
Read insights, thought leadership, and platform updates.
No Blogs Match Your Results
Please try again or contact marketing@threatconnect.com for more information on our blogs.

A Song of Intel and Fancy
A case study tracking adversary infrastructure through SSL certificate use featuring Fancy Bear/APT28/Sofacy. A long time ago, in a galaxy… No. Stop. We’re not doing that anymore. Instead, we’re pivoting to Game of Thrones, or A Song of Ice and Fire for you bookworms, because the fantastical realm provides great material we can relate to […]
Polarity – Open Source Intelligence Integrations
If you use open source threat intelligence platforms, we have two integrations you’re going to love. Polarity recently developed open-source integrations with AlienVault’s Open Threat Exchange (OTX), and Shodan! Yes, you read that right. We’re launching two integrations back-to-back. By integrating with these open source products, we are enabling threat analysts to take full advantage […]
Query a Host or URL Indicator in Archive.org’s Wayback Machine
One-Click querying of the Wayback Machine See if a website has been archived in the Wayback Machine ThreatConnect developed the Playbooks capability to help analysts automate time consuming and repetitive tasks so they can focus on what is most important. And in many cases, to ensure the analysis process can occur consistently and in real […]
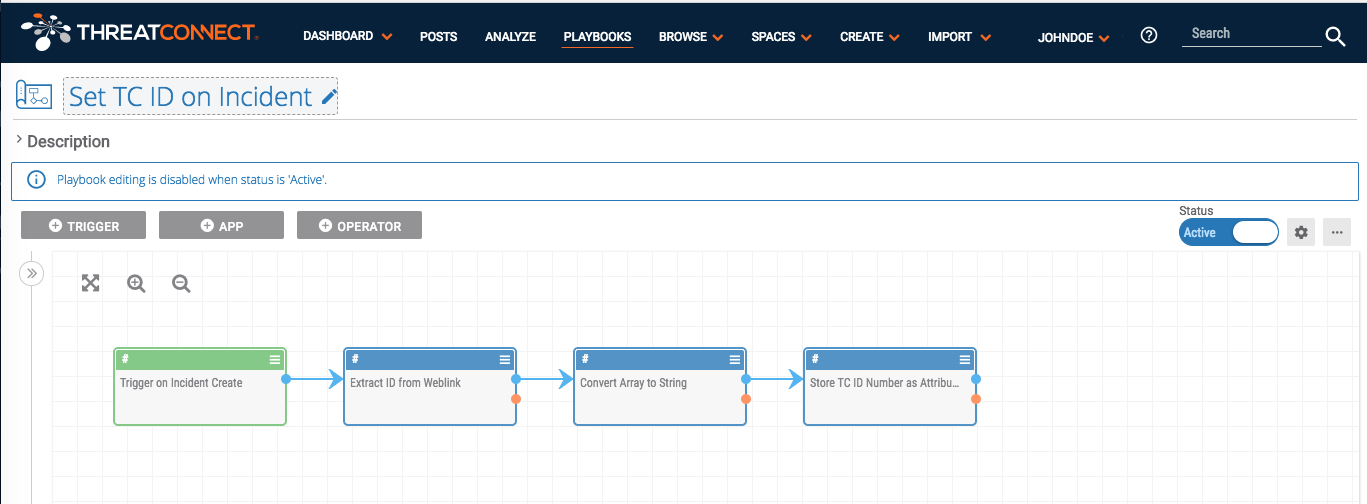
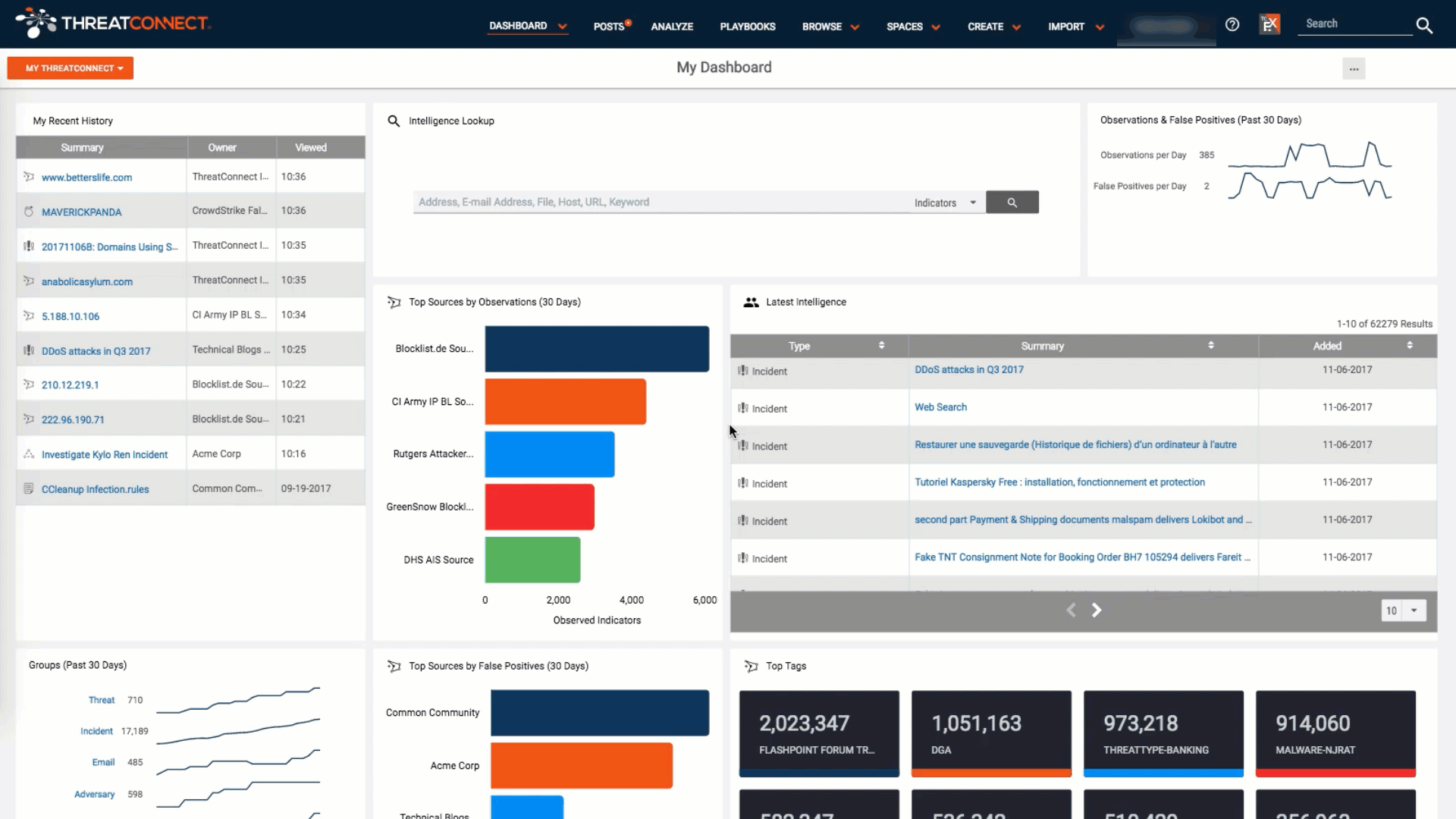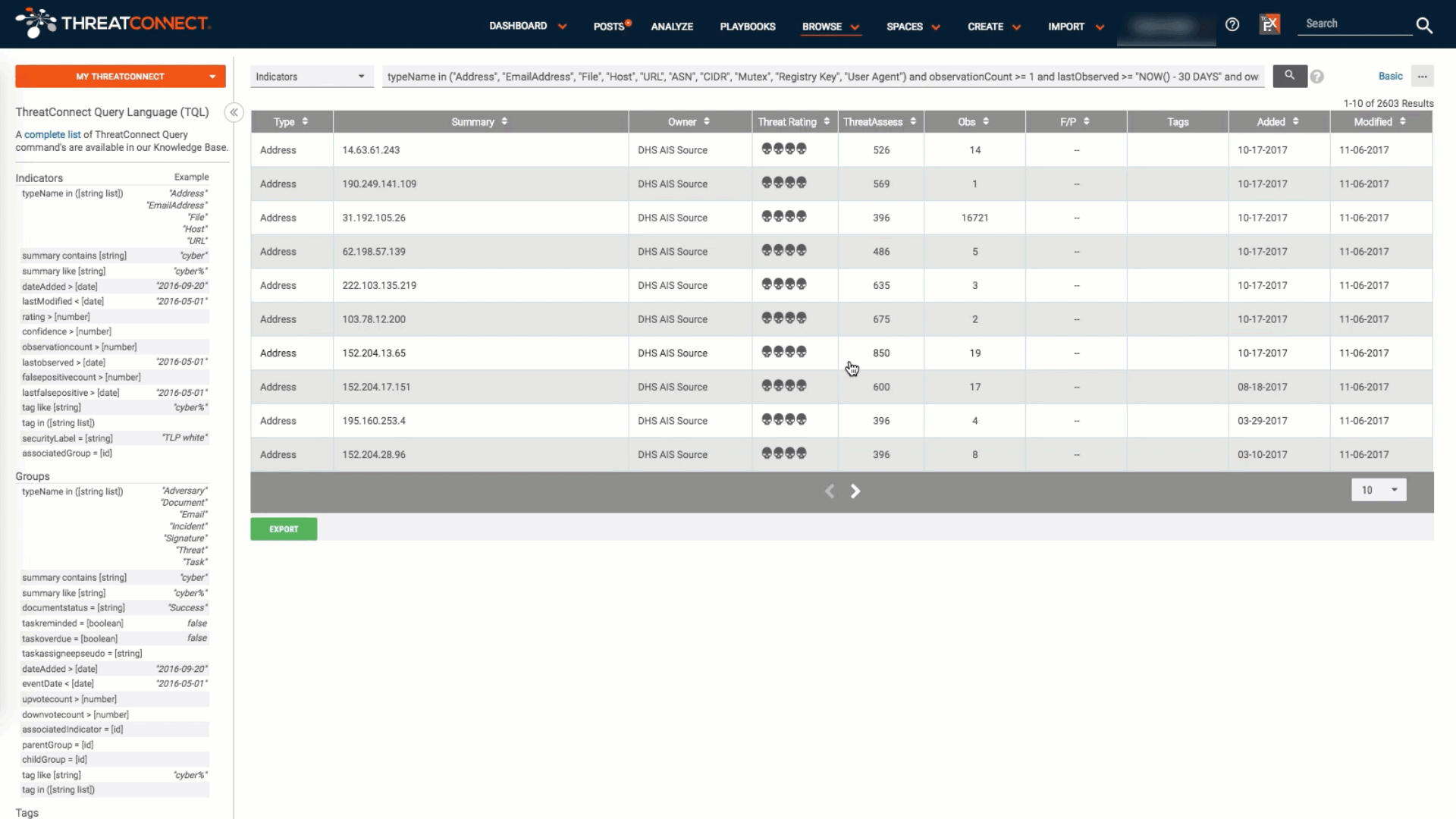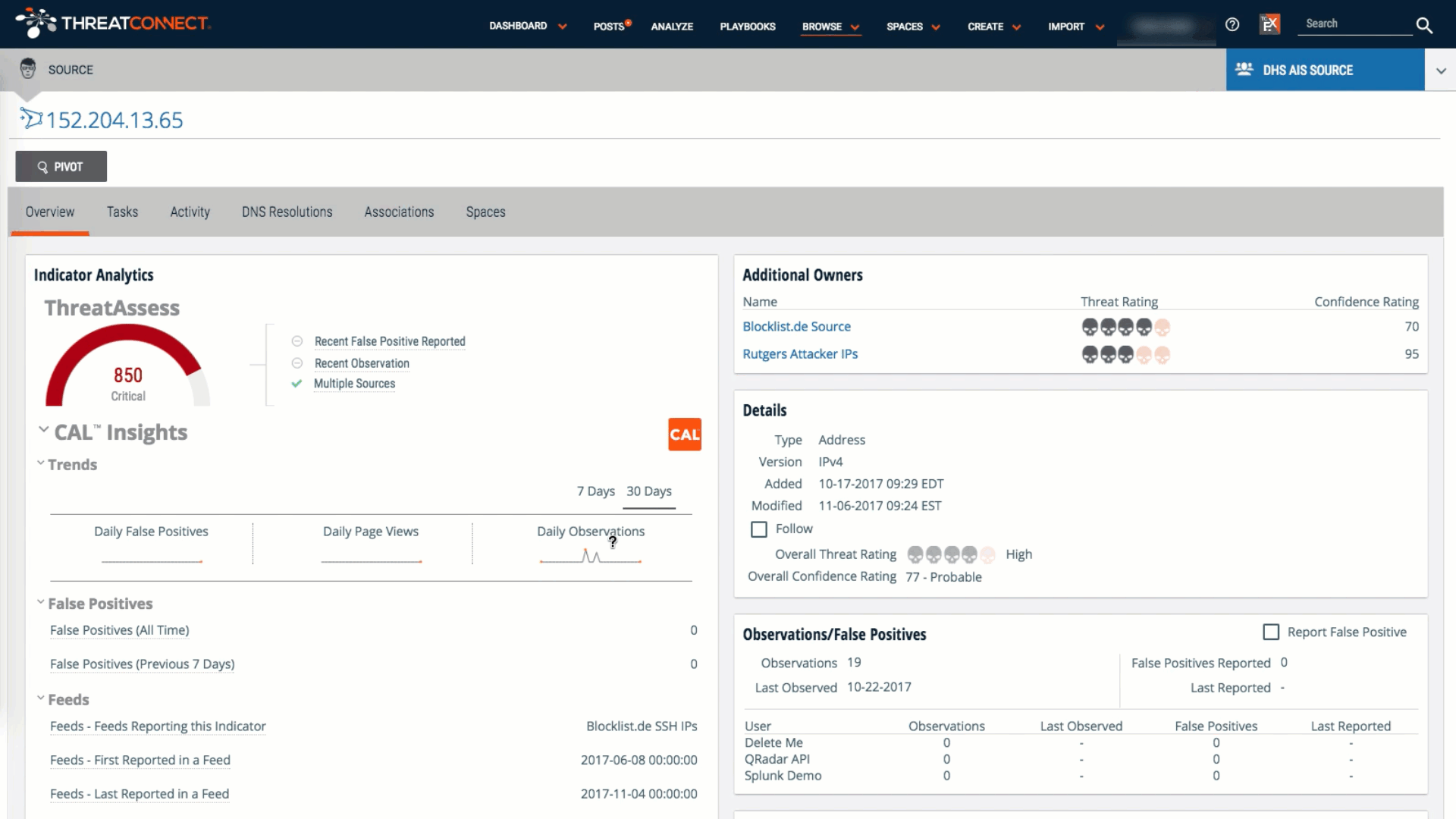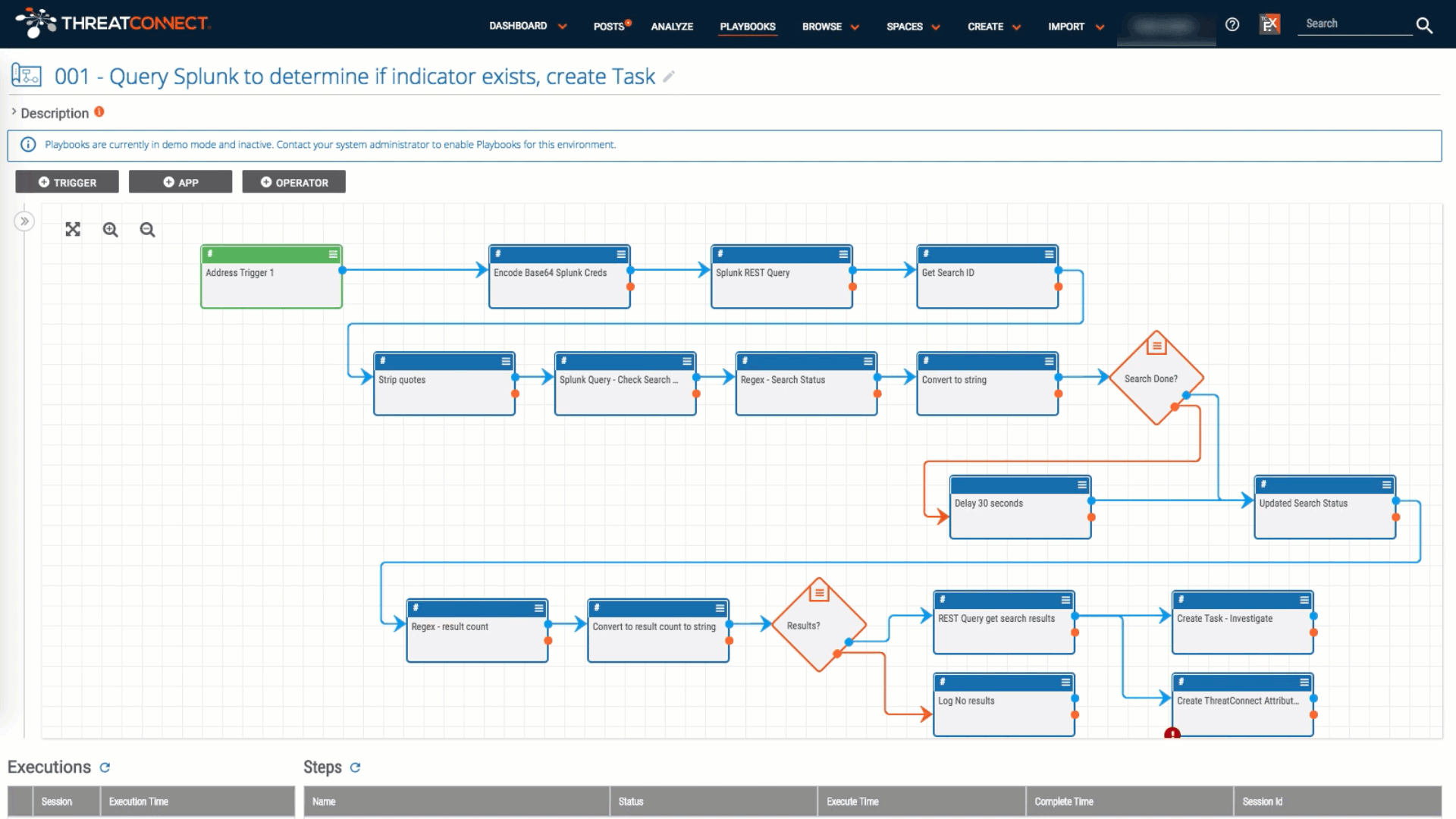
Playbook Fridays: Using Playbooks to populate custom attributes
Create Custom Attribute Types and Validation Rules, then use Playbooks to populate them automatically I was working with a customer who wanted to use ThreatConnect’s Task and workflow features like a traditional ticketing system, with a unique identifier for data objects that they could key off of and pass to other teams as needed. This […]
Duping Doping Domains
Possible Fancy Bear Domains Spoofing Anti-Doping and Olympic Organizations Update – 1/19/18 We recently identified two additional domains — login-ukad[.]org[.]uk and adfs-ukad[.]org[.]uk — which appear to spoof UK Anti-Doping. The domain login-ukad.org.uk uses the Domains4Bitcoins name server previously mentioned and, as of January 19 2018, is hosted on dedicated server at the IP 185.189.112[.]191. This […]
Please Do Not Feed the Phish
How to Avoid Phishing Attacks We’ve all heard the phishing attack stories that start with someone receiving an email that requests an urgent invoice review or password change, and ends with a data breach where personal information is compromised and money is lost. Although many of us may roll our eyes at the possibility of […]
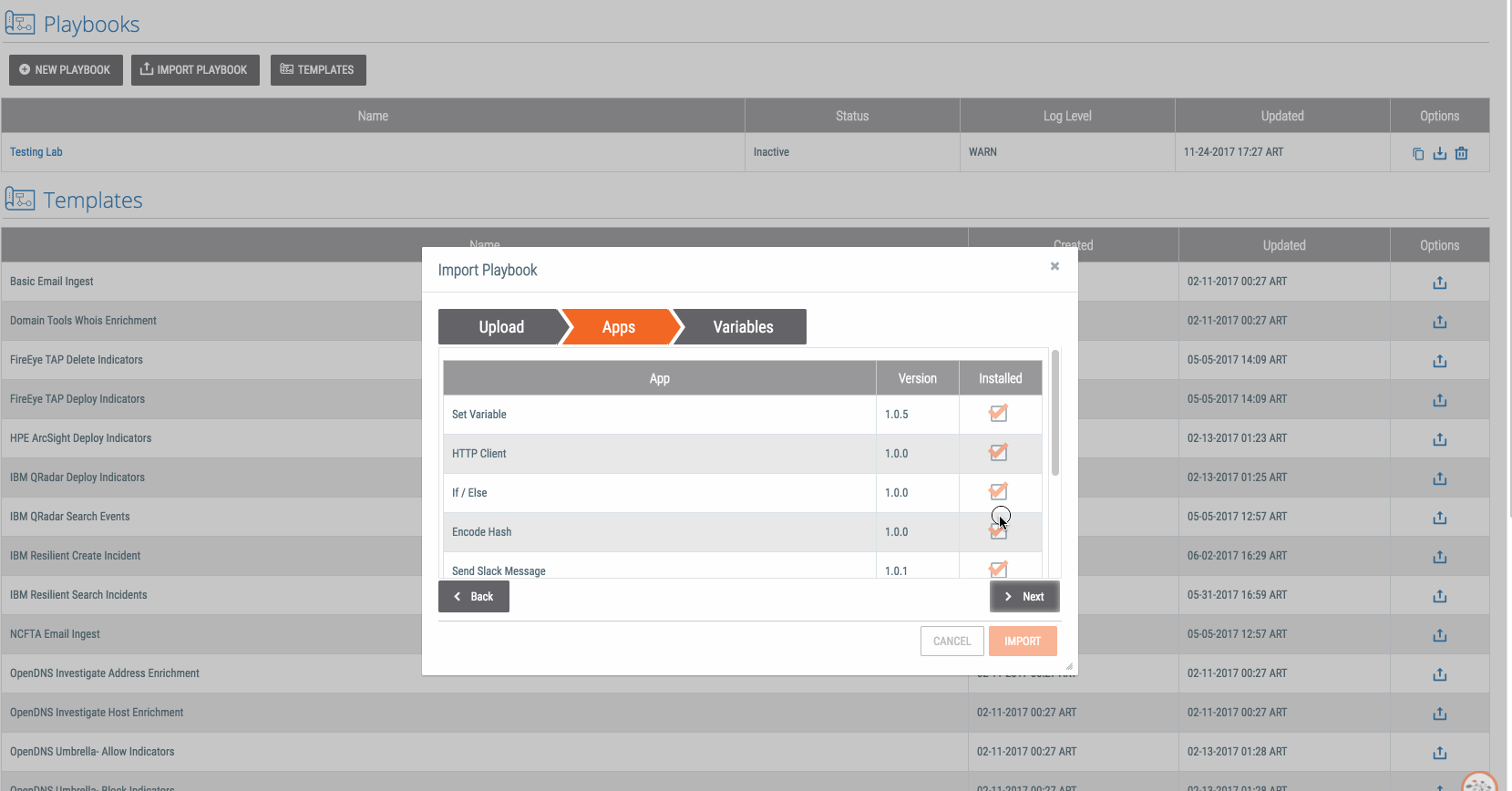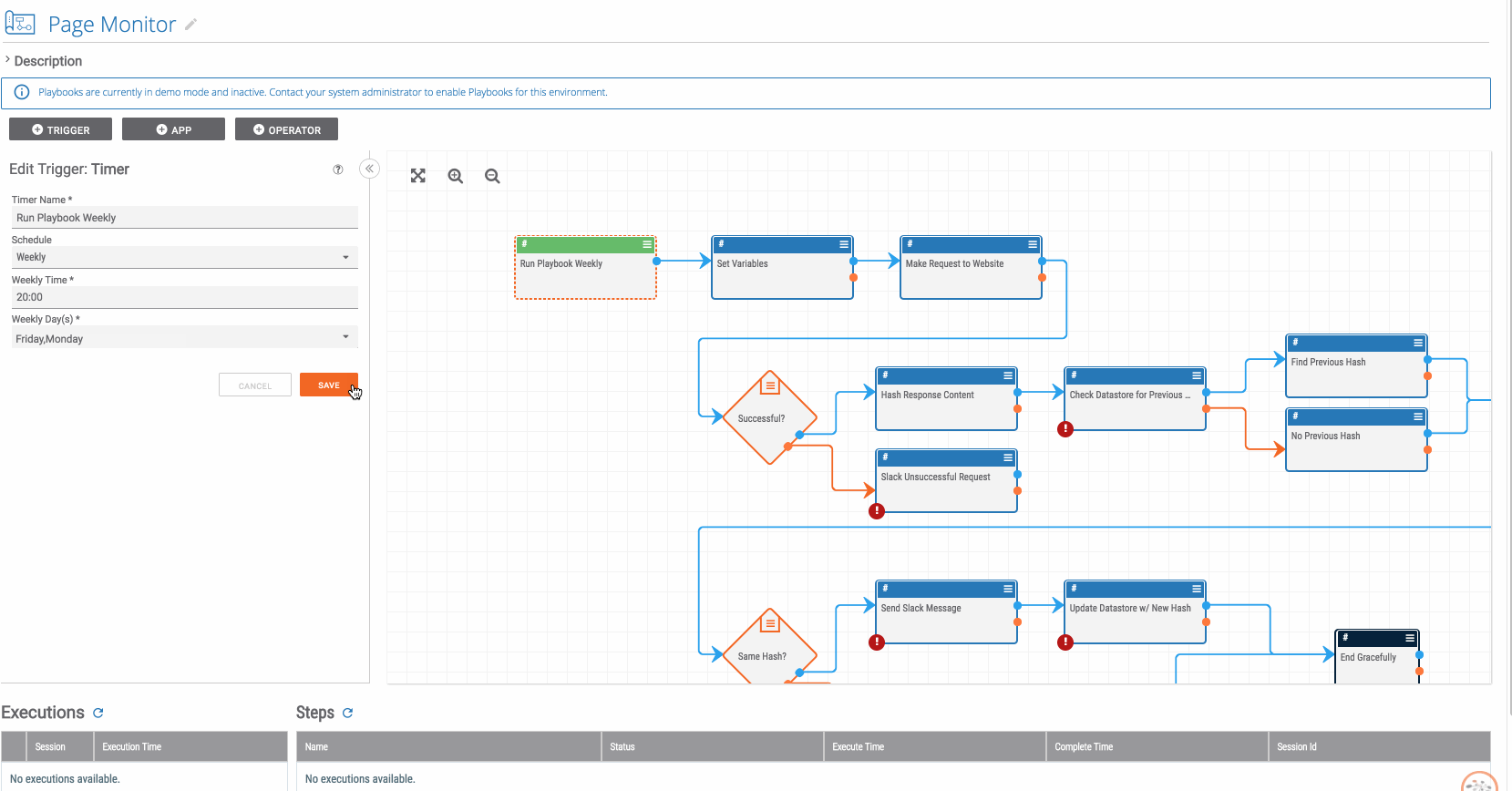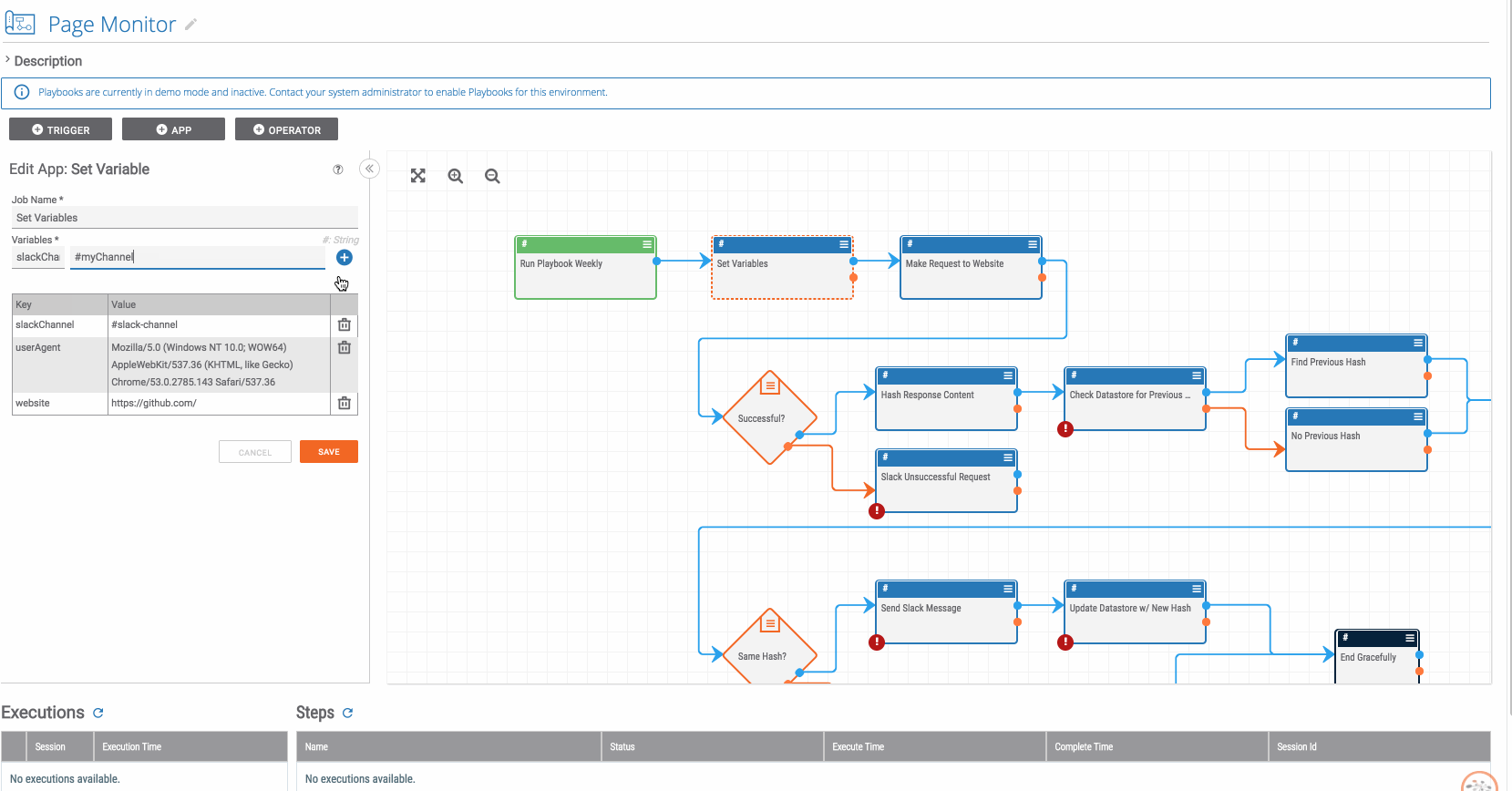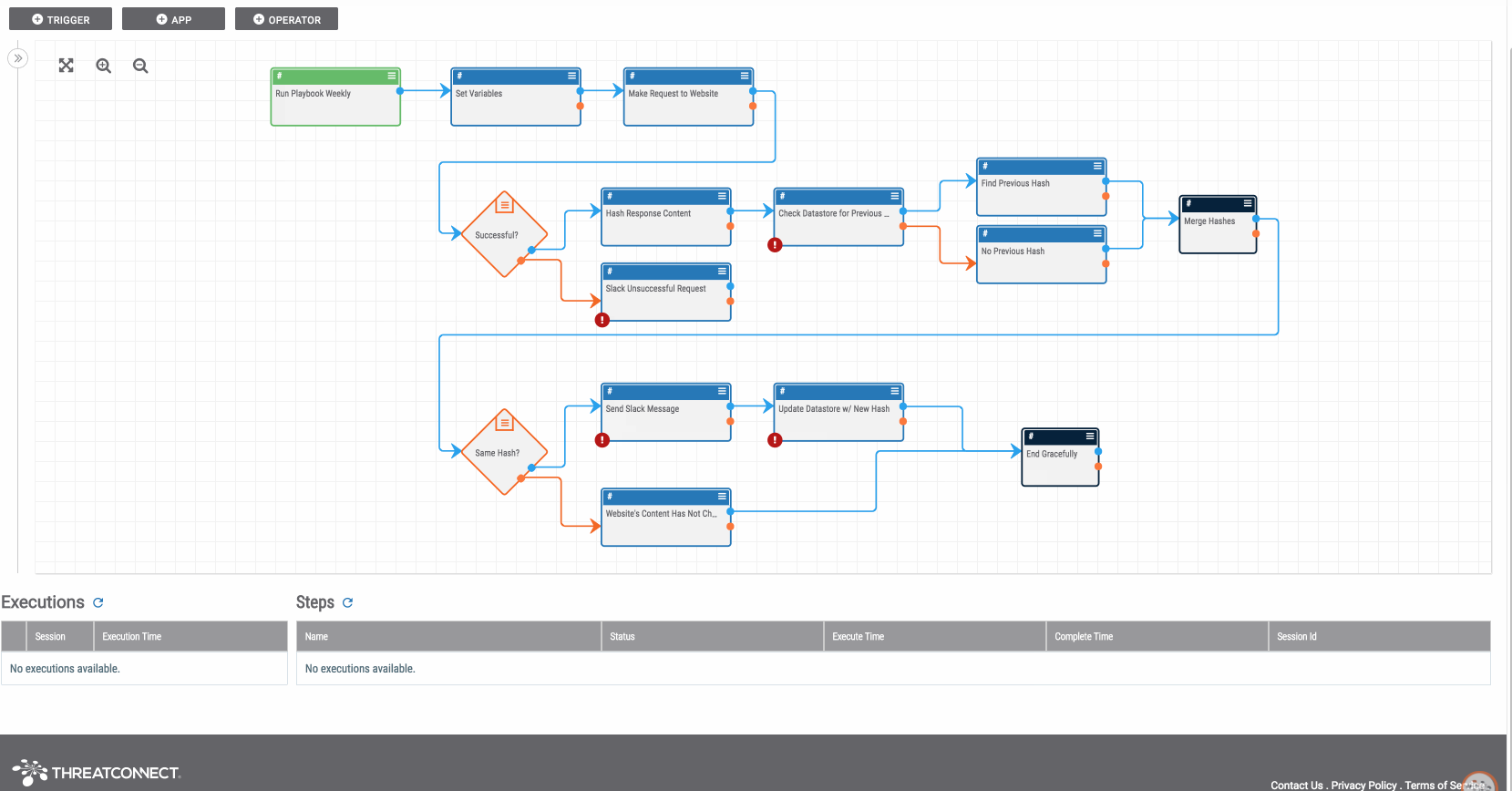
Playbook Fridays: Task Management
Playbook Fridays: Task Management Simulate a task in ThreatConnect which can be modified to recur daily, weekly, or monthly ThreatConnect developed the Playbooks capability to help analysts automate time consuming and repetitive tasks so they can focus on what is most important. And in many cases, to ensure the analysis process can occur consistently and […]
ThreatConnect Provides a Report on Healthcare and Medical Industry Threats
Learn about the threats and how to protect your healthcare organization Summary Medical and health organizations, which include organizations operating in the pharmaceutical sector, face a variety of threats that are inherent to the services they provide and the data they safeguard. Within medical and health verticals the risks associated with compromise are often significantly […]
Best Practices for Dashboards in Cybersecurity and Threat Intelligence
Explained Using New ThreatConnect Dashboards There’s no shortage of “dashboards” available in the software world. Walking the floor at any major industry event, it’s hard to miss the hordes of vendors touting their wares by showcasing line graphs, fancy animations, and (shudder) pie charts on big screen displays designed to shock and awe attendees into […]
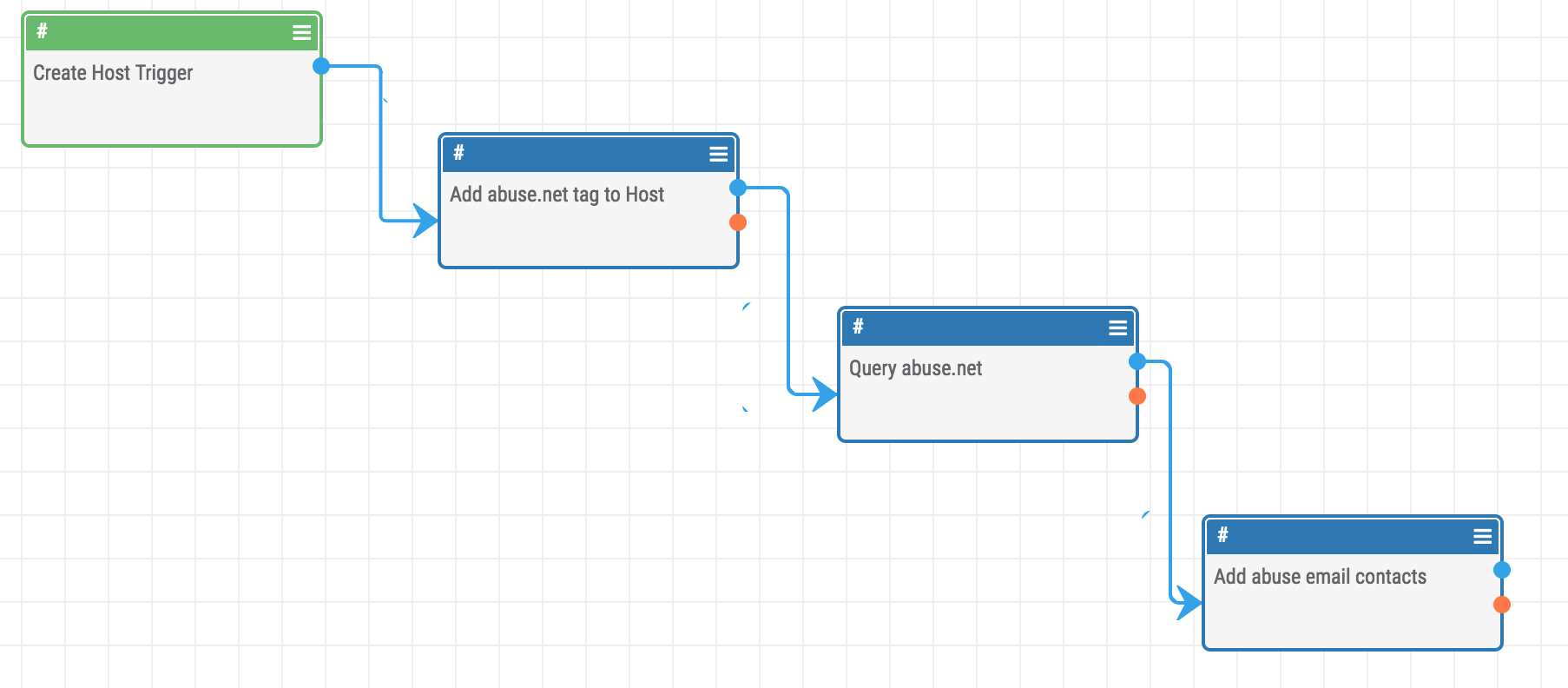
Playbook Fridays: How to Query Abuse.net with Playbooks
Query abuse.net for abuse contacts registered to a domain ThreatConnect developed the Playbooks capability to help analysts automate time consuming and repetitive tasks so they can focus on what is most important. You can also communicate with third-party services to trigger events outside of ThreatConnect. Why Was the Playbook Created? With the massive amount of […]
DNC Association Does Not Compute
Joining the cyber community to conduct independent analysis of the DNC Hack Recently, an article purported that the Democratic National Committee (DNC) turned down requests from FBI forensic units to look at its server and instead opted to use ThreatConnect and two other cyber security firms. While we cannot speak to the veracity of the […]
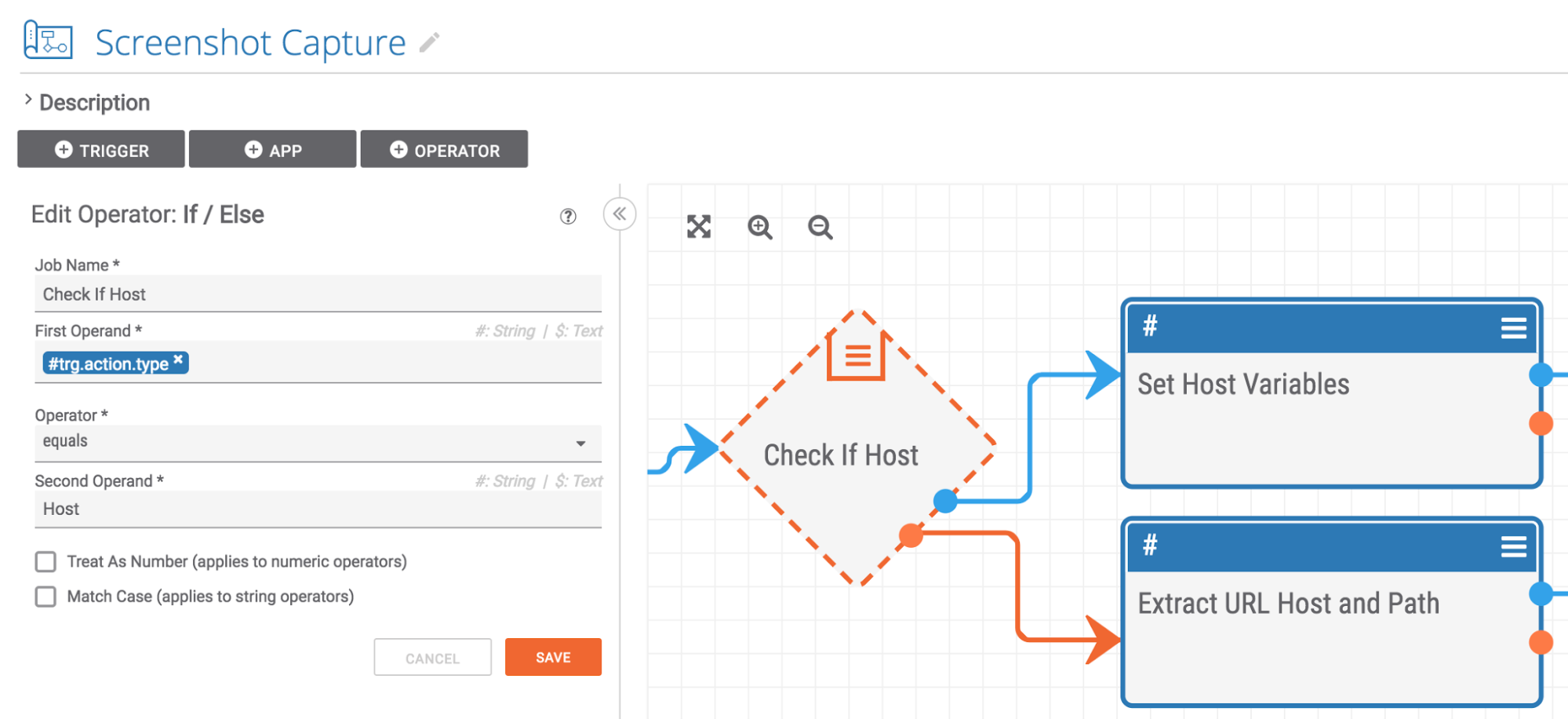
Playbook Fridays: Taking Screenshots with a Playbook
Playbook Fridays: Screenshot Capture Playbook ThreatConnect developed the Playbooks capability to help analysts automate time consuming and repetitive tasks so they can focus on what is most important. You can also communicate with third-party services to trigger events outside of ThreatConnect. Why was this Playbook created? When analyzing a phishing page, keeping a screenshot as […]
