Posted
If you’ve seen our blog, “Luke in the Sky with Diamonds,” or have read Adam Shostack’s excellent book: “Threats: What Every Engineer Should Learn From Star Wars,” you know that Star Wars is really just a series of cybersecurity parables. In this blog, we’re going to examine how the lead-up to the Battle of Hoth in The Empire Strikes Back illustrates some of the shortcomings of the traditional Threat Intelligence Cycle, as well as how the Galactic Empire was able to overcome those shortcomings by leveraging an Evolved Threat Intelligence Cycle.
The Battle of Hoth itself is a textbook example of the value of threat intel, which we can define as “knowledge of an adversary that can be used to inform action.” In this case, the knowledge was the location of the Rebel’s hidden base, and the ultimate action was an overwhelming Imperial victory against the Rebellion.
The Traditional Intelligence Cycle
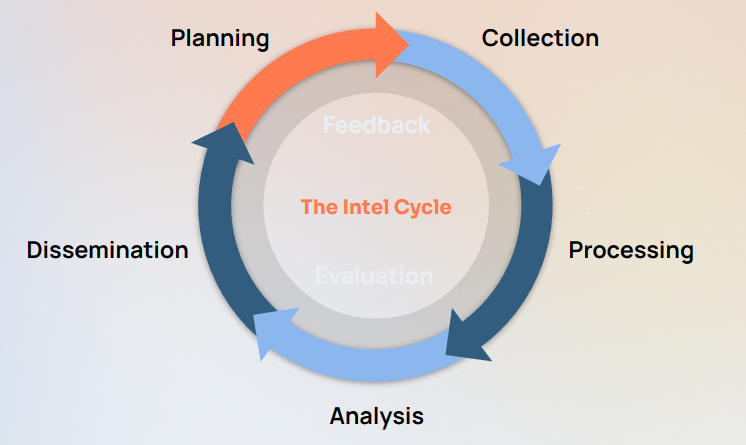
Let’s look at how the Intel Cycle was put to use here. As a refresher, the Intel Cycle consists of five phases:
- Planning and Direction
- Collection
- Processing
- Analysis and Production
- Dissemination and Integration
“Feedback and Evaluation” is thrown in as a meta-phase intended to ensure continuous improvement throughout the cycle.
Planning and Direction

I wish Darth Vader were my CISO!
In the opening of the film, Darth Vader is painted as an effective manager. He sets clear, specific objectives for the team’s intelligence activity: find the Rebel base and Luke Skywalker. This is a well-aligned Priority Intelligence Requirement because it specifically addresses threats that are highly relevant to the security of the Empire. So far, so good!
Collection
An Imperial Probe Droid.
Following Planning and Direction, the Imperial Navy leaps to action and sends thousands of probe droids into the far reaches of space. This is a very broad but necessary Collection effort.
Processing

[John Williams intensifies]
Even though Han and Chewbacca managed to trigger the probe droid’s self-destruct while conducting a bit of intrusion analysis, the droid still managed to radio its findings back to the fleet, where the data was decrypted and Processed for final analysis.
Analysis

A fragment of intelligence from a probe droid in the Hoth system.
Upon examining the probe droid’s data, Imperial agents were able to identify human life readings.
Dissemination

Just another SOC meeting.
This is where things start to go off the rails. Captain Piett, a threat intel analyst, attempts to convey his findings to Admiral Ozzel, who’s focused on operations. The Admiral is concerned about false positives: “If we followed up every lead [it would waste resources]!” He has no desire to take action on the disseminated intelligence.
That Is Why You Fail
So we have a plan, data is collected, processed, and analyzed, disseminated, and Captain Piett even gets some feedback (“I want proof, not leads!”). We have a fully complete and closed intelligence cycle. If the Empire didn’t find a better way to operationalize their intel, the movie would be over: Captain Piett would go back to searching, the Rebels would have had time for a complete evacuation, and Luke Skywalker would have eluded Vader’s grasp.
Of course, that’s not what happens. Let’s take a look at the shortcomings of the traditional cycle, and how the Empire took a move evolved approach.
Limitations of the Intel Cycle
There are a few key limitations with the intel cycle, but fundamentally they boil down to the same point: the cycle is treated as a fully closed loop. Intel is disseminated… but then what? Does it sit, ignored, in a SOC analyst’s inbox? Does it blow up a SIEM with false positives? Does it miss a true positive due to a flawed detection signature? Does a power-tripping admiral reject it due to a culture of silos and backstabbing?
Lack of Accountability
While the intel cycle does have a “feedback” step, it’s not strictly enforced and very often is not properly quantified. Teams can end up in echo chambers, and as with the case of Admiral Ozzel often the feedback is based on a lack of trust or confidence in the very intelligence that’s supposed to be informing action!
The end result is that threat intelligence can often be seen as a nice-to-have rather than an absolute essential element of a security organization. As we’ll see, we know that the Empire does consider it essential, and it ultimately leads to their victory during the Battle of Hoth.
Lack of Stakeholder Involvement
Intelligence doesn’t exist for its own sake, so it’s curious that the stakeholders it’s supposed to benefit aren’t even called out in the cycle! There’s a strong risk that Dissemination is treated as a “toss it over the fence” kind of step. If Darth Vader is the one setting the PIRs for his team, why is he not looped in when relevant intelligence is uncovered?
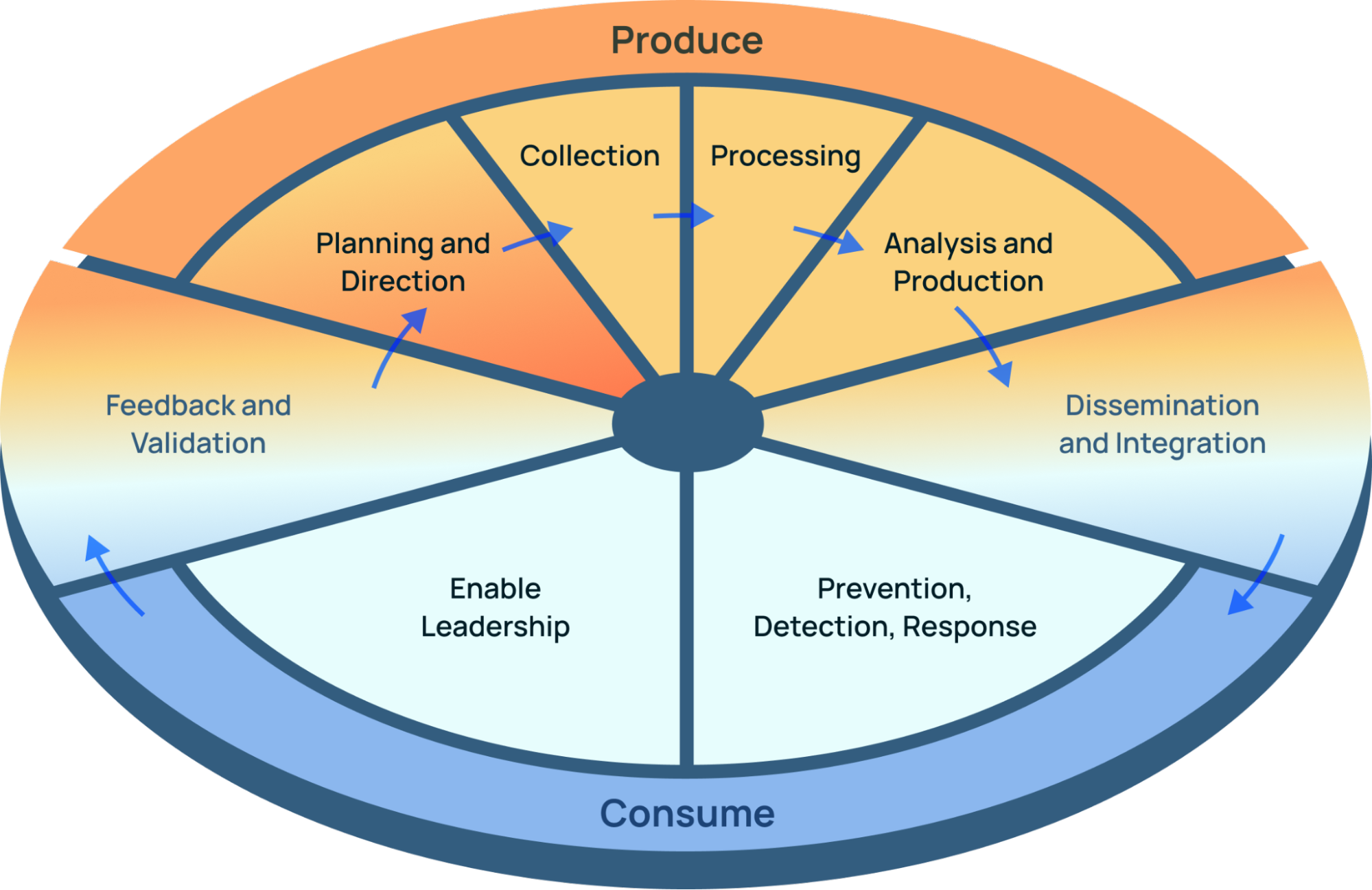
The Evolved Intelligence Cycle
A delicious intelligence pizza.
The Evolved Intelligence Cycle solves these issues in a few key ways:
- It explicitly calls out the personas involved in threat intelligence: Producers (CTI analysts, researchers, Captain Piett, etc.), and Consumers (SOC/IR, threat hunters, leadership/CISOs, red and blue teams, Admiral Ozzel, Darth Vader, etc.).
- It takes into account the action part of threat intel (Dissemination is not action!), such as detection and enabling leadership to make strategic decisions.
- Dissemination and Feedback are “bridge” steps between the two personas, which turns threat intelligence into a truly collaborative discipline across the entire security organization.
Consumers must have agency and a voice in the intel cycle, and Producers need to be held accountable for the quality of the intel they produce. “Feedback” here means looking at data like detection efficacy (e.g. false positives vs true positives), actions taken, and whether decisions were informed. If you’d like to learn more about how to measure the overall impact of threat intelligence, definitely check out this talk from our own Marika Chauvin: How to Get Promoted: Developing Metrics to Show How Threat Intel Works.
The Empire: Evolved
Luckily for the Empire (but unluckily for the Rebellion!), Darth Vader understands the importance of accountability and stakeholder involvement.

General Veers must have ice in his veins to stand so close!
Since Vader’s the primary stakeholder of the “Find the Rebel Base” Priority Intelligence Requirement, he inserts himself as an Intelligence Consumer into the conversation.
Consumption in Focus

Now this is what I call taking action based on knowledge of an adversary!
| Enable Leadership |
Leaders and Sith lords have the big picture and need the right intel to make effective decisions.
Prevention, Detection, and Response
|
Continuing the Loop
There are plenty of examples throughout the rest of the film of the Evolved Threat Intel Cycle loop continuing to run:
- Intelligence is acquired that the Rebels have raised their shield generator, which leads to the Consumers changing their Response action from orbital bombardment to ground assault.
- Priority Intelligence Requirements are changed based on new information to find the Millenium Falcon, and Intel Producers conduct several pivots to accomplish this (asteroid bombardment, attempted hyperspace tracking, etc.).
- Consumers are supplemented with third-party threat hunt teams (i.e. bounty hunters like Boba Fett and Bossk).
- The entire security organization collaborates to set up a honeypot to lure Luke Skywalker to Cloud City on Bespin. Or should it be considered ransomware?
The Importance of Feedback

The best managers cultivate top talent and promote from within.
We’ll close where we started: with Darth Vader as an effective manager. Giving actionable feedback and making adjustments to inform the next run through the evolved intel cycle is critical to improving the overall quality, relevance, and effectiveness of threat intelligence. Vader does a great job of breaking down silos (by using the Force to choke one bad apple), and by promoting Captain Piett to Admiral, he’s effectively giving a vote of confidence to the power of threat intel and creating a fusion center model. He continues to give feedback to his team throughout the film, thanks to him being an empowered intel Consumer.
Conclusion
The Battle of Hoth in The Empire Strikes Back is a clear example of the value of threat intelligence. The film highlights the limitations of the traditional Threat Intelligence Cycle, which is often treated as a closed loop and lacks accountability and stakeholder involvement. However, the Galactic Empire was able to overcome these limitations by adopting an Evolved Threat Intelligence Cycle. This approach explicitly calls out the personas involved in threat intelligence, ensures continuous improvement, and fosters collaboration and trust between producers and consumers of intelligence. The end result is that threat intelligence becomes an essential element of the security organization, leading to successful operations and outcomes.
One thing that the Empire did not have was a software platform purpose-built to operationalize the Evolved Threat Intel Cycle: a TI Ops platform. A TI Ops platform takes the Evolved Cycle and streamlines each phase with automation and analytics. A TI Ops platform helps boost consumer confidence in the cycle and gives Producers tools that help them demonstrate how they’re making a difference to the broader security organization. Perhaps if Admiral Ozzel had had a TI Ops platform, he wouldn’t have faced Vader’s wrath!
May the Force be with you.
If you’d like to learn more about our Threat Intelligence Operations and the Evolved Threat Intel Lifecycle, please read “The Dawn of TI Ops.”

