Posted
In recent years, there’s been an increase in attacks targeted specifically toward enterprise software vendors. Nation-states and cyber-criminal gangs are persistently attacking these organizations with increasing sophistication. Attacks like the one against SolarWinds exemplify the challenges software vendors face and it’s getting worse. Microsoft noted that Russian hackers are systematically attempting to infiltrate technology supply chains. Cybergangs are stealing intellectual property, like source code, as well as data in an attempt to extort software vendors.
How can software vendors protect and defend against these increasingly hostile threat actors? One way is to leverage cyber threat intelligence (CTI) to gain an advantage over the attackers. Operationalizing CTI across the teams responsible for protecting, detecting, and responding to attacks is critical, and how it’s operationalized takes several forms. One of those is through threat hunting.
The goal of threat hunting is to dig deeper to find malicious actors in your environment that have slipped past your security defenses. The challenge for many security teams, whether it’s the SOC or the incident response team, is they struggle to define and implement a threat hunting program due to a lack of know-how. “If I’m going threat hunt, where would I start?” is a common question. The answer lies in having relevant CTI and having a platform that provides a single source of applicable CTI, along with the capabilities that allow analysts to be threat hunters – visualizations, automation, and analytics for example.
With the right platform, security teams at enterprise software vendors can implement and sustain a threat hunting capability that allows them to have the right insights on threat actors, efficiently leverage threat intelligence to hunt for indicators and artifacts across their environments, and collaborate with their peers across the organization, whether within the security team, IT, or DevOps.
Where Do You Start?
This is where an Intelligence-powered Security Operations Platform comes to the rescue. An analyst needs a robust CTI library, a marketplace of apps to wire all the needed security tools together, community-sourced insights on threats relevant to their vertical, and automation to make hunting and responding to any detected threats faster and smarter.
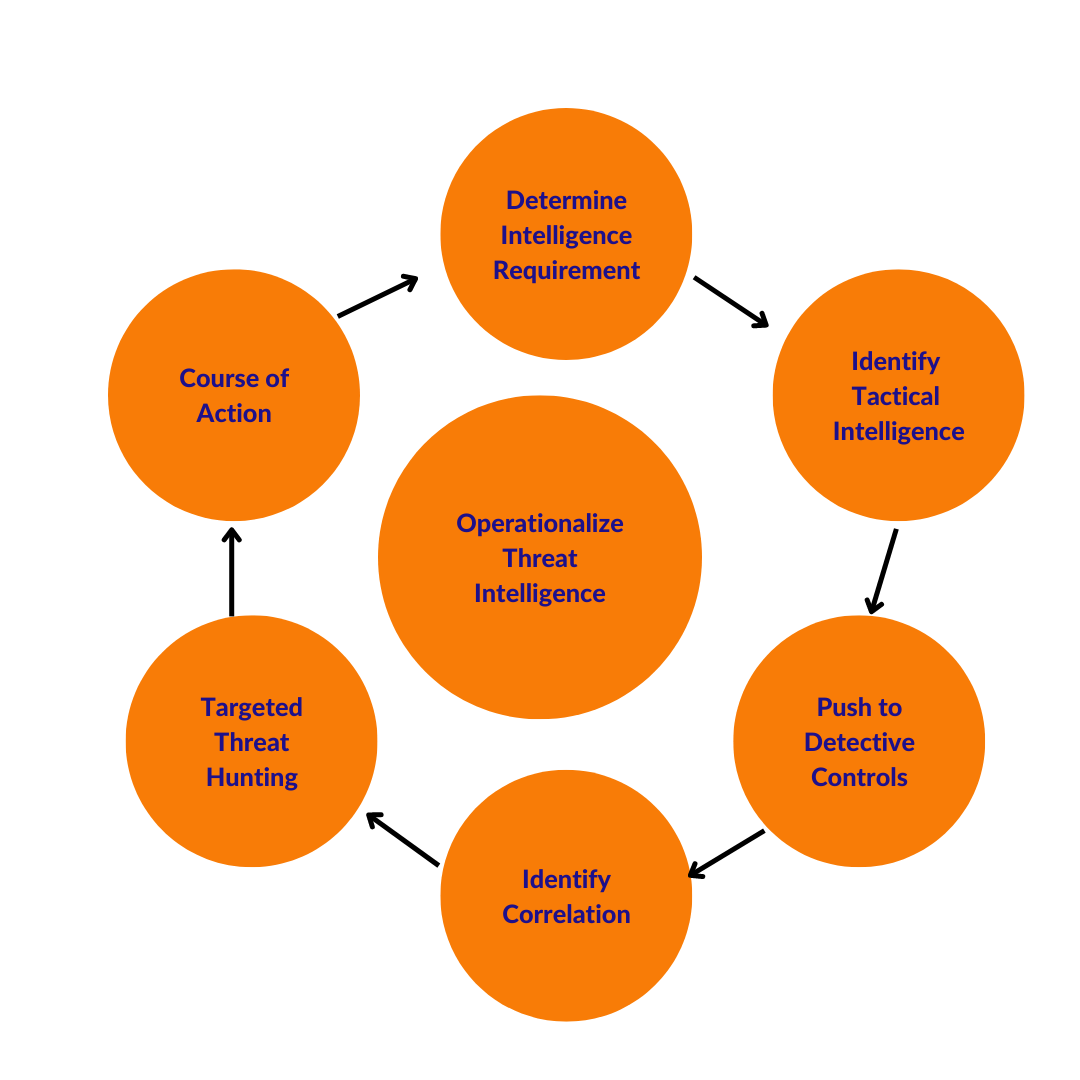
So how does threat hunting work in practice? First, whoever is threat hunting has a hypothesis or starting point, like an indicator or specific attacker tactic, technique, and procedure (TTP) provided by the CTI team. They will start with that “thread” and pull on it seeing where it takes them to determine if there is evidence of an attacker in the environment. If there is evidence, they will share it with the incident response and SecOps teams for further action. The IR, SecOps, and CTI teams work together to learn more information about the attack and understand if any new Indicators of Compromise (IOC) were found – which helps determine the scale of the attack and if security controls are working as designed. Once the attacker is evicted, the SecOps team will take corrective actions based upon what was learned about the attack in order to reduce the risk of future attacks.
How Can ThreatConnect Help?
ThreatConnect’s Intelligence-Powered Security Operations platform helps teams quickly discover if a threat is lurking undetected in your environment. It is designed to bring together SecOps teams under one platform to go from reactive to proactive by leveraging risk insights, threat intelligence, and analyst knowledge to drive every decision and action.
When using ThreatConnect for Threat Hunting, you’re able to:
Improve Decision Making
- Identify, detect, and respond to threats that are targeting your organization to better focus analysis and response efforts
- Integrating not only with existing infrastructure but leveraging the contextual knowledge of threats and related indicators via our analytics engine, Collective Analytics Layer (CAL), which makes decision-making easier for analysts during the investigation.
Reduce dwell time and time to respond
- Define necessary response actions allowing consistency and removing the requirement to recall the step-by-step workflow
Understand Defensive Controls Effectiveness and Take Corrective Action
- By working together in one platform, security teams learn more information about the attack and understand if any new IOC exists. All team members have clarity on if the defensive controls worked or not and then have to take corrective actions based on their findings.
Maximize efficiency by automatically escalating an investigation with a single click
- Once you have worked through the threat hunting exercise, you can automatically escalate to an investigation. The investigation will help you understand whether the attacker gained access and how long the attack has gone undetected
Maximize collaboration by reducing silos and enabling better information sharing
- CTI analysts collect information about a potential attack and share it with the SecOps team for further investigation or remediation
- SecOps team gains more context about a specific indicator or threat to make more confident decisions
With ThreatConnect, you can make threat hunting a regular occurrence and proactively identify security gaps and vulnerabilities. Processes that previously took weeks or months, can now be completed in minutes or hours.
ThreatConnect enables security operations and threat intelligence teams to work together for more efficient, effective, and collaborative cyber defense and protection. With ThreatConnect, organizations infuse threat intelligence and cyber risk quantification into their work, allowing them to orchestrate and automate processes to respond faster and more confidently than ever before. Nearly 200 enterprises and thousands of security operations professionals rely on ThreatConnect every day to protect their most critical systems. Learn more at www.threatconnect.com.
