Posted
ThreatConnect’s 7.1 release delivers an even better ThreatConnect user experience. ThreatConnect 7.1 strengthens capabilities introduced in 7.0, including Enrichment and Reporting, providing more flexibility and customization while also refining the Platform for a more streamlined user experience so security teams can be more efficient and effective.
Built-in Enrichment v2
When investigating an indicator, knowledge is power. The more analysts know about an indicator, the faster they can assess its relevance and severity to the organization. In ThreatConnect 7.0, we introduced our first iteration of built-in Enrichment with VirusTotal, enabling teams to understand the maliciousness of an indicator and links and dependencies between indicators. In this latest release, we added built-in Enrichment with Shodan and expanded on our VirusTotal capabilities for even more efficient and effective investigations,
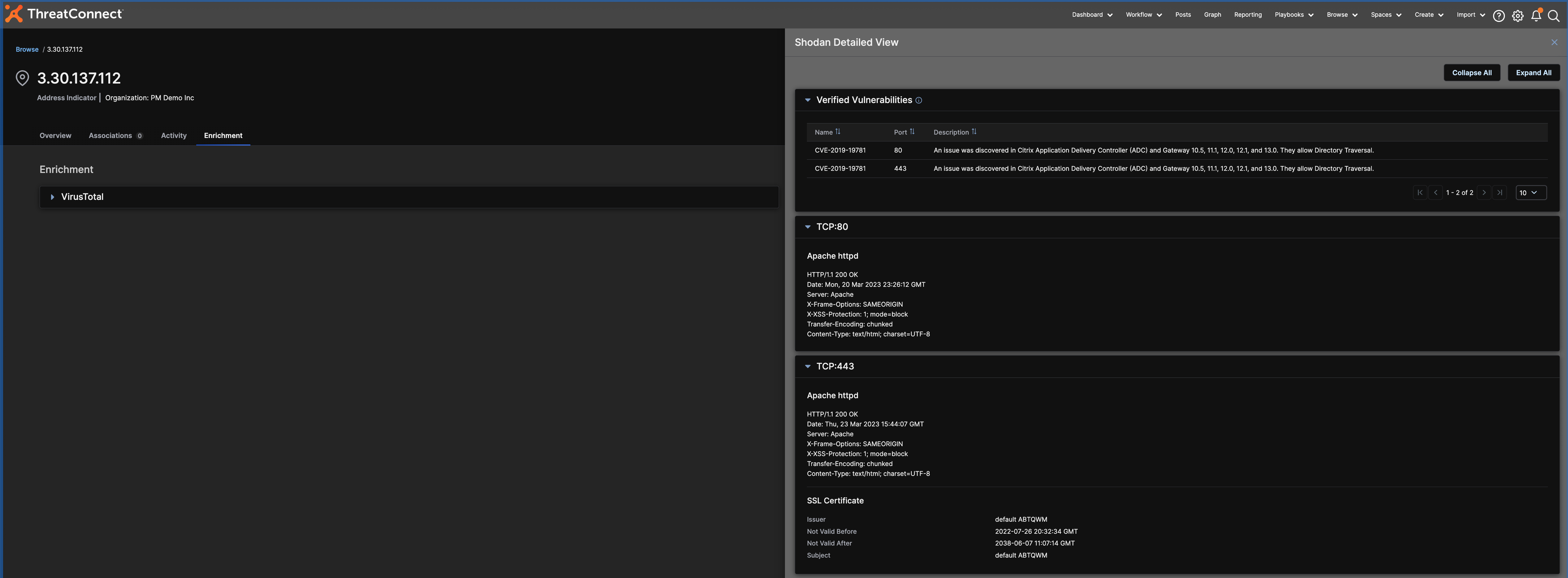
Built-in Enrichment with Shodan
Enrichment with Shodan adds context to IP addresses. The In-Platform Shodan Detail View includes details on Ports, Protocols, and Associated Certificates, as well as whether a vulnerability is verified or unverified. Details on Ports, Protocols, and Associated Certificates help identify potential risks in the form of misconfigurations, expired certificates, and weak cryptographic algorithms. Vulnerabilities verified by Shodan are easily prioritized by analysts, while unverified vulnerabilities need further investigation from them.
Analysts can scrutinize the contextual information from Shodan in the Detail View on the Platform and compare it to the enrichment data from VirusTotal on the same page to identify patterns. They can also view the data in Threat Graph, our visualization tool, to explore, pivot, and gain insight into connections between Indicators for both Shodan and VirusTotal Enrichment data.
Explore Enrichment with Shodan in our interactive demo
VirusTotal Enrichment Improvements
In ThreatConnect 7.1, we include more improvements to Enrichment with VirusTotal. We added VirusTotal enrichment data to Workflow Cases to the Artifacts section so security operations teams have all of the information they need in one place. We also added automatic Enrichment with VirusTotal via our v3 API and the ability to import VirusTotal relationship data to new or existing Groups for a deeper understanding of relationships between Indicators.
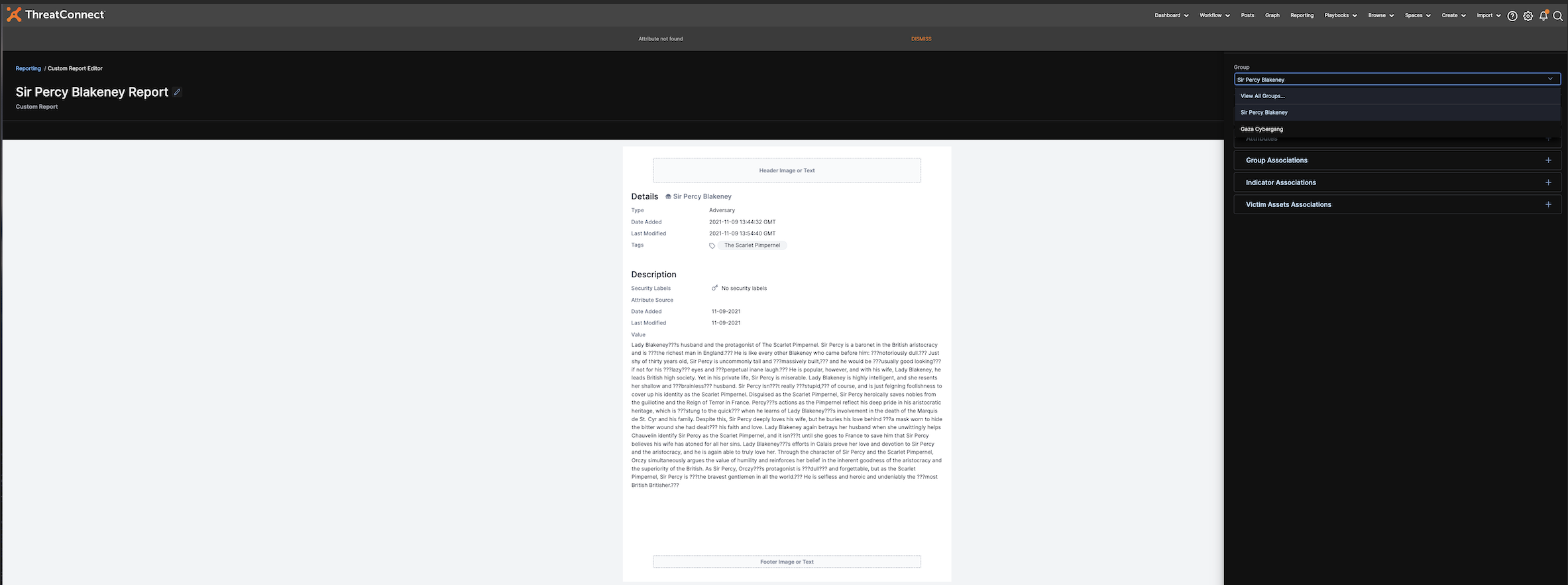
Native Reporting v2
The ability to quickly and easily disseminate information and enable leadership is key to a successful threat intelligence operations program, but it’s not about getting just any information in front of stakeholders. It’s about getting the right information in front of the right stakeholders at the right time. In our second iteration of Reporting, we provide even more flexibility for building reports so teams can be precise and effective with the information they share.
In ThreatConnect 7.0, users could build Reports from Groups. Now, users can also create Reports directly from Workflow Cases with the flexibility to create more customized reports that include data from multiple Groups and Cases. Multi Group and Case support enables users to create reports around topics like Threat Groups they observed in a week or cases they are working on to streamline their investigations and organize their data more efficiently.
For even more flexibility, users can create a generic report, regardless of whether the data is associated with a Group or Case. Using text blocks, users can easily and quickly add relevant information to a Report without creating a Case or Group first. Generic reporting gives users more control over the information they include in a report and speeds up dissemination.
User Experience Improvements
To deliver a more streamlined user experience on the ThreatConnect Platform, we are continuously elevating the right information so analysts can make fast and confident decisions. In ThreatConnect 7.1, users get more context with Pinned Association Attributes on the Overview page and CAL Impact Factors to understand the factors and their impact on a CAL score, a reputation score for the criticality of an Indicator. Additionally, users can automatically associate Indicators and Groups to a Group with ThreatConnect Query Language (TQL).
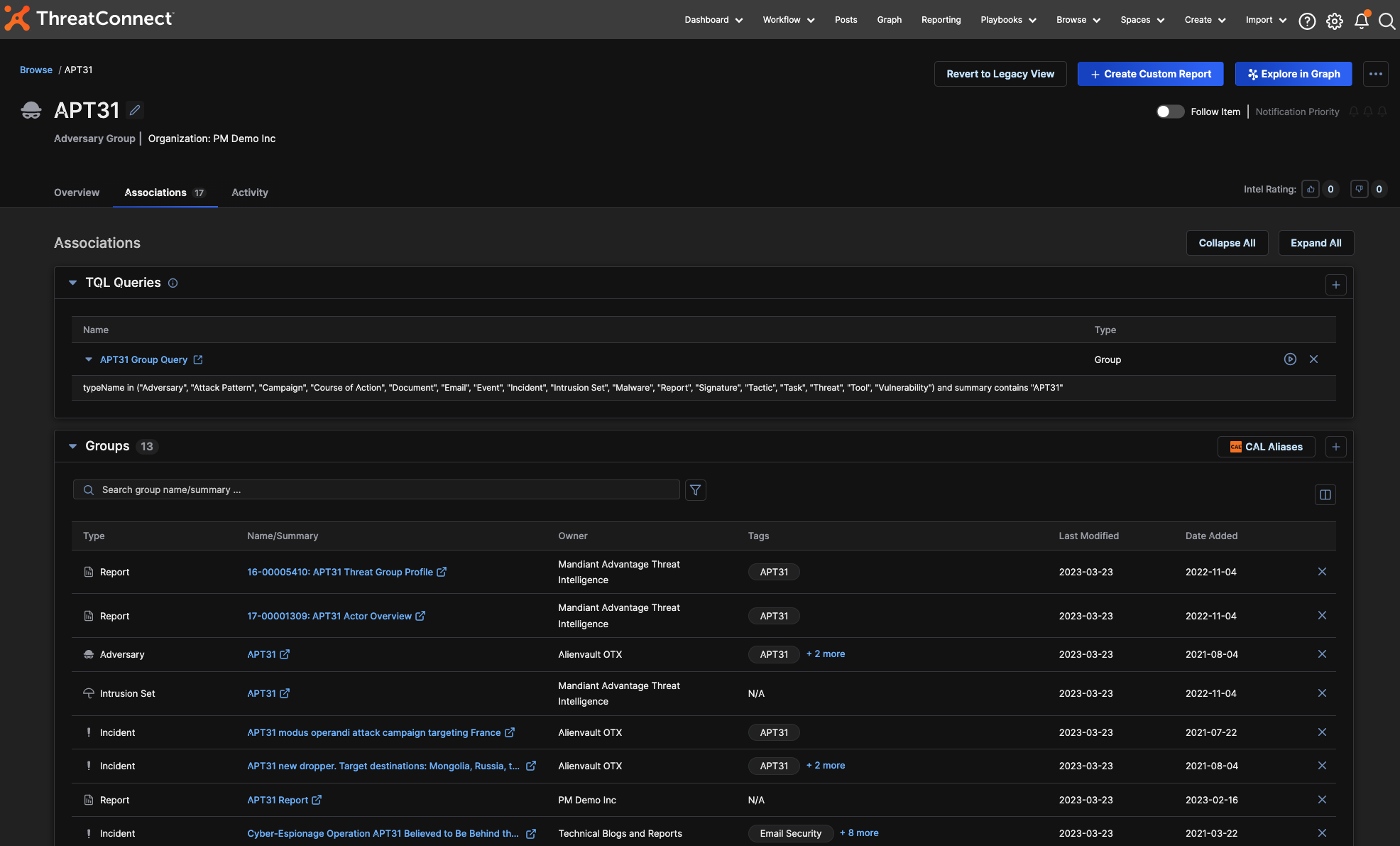
Automated Associations with TQL
Automated Associations with TQL, ThreatConnect’s proprietary query language, allows users to assign a TQL query to a Group. That query then automatically searches ThreatConnect for Groups or Indicators matching the TQL query and associates those items directly to the assigned Group, making the process of building a threat profile much faster and more streamlined. Each query is scheduled to run nightly but can be run on-demand to provide the most up-to-date information.
Automated Associations bring together all of the information an analyst has about a topic so they can build out their Threat Library and Threat Actor Profiles without having to dig around the Platform. This feature can also be used to track Intrusion Sets, MITRE techniques, and Vulnerabilities without the need to build Dashboards.
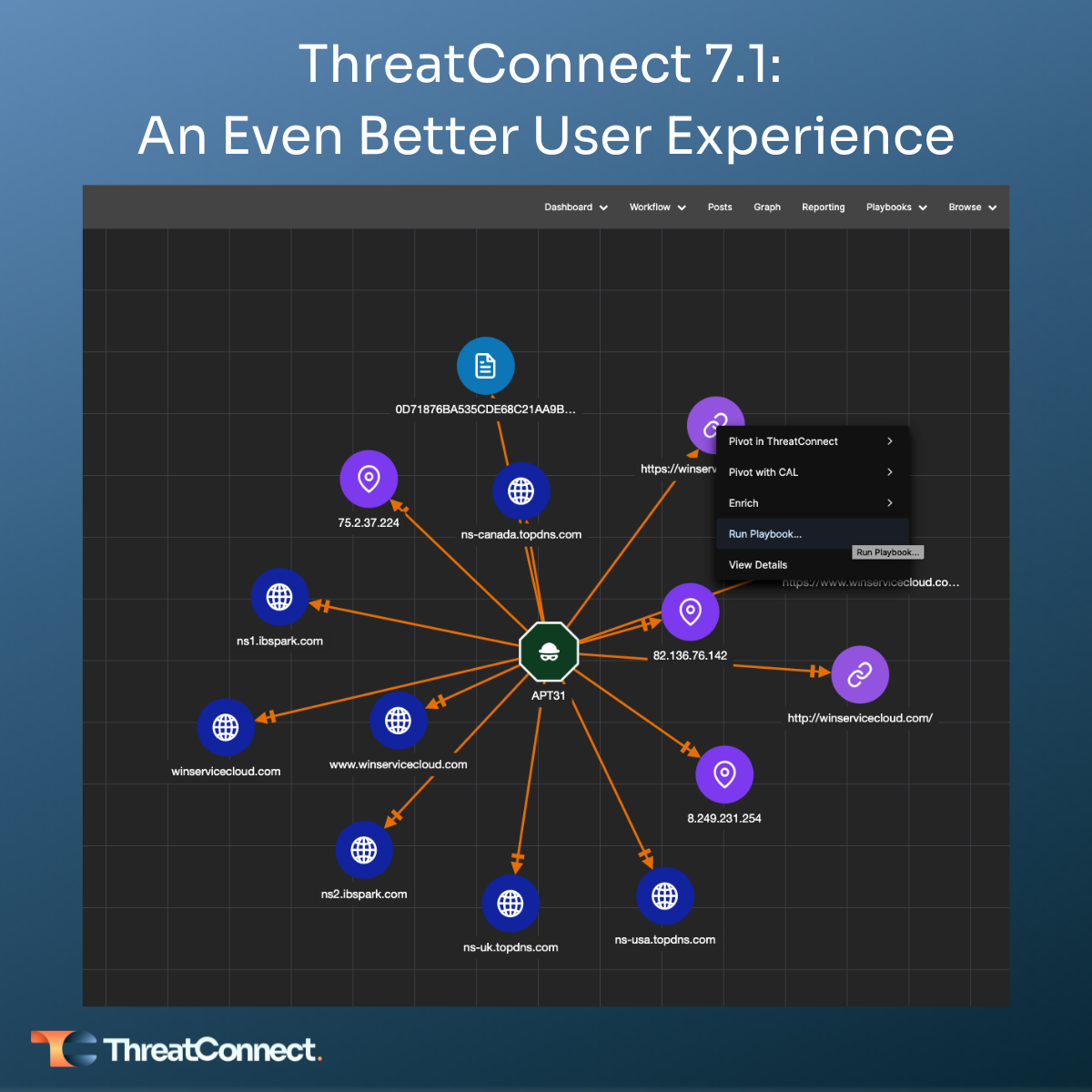
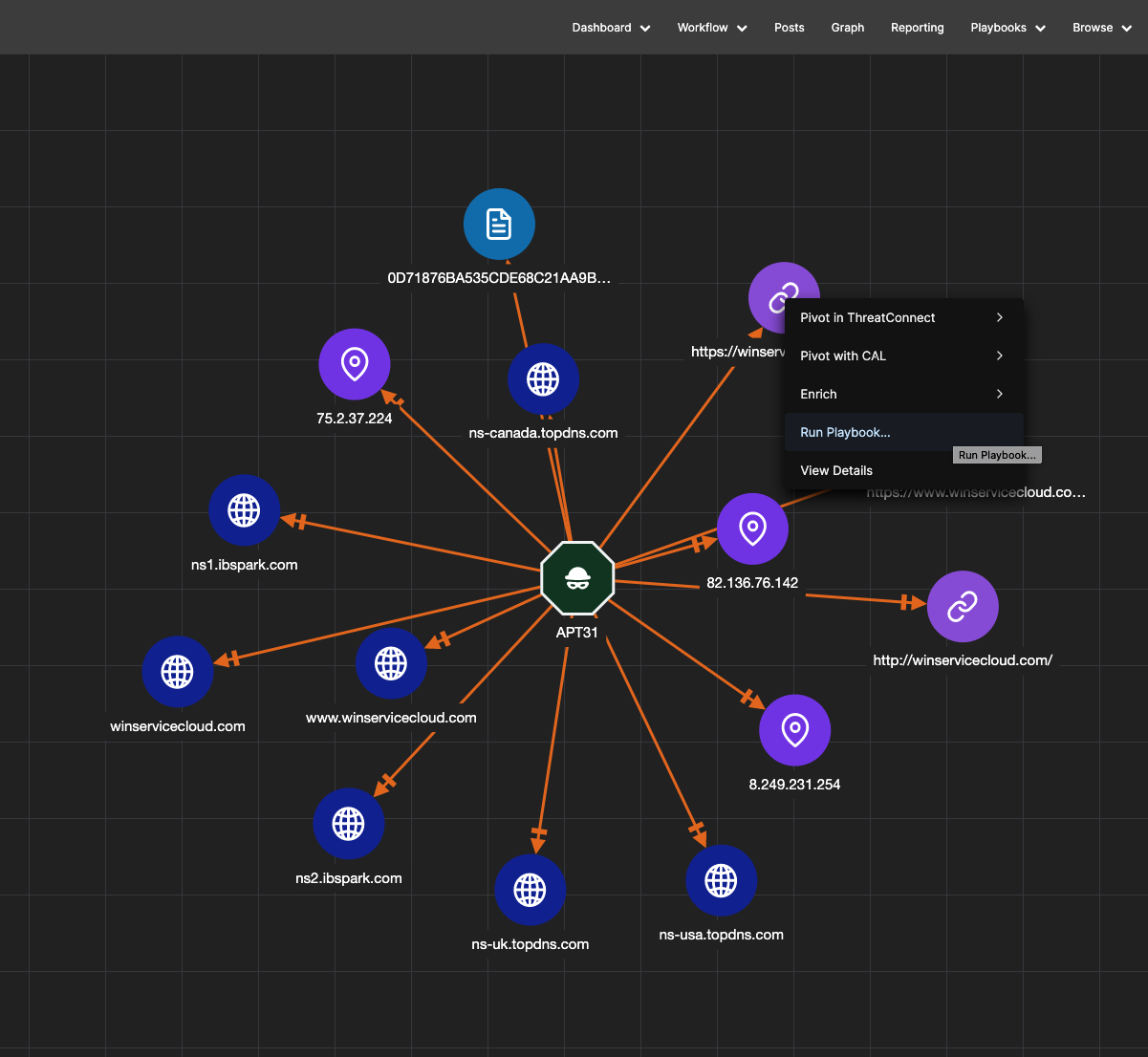
Threat Graph Enhancements
Threat Graph is ThreatConnect’s visualization tool used by analysts to view, pivot, and explore relationships in their datasets. In ThreatConnect 7.1, users can run Playbooks directly in Threat Graph so they can efficiently investigate and act on Indicators in one place. Users can even run a Playbook on multiple Indicators for maximum efficiency.
Explore Playbooks in Threat Graph with our interactive demo
Additional Features and Fixes
- Explore and Pivot on Tags in Threat Graph
- Added ‘default source’ attribute to the Detail page
- Ability to save a source with an attribute when editing
For more information on these new capabilities and how ThreatConnect can help your organization operationalize threat intelligence, please reach out to sales@threatconnect.com or request a demo.