Posted
The Problem: When “Zero-Day” Means Everything and Nothing
CTI Teams’ inbox and feeds overflow daily with mentions of “zero-day” vulnerabilities. Blogs, reports, vendor advisories, and social media all promise the next catastrophic exploit. But behind the scary headlines, there is a lot of noise, generic chatter, academic discussions, or even misplaced buzzwords.
Meanwhile, attackers aren’t waiting. They’re moving fast to weaponize vulnerabilities that matter. And your team is stuck sifting through OSINT noise, trying to separate hype from signal.
This results in analysts chasing false leads, response teams struggling to prioritize the right patches, and CISOs are left asking the question no leader wants to hear: “Are we actually reducing risk, or just reading reports?”
The Struggle: Drowning in Vulnerability Reporting
The challenge isn’t a lack of data, it’s too much of it. Every day, there are advisories, blogs, and threat intel feeds that generate a flood of unstructured reporting on vulnerabilities. Buried in that flood are the handful of zero-day and actively exploited vulnerabilities that truly matter, but they’re mixed in with commentary, hype, and duplicates. Analysts spend valuable time parsing text-heavy documents that provide little clarity on what’s being actively weaponized in the wild.
Many CTI teams leveraging ThreatConnect features focus on Vulnerabilities:
- Zero-Day Focus: Across industries, CTI teams have built ThreatConnect Intelligence Requirements (IRs) that overwhelmingly emphasize zero-day vulnerabilities compared to other topics.
- Executive Concern: Priority Intelligence Requirements (PIRs) reflect an urgent need for decision-makers to know which zero-days and exploited vulnerabilities pose the greatest risk to their business right now.
- Granular Questions: At the analyst level, IRs dig deeper, asking which industries are impacted, which threat actors are exploiting these vulnerabilities, and what tactics, techniques, and procedures (TTPs) they’re using.
In short, businesses need clarity on risk, analysts need context, and both are drowning in unstructured noise about vulnerabilities.
ThreatConnect AI Separates Signal from Noise
Enter ThreatConnect’s AI Exploited-Vulnerability Analyzer, powered by the ThreatConnect CAL™ Doc Analysis Service. Instead of forcing analysts to wade through unstructured noise, it highlights the vulnerabilities that are actively being weaponized. This capability is a key part of ThreatConnect’s broader vulnerability management strategy. Alongside this capability, ThreatConnect has recently introduced a unified vulnerability view that consolidates knowledge from across feeds into a single interface, making it faster and easier to research any Common Vulnerabilities and Exposures (CVE). Together, these improvements ensure that critical vulnerability intelligence is not only comprehensive but also accessible in one place, helping analysts move from discovery to action with confidence.
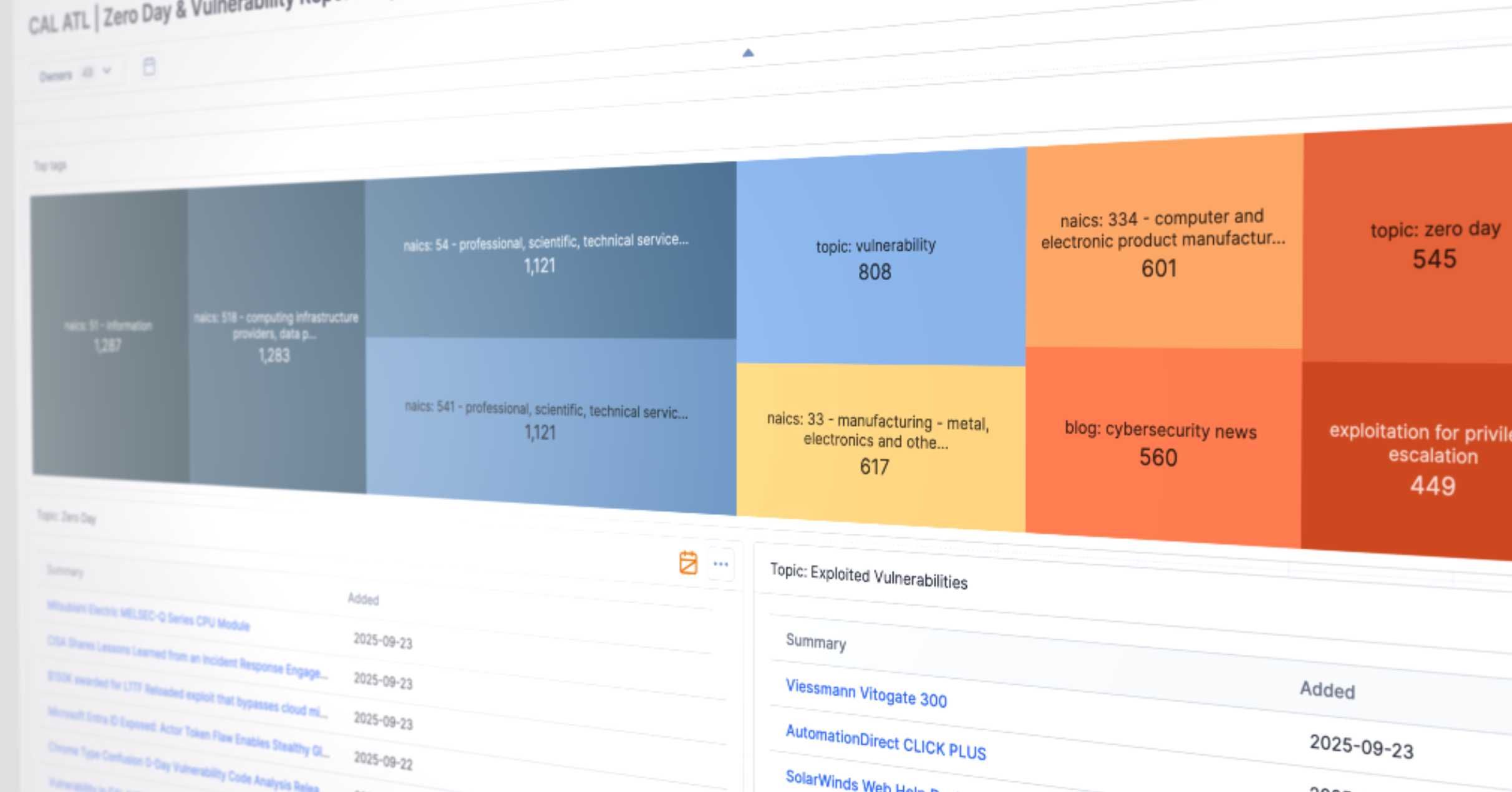
Only 5.8% of all CAL ATL OSINT articles were found to be actionable vulnerability intelligence
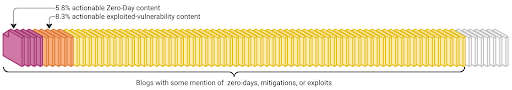
The scale of the problem is real. In just a three-month period, CAL™ Automated Threat Library (ATL) processed more than 8,000 OSINT reports. 86% contained some mention of vulnerabilities, zero-days, mitigations, or exploits. But AI Exploited-Vulnerability Analyzer determined that only 5.8% were actionable Zero-Day content, and 8.3% was actionable exploited-vulnerability content.
Without the utilization of ThreatConnect’s AI Exploited Vulnerability Analyzer, analysts are forced to sift through thousands of references to ‘risks’–but they are inapplicable risks that translate into inactionable intel. With ThreatConnect AI, the load is prioritized to the top 14.1% of reports that are the most relevant and actionable.
That shift isn’t just clarity; it’s hundreds of analyst hours saved. At an average of 2–3 minutes per report, reviewing all 8,000 reports could consume more than 400 hours. By surfacing only the 14.1% that truly matter, and further condensing them with vulnerability-specific summaries, ThreatConnect AI ensures analysts spend their time on the highest-risk issues, not buried in noise.
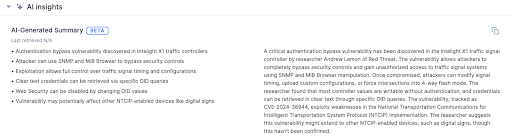
The payoff is twofold: teams reclaim time, and they avoid the serious risk of missing critical vulnerability advisories simply because there weren’t enough hours in the day to manually review every report. And when analysts combine this with other Doc Analysis Service features, such as industry classification, MITRE ATT&CK AI Classification, and other components that extract CVEs and IoCs, they can leverage the full power of ThreatConnect’s data model to pinpoint vulnerabilities that matter most to their business’s risk.
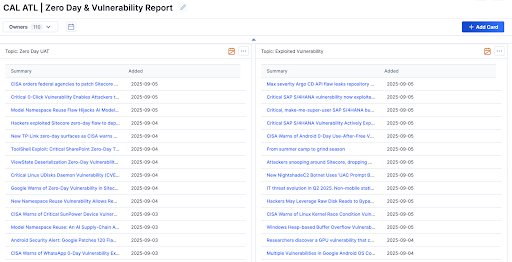
Here’s how AI Exploited-Vulnerability Classification makes the difference:
- Noise Reduction: In CAL™ Automated Threat Library (ATL), AI Exploited-Vulnerability Classification automatically scans report descriptions, filtering out non-relevant references (ads, slang, policy chatter) that pollute traditional keyword searches.
- Signal Amplification: Applies precise AI tags to the Reports that matter.
- Vulnerability Summaries: Generates AI-driven summaries customized for vulnerability topics, identifying CVEs, affected systems, exploit details, and fixes so analysts can move from report to action faster.
The result: less time wasted on irrelevant reports, and more time focused on defending against the threats that matter most.
Extending the Power: From Intel to Automation
ThreatConnect’s AI Exploited-Vulnerability Analyzer is already available in CAL™ Automated Threat Library (ATL), but its impact doesn’t stop there. Soon, the capability will extend into ThreatConnect Playbooks, the low-code automation engine, and into the Polarity platform, where analysts can apply it directly while reviewing documents.
That means:
- In the Doc Analysis Playbook: Organizations can set automated workflows that detect new exploited vulnerability reports. Playbooks can enrich findings, trigger alerts, or open tickets in vulnerability management systems and turning awareness into immediate action.
- In Polarity: Analysts can leverage key AI features when reviewing threat intel documents in real time, cutting through noise on the fly and surfacing only the vulnerabilities that truly matter.
Analysts will have these AI-driven insights wherever they work. Whether pivoting through CAL™ Automated Threat Library (ATL), automating enrichment in ThreatConnect Playbooks, or reviewing reports directly in Polarity. This flexibility ensures the signal is available in the moment it’s needed most, integrated seamlessly into their existing workflows.
Transform Noise to Signal
In a world where noise grows faster than signal, the real value lies in precision. With the AI Exploited-Vulnerability Analyzer, ThreatConnect turns the flood of vulnerability chatter into an actionable signal. It empowers analysts to reclaim their time, enables CTI leads to prove value to executives, and helps organizations close the gap between intelligence and action.
Explore the AI Exploited-Vulnerability Analyzer in CAL™ Automated Threat Library (ATL) today, and stay tuned for its expansion into the Doc Analysis Playbook.