Posted
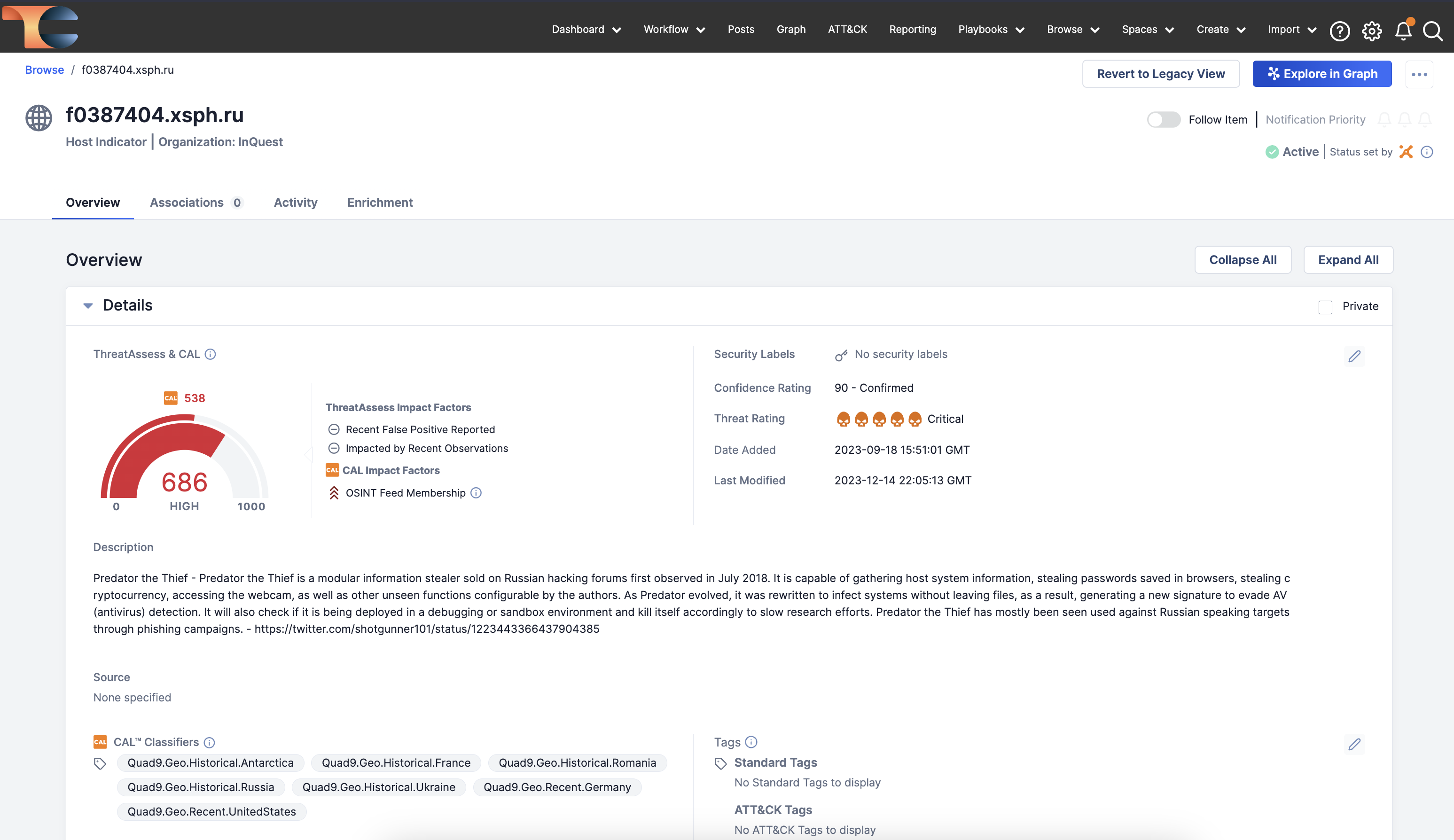
ThreatConnect and InQuest are excited to announce the availability of a new integration between InQuest InSights Threat Intelligence and ThreatConnect’s TI Ops Platform. InQuest’s high-fidelity threat intel is derived from their at-scale file analysis of malware and enriched with a variety of open-source and proprietary reputation sources. The integration with ThreatConnect’s TI Ops Platform makes InQuest’s indicators of compromise (IOCs) available for use by CTI analysts, and a wide variety of SIEM and security analytic tools, and endpoint, network, and cloud security solutions to improve their detection capabilities while reducing false positives.
InQuest’s Unique Capability and Visibility
InQuest InSights provides visibility into indicators extracted from file-based analysis across their customer base, partnerships, and their own analysis platform. This gives security teams a unique perspective based on real attacks seen in the wild, typically from threat actor groups that are more advanced in evasion and who often target highly sensitive, strategic sectors.
Hard numbers back the timeliness and uniqueness. InQuest’s IOCs are 92.9% unique from existing threat intel data shared with Quad9.net, and average 383 days before public dissemination or are discussed as a “new threat” by other major commercial TI data providers.
Internal Sources Powering InQuest InSights Threat Intelligence
InQuest uses several internal sources to create its threat intelligence feeds:
- InQuest InSights C2: A focused dataset that brings InQuest’s most novel analysis on malware command and control (C2) infrastructure. This feed is primarily composed of the output of InQuest’s threat intelligence analysts’ work product as well as proprietary sources.
- InQuest InSights TI: A threat feed composed of indicators relating to adversary infrastructure used for a variety of abuse, including malware staging, phishing, VPN and proxy endpoints, and attack origination, including mail delivery, scanning and exploitation, and network penetration. This feed includes data from InQuest intelligence analysis and our partner networks.
- InQuest Labs RepDB: A collection of reputation data leveraged by the InQuest TI team to validate and contextualize InQuest Threat Intelligence. It consists of two dozen of the most trusted reputation datasets available privately and commercially as well as output of InQuest’s state-of-the-art Deep File Inspection® (DFI) technology.
- InQuest Labs IOCDB: A rich OSINT-focused feed that contains hundreds of sources pulled from the Internet filtered and contextualized to provide high-quality indicators and data in a timely manner.
- InQuest Labs DFIDB: A feed composed of indicators extracted from publicly shared files as well as files uploaded to labs.inquest.net for analysis by InQuest DFI file analysis. This feed contains quality indicators good for hunting that have not been validated by an analyst at InQuest.
The combination of reputation, open source intelligence, and unique/novel data produced by InQuest’s file analysis and infrastructure analysis capabilities delivers cutting-edge insight and context into the threat landscape.
InQuest InSights in ThreatConnect
InQuest’s InSights in the ThreatConnect TI Ops Platform provides CTI and Security Operations teams additional coverage across their Threat Library and enables that intelligence to be operationalized to deliver impact and value across the range of integrated threat detection and prevention solutions. InQuest’s Threat Intel can be used in a range of use cases including Threat Detection and Prevention, Incident Response, Threat Hunting, and Reporting Tactical and Strategic Intelligence.
Take the next step
The ThreatConnect TI Ops Platform makes it easy to realize the value of InQuest’s Threat Intelligence with these and many other use cases. If you’d like to learn more, check out our marketplace, or reach out to our team to learn more or see a demo!
