Posted
The stakes facing USA’s critical public infrastructure organizations in today’s threat environment are higher than ever before. Targeted with an onslaught of relentless attacks and malicious activity, threat actors can and must be stopped every single time. Through a combination of prevention and blocking, if even one successful attempt to sabotage a water system, community healthcare provider, transportation system, food distributor, emergency services provider, or electrical grid happens, it can threaten the health and well-being of a community. And with an increasing number of high-profile ransomware attacks, like the 2021 Colonial Pipeline shutdown that affected travel on the U.S. East Coast for days or the malicious actors that added lye to the water supply in Oldsmar, FL, but were quickly thwarted, this issue is also making the wrong kind of headlines.
New Industry Cyber Performance Measures
In October 2022, the U.S. Department of Homeland Security released Cybersecurity Performance Goals (CPGs), a set of baseline measures that critical infrastructure agencies of all sizes can leverage to ‘protect against cyber threats.’ They are intended to be implemented with the NIST Cybersecurity Framework to help organizations across the private sector and government take action on the most impactful cybersecurity practices.
CPG measures simplify what could be vast and unwieldy expectations for organizations that don’t know where to start – and provide a focus for organizations with security programs that need to evaluate their current maturity. Designed by the Cybersecurity and Infrastructure Security Agency (CISA), the CPG measures hone in on areas that will decrease risks to networks, data, and systems to protect U.S. infrastructure and supply chains. Each CPG includes risks, tactics, techniques, & procedures (TTPs), outcomes, scope, security practices, and recommended actions. The CPGs include:
- Account Security
- Data Security
- Device Security
- Vulnerability Management
- Response and Recovery
- Supply Chain / Third Party
- Governance and Training
Intelligence-Powered Security Operations Can Help Meet CPGs
The CPGs outlined by CISA and DHS offer critical infrastructure sectors a set of standards for organizations of all sizes, as well as a way to prioritize investments in security. To meet these objectives, many teams will need to make meaningful structural changes and transition from a reactive to a proactive security posture. Public sector organizations who want to make this transition should consider adopting an Intelligence-Powered Security Operations model.
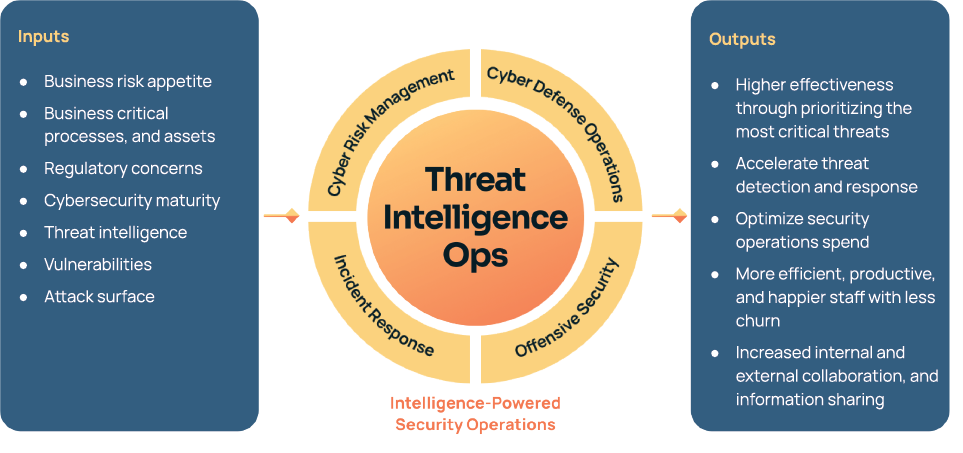
When organizations make the decision to place Threat Intelligence Operations (TI Ops) at the core of all security activities and infuse threat intelligence throughout their organization, they can prioritize resources and focus their efforts on addressing the biggest risks and threats. Intelligence-Powered Security Operations combine people, processes, and technology to deliver an agile security organization with centralized functions prepared to protect against, detect and respond to malicious activity based on high-fidelity threat intelligence. A key outcome of adopting this model is the ability to accelerate the time to detect and respond to threats by prioritizing threats targeting your organization.
How ThreatConnect Enables Intelligence-Powered Operations to Protect Critical Infrastructure
When TI Ops infuses threat intelligence into everything security operations does, it results in better decision-making, greater efficiency, and stronger collaboration. The ThreatConnect Platform centralizes threat intelligence, automates key activities, and enables information sharing across the security organization. The security team will act on high-fidelity threat intelligence to prioritize their efforts thanks to real-time intelligence feeds enriched with CAL™ analytics and insights from the ThreatConnect global user community. Automation saves teams time with standard and repeatable best practices that speed up the time to respond and remediate threats.
Infusing threat intelligence into an alert triage program empowers analysts to quickly cross-check alert data with current threat intelligence sources to get the latest updates on active threats and make informed decisions. The Platform offers integrations with firewalls, endpoint/network security, security analytics, SIEM, etc., to get better detections, a reduction in false positives, the ability to link related alerts across tools into a single incident and better alert prioritization, which makes organizations more effective and efficient.
An entire set of CPG measures is dedicated to Vulnerability Management. The ThreatConnect Platform enables vulnerability prioritization to ensure the riskiest vulnerabilities are addressed first by ingesting relevant vulnerability data, scoring vulnerabilities, and prioritizing actively exploitable vulnerabilities.
ThreatConnect Helps Transform Security Organizations
As critical public infrastructure organizations review the recently released CPGs, and CISA continues to expand guidance for individual sectors, Intelligence-Powered Security Operations offers security operations teams a guide to modernizing by placing TI Ops at the core of security activities and infusing threat intelligence into everything they do. The ThreatConnect Platform empowers TI Ops teams as it aggregates, analyzes, and makes intelligence actionable.
Reach out to us at https://threatconnect.com/contact/, and we’ll be pleased to share a customized demonstration of the ThreatConnect Platform to show how we can help your organization achieve the expectations associated with the CPGs.

