
Read insights, thought leadership, and platform updates.
No Blogs Match Your Results
Please try again or contact marketing@threatconnect.com for more information on our blogs.
ThreatConnect’s Developer Partner Program: We Meme Business
Integrations have always been at the heart of ThreatConnect’s product and company strategy. Never has that been more true than when we made the decision to move into the SOAR (security orchestration, automation, and response) market: integrations have become even more vital. A broad and open ecosystem of apps and integrations is crucial for the […]
How to Improve Collaboration with Security Teams and Technology using ThreatConnect
ThreatConnect is an intelligence-led, SOAR Platform. We bring a critically important solution to market for our clients as we combine our world-class Threat Intelligence Platform with SOAR under one banner. This ensures that intelligence feeds operations and operations informs intelligence for future actions, continually improving the time to detect and respond to threats. In our […]

Polarity User Tips: Reference Channels
Today’s post continues an ongoing series on Polarity User Tips. Data tells a story, Polarity helps you see it with Augmented Reality overlaying contextual information as you work, giving you the right data at the right time to make informed decisions and take action with speed. This guide explains how you can see the story […]
Playbook Fridays: DomainTools Iris Investigate Monitor
Welcome to ThreatConnect’s Playbook Fridays! We will continually publish posts featuring Playbooks (and sometimes Dashboards!) that can be built in the Platform. ThreatConnect developed the Playbooks capability to help analysts automate time consuming and repetitive tasks so they can focus on what is most important. And in many cases, to ensure the analysis process can […]
Improving Accuracy and Efficiency in Security Operations with ThreatConnect
ThreatConnect is the central nervous system for your entire security ecosystem. Our intelligence-driven Security Orchestration Automation and Response (SOAR) Platform is a place for your security team to work smarter, together. As a company, we are driving the evolution of security operations by delivering enriched, fortified, context-filled threat intelligence along with comprehensive analytics, seamless automation […]
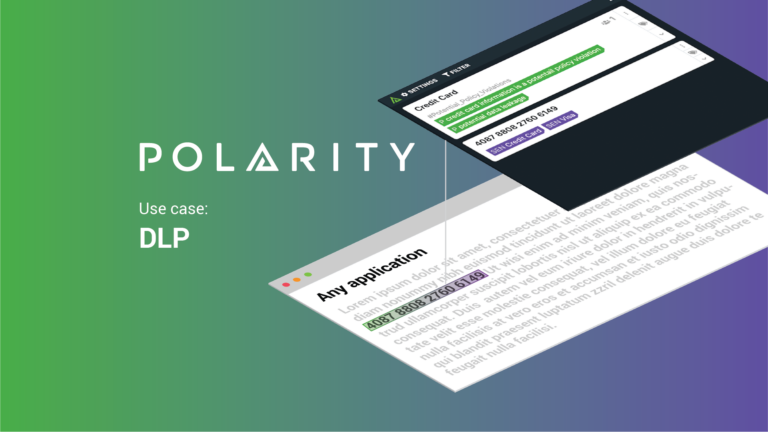
How Polarity can help Data Loss Prevention
Today’s post continues an ongoing series on Polarity Use Cases. With a solution that overlays on any screen you’re looking at, Polarity has as many use cases as you do tasks in your workflow. Using Polarity, you’ll be armed with data awareness and recall so you can make better decisions, faster. This example showcases our […]
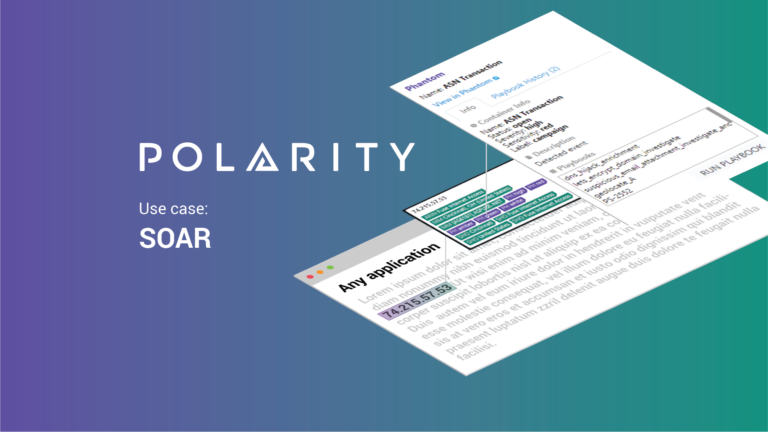
SOAR Higher with Polarity
Security Operations Automation & Response (SOAR) platforms are now widely deployed as a way to address an ever-increasing volume of attacks. From automating the response to phishing emails to more sophisticated playbooks, SOAR platforms are producing positive results. Still, security teams recognize that not everything can be automated, and even what can be addressed with […]

React Immediately to Insider Threats with the Polarity-Securonix Integration
Today’s post continues an ongoing series on Polarity Integrations. With over 100 powerful integrations, the Polarity Integrations Library allows users to connect Polarity to the tools they already use in their workflow, arming them with even better data awareness and recall. This example showcases our integration with Securonix. Insider threats are one of the fastest-growing risk […]
Playbook Fridays: Converting Apps
Welcome to ThreatConnect’s Playbook Fridays! We will continually publish posts featuring Playbooks (and sometimes Dashboards!) that can be built in the Platform. ThreatConnect developed the Playbooks capability to help analysts automate time consuming and repetitive tasks so they can focus on what is most important. And in many cases, to ensure the analysis process can […]
Build a Single Source of Truth
Gartner® defines a SOAR platform as ”security orchestration, automation and response technologies that enable organizations to collect security threats data and alerts from different sources, where incident analysis and triage can be performed leveraging a combination of human and machine power to help define, prioritize and drive standardized incident response activities according to a standard […]

Get Instantaneous Awareness of Threat Intelligence with the Polarity-Recorded Future Integration
Today’s post continues an ongoing series on Polarity Integrations. With over 100 powerful integrations, the Polarity Integrations Library allows users to connect Polarity to the tools they already use in their workflow, arming them with even better data awareness and recall. This example showcases our integration with Recorded Future. We are excited to announce our latest […]
Playbook Fridays: Automatically import and tag your RSS feed data with Covid-19 Tags
Welcome to ThreatConnect’s Playbook Fridays! We will continually publish posts featuring Playbooks (and sometimes Dashboards!) that can be built in the Platform. ThreatConnect developed the Playbooks capability to help analysts automate time consuming and repetitive tasks so they can focus on what is most important. And in many cases, to ensure the analysis process can […]
