
Read insights, thought leadership, and platform updates.
No Blogs Match Your Results
Please try again or contact marketing@threatconnect.com for more information on our blogs.

SolarWinds Hack Spurs Interest In Risk-Based Threat Hunting
The SolarWinds hack of the software supply chain, which is considered the most significant and far-reaching cyber espionage operation targeting the U.S. government to date, has elevated the government’s interest in risk-based threat hunting. The Cybersecurity and Infrastructure Security Agency (CISA) last month issued a request for information on industry’s ability to support a Threat […]
Threat Hunting Use Case (Video): Sunburst Malware
The SolarWinds attack, disclosed by security firm FireEye and Microsoft in December, may have breached as many as 18,000 government and private sector organizations. It has been characterized as the largest and most sophisticated cyber attack the world has ever seen, and was made possible by the Sunburst malware the attackers implanted in legitimate digitally […]
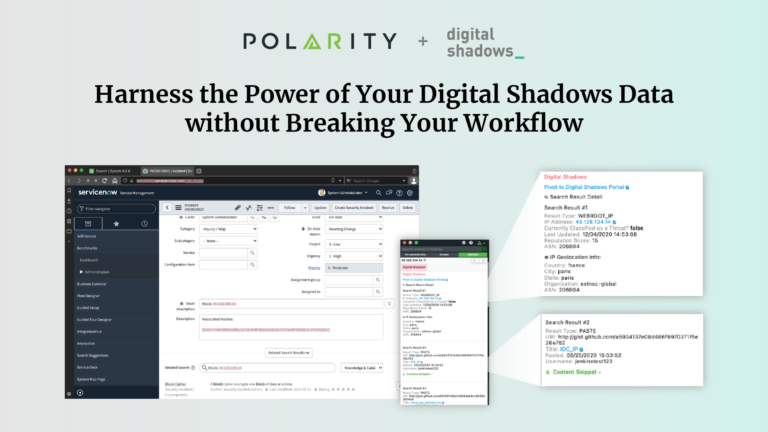
Harness the Power of Your Digital Shadows Data without Breaking Your Workflow
Today’s post continues an ongoing series on Polarity Integrations. Data tells a story, Polarity helps you see it with Augmented Reality overlaying contextual information from the applications you use every day, no glasses or goggles required. With over 100 powerful integrations, Polarity’s open-source Integrations Library arms you with the right data at the right time […]
Improving Upon The FAIR Standard’s Time-to-Value
The Factor Analysis of Information Risk (FAIR) is the de facto standard quantitative model for information security and operational risk. And while FAIR continues to have a positive impact on how security professionals think about and communicate risk, the upfront costs associated with starting a FAIR program and the time it takes to realize actual […]
ThreatConnect and Malwarebytes Nebula: Make Your Cloud-Based EDR SOAR
ThreatConnect is pleased to deliver a Playbook app for joint customers to leverage Malwarebytes Nebula. Malwarebytes Nebula is a cloud-hosted security operations platform that allows you to manage control of any malware or ransomware incident. With this Playbook App, you can take immediate action to investigate, stop, and remediate potential threats at the endpoint based […]
Communicating Risk, Threat, Response to the C-Suite & Board
The Wannacry ransomware attack made 2017 one of the worst years for cybersecurity in recent memory, incapacitating hundreds of thousands of computers in 150 countries and causing billions of dollars in financial losses. There was also a silver lining: Suddenly, senior business executives and boards of directors began asking detailed questions about how much cyber […]

Key Functionalities of a Modern Cyber Threat Intelligence Program
More and more organizations, both large and small, are beginning to realize the benefits of creating a cyber threat intelligence (CTI) program. In fact, 85 percent of the organizations surveyed in the 2021 SANS Cyber Threat Intelligence Survey said they produce or consume CTI — a 7 percent increase over last year. But a modern […]
ThreatConnect and ANY.RUN – Better Malware Analysis
ThreatConnect and ANY.RUN have partnered to deliver a Playbook App for joint customers to leverage. With the addition of this Playbook App, you will be able to submit files to ANY.RUN for sandboxing and retrieve results automatically via Playbooks. This all leads to more informed decision making and more efficient remediation of malicious files through […]
ThreatConnect and Slack: Streamline Investigative Team Collaboration
ThreatConnect has revamped our existing integration with Slack by leveraging their latest APIs and Authentication, doing this allows us to include a ton more functionality. With Playbooks, you can automatically keep team members informed, get instant updates with notifications or escalations, and create channels as part of investigations. By automating this process, you turn your […]

Polarity in Action: Event Triage Use Case
Today’s post continues an ongoing series on Polarity in Action, demonstrating how Polarity helps you to see the story in your data without sacrificing thoroughness or speed. In today’s video, Polarity’s resident SOC expert, Terry McGraw, walks through an event triage use case, showcasing how Polarity provides analysts with all of the data they need, […]
CrimsonIAS: Listening for an 3v1l User
Executive Summary CrimsonIAS is a Delphi-written backdoor dating back to at least 2017 that enables operators to run command line tools, exfiltrate files, and upload files to the infected machine. CrimsonIAS is notable as it listens for incoming connections only; making it different from typical Windows backdoors that beacons out. The characteristics found in CrimsonIAS’s […]
TIP & SOAR: Creating Increased Capability For Less Mature Teams
Building a threat intelligence-led security program with security orchestration, automation, and response (SOAR) capabilities helps to advance your program and gives your company or agency a fighting chance to defeat these advanced and evolving threats. Businesses and organizations with less mature cybersecurity programs tend to be in a constant state of reacting to threats, vulnerabilities, […]
