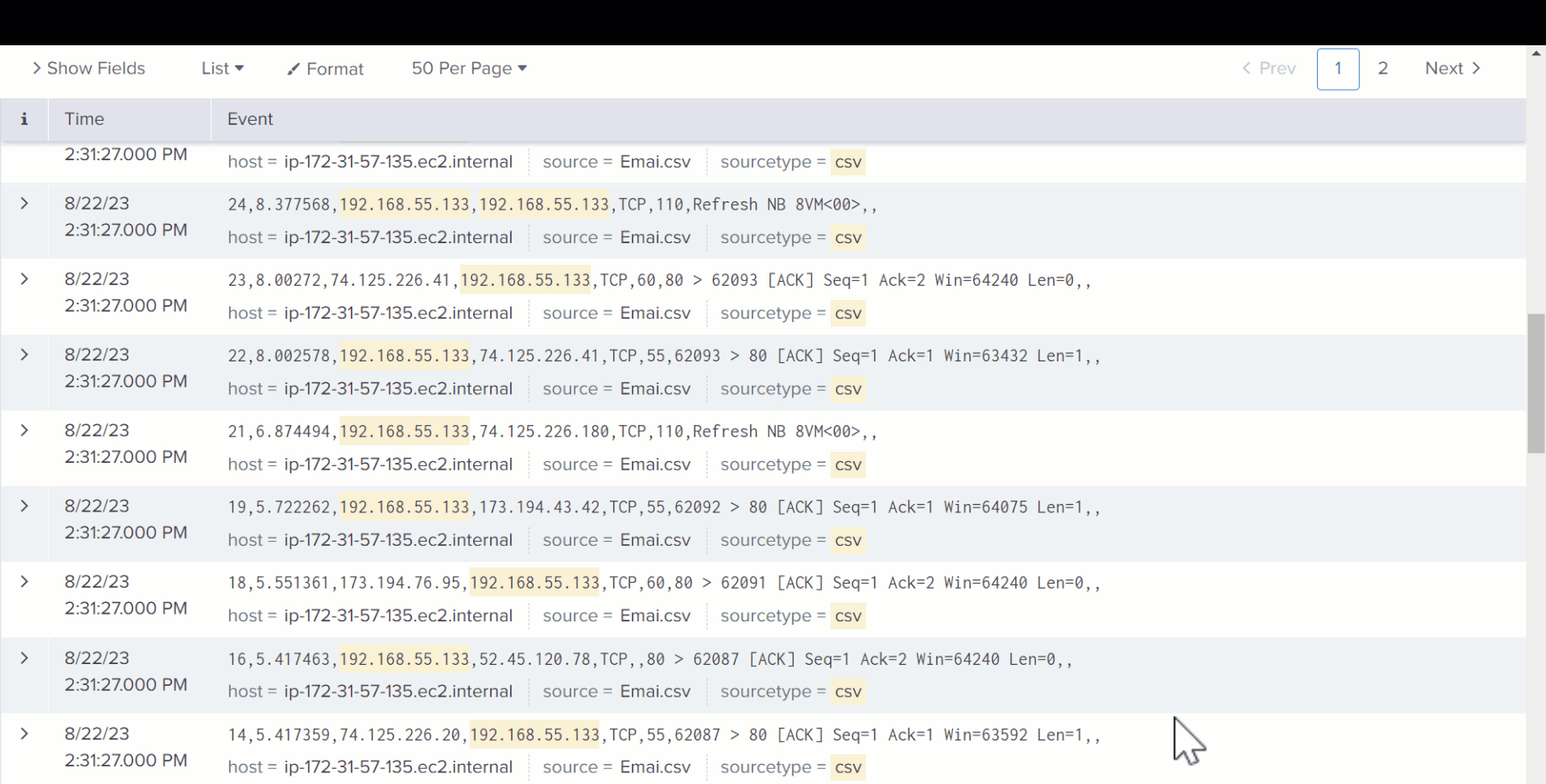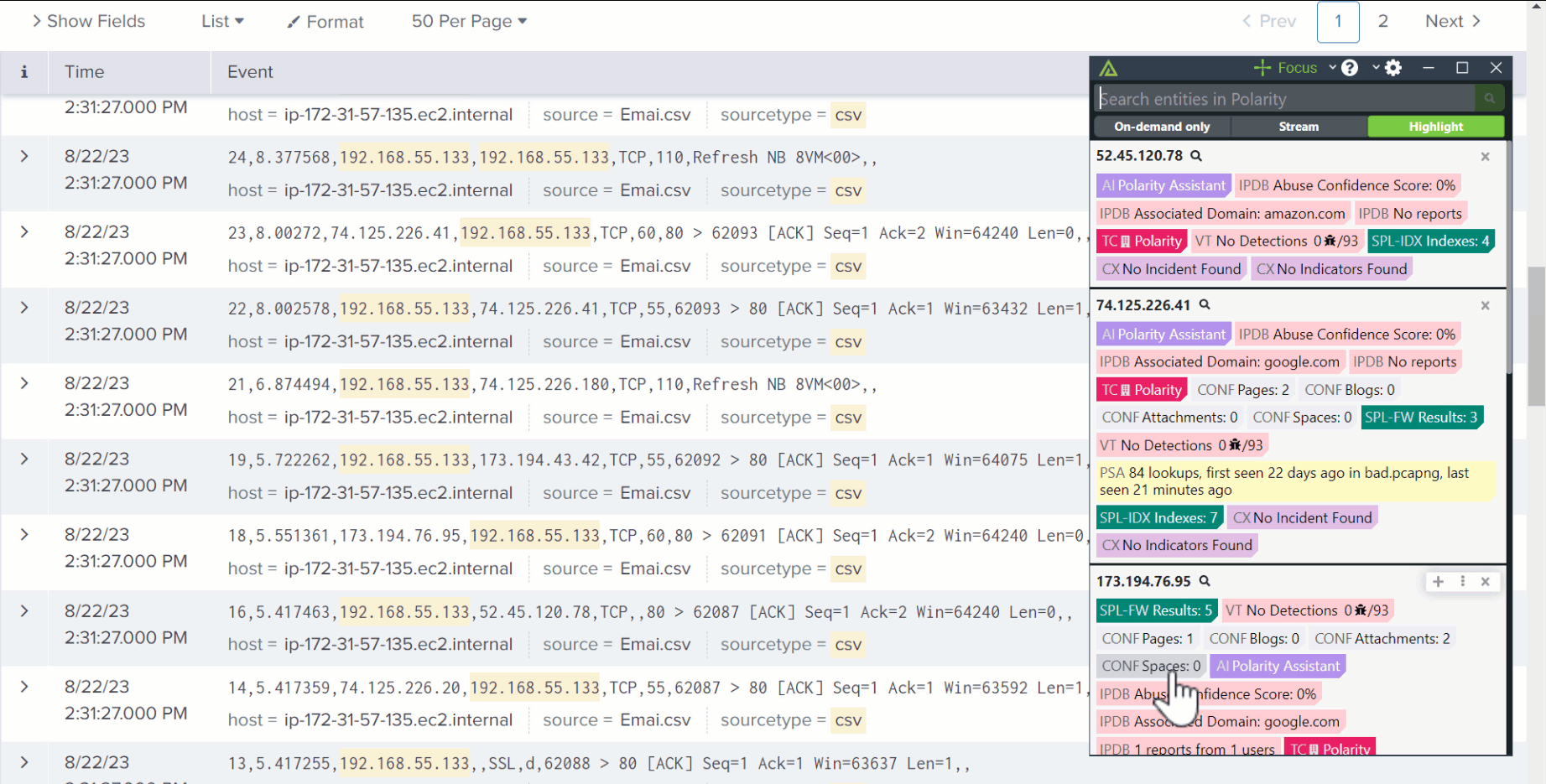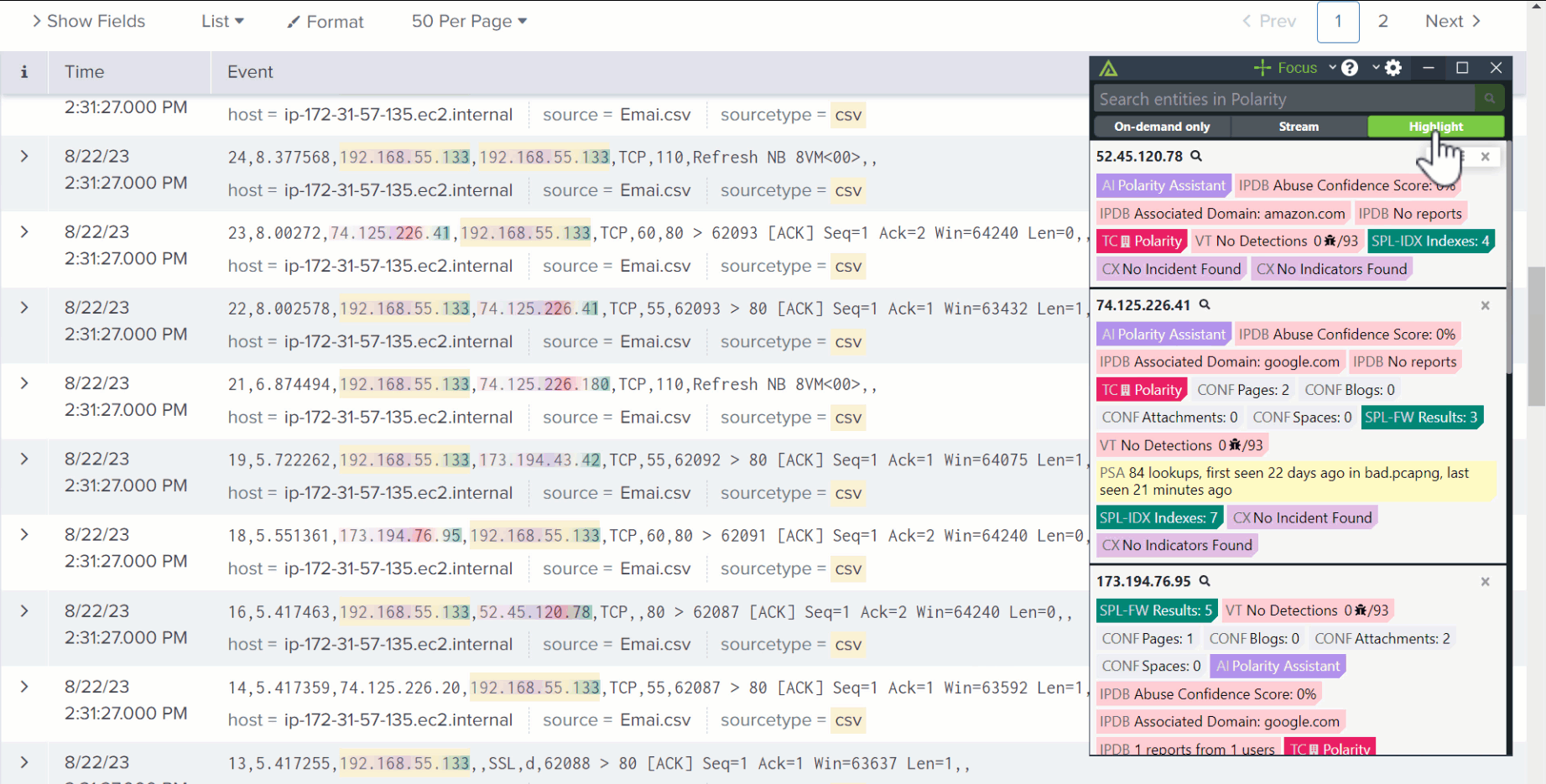
Search works like magic across 150+ toolsTI Ops, VirusTotal, Splunk, Shodan, and more.
Results appear directly over the alert you’re working on.
Analysts don’t need to centralize, normalize, or ingest data into another platform. Just highlight, and go.

300% faster case closure the first month deployed

“It took a 2–5 minute task and turned it into a 2-second task“

“We get more utilization out of our threat intel.”

“Our incident response time from soup-to-nuts went from 7 hours to 37 minutes.“

Enhance your security operations with the Polarity Enterprise. Discover our solution for federated search, real-time contextual intelligence, and seamless integrations.

Discover how Wyndham's security teams enhanced their threat detection and response with ThreatConnect TI Ops and Polarity, streamlining operations and improving efficiency.

Streamline threat intel workflows and provide real-time contextual information for SecOps and CTI teams.
To surface curated threat intelligence instantly in any workflow
To show business risk and impact context during alert triage and response
By capturing new intel and feedback in real time

Trusted By Leading Companies
Polarity is a force-multiplier for our security team whether its threat hunting or another discipline. In Highlight or On-demand mode we have confidence that all of our most valuable information is
delivered, cross-referenced against multiple sources, and is acted upon at the right time.
Polarity enabled our incident response team to quickly draw on historic intelligence which furthered their ability to respond effectively to observed events
Our investment in Polarity led to an annual ROI of nearly 200% based on just its initial use cases. Since purchase, we continue to find ways to use Polarity to increase the speed and thoroughness of the team.