Posted
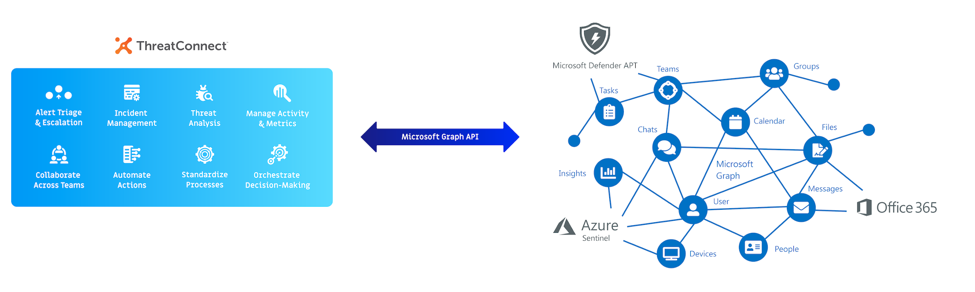
We’ve got big news! ThreatConnect now integrates with Microsoft Graph, allowing ThreatConnect customers to connect with nearly any piece of Microsoft technology. This integration acts as a communication bridge between the ThreatConnect Platform and the Microsoft portfolio.
The ThreatConnect Apps now available include:
- Microsoft Graph Mail Messages Playbook App
- Microsoft Graph Mail Attachments Playbook App
- Microsoft Graph Security Threat Indicators Playbook App
- Microsoft Graph Security Threat Indicators Job App
- Microsoft Graph Security Alerts Playbook App
- Microsoft Azure Active Directory Playbook App
- Microsoft Graph Teamwork (Teams) Playbook App
- Microsoft Graph Notifications App Service*
*App will be available for Dedicated Cloud deployments of ThreatConnect (on-premise not supported at this time)
Our integration with Microsoft Graph allows countless use cases to be fleshed out and discovered, but thanks to these Apps, the following use cases are immediately available:
Perform Office 365 Phishing Investigation
With two new Playbook Apps, you can automatically trigger a Playbook once you receive an email in a phishing mailbox in Office 365. The Playbook will then parse the email and any attachments and orchestrate an investigation of the email using a combination of ThreatConnect intelligence, ThreatConnect’s CAL™, malware analysis tools, and data enrichment sources. If the email is suspicious or requires further remediation, ThreatConnect can create a Case leveraging our new Workflow feature and assign it to an analyst for further investigation and remediation.
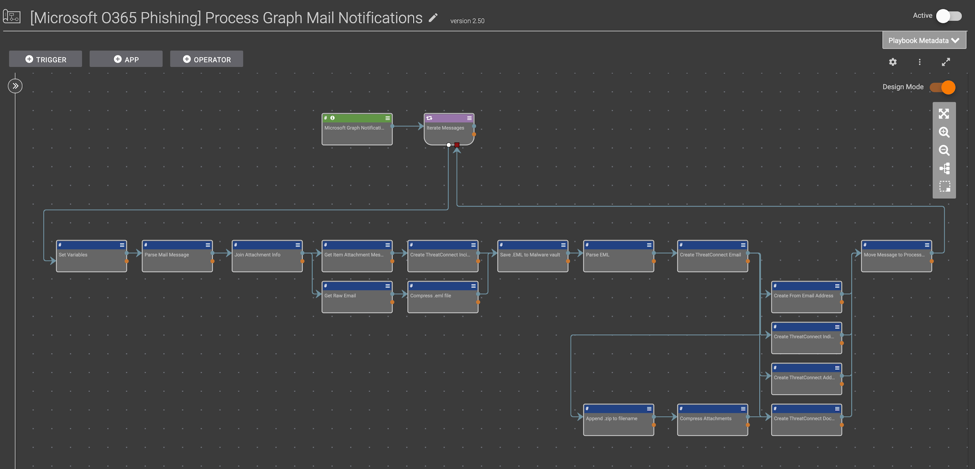
[Microsoft O365 Phishing] Process Graph Mail Notifications Playbook Template Available in App Catalog
Apps used:
- Microsoft Graph Mail Messages Playbook App
- Microsoft Graph Mail Attachments Playbook App
Deploy Indicators to Microsoft Defender ATP and Azure Sentinel
You can now easily send indicators to products like Microsoft Defender ATP (Advanced Threat Protection) and Azure Sentinel using the Microsoft Graph Security Threat Indicators Playbook App or Job App. The job app allows you to send thousands of indicators in bulk (vs. tactically with the Playbook app). ThreatConnect helps to increase accuracy and efficiency in your organization by ensuring that only high fidelity indicators are being sent to Microsoft Graph to be sent further along to products like Microsoft Defender ATP and Azure Sentinel. Once indicators have made it to these products, you can set up alerts and block actions for them. When alerts are generated based on intelligence from ThreatConnect, you’ll feel confident to make fast and informed decisions.
Apps used:
- Microsoft Graph Security Threat Indicators Playbook App
- Microsoft Graph Security Threat Indicators Job App
Triage Graph Security Alerts
With Microsoft Graph Security alerts, you can unify and streamline management of security issues across all of your integrated solutions. With ThreatConnect, you are now able to automatically trigger a Playbook based on a Graph Change Notification for Security Alerts. Keep in mind that security alerts can come from multiple Microsoft products, which include Azure Sentinel, Azure Security Center, Azure Active Directory Identity Protection, Cloud App Security, Azure Advanced Threat Protection, and Azure Information Protection. This Playbook will orchestrate decision making and either automatically resolve the alert or open a Case in Workflow for further investigation.
Apps used:
- Microsoft Graph Security Alerts Playbook App
Get Valuable ROI Metrics
Now, you can filter Microsoft Security Alert notifications on the intelligence housed in ThreatConnect. In other words, you can receive security alerts anytime there’s a match against ThreatConnect intelligence and then use that intelligence to report observations or false positives (two important ROI (return on investment) metrics used throughout ThreatConnect Dashboards). You can use these vital ROI metrics to make decisions on if you should escalate the alert to its own case in Workflow. You can even visualize your ROI by creating Dashboards that would show you how many observations and false positives you have across various Microsoft products. That snapshot view is essential for understanding the ROI you are getting back from these solutions working together.
Apps used:
- Microsoft Graph Security Alerts Playbook App
Get or Update Users Information
With this Playbook App, you can get Microsoft Azure Active Directory User account information including Groups and Applications the user has access to. This information can be used for making automated decisions about the next steps to take in the investigation as well as helping you to have all the information you need without having to collect it manually.
Apps used:
- Microsoft Azure Active Directory Playbook App
Create Microsoft Teams Channel as Part of Investigation
With this Playbook App, you can create a channel in Microsoft Teams as part of an investigation process and then post relevant updates to the channel as the investigation unfolds. You can also use it to request permission for action or notify a user that they need to take an action.
Apps used:
- Microsoft Graph Teamwork (Teams)
These are just a few of the use cases and Playbook templates that our users can leverage right off the bat with our integration with Microsoft Graph. As it gives us access to nearly any Microsoft product, we expect this list to grow over time as we develop additional Playbook Apps and Templates. We are excited to explore Microsoft Graph and the ways it can increase accuracy and efficiency for cybersecurity teams.