
Read insights, thought leadership, and platform updates.
No Blogs Match Your Results
Please try again or contact marketing@threatconnect.com for more information on our blogs.
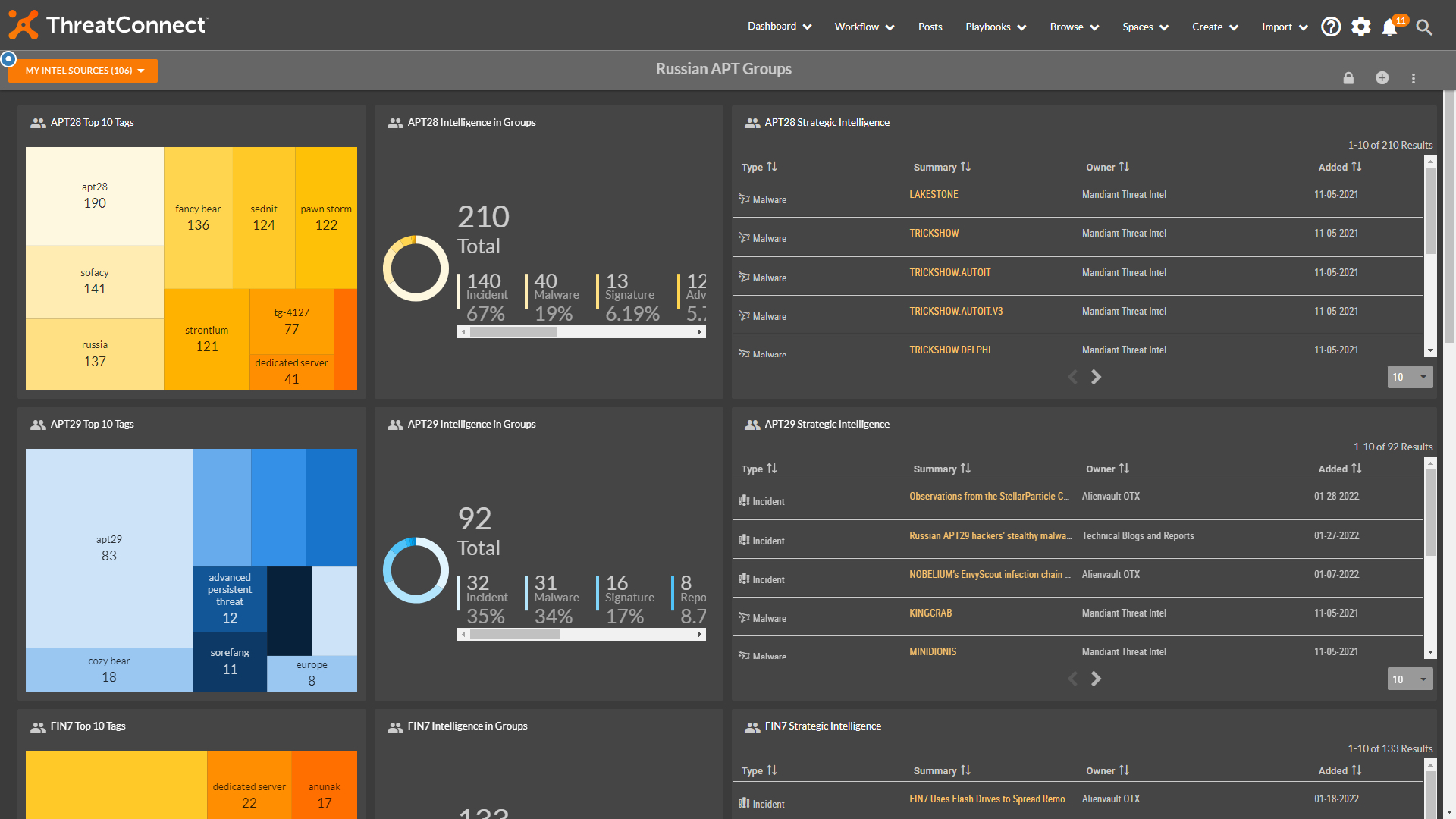
How To: Russian Threat Actor Dashboards
Since our previous threat intelligence dashboards blog on how to get more visibility over the threat landscape associated with the Russian-Ukraine war, the situation unfortunately hasn’t been resolved, and the U.S. Government has recently issued statements warning of potential cyberattacks by Russia against the United States ThreatConnect has continued to look at how we can […]

Every Type of SOC Needs a SOAR
Many organizations have a Security Operations Center (SOC). It may not be one that has a large room full of analysts, engineers, threat hunters, and incident responders, with a wall of monitors providing a heads-up display for the staff. It may be a couple of staff working remotely augmented by a SOC as a […]

To Code Or Not To Code
To code or not to code? That is the question that many security teams grapple with when attempting to solve a specific problem or introduce a new capability. While TIP and SOAR platforms like ThreatConnect offer many out of the box applications and integrations to support threat intelligence and security operations teams, there may come […]
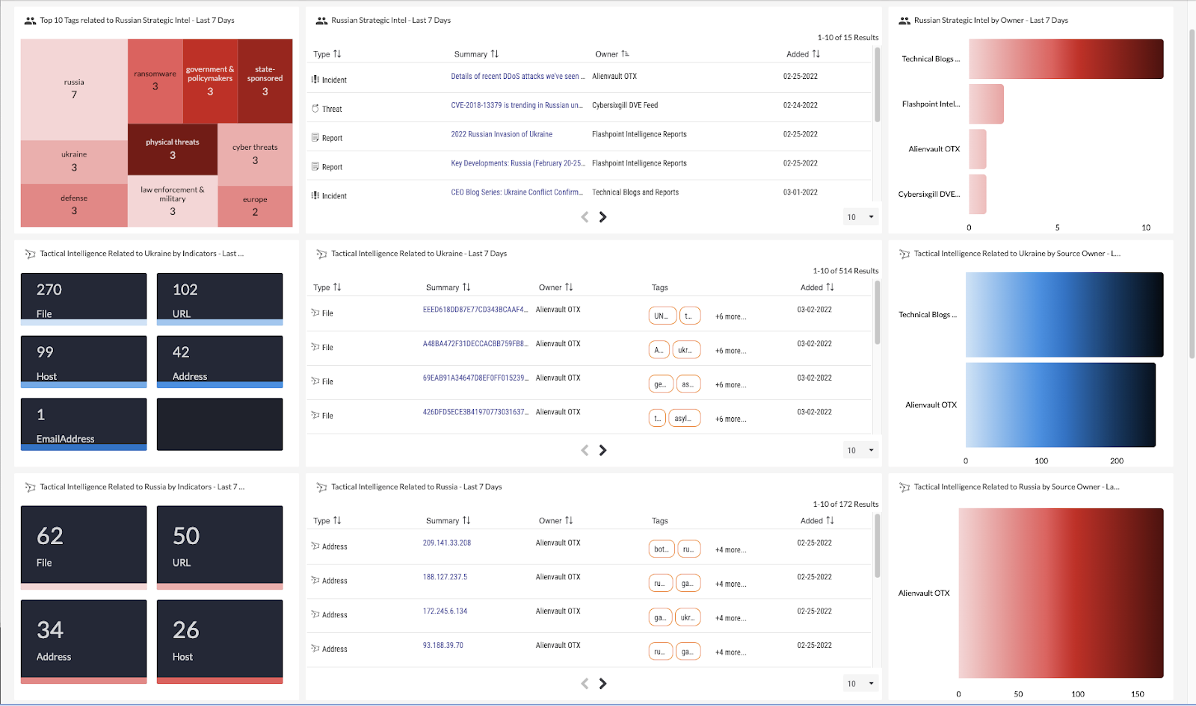
How to: Dashboards for Ukraine Conflict Threat Intelligence
The ThreatConnect Platform is optimized for providing organizations the ability to create a custom dashboard for pulling together real-time, topical threat intelligence into a single view. The current situation in Ukraine has led organizations to ask – “how should I operationalize our intelligence related to this situation so we can have a better perspective on […]

Let’s talk about CFOs and Cyber Risk
If you have read my previous three blogs in this ‘Let’s talk’ series, you’ll know that we’ve talked about our conversations with CISOs and CIO – and now it’s time to turn our attention to Chief Financial Officers (CFOs). The CFO’s job is really important. They’re the ones who determine financial strategy and budgets. Usually, […]
Software and Seinfeld with ThreatConnect’s CAL™
It’s been awhile since the CAL Analytics team has updated the world on our latest creations. Right before the holidays, we released our CAL 2.11 update (some months after our CAL 2.10 update). Both of these major releases shared a common theme: getting you more data. Now that people are returning to work and facing […]
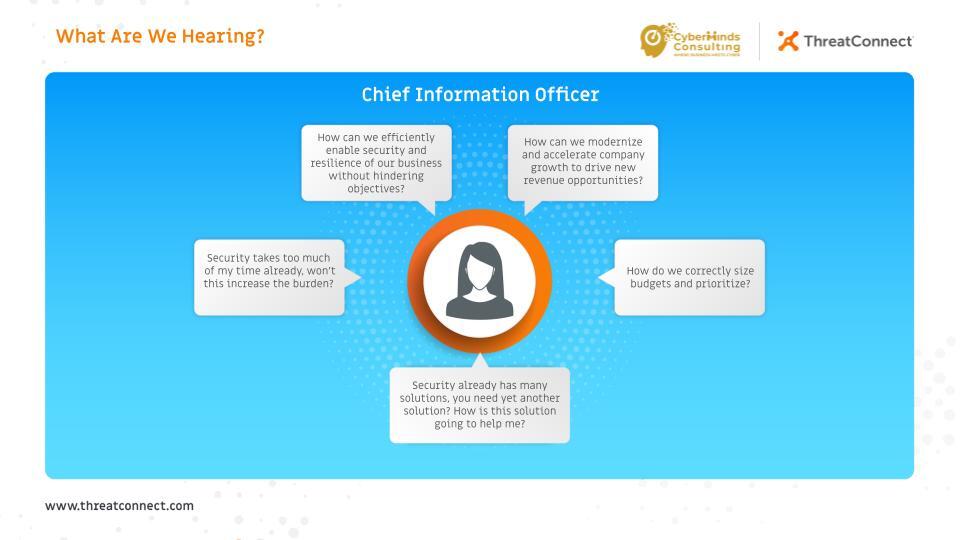
Let’s talk about CIOs and Cyber Risk
In our previous blog, we looked at how cyber risk quantification (CRQ) can help CISOs and their teams to address some of the most pressing cybersecurity issues today. But change requires buy-in, so cross-functional collaboration and communication are vital. In this blog, we are going to look further into the concerns of their fellow C-suite […]
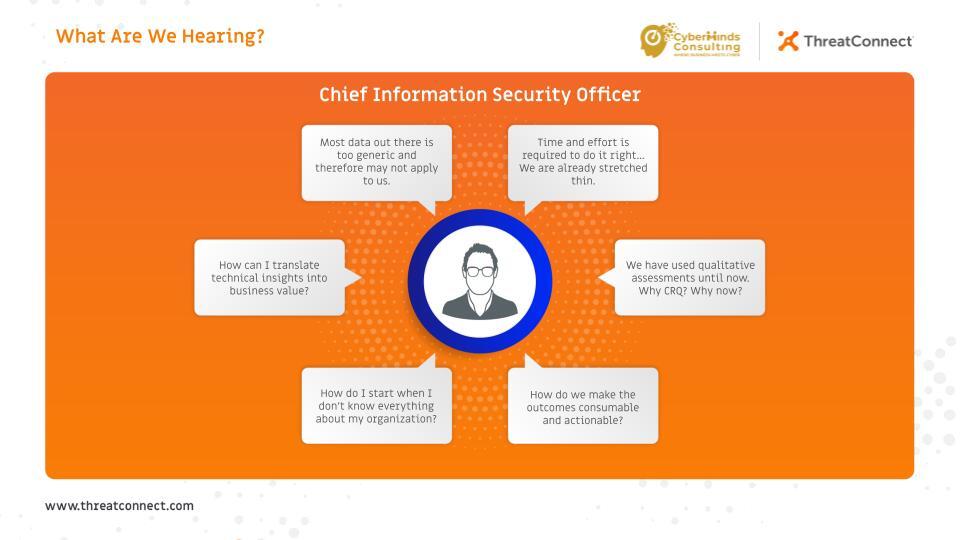
Let’s Talk About CISOs and Cyber Risk Quantification
Chief Information Security Officers (CISOs) serve a critical role in protecting their business from internal and external threats. They need to design and implement the right resources to mitigate growing digital security risks and maintain regulatory compliance. This requires an understanding of the current and future security risks to business operations that could hinder the […]

It’s Time to Make Crypto Assets First-Class Citizens in Threat Intelligence
As the world evolves from Web 2.0 to Web 3.0 – think decentralized protocols for crypto assets, identities, and compute-services leveraging blockchain technology – cyber threat teams must evolve their understanding of the technology at play to stay ahead of threats. That’s easier said than done. Some of the challenges that security teams face are […]

4 Key Drivers Accelerating Cyber Risk Quantification
If you’ve attended any of our webinars on Cyber Risk Quantification (CRQ) in recent months, you’ll know that this is a topic I love talking about! You’re either thinking this is not true, or I’m paid to say that right…? I know. Well, the truth is, I like problem-solving and in the cyber world – […]

ThreatConnect’s Top 5 Webinars In 2021
A survey by the Independent revealed that a typical British household will watch a staggering 62 hours of TV, shows, and movies over the Holiday period between December 20th and January 2nd! But I’m sure with the recent lockdowns and travel restrictions, most of us have already looked through everything on Netflix and binged our […]

The UK’s Cyber Strategy 2022: The 5 Pillars
This past year has seen ruthless cyber attacks on individuals, businesses and nation-states. Colonial Pipeline, Ireland’s Health Service Executive (HSE), JBS, and Florida’s Water Supply are just some examples of gaps in securing critical infrastructure. It’s time for governments to be drivers of change and take steps to counter growing threats. The United Kingdom is […]
