
Read insights, thought leadership, and platform updates.
No Blogs Match Your Results
Please try again or contact marketing@threatconnect.com for more information on our blogs.

From Frustration to Clarity: The Importance of Quantifying Risks in Risk Management
Cyber Risk Quantification should be part of any Risk Management program because quantifying risk enables better business and cybersecurity decision-making, in addition to increasing need driven by frameworks and regulations, such as the proposed changes to NIST Cybersecurity Framework 2.0 and the recent US SEC Cybersecurity Rules. Given my past experience both working in & […]

ThreatConnect TI Ops Platform 7.4: Faster Analysis, Enhance Defenses
Empower Your Security Controls Coverage with ATT&CK Visualizer In today’s cybersecurity landscape, the faster you can identify and mitigate threats, the less damage they can cause. To gain the upper hand, security teams are turning to the MITRE ATT&CK framework – a comprehensive matrix of the tactics and techniques used by real-world threat actors. The […]

Unveiling InQuest Insights in the ThreatConnect TI Ops Platform
ThreatConnect and InQuest are excited to announce the availability of a new integration between InQuest InSights Threat Intelligence and ThreatConnect’s TI Ops Platform. InQuest’s high-fidelity threat intel is derived from their at-scale file analysis of malware and enriched with a variety of open-source and proprietary reputation sources. The integration with ThreatConnect’s TI Ops Platform makes […]

Announcing A New Partnership Between Bayse and ThreatConnect
We are excited to announce that Bayse Intelligence and ThreatConnect have a new strategic partnership, starting with the integration of Bayse Early Alert – Bayse’s phishing intelligence feed. Phishing-style attacks are not going away Like many of the most challenging problems in cybersecurity, phishing is a constantly evolving challenge for enterprises of every size. According […]

8 Questions to Ask a Threat Intelligence Platform Vendor
The threat intelligence (TI) landscape contains a varying number of services and technologies, so finding the right threat intelligence platform can be daunting. Still, this decision is crucial to turning your threat intel data into something valuable for intel customers. To help you find the right platform, we’ve compiled eight questions to ask threat intelligence […]

What Is Strategic Risk Quantification?
Authored By: Andrew Dillin, Threat Intelligence Lead – Cyber & Physical at NatWest Group A question posed to me following an earlier LinkedIn post of mine. Is there a good way of working out if you are being targeted more than your peers? How sustained or capable the threat is etc? Organizations will normally have […]

How To Effectively Measure the Value of Threat Intelligence
Authored By: Andrew Dillin, Threat Intelligence Lead – Cyber & Physical at NatWest Group As we come to the end of the year, a number of us will be working hard to report the tangible change Threat Intelligence has made to the organization over the past year. We hear a lot about KRI’s and other […]

How To Identify The Right Platform For Your Cyber Threat Intel Needs
Cyber threat intel (CTI) teams, and organizations looking to stand up a new CTI function, face a variety of challenges. Many organizations jump into CTI without enough (or any) planning, which leads to a host of issues, like knowing what type of data sources are needed, what kind of intelligence needs to be produced, how […]
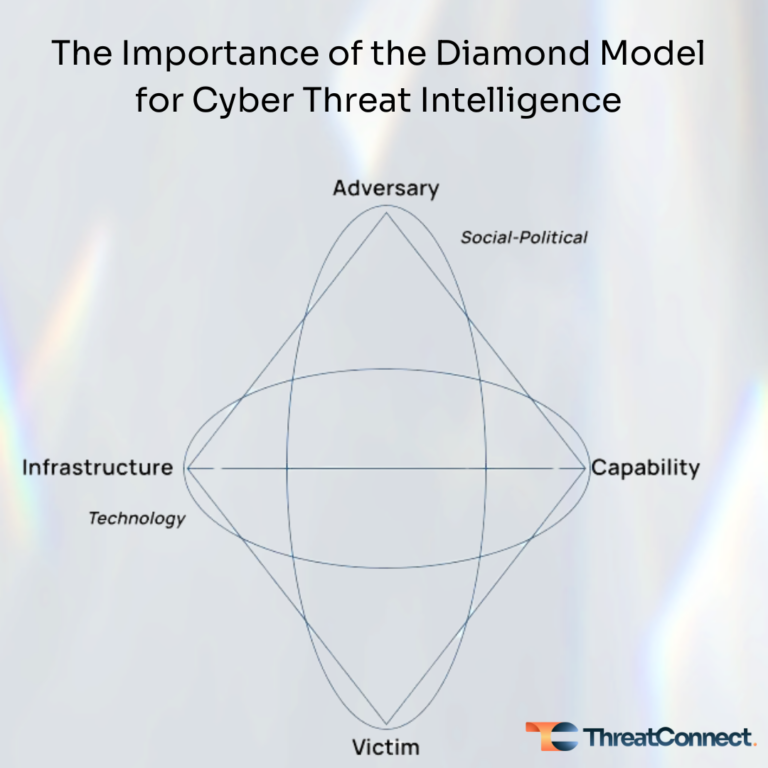
The Importance of the Diamond Model for Cyber Threat Intelligence
The Diamond Model of Intrusion Analysis (aka the Diamond Model), written by Sergio Caltagirone, Andy Pendergast (co-founder and EVP of Product at ThreatConnect), and Christopher Betz, is a cornerstone of cyber threat intelligence tradecraft. It was released in 2013 in what I believe was one of the most constructive periods of cybersecurity when other important […]

Empower Your CTI: A 3-Step Guide to Creating Intelligence Requirements on ThreatConnect’s TI Ops Platform
Cyber Intel Analysis is a growing concern for organizations of all sizes. Staying ahead of evolving digital threats can seem like an impossible task. That’s where ThreatConnect’s TI Ops Platform comes in, offering a powerful solution to guide your CTI efforts through ThreatConnect Intelligence Requirements. The best part? Creating and managing your Intelligence Requirements (IRs) […]

FAIRCon 2023 Wrap-up – Our Biggest Highlights and Takeaways
I had the privilege of attending FAIRCON ‘23 Embrace Digital: Managing the Risk of Digital Transformation, Cloud, and AI this year, not as a speaker or a sponsor but as an attendee. It was great being able to catch up with people and to hear how organizations are advancing their cyber risk quantification (CRQ) programs. […]

The Importance of Quantifying Cyber Risk in Decision-Making
When making cybersecurity decisions, like ‘where to apply my investments,’ CISOs, executives, and boards rely on various insights and data points. Cyber risk quantification (CRQ) allows decision-makers to make data-driven, objective, and defensible decisions and enables more effective discussions between the CISO and business leaders. If you want to make business decisions as informed as […]
