CrowdStrike Falcon Intelligence Engine
The ThreatConnect integration with CrowdStrike Falcon Intelligence allows ThreatConnect customers to import information Reports, Indicators, and Actors, along with all of their context from the CrowdStrike Falcon Intelligence feed into ThreatConnect. There is both a Playbook app and Job app for this integration.
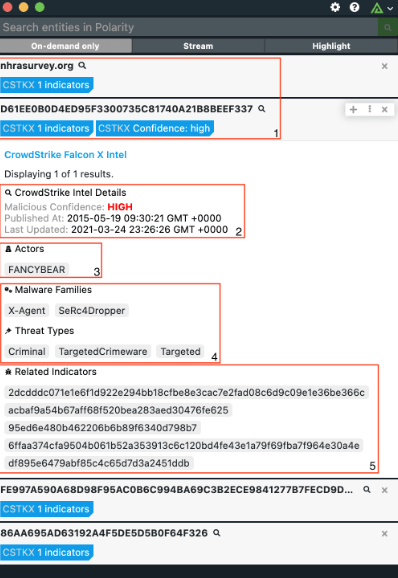
The integration supports address, email address, file, host, URL, email subject, mutex and registry key indicator types. Indicators are associated with Reports and Adversaries in ThreatConnect. Reports are also associated with Adversaries in ThreatConnect.
ThreatConnect can also take tag indicators from CrowdStrike with the relevant Mitre ATT&CK tactics & techniques in ThreatConnect. Not only does this make it easy to operationalize CrowdStrike Falcon Intel indicators based on specific tactics & techniques, but it opens up a whole new web of relationships across intel feeds for research and analysis.
This app interacts with CrowdStrike Falcon Intelligence to retrieve intelligence related to a submitted indicator. Submitting an indicator, such as an address, URL, host, etc., finds the Indicator ID and enrichment data including indicators, type, labels, and relations.
The following actions are available within the Playbook App:
- Enrich Indicator - Retrieve the Indicator ID and enrichment data including relations for one Indicator. Based on the indicator type and an exact match to a unique value.
- Query Indicator - Retrieve data for possibly multiple Indicators based on fuzzy search.
These apps can be found in the ThreatConnect App Catalog under the names: CrowdStrike Falcon Intelligence (Playbook), and Crowdstrike Falcon Intelligence Engine (API Service)
Keep Reading


 Polarity
Polarity