
Read insights, thought leadership, and platform updates.
No Blogs Match Your Results
Please try again or contact marketing@threatconnect.com for more information on our blogs.
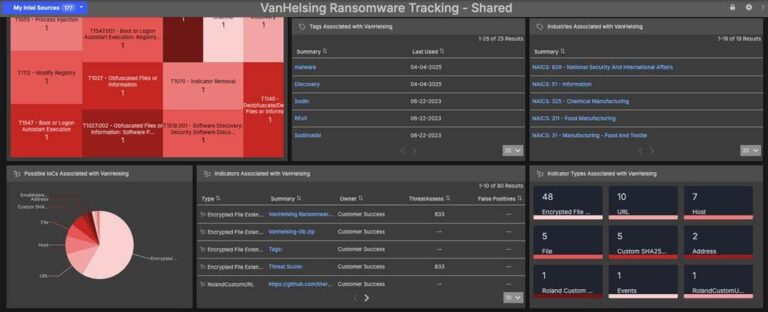
VanHelsingRaaS Intelligence Dashboard Immediately Available for ThreatConnect
VanHelsingRaaS is a reemerging ransomware-as-a-service variant. First used years ago by the likes of UNC4841, it resurfaced in March of 2025 and has been observed to be affecting multiple industry verticals. (See: The Hacker News) The VanHelsing Ransomware Threat Dashboard in ThreatConnect provides security teams with real-time intelligence on the VanHelsingRaaS. This dashboard aggregates data from […]

Tips & Tricks to Get the Most out of RSAC 2025
By now, you’ve probably purchased your passes. Your flight is booked. Your supply of business cards sits at the ready. What more is there to do in preparation for RSAC 2025, taking place from April 28 to May 1 at the Moscone Center in San Francisco? Possibly quite a lot! That’s because when it comes […]

ThreatConnect’s Bayesian Expert: It’s Time to Look Beyond Cool Data Models
The Advanced Persistent Talent series profiles ThreatConnect employees and explores how their work impacts products and offerings, how they got here, and their views on the industry at large. Want to know more about a particular team? Let us know! Bayesian analysis is a statistical method where you start with a “prior belief” about something, […]

ThreatConnect 7.9 is Live: Smarter SLAs, Unified Search, and More Control for Security Teams
In a world where time is the enemy, ThreatConnect 7.9 helps you take it back. Whether you’re a SOC analyst racing the clock to contain a ransomware outbreak, a CTI analyst piecing together adversary behavior, or an MSSP juggling dozens of concurrent investigations, this release gives you the tools to detect faster, respond smarter, and […]

Medusa Intelligence Dashboard – Immediately Available for ThreatConnect
The Medusa Ransomware Threat Dashboard in ThreatConnect provides security teams with real-time visibility into the latest activities, indicators, and trends associated with the Medusa ransomware threat group. This dashboard aggregates threat intelligence from multiple sources, enabling analysts to proactively detect, track, and mitigate Medusa-related threats before they impact the organization. Key Benefits: Centralized Intelligence: Consolidates […]

Unlock Better Decisions with Risk Quantification
Whether in business or in life, we are faced with making decisions every day, but how do you know you’re making the right one? Enter risk quantification—a powerful tool that transforms decision-making by providing actionable insights based on measurable data rather than instincts or guesswork. By translating risks into tangible numbers, organizations can prioritize actions, […]

Threat Intel at Your Fingertips: Helping Analysts Move Faster Than Ever
The Analyst’s Dilemma: Too Much Noise, Too Little Time Let’s be honest—being a security analyst is a constant race against time. You’re bombarded with alerts, threat feeds, intelligence reports, and SOC escalations while trying to correlate data, determine risk, and take action—before a breach occurs. The challenge isn’t just getting intelligence; it’s getting the right […]

Align Your Security Operations with MITRE ATT&CK v16 Using the ThreatConnect ATT&CK Visualizer
Last October, MITRE released ATT&CK v16. In a blog post, the organization described its latest updates as a mission in balance, with the goal of “striking that perfect chord between familiar and pioneering to keep things real and actionable.” While MITRE’s ATT&CK framework is a well-known and popular tool in cybersecurity circles, many teams still […]
Transforming Third-Party Risk Strategy with Financial Risk Quantification & SecurityScorecard
Organizations today rely heavily on third-party vendors to support their operations (e.g., call centers, shipping centers, data storage providers, etc.). While these partnerships offer numerous benefits, they can also introduce significant cyber risks. Managing a complex network of vendors can be difficult, as traditional risk assessments often don’t provide a clear or measurable view of […]

Debunking Anomali’s Claims: Why ThreatConnect is the Superior Threat Intelligence Platform
As a cybersecurity vendor, I like to take a larger view of the market when it comes to the competition. Competitor or not, we’re all on the same side: fighting the good fight against attackers – and hopefully whatever solution is chosen by cybersecurity teams helps them stay ahead and maintain whatever advantage that vendor […]

Automating Threat Data Retrieval: How ThreatConnect, Polarity, and the TQL Generator are Changing the Game
You’re a CTI Analyst tasked with investigating a potential phishing campaign targeting your organization. An alert flags a suspicious email containing a URL that may be linked to a known threat actor. It would be best to determine the URL’s risk level, identify related indicators, and quickly distribute actionable intelligence to your security team. Toggling […]

Higher Fidelity Investigations with Actionable Search, TQL Generator, and More in TI Ops 7.8
When a critical alert lands on your desk, every second counts. Whether you’re triaging flagged IPs, investigating APT activity, or gathering intelligence for a report, the pressure to act quickly and accurately can feel relentless. The reality is clear: manual investigations are too slow, and incomplete data leaves room for error. You need tools that […]
