Posted
Empower Your Security Controls Coverage with ATT&CK Visualizer
In today’s cybersecurity landscape, the faster you can identify and mitigate threats, the less damage they can cause. To gain the upper hand, security teams are turning to the MITRE ATT&CK framework – a comprehensive matrix of the tactics and techniques used by real-world threat actors.
The latest release of ATT&CK Visualizer tackles a critical challenge: understanding your organization’s security controls coverage against specific threats. Adversaries employ many tactics and techniques, making it hard for security teams to pinpoint vulnerabilities. To defend effectively, you need to know where you’re exposed.
Explore more features updates with our TI Ops 7.4 interactive demo
ATT&CK Visualizer, based on the MITRE ATT&CK framework, is a valuable resource for threat hunters, defenders, red teams, and anyone assessing risk. TI Ops 7.4 introduces the ability to assign security controls coverage to specific ATT&CK techniques and sub-techniques. This new feature lets you evaluate each tactic and technique adversaries use and determine how well you can defend against them. Once security controls coverage is assessed and captured in ATT&CK Visualizer, the security team can access this knowledge, filter and regularly update.
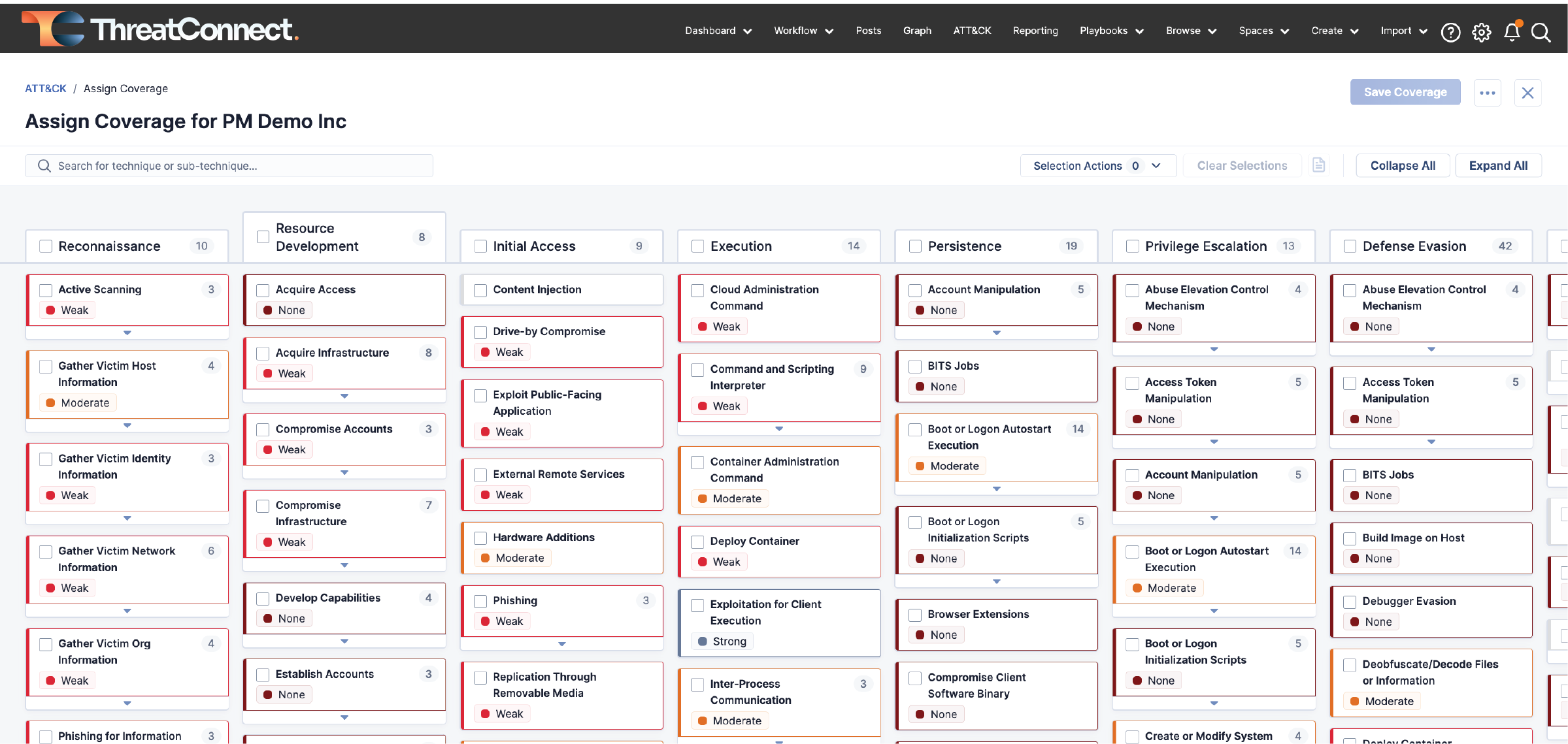
Other ATT&CK Visualizer updates include:
Identify Groups using Similar Techniques – New capabilities allow users to identify groups using similar techniques. This functionality aids in focused analysis, enabling security teams to spot groups employing comparable tactics quickly. This approach enhances the precision of threat assessment and response strategies.
Simplified Import of MITRE ATT&CK Navigator Json – TI Ops 7.4 allows for the seamless import of MITRE ATT&CK Navigator Json into the platform. Centralizing this information within the ThreatConnect platform streamlines investigative processes for security analysts, contributing to increased efficiency.
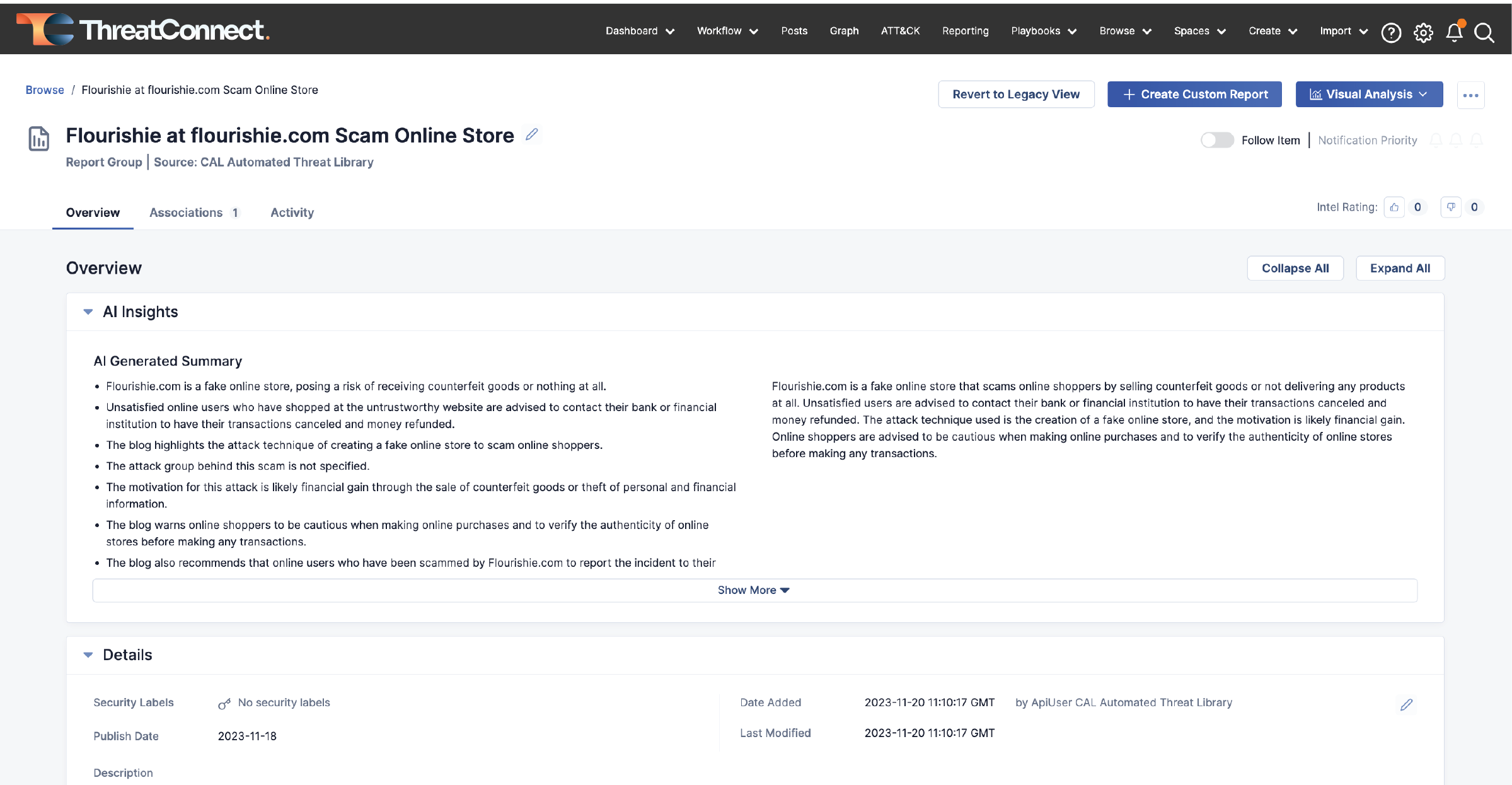
AI Insights: Elevating Report Understanding
Also new, CAL ATL users will see an AI Generated summary card prominently displayed at the top of the Report Group’s overview page. This summary will consist of brief, easy-to-read bullet points, providing users with a high-level understanding of the report’s contents. The goal is to empower users to efficiently decide whether a report warrants further attention or analysis, optimizing their workflow and ensuring a more focused and informed approach to threat intelligence.
Reporting Enhancements: Simplified Document Creation
This update aims to further streamline report creation, offering a platform for crafting visually appealing documents through a new what you see is what you get (WYSIWYG) user experience. With a focus on personalization, users can now ensure reports align with their unique style.
The updated Text Editor enables users to insert images directly into reports, utilize text highlighting for key points, ensure professional layouts with text alignment options, customize font colors, choose from an expanded font selection, and improve overall text formatting with support for headings and normal text. These additions provide users with more tools to create impactful and personalized reports.
Reporting will be upgraded further to support templates in TI Ops 7.5. Templates will allow users to create reports from a schema for repeated use.
Built-In Enrichment – RiskIQ: Simplifying Threat Analysis
Built-in Enrichment for RiskIQ helps users see and understand potential security threats more efficiently. Instead of dealing with complicated steps or checking many different websites, this solution makes it simpler. It brings RiskIQ directly into the process so users can quickly get a clear view of potential issues.
Intelligence Requirements: Delivering Tailored Solutions
This updated version of Intelligence Requirements is designed to help prioritize information and transform threat intelligence operations into a more efficient and practical function. With the new Match Drawer – users have the ability to see what keywords a result matched against and quickly understand why something matched, rather than just seeing that it did. This will enable users with a more contextual understanding of why a specific result appears in their intelligence requirement results list.
For more information on these new capabilities and how ThreatConnect can help your organization operationalize threat intelligence, please reach out to sales@threatconnect.com or request a demo.

