Posted
I had the privilege of attending FAIRCON ‘23 Embrace Digital: Managing the Risk of Digital Transformation, Cloud, and AI this year, not as a speaker or a sponsor but as an attendee. It was great being able to catch up with people and to hear how organizations are advancing their cyber risk quantification (CRQ) programs. This conference is always a good place to hear about both the ups but also the challenges of putting CRQ into practice.
There were talks around
- The recent SEC Cybersecurity rules and how they will potentially affect publicly traded companies, and how risk quantification is going to help with complying with those rules
- How to leverage MITRE ATT&CK to run a CRQ analysis
- How to leverage controls to help prioritize vulnerabilities
- How to quantify the risk with third parties.
All the talks highlighted the need for CRQ to help organizations to make better decisions. That’s the positive side. The downside to these talks is there are still a lot of theories about how to do some of these activities but not a lot of truly actionable takeaways. There is still a lot of work that needs to be done to make CRQ ubiquitous.
This got me thinking about how CRQ can be made easier and more actionable. Over the next couple of blogs, I (and my colleagues) will show how the ThreatConnect Risk Quantifier (RQ) platform can help. To start this conversation, I want to touch on how RQ can leverage a combination of both your organizational data and industry data all the way down to the MITRE ATT&CK level so you can truly get an understanding of your cyber risks. ThreatConnect RQ maps controls to ATT&CK in order to help you understand your risk landscape.
What is MITRE ATT&CK?
MITRE ATT&CK is a framework that provides a detailed model of how cyber adversaries operate. It categorizes various tactics, techniques, and sub-techniques used by attackers during the different stages of an attack (like an expanded version of the Cyber Kill Chain), helping organizations understand and defend against threats. ATT&CK is widely used to enhance threat detection, support incident response, and improve an organization’s security posture by aligning defensive strategies with real-world attacker behavior.
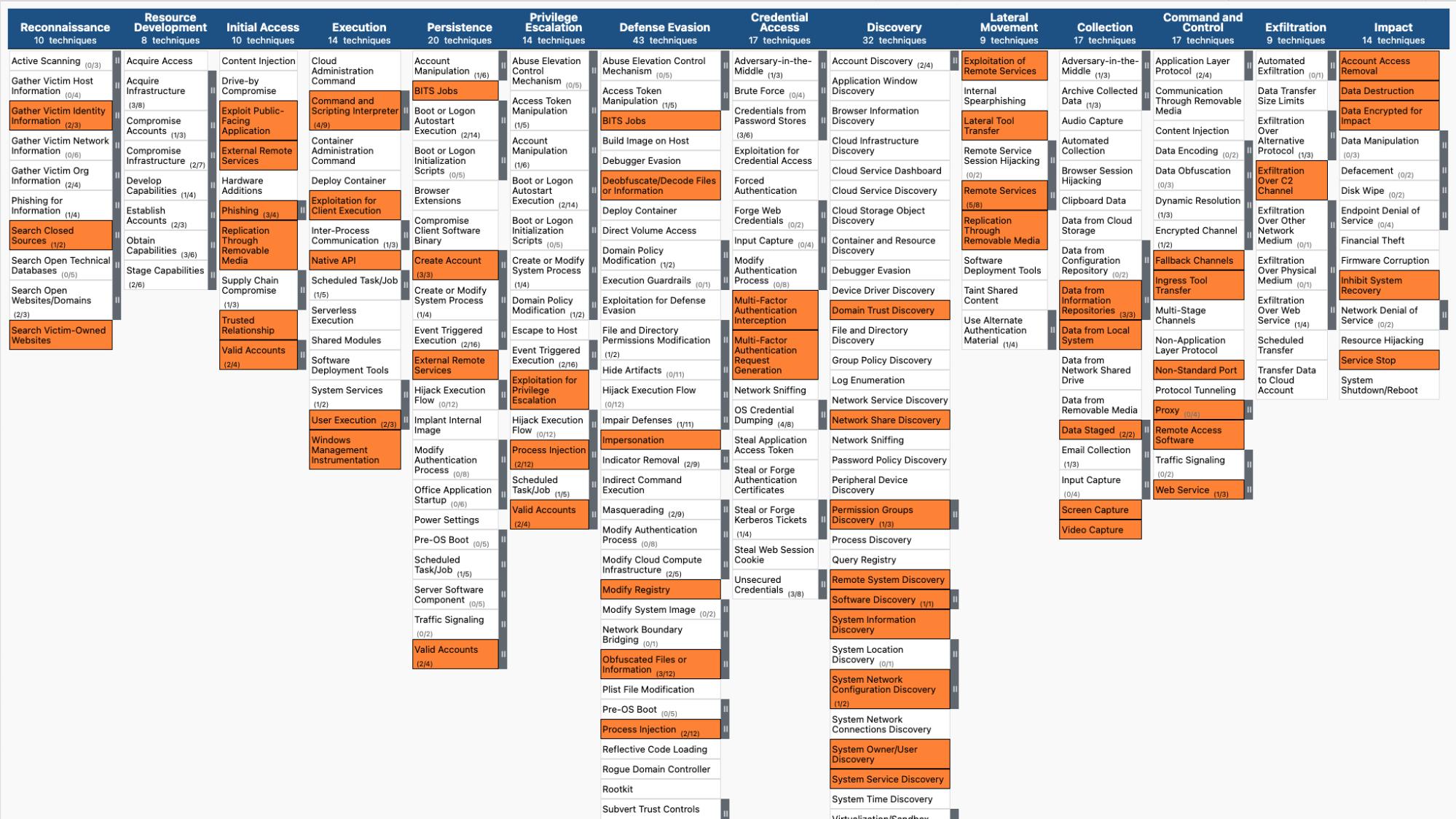
Example view of ATT&CK highlighting common techniques across a set of threat actors
The biggest takeaway I heard at FAIRCON was that mapping risk down to the MITRE ATT&CK level is that IT IS HARD. From what I have seen as someone with 8 years in this CRQ industry, it is hard for one main reason: MITRE doesn’t map perfectly to FAIR because it accounts for any path an attacker could take within the environment. There is what seems like an endless combination of paths to loss. It raises questions like:
- What would an analyst consider Threat Event Frequency?
- Where is it in the loss flow?
- When is an attack considered an “attempt”?
Nothing against FAIR here, but those questions are very valid and are what makes it challenging. It really depends on the FAIR risk practitioners experience (and this can vary from practitioner to practitioner). To use a phishing attack as an example, one practitioner could say that TEF is when an actor successfully sends a phishing email. Another could say it’s only an attempt when the email gets past the organization’s spam filters. Both have drastically different values that could be entered, and both can be considered correct. Yet none of these incorporate MITRE ATT&CK TTPs and their frequency or effectiveness.
Thankfully, the industry-leading ThreatConnect Risk Quantifier (RQ) platform allows users to map their risks all the way down to the ATT&CK framework level. RQ was built on the concept that an attacker has to execute their attack (via an attack pattern) to cause impact. RQ has built-in – using threat intelligence and defensive postures – the ability to run MITRE ATT&CKs since its inception.
RQ also takes in your defensive posture – in the form of controls and vulnerabilities – to determine attacker success (via MITRE ATT&CK). This enables the risk practitioner to quickly determine what threats are plaguing their environment and the amount of exposure to those risks. The Platform even takes it a step further by providing automatic recommendations as to how to reduce your risk exposure.
In our next blog, we are going to talk about how to leverage controls to help prioritize vulnerability patching. In the interim, please read our paper on operationalizing cyber risk quantification, and reach out to one of our experts if you would like to learn more about ThreatConnect RQ.
