Posted
Building a threat intelligence-led security program with security orchestration, automation, and response (SOAR) capabilities helps to advance your program and gives your company or agency a fighting chance to defeat these advanced and evolving threats.
Businesses and organizations with less mature cybersecurity programs tend to be in a constant state of reacting to threats, vulnerabilities, and incidents. That’s a recipe for disaster in a world of highly-sophisticated criminal and state-sponsored adversaries, known as Advanced Persistent Threats (APTs).
Here’s a TIP on Threat Intelligence Platforms
Organizations that are just getting started with threat intelligence rarely have made a large investment in intelligence processes. In such organizations, there is likely no one person or group charged with the management of threat intelligence automation.
It is tempting to turn on product-integrated feeds, and this will suffice for that product if the intelligence is properly refined and vetted by the provider. But this refinement rarely occurs within intelligence feeds and, as such, problems typically arise when hooking threat intelligence directly into products. The integration can cause as many problems as it solves, resulting in high false-positive rates or blocks if the intelligence feed is “raw” or of low quality. The security team can become overwhelmed with data in multiple product and organizational silos, like spreadsheets buried in a shared drive’s directory structure.
If you want to build a threat intelligence-led security program to stay ahead of advanced adversaries requires a Threat Intelligence Platform (TIP) to support analysis and deliver deep insight and context to help identify, analyze, and take action against the threats that matter most. You may be thinking – “if I don’t have a mature threat intel program, how could I possibly be ready for a TIP?” The answer is simple – a TIP actually helps to overcome resource gaps and advance your intel program. It acts as a powerful workbench to drive out complexity, streamline processes and amplify human capability.
A TIP should help “sort the wheat from the chaff” from the various feeds through the use of automated analytics that lower the number of potential false positives from the various sources it is processing when the data is deployed.
What should you look for in a world-class Threat Intelligence Platform? Your TIP should be capable of:
- Automating intelligence collection from any source
- Reducing false positives and freeing analysts to focus on legitimate alerts and threats
- Harnessing global, crowdsourced intelligence (ThreatConnect does this via our Collective Analytics Layer, or CAL)
- Enriching threat data with context
- Providing out-of-box templates for automation of processes with Playbooks
- Producing an at-a-glance view of priorities (including PIRs) with flexible Dashboards
- Integrating with SIEM, EDR, SAO, SIRP, SOAR, firewall and other tools
- Breaking down silos between teams and technologies
Organizations have different levels of maturity and capacity to leverage threat intelligence effectively. These factors are largely dependent on the organization’s perceived need and resulting investments in threat intelligence and related personnel and processes. The use cases for threat intelligence grow as an organization’s capability to leverage it grows. Regardless of your maturity level, if you’re looking to build a threat intelligence-led security program, you need a TIP.
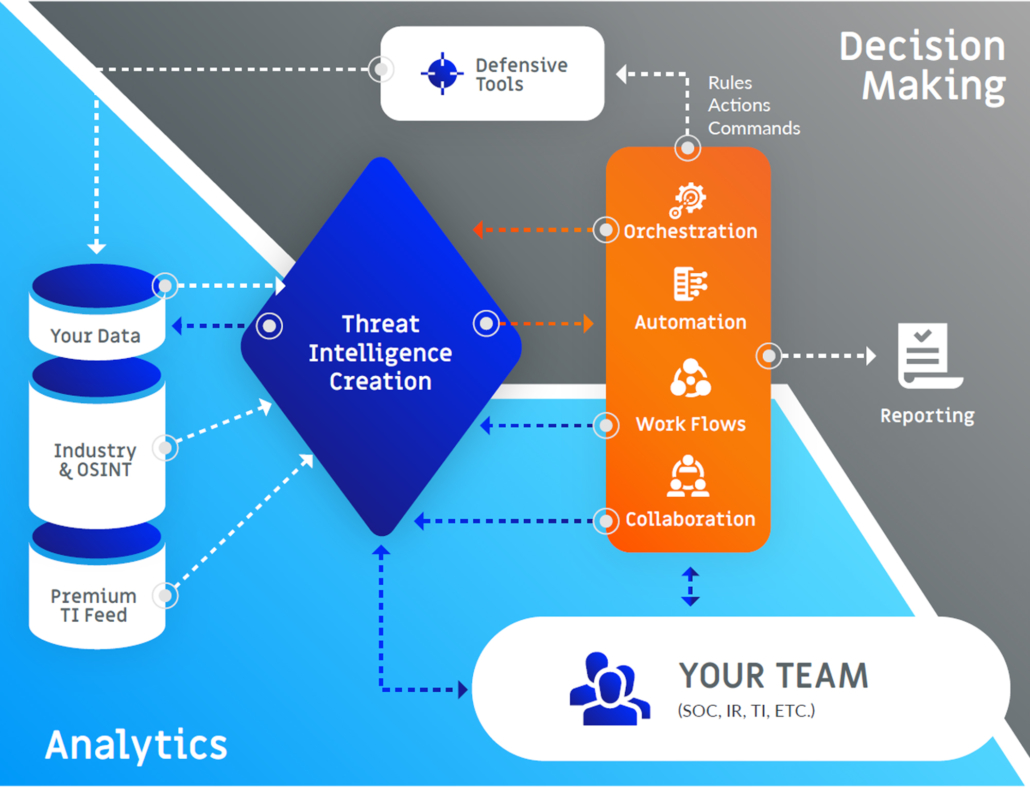
At the end of the day, a TIP should allow your security team to aggregate all available threat data – both internal and external, structured and unstructured – analyze it rapidly, automate action, and then produce tactical, operational, and strategic threat intelligence all in one place.
SOAR Over Roadblocks
Regardless of an organization’s threat intelligence maturity level, most have dozens, if not hundreds, of security tools in use at any given time. Each of these tools creates its own logs and contributes to an environment ripe for security alert overload and inconsistent triage.
This exponential increase of data and alerts means that quick decision-making and execution needs to find a way to scale. To counter this, many have turned to new solutions designed to automate and orchestrate some aspects of their cybersecurity operations – in real time – and bolster staff productivity through reducing workload. Where full automation is not possible or advisable, these same solutions are expected to present the relevant data and facts to enable responsible staff to make fast, informed decisions.
Security orchestration and automation integrates different technologies and allows you to conduct defensive actions: it increases your effectiveness in stopping, containing, and preventing attacks. Integration is important since your teams are likely to have little patience for point solutions that are difficult to implement or get value from.
What should you look for in a world-class SOAR Platform? Your SOAR should be capable of:
- Providing a central location to integrate security tools and processes
- Automating collection, mapping, enrichment, hunting and tracking of threats
- Operationalizing curated intelligence faster
- Increasing speed of holistic context on intelligence by connecting technologies
- Leveraging Playbooks to delegate and automate tasks and remove roadblocks
- Real-time collaboration across roles and teams
- Workflows and Case Management to improve efficiency
- Record, Analyze and interact with all information related to a case
- Expedite artifact collection from a variety of sources
- Reduce risk of missing critical steps
- Get instant updates with a team-based notification system
- Creating a continuous feedback loop across intelligence, operations and response teams
TIP & SOAR Together
Build a threat intelligence-led SOAR
When using intelligence and orchestration together, situational awareness and historical data determine when and how a task should be done. Intelligence allows the process to be adaptive to the changing environment. And, allows you to strategically plan for a better program.
While some organizations do not have a formally defined intelligence function on their team, the concept of using what you know about the threat-space to inform your operations exists in all organizations. Regardless of whether an explicitly named threat intelligence analyst employee is on staff, the relationship between intelligence and operations is fundamental and present in all security teams.
As threat intelligence drives your orchestrated actions, the result of those actions can be used to create or enhance existing threat intelligence. Thus, a feedback loop is created — threat intelligence drives orchestration, orchestration enhances threat intelligence.
Build a threat intelligence-led security program with security orchestration, automation, and response (SOAR)