
Read insights, thought leadership, and platform updates.
No Blogs Match Your Results
Please try again or contact marketing@threatconnect.com for more information on our blogs.

Lessons in Communicating Cyber Risk to the Board and Business Leaders
Business leaders are not always technically-focused, so it is important for security teams to examine how they are communicating risk to leadership and ensure those methods are being effectively received. Overly technical or qualitative methods run the risk of the message getting lost or distorted so well-run security programs are evolving their approach to measuring […]

Tactical Threat Hunting – What Is It And How Do You Start?
Alert overload takes the security team’s attention away from many other essential aspects of keeping a healthy cyber ecosystem. Many teams cannot define and implement a threat hunting program because of resource shortages or they simply lack the know-how. Complexity in defensive control integrations is also a roadblock, and the lack of integrated workflow makes […]
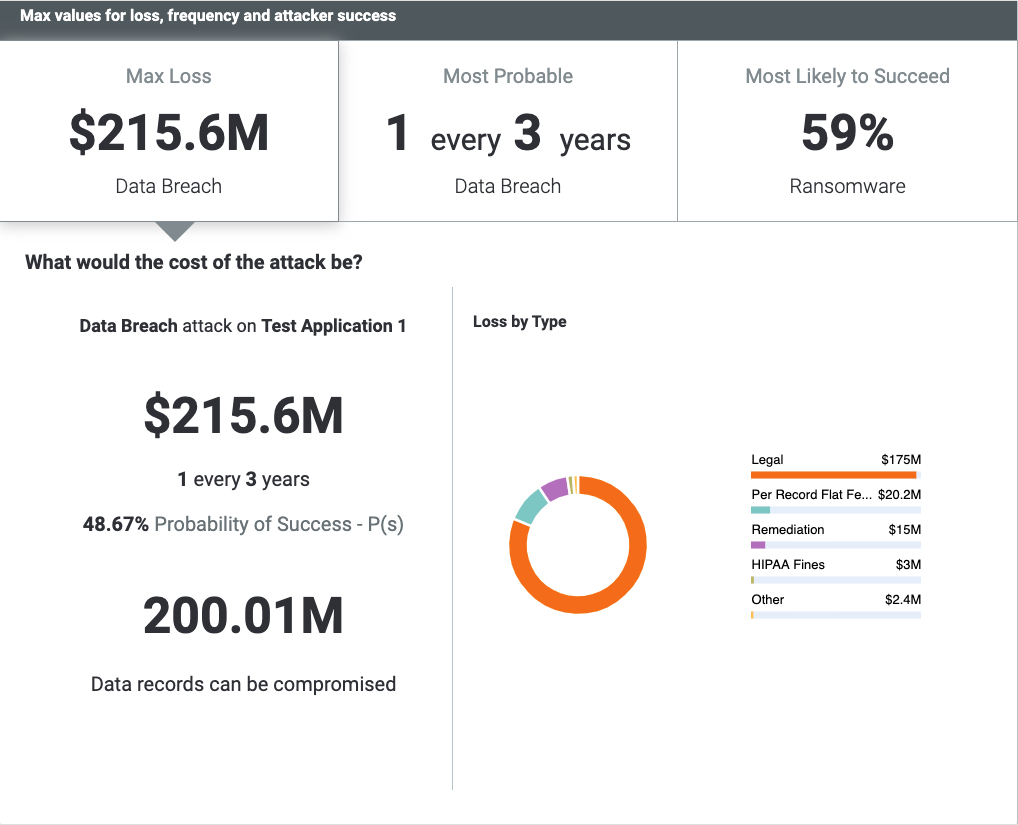
ThreatConnect RQ 6.3 – Making FAIR Even Easier
We’re excited to announce the release of ThreatConnect Risk Quantifier (RQ) version 6.3! This update is now available and provides a number of enhancements that make cyber risk quantification (CRQ) even easier to implement and use, particularly focusing on making the FAIR analysis faster, with less effort. Pre-populated FAIR Loss Magnitude RQ 6.3 now includes […]

The 3 Key Elements of an Effective Cyber Threat Intelligence Program
There is often a conversational disconnect between a cybersecurity team and other departments of an organization. But as cyber is becoming an increasingly large part of business strategy, cybersecurity and threat intelligence must speak the language of business. Cyber Threat Intelligence (CTI) programs are crucial in the way they protect an organization from threats. Businesses […]

How To Select The Best SOAR Platform For Your Organization
Information overload is a common challenge facing Security Operations Centers (SOCs). Security analysts are bombarded with hundreds of alerts of potential security events. Sifting through and prioritizing the most important events can take weeks, months, or even longer. Without the insight of threat intelligence and orchestrated processes to make sense of all the data coming […]

3 Strategies for Dealing With the Widening Cybersecurity Skills Gap
Many Security Operations Center (SOC) teams are under immense pressure! They’re facing many different challenges and while cybersecurity spending is increasing, investment isn’t always placed where it is needed most (and this is a contributing factor). Creating and maintaining a top-performing SOC team takes time and money. The average cost for employing and maintaining an […]

The Power of Combining Outside-In and Inside-Out Cyber Risk Quantification
ThreatConnect is excited about the partnership with SecurityScorecard for their Cyber Risk Quantification (CRQ) solution powered by ThreatConnect Risk Quantifier (RQ). Applying ThreatConnect’s statistical and machine learning algorithms to the Security Scorecard data enables customers to easily understand their risk, both external and internal, and more importantly prioritize which factors should be improved based on […]

Why Build A Threat Library?
Cyber threat actors are using more sophisticated tools, techniques, and procedures that are outpacing traditional security solutions. As a result, things such as intrusion detection systems, anti-virus programs, and conventional incident response methodologies by themselves are no longer sufficient to close the widening gap between security and the current threat landscape. Analysts are over-worked and […]

4 Actions To Help Protect Your Organization From Malicious Russian Cyber Activity
The Russian invasion of Ukraine has escalated past traditional warfare. The impact and implications of the attack will be felt far past the region’s borders. The U.S. Government has recently issued statements warning of potential cyberattacks by Russia against the United States. Organizations need to re-evaluate their security measures and should be on the defense […]

The Importance of Assessing & Communicating the Financial Impact of Cyber Risks
Just as a captain would navigate their ship across vast oceans, it’s the responsibility of business leaders to determine the direction of the overall corporate strategy. To do this effectively, they need to understand their environment and the conditions that may hinder them along the way. Unfortunately, things aren’t always smooth sailing in real […]

Supercharge Your Security Operations With ThreatConnect 6.5
Security operations teams are super busy and it’s not getting any easier. Analysts need to be able to get more done in their day by working smarter, faster, and better. We get it and we hear you! In this release of ThreatConnect 6.5, we have supercharged the ThreatConnect Platform with some exciting updates: Threat Intel, […]
A Long Way in 11 Years: I’m Passing the Torch at ThreatConnect
After 11 years the time has come for me to pass the torch as ThreatConnect’s CEO. This decision, although hard, is one that I make with great pride for how far the company has come from founding through startup, to what it is today. I’m so proud of the advancements we’ve driven in cybersecurity, proud […]
