What Is a Threat Intelligence Platform?
Threat intelligence platforms (TIP) and tools are software solutions designed to facilitate the collection, analysis, and management of threat intelligence data. These platforms offer a centralized and organized environment for analysts to collect, gather, process, and analyze threat intelligence effectively.
To enhance its efficacy, threat intelligence tools often integrate with tools to detect and/or prevent threats, like SIEM, XDR, endpoint, and network security solutions, to help analysts prioritize alerts and determine urgency. Moreover, these tools support basic triage and investigation processes for alerts generated by threat detection, prevention, and response tools. Finally, threat intelligence platforms foster information sharing primarily through the exchange of indicators with other teams and external parties.
Key Capabilities and Features of a Threat Intelligence Platform
While threats evolve and occur spontaneously, the process for finding and analyzing the data is virtually the same. There are six primary features and capabilities to look for in a TIP.
This includes:
- Aggregation: Collecting threat intelligence data from multiple open-source, commercial, and proprietary sources.
- Threat analysis: Using the indicator of compromise (IOC) correlation to match collected IPs, hashes, and domains with internal security logs. It uses Machine Learning and AI-driven analysis to identify patterns and predict threats.
- Enrichment: Enhancing raw intel with additional context and metadata. Perform threat scoring by assigning risk levels to threats by cross-referencing known malicious entities with global threat repositories.
- Automation: Triggering predefined actions such as blocking IPs and notifying security teams of high-risk threats.
- Threat Analytics: Validating and analyzing collected intel to identify trends and patterns.
- Intel Sharing: Sharing intel via machine-readable data feeds for consumption by downstream security technologies and sharing threat intelligence with trusted partners or industry peers.
- Dashboards: Displaying charts and tables related to collected intelligence to visually convey information, including attack path visualization.
Cyber threat intelligence analysts, SOC analysts, and incident responders can use and take advantage of the features a TIP provides.
How a Threat Intelligence Platform Works
A threat intelligence platform automatically collects and analyzes external threat data to help organizations improve their security landscape. The process involves several stages that are all crucial for developing defenses against threats.
Here’s how a threat intelligence platform works:
- Data collection: TIPs gather raw data from various sources, including open-source intelligence (OSINT), security vendors, communities, and national vulnerability databases. Internal sources, from server logs to past incident reports, are also used to collect data.
- Data normalization: The collected data is normalized to ensure consistency in format and structure. Normalization makes analysis and correlation easier across different data sources.
- Data enrichment: A threat intelligence platform enriches the data by adding context to transform raw data into meaningful insights. This stage helps security teams understand the relevance and severity of threats.
- Analysis: The Platform analyzes the data to identify patterns, trends, and relationships between different threats. It helps analysts understand the context and implications of the threat and how it specifically applies to the organization.
- Integration: These platforms can often integrate with other security tools, such as Security Information and Event Management (SIEM) or endpoint, to automate responses and enhance overall security operations.
- Continuous improvement: Since threats are constantly evolving, threat intelligence requires continuous improvement. Through feedback from past incidences, these platforms allow organizations to refine their security processes and enhance defense mechanisms.
Who Uses a Threat Intelligence Platform?
A threat intelligence platform is used by various teams within an organization. With its intel-sharing features, it’s easier for both technical and non-technical shareholders to access threat information.
Some of the organization roles that use the Platform include:
- Security operations centers (SOC): SOC teams are responsible for monitoring and analyzing an organization’s security posture on an ongoing basis. They use threat intelligence platforms to detect, respond to, and mitigate security incidents by enriching alerts and linking them to incidents.
- Security and IT analysts: Security and IT analysts leverage threat intelligence platforms to improve detection and prevention capabilities. The Platform allows them to implement proactive measures to strengthen security controls and respond effectively to incidents.
- Computer security incident response teams (CSIRT): A CSIRT reviews and responds to security incidents within the organization. They rely on threat intelligence platforms to speed up the process of gathering contextual information about threats, including motives, attributes and tactics, techniques, and procedures (TTPs), as well as root cause analysis. This enables the team to investigate incidents thoroughly and develop effective response strategies.
- Intel analysts: Intel analysts focus on uncovering and tracking security threats to the organization through advanced analysis. They utilize threat intelligence platforms for alert triage and incident response, aggregate structured and unstructured data reports, and direct vulnerability patch prioritization.
- Executive management: Management and executive teams use threat intelligence platforms to better understand the organization’s security landscape and threat level. This information helps them make strategic decisions and allocate resources effectively, as well as develop a security roadmap.
- Cyber threat hunters: Leveraging TIP data, cyber threat hunters proactively search for undetected threats within an organization’s network.
- Risk management and compliance teams: These teams ensure compliance with cybersecurity regulations such as GDPR, NIST, and ISO 27001.
Benefits of a Threat Intel Platform
Threat intelligence platforms are beneficial for companies in order to stay on top of the latest cyber security intelligence. Threat intel is crucial to mitigating cyber threats to a company. Integrating a threat intelligence platform into security operations and cyber risk management offers several benefits, including:
- Early threat detection: Real-time insights on threat actors help security teams detect threats early, allowing them to take action to prevent and minimize the impact of attacks.
- Easily share information: TIPs make sharing information and threat findings easy between internal stakeholders and external partners.
- Industry-specific insights: The platform provides security teams with timely insights into cyber threats affecting their industry.
- Reduce threat impact: TIPs can automate responses and facilitate early threat detection, which helps organizations address the threat before it has a significant impact on the infrastructure.
- Informed decision-making: The platform provides valuable information that aids organizations in making informed decisions about security strategies.
- Faster incident response: A TIP automates threat analysis and prioritization to reduce alert fatigue.
- Enhanced threat visibility: Threat intelligence platforms offer detailed intelligence on attacker tactics, techniques, and procedures (TTPs) using frameworks like MITRE ATT&CK.
- Proactive threat hunting: The platform enables practice searches for hidden threats within networks.
- Automation: TIPs reduce manual effort by automating threat ingestion, analysis, and response.
- Strengthen compliance and risk management: Threat intelligence platforms meet regulatory compliance requirements like GDPR, NIST, and OCI DSS.
- Reduces financial and reputational damage: The platform reduces costs associated with incident response, legal fees, and regulatory fines by proactively identifying, quickly responding, and eliminating threats.
Types of Threat Intelligence
Cyber threat intelligence comes in various types that cater to different security needs. Organizations categorize threat intelligence to tailor their strategies and address specific threats effectively. The main types include:
Strategic Threat Intelligence
Strategic threat intelligence focuses on the long-term implications of threats and the overall threat landscape. It involves analyzing broader trends and emerging threats that could impact business or national security.
This type of intelligence is typically used by senior management and decision-makers to inform risk management strategies, resource allocation, and policy development.
Tactical Threat Intelligence
Tactical threat intelligence helps detect threats that organizations face by analyzing information about specific actor TTPs and IOCs. SOC teams and incident reporters often use it to enhance their defenses and improve incident response.
Operational Threat Intelligence
Operational threat intelligence provides insights into ongoing and imminent threats, including the motivations and capabilities of threat actors. It helps organizations understand the TTPs used by malicious actors and allows them to anticipate potential attacks. It can include information about threat actor groups, their targets, and their historical attack patterns.
Technical Threat Intelligence
Technical threat intelligence is concerned with technical details, including IOCs, IP addresses, and malware signatures. It’s instrumental for IT and security teams in building up defenses and responses to technical threats. It can be used in various applications, from malware behavior analysis to updating signatures for prevention systems.
ThreatConnect’s Threat Intelligence Platform is the Leading TIP in the Industry
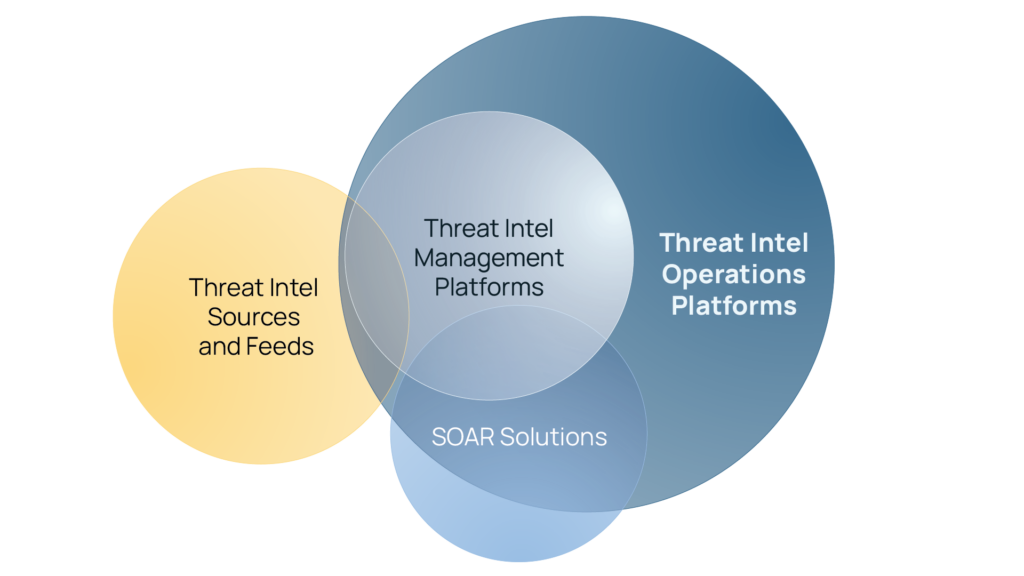
Organizations beginning to mature their cyber threat intelligence programs need a threat intelligence platform that enables them to leverage and disseminate their threat intel. Depending on the specific needs of the threat intel team, and broader cybersecurity and operations team, there are different available solution paths:
- Threat Intel service providers and threat feeds may offer a platform with some operational capabilities to leverage their proprietary intel.
- Threat Intelligence Platforms (TIPs) focus primarily on the aggregation, management, and analysis of intel.
- Threat Intelligence Operations platforms are a modern solution that goes beyond TIPs enabling the operationalization of threat intel analyst work and their outputs.
There is a wide variation between these platforms. One thing is common, they can help manage threat intelligence, but most struggle to operationalize it.
How Our TIP Works
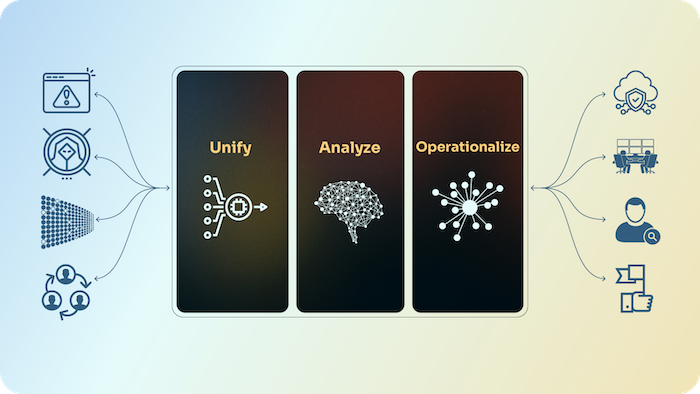
A Threat Intelligence Operations (TI Ops) Platform is an evolution of TIPs that contains modern features, like AI and automation, for threat intelligence work. A TI Ops Platform goes beyond helping analysts manage and produce threat intelligence; it enables threat intelligence to be operationalized for both intel producers and consumers/customers.
ThreatConnect’s TI Ops platform has several features to help cybersecurity teams proactively maintain the security and resilience of their company’s data and assets.
Key platform features include:
- Unified Threat Library: Serves as a comprehensive source of threat intelligence that is adaptable to your needs and capable of handling vast amounts of data. It standardizes and streamlines threat intel, making it ready for use by Threat Intel and SecOps teams.
- CAL™: This innovative capability uses Generative AI, natural language processing (NLP), and machine learning (ML) to deliver advanced analytics and global intelligence.
- Built-in Low-Code Automation: Low-code automation helps analysts save valuable time and focus on more critical operational threat intelligence activities by enabling the rapid construction and automation of tasks, processes, and playbooks.
- Visualize Threat Behaviors: ATT&CK Visualizer streamlines the process of mapping threat actor tactics, techniques, and procedures (TTPs) directly against threat intel and organizational defenses.
- Intelligence Requirements: The platform’s Intelligence Requirements capability enables customers to define, activate, and track their requirements, improving threat intelligence operations to be more efficient and actionable.
- Built-in Reporting: Sharing threat intel with security operations and cyber risk leaders is vital for timely, data-driven decisions. Reporting built directly into the platform enables analysts to easily create, share, and manage actionable reports.
Related Resources:
To understand the different types of Threat Intelligence Platforms, check out our Buyer’s Guide for Threat Intelligence Operations.
To decide which TIP is right for your organization, check out Choosing the Right Threat Intelligence Platform.
There are 8 crucial questions to ask when evaluating a Threat Intel Platform to make it the correct fit. Check them out – 8 Questions to Ask a Threat Intelligence Platform Vendor.
To learn more about ThreatConnect’s TI Ops Platform, visit our Threat Intelligence Platform page and take the interactive tour!
Dive deeper into ThreatConnect’s TI Ops Platform capabilities with these resources:
