
Read insights, thought leadership, and platform updates.
No Blogs Match Your Results
Please try again or contact marketing@threatconnect.com for more information on our blogs.
How to Manage and Integrate Signatures in ThreatConnect
Signature Management in ThreatConnect ThreatConnect API with SDKs enables users to develop tools that can automate signature generation and integrate signatures into existing security products When most people first see the ThreatConnect security platform, they may be introduced to the Signatures feature that allows analysts and users to store multiple types of signatures. However, the […]
Cyber Stratego: Strategic vs. Tactical Threat Intelligence
How You Can Apply Strategic and Tactical Threat Intelligence in ThreatConnect One of the questions we get from users of the ThreatConnect platform is, given an encountered indicator, “what should we look for in the platform?” Of course, as with most things intelligence-related, the answer is “it depends.” It depends on your organization’s sources and […]
Can a BEAR Fit Down a Rabbit Hole?
Can a BEAR Fit Down a Rabbit Hole? ThreatConnect Identifies Infrastructure Nexus Between Attacks Against State Election Boards and Spearphishing Campaign Against Turkish, Ukrainian Governments The question on everyone’s mind: Who is behind the recently reported compromises of Arizona and Illinois’ state board of elections (SBOE)? The answer is, we don’t know. When we reviewed FBI […]
Does a BEAR Leak in the Woods?
Identifies DCLeaks As Another Russian-backed Influence Outlet Read the full series of ThreatConnect posts following the DNC Breach: “Rebooting Watergate: Tapping into the Democratic National Committee“, “Shiny Object? Guccifer 2.0 and the DNC Breach“, “What’s in a Name Server?“, “Guccifer 2.0: the Man, the Myth, the Legend?“, “Guccifer 2.0: All Roads Lead to Russia“, “FANCY BEAR […]
FANCY BEAR Has an (IT) Itch that They Can’t Scratch
*This post can also be found on the Fidelis blog, ThreatGeek.* FANCY BEAR Has an (IT) Itch that They Can’t Scratch ThreatConnect and Fidelis team up to explore the Democratic Congressional Campaign Committee (DCCC) compromise Following news reports that the Democratic Congressional Campaign Committee (DCCC) was breached via a spoofed donation website, […]
Guccifer 2.0: All Roads Lead to Russia
Guccifer 2.0: All Roads Lead to Russia Update 07/26/2016 4:00pm EDT Joe Uchill with The Hill, who has previously covered Guccifer 2.0 and the Wikileaks DNC data dump, has provided us with redacted information on his communications with Guccifer 2.0 that has raised our confidence in our current assessments and hypotheses. Check out Joe’s story […]
Guccifer 2.0: the Man, the Myth, the Legend?
Guccifer 2.0: the Man, the Myth, the Legend? ThreatConnect reassesses Guccifer 2.0’s claims in light of his recent public statements Read the full series of ThreatConnect posts following the DNC Breach: “Rebooting Watergate: Tapping into the Democratic National Committee“, “Shiny Object? Guccifer 2.0 and the DNC Breach“, “What’s in a Name Server?“, “Guccifer 2.0: the Man, […]
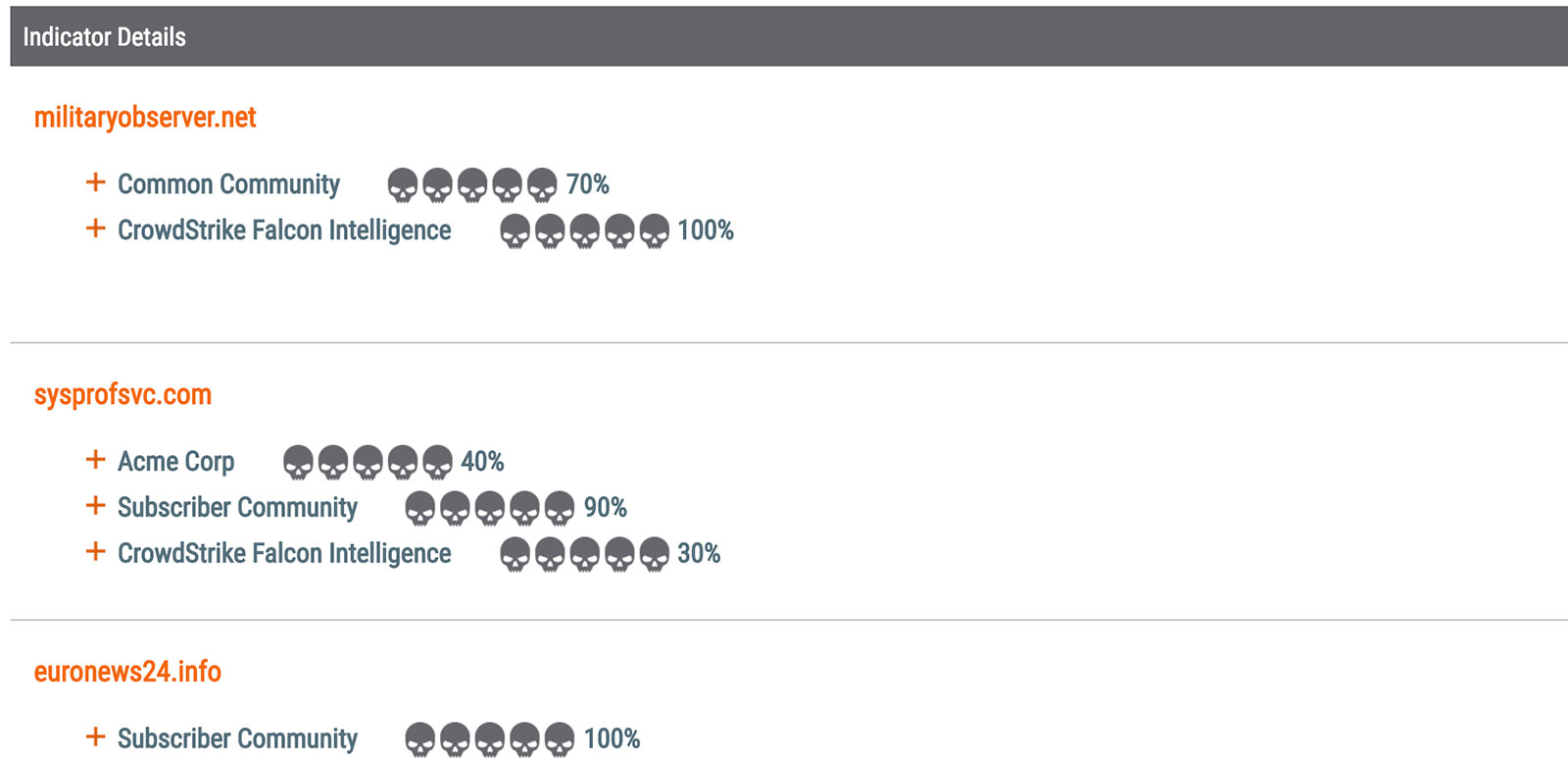
What’s in a Name Server?
What’s in a Name… Server? That which we call an APT. By any other name would smell as foul. Read the full series of ThreatConnect posts following the DNC Breach: “Rebooting Watergate: Tapping into the Democratic National Committee“, “Shiny Object? Guccifer 2.0 and the DNC Breach“, “What’s in a Name Server?“, “Guccifer 2.0: the Man, the […]
Shiny Object? Guccifer 2.0 and the DNC Breach
The Shiйy ФbjЭkt? ThreatConnect challenges Guccifer 2.0’s claimed attribution for the Democratic National Committee (DNC) breach Read the full series of ThreatConnect posts following the DNC Breach: “Rebooting Watergate: Tapping into the Democratic National Committee“, “Shiny Object? Guccifer 2.0 and the DNC Breach“, “What’s in a Name Server?“, “Guccifer 2.0: the Man, the Myth, the Legend?“, […]
Rebooting Watergate: Tapping into the Democratic National Committee
Fancy Bears and Where to Find Them ThreatConnect uses the Crowdstrike blog article as a basis for conducting further research into the DNC breach and identifies additional infrastructure. On June 15, 2016 our partner, Crowdstrike, published a blog article detailing the breach of the Democratic National Committee (DNC) by two Russia-based threat groups, one of […]
The Best Threat Intelligence Feeds
“What are the best, most important threat intelligence feeds that I should integrate into my security operations?“ What Feeds Me, Destroys Me Seriously, every time I get this question a little part of me dies. My left eye begins to twitch. This wave of heat rises up from my belly, and I feel it in […]
May the Fourth be with you: A Star Wars InfoSec Bibliography
Collecting and connecting things is a big part of what we do here at ThreatConnect. We aggregate disparate sources of threat data/intel so it’s within easy reach when you need it. We integrate a bunch of tools and techs via our platform so all that aggregated intel can be put to good use throughout your […]
