
Read insights, thought leadership, and platform updates.
No Blogs Match Your Results
Please try again or contact marketing@threatconnect.com for more information on our blogs.

The Best Tools to Keep your Remote Security Team on the Same Page
Here at Polarity, we’re a remote-first team, meaning our culture and infrastructure is built around remote work – it’s part of our identity as an organization. If you’re now working from home for an organization that typically works in an office, you’ll find yourself less prepared for the “new normal” of remote life that we’re collectively […]
7 Tips for Working from Home
Many of us are stuck at working from home due to COVID-19. These are very surreal times. For some of you (us), being at home trying to work might be a whole new world. Well, we’re here to help navigate these uncharted waters. A lot of ThreatConnectors have worked remotely for years, so we went […]
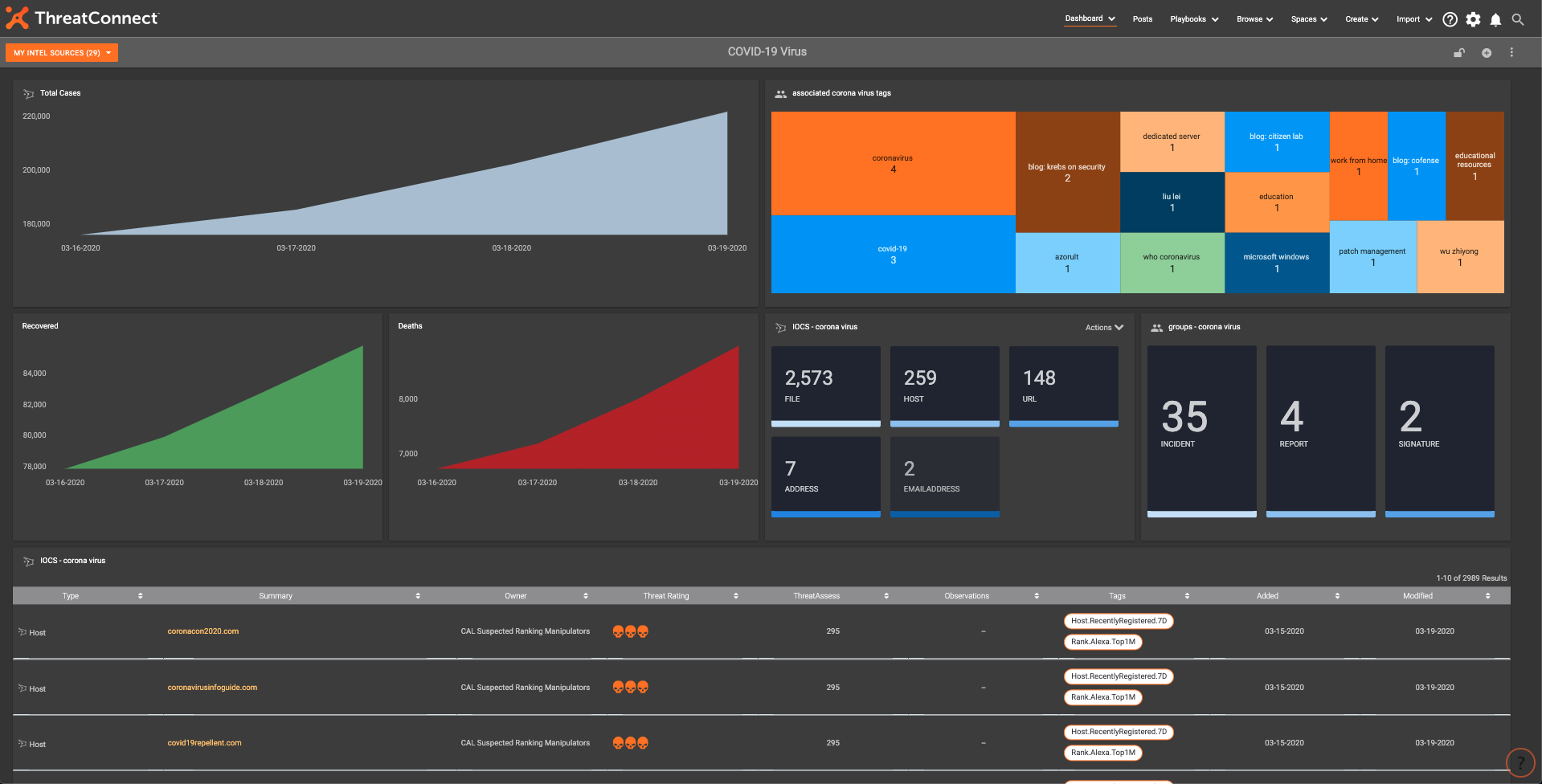
Special Playbook Fridays: COVID-19 Dashboard, Metrics, and Search
We’ve got options for how you can track activity related to Coronavirus / COVID-19 in the ThreatConnect Platform: 1. New System Dashboard – COVID-19 Related Activity The ThreatConnect Research Team has created the ‘COVID-19-Related Activity Dashboard’, which provides a single location to view consolidated, relevant intelligence from across various sources where threat actors are leveraging […]
Automation Anxiety? Don’t Worry.
More efficient processes. Better staff utilization. Increased documentation of processes. These are just a few of the benefits of automation, yet organizations may be slow to adopt automation technologies due to a fear of the unknown. The thought of automating some of their most critical processes does initially cause anxiety for some, but if I […]
Playbook Fridays: ATT&CK Tag Framework
This Component creates a uniform structure for ATT&CK tags which can then be leveraged to create TQL queries, dashboards, or even newer Playbooks. And, since this is a Component, it can be added to any Playbook. This component can be used with any 3rd party intel which brings in ATT&CK data It only requires a […]

Get Immediate Awareness of Malware with the Polarity-Cybereason Integration
With increasing speed and ferocity, Cyber Criminals are evolving their tactics and tools to target and hack even the most protected environments. Cybersecurity teams are struggling to efficiently detect new threats in this landscape, making endpoint protection systems even more vital. In order to keep up with this ever-present challenge, cybersecurity teams must rely on […]
Playbook Fridays: dan.me TOR Full List with Details
This Playbook gets the listing of TOR nodes from dan.me website and parses all of the information into ThreatConnect for consumption. TOR is often used by malicious actors to conceal their identity and operate anonymously. Tracking these along with their respective ThreatAssess scores and organization specific observations will help analysts spot potential threats. https://github.com/torproject/torspec/blob/main/dir-spec.txt Details […]

Polarity User Tips: IP Social Distancing
In the opening act of 2020, we’re busier than ever. Building on 2019’s Productivity: Part I, we want to introduce 4 additional productivity hacks to give you back even more of your time this year. Give these tips a read and take the opportunity to implement some new habits – you might be surprised by the […]

The hardest part of remote work – and how to tackle it – Part II
Those of us who can address the inherent challenges of remote work can thrive despite them. By implementing some simple tactics, we can learn to be high-performers as well as satisfied employees in a remote setting. To build on Part I, here are some tactics to address the challenges of remote work from the organizational level. […]

The hardest part of remote work – and how to tackle it – Part I
It’s safe to say that the honeymoon phase of remote work is coming to a close. With more and more teams fully dispersing, the stock photo fantasy of reclining on a white sand beach, laptop and piña colada in hand, has started to dissipate as the reality of remote work comes into wider recognition. Sure, there […]
Introducing ThreatConnect’s New Learning Portal
New courses and our knowledge base are combined in one place We are very excited to introduce our new Learning Portal! Accessible to all of our registered users, this portal not only houses the courses that are available to users, but is also the new home of our Knowledge Base. The Knowledge Base is where you […]

Automatically Access Key Intelligence Reports with the Polarity-Flashpoint Integration
More and more sensitive information ends up on illicit online communities every day, and trying to comprehend all of that information and turn it into actionable intelligence for your organization is difficult. Flashpoint provides Business Risk Intelligence (BRI) to empower organizations worldwide to combat threats and adversaries. Fueled by a combination of sophisticated technology, advanced data collections, […]
