Posted
Since our previous threat intelligence dashboards blog on how to get more visibility over the threat landscape associated with the Russian-Ukraine war, the situation unfortunately hasn’t been resolved, and the U.S. Government has recently issued statements warning of potential cyberattacks by Russia against the United States
ThreatConnect has continued to look at how we can provide our customers with more precise monitoring of threat intelligence and threats emanating from Russia. We have created custom dashboards that monitor for a variety of Russian threat actors. We go through each of those below with an explanation of how to construct the dashboards or add individual cards if you want to integrate these into some of your existing dashboards.
There are two dashboards, one is a new one focused on Russian APT groups and the other is an update to the dashboards we highlighted in our previous blog post and in this guide. All the cards with instructions to create these dashboards are available in this guide.
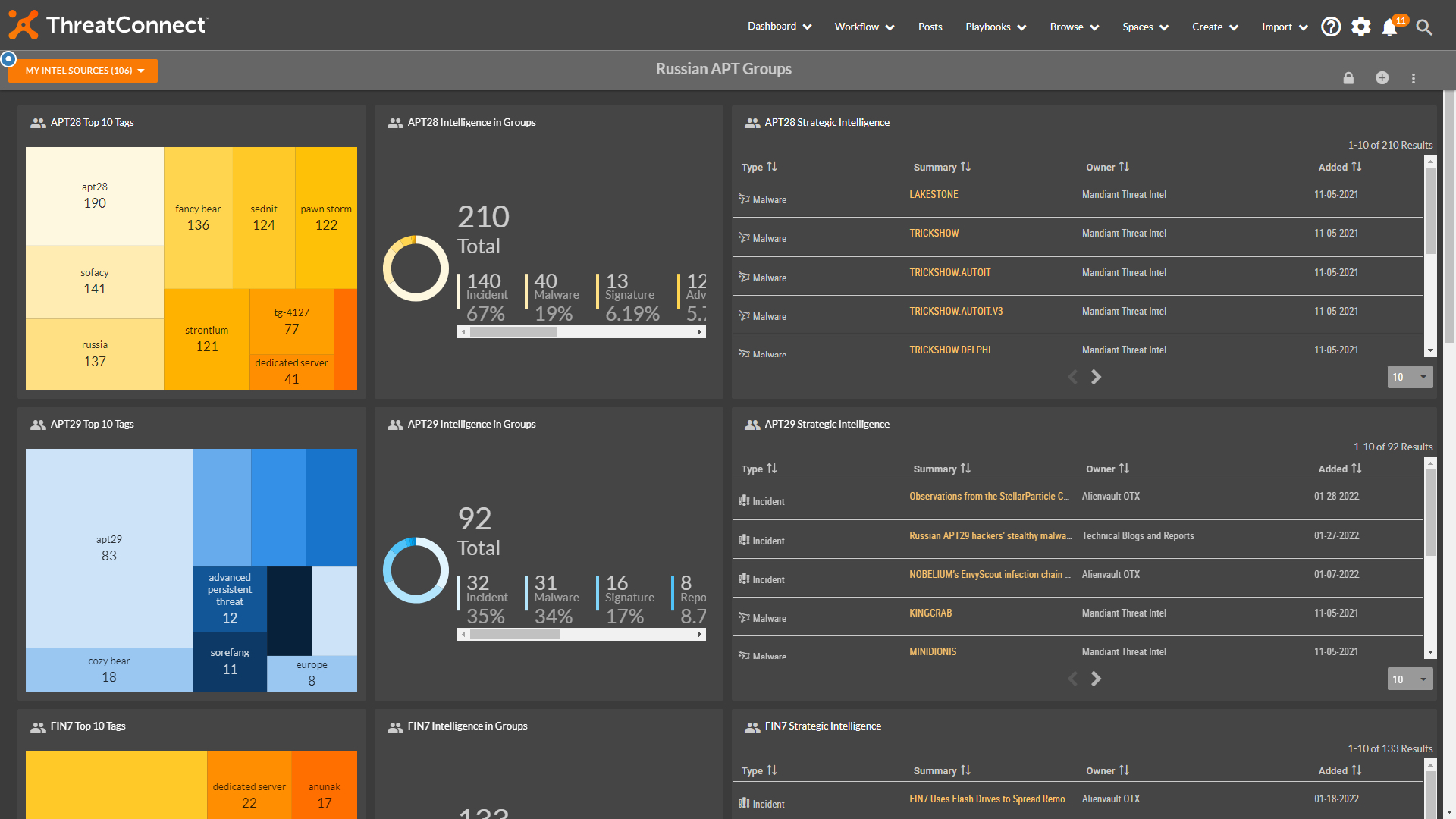
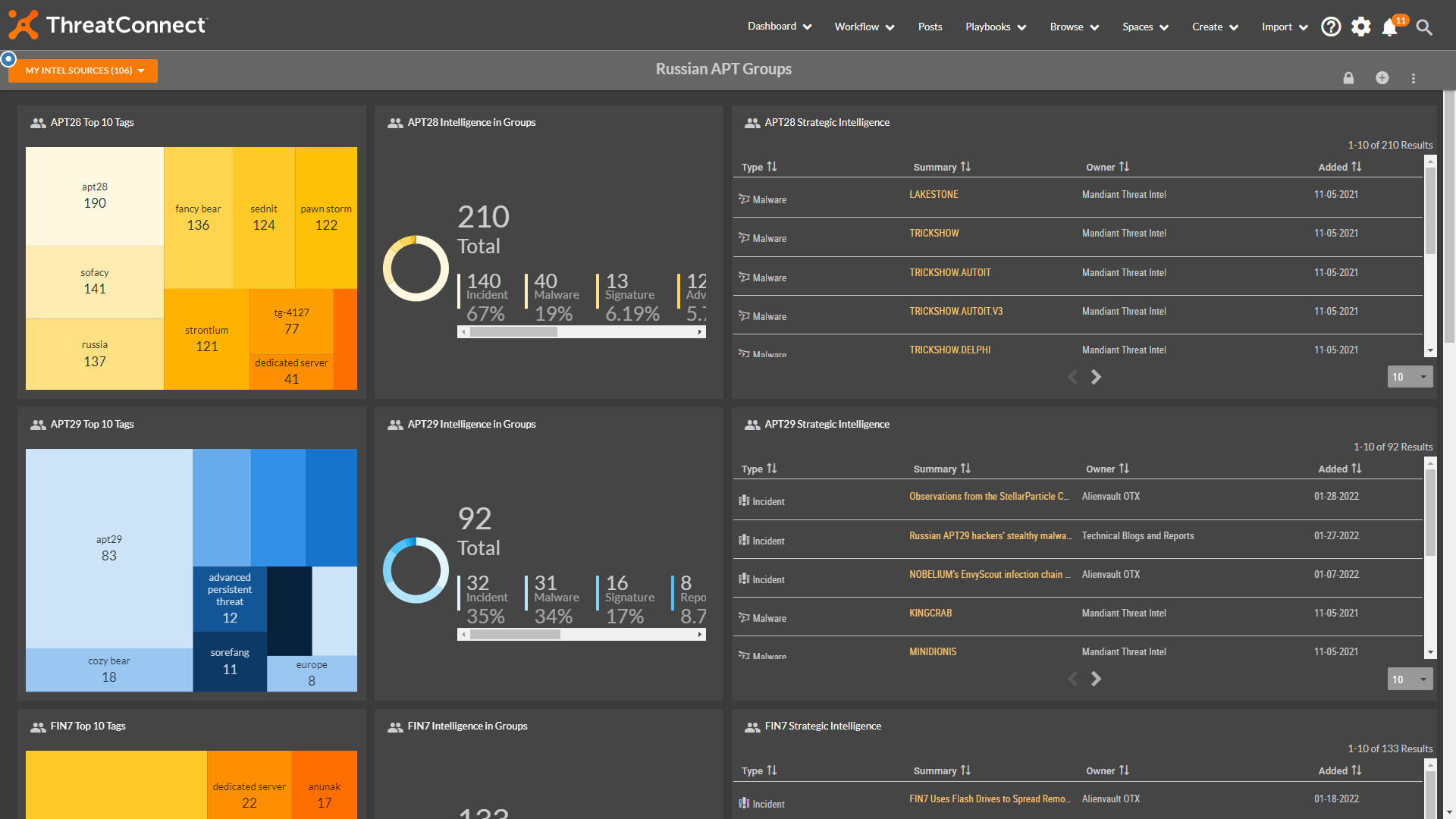
This new dashboard focuses on Russian APT Groups.
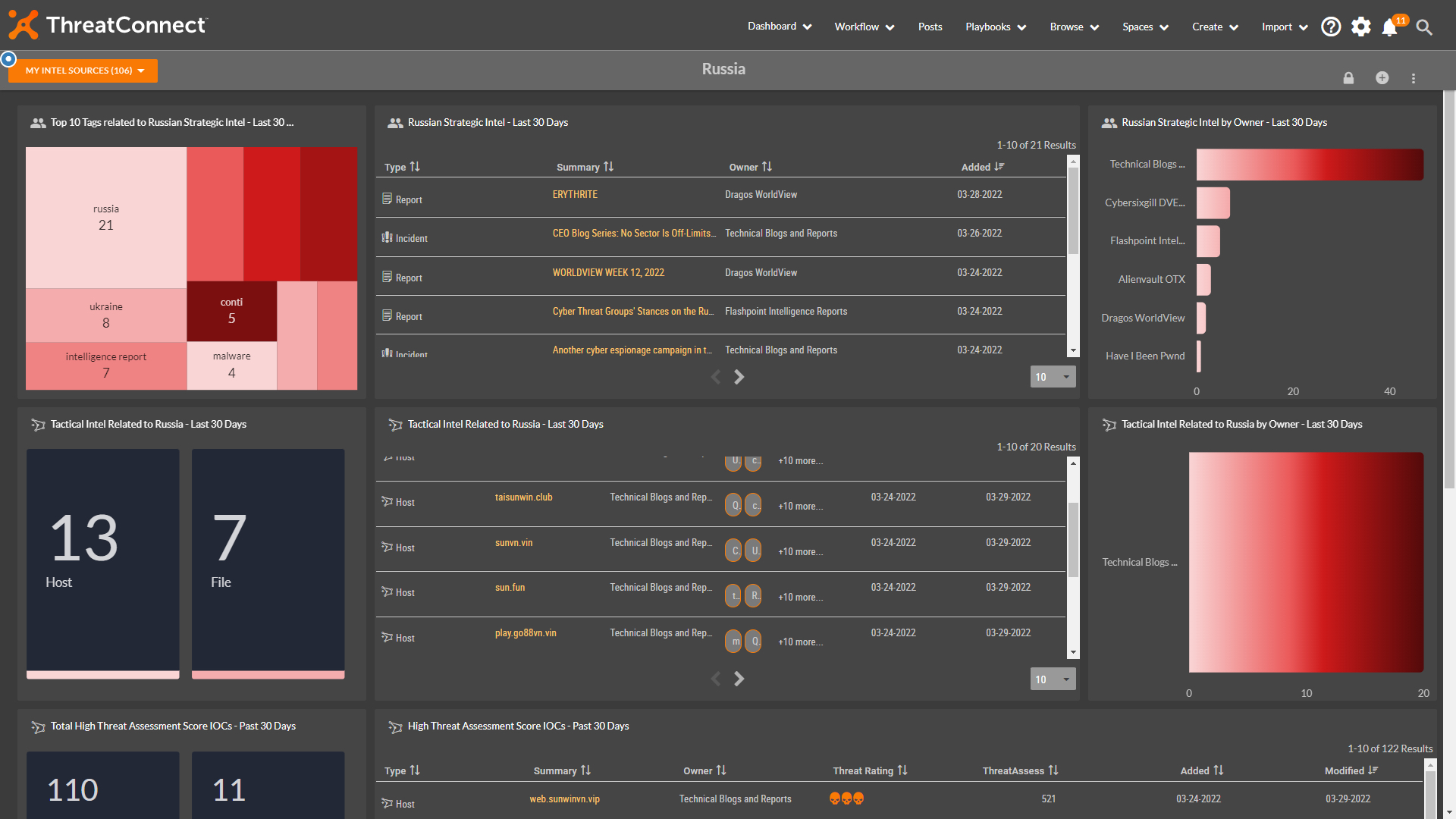
This is an updated dashboard from our previously provided ones that focuses primarily on Russian-specific Threat Intelligence.
So how do you get started if you want to create your own dashboard bringing together the intelligence you have in ThreatConnect?
If you’ve never created a custom dashboard in ThreatConnect or need a fresher, start with this tutorial.
If you need further assistance, please reach out to the ThreatConnect Customer Service team and they will be happy to help you build out a dashboard.
Authored by Product Marketing (Toby Bussa) and Solution Engineering (Mike Summers)