Posted
Cyber threat actors are using more sophisticated tools, techniques, and procedures that are outpacing traditional security solutions. As a result, things such as intrusion detection systems, anti-virus programs, and conventional incident response methodologies by themselves are no longer sufficient to close the widening gap between security and the current threat landscape.
Analysts are over-worked and over-burdened by increasing volumes of threat data that come in different formats and different levels of quality. In addition, the relevance of threat data is often questionable, adding more work for the analysts to prioritize threats that actually matter to the organization.
It’s challenging to work with so much information, combining it and comparing it with internal data, performing quality control, and preparing it for dissemination and operationalization. In addition, collection, enrichment, and analysis of threat data is a time-sensitive operation that is all too often manual.
Let’s change that.
Where Do You Start?
This is where a Threat Intelligence Platform (TIP) comes in. The end goal of building a threat library is to forge a record system of the threats relevant to your organization and support better, faster decision-making and operations.
It’s essential to have a holistic view of your threat landscape. A TIP enables you to normalize intelligence collection and identify, detect, and respond to specific types of threats that are most relevant to your organization. Adopting an intel-driven operations platform benefits your Security Operations Team (SecOps) and your Cyber Threat Intelligence (CTI) Team.
The SecOps team can quickly gather threat data and create a process to automatically add any found threat intel in one central, secure threat library. They have a trusted intelligence repository to reference for additional context when needed.
For the threat intelligence team, building a threat library in one centralized platform allows them to curate and develop a single source of truth for aggregating and normalizing threat intelligence. They can understand threat data at a deeper level than they would otherwise from the originating intelligence source by using analytics, crowdsourced data, and machine learning.
How Can ThreatConnect Help?
ThreatConnect’s TIP significantly reduces the time it takes to get high-quality intelligence into business operations. Through our industry-leading TIP, this use case is easily solved by creating a historical library of threats and intelligence to help you better identify, detect, & respond to threats that are targeting your organization.
Taking it a step further, gain a deeper understanding and insights with ThreatAssess and our Collective Analytics Layer (CAL). CAL provides an anonymous way to learn how many times potential threats were identified across thousands of deployed ThreatConnect instances around the world. This offers immediate insight into how widespread and relevant a threat is, and provides global context. ThreatAssess then leverages a single actionable score to capture and convey the priority of the threat and offers a decision on what to do next. As you build your threat library, you can fine-tune your ThreatAssess score so that it’s accurate and relevant to your organization and industry.
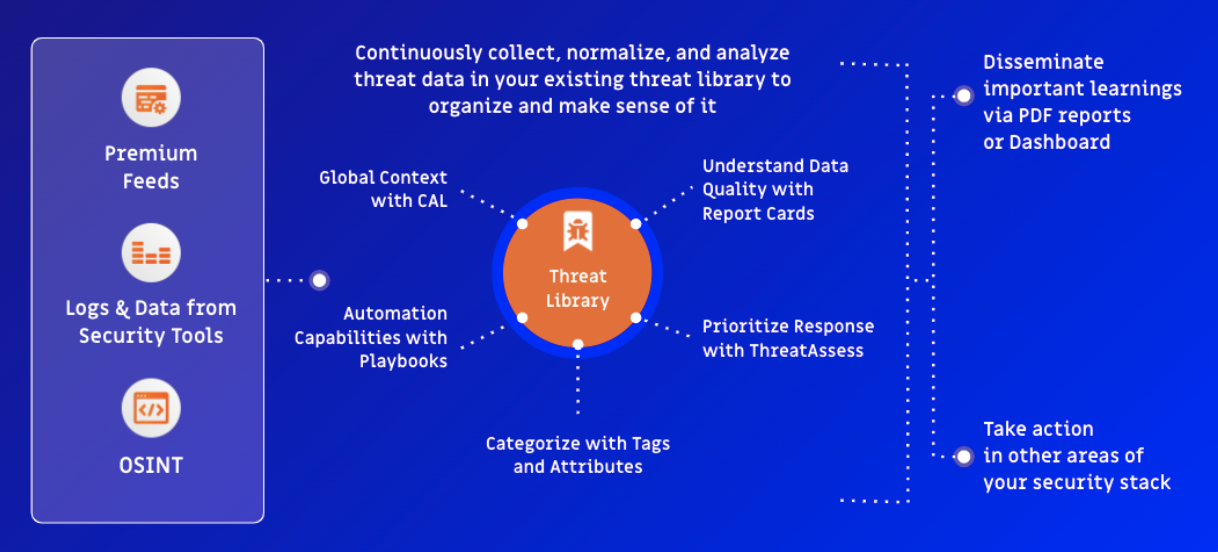
During their investigations, your SOC team can uncover new intelligence that can continue growing your threat library. Using a well-suited Threat Intelligence Platform, your SOC can reduce the time it takes to get high confidence intelligence to the operations teams for faster decision-making.
Threat intelligence can guide security operations toward better decisions, and security operations serve as the source of valuable new intelligence. It continues in a never-ending security feedback loop. Organizations need to move faster, collaborate more intently, and make better use of existing tools to better protect their environment from dangerous threat actors.

