Posted
As a cybersecurity vendor, I like to take a larger view of the market when it comes to the competition. Competitor or not, we’re all on the same side: fighting the good fight against attackers – and hopefully whatever solution is chosen by cybersecurity teams helps them stay ahead and maintain whatever advantage that vendor offers.
That’s why it’s so important that cybersecurity teams understand what they’re getting when they spend hard-to-get budget on new resources. Recently, one of our competitors wrote up an “us vs. them.” I’d like to set the record straight on some of their claims so that prospects have an accurate, high-integrity view when selecting a threat intelligence platform vendor.
This blog is not a condemnation of the competition – it’s a fact-by-fact correction of what they said.
In fact, here’s a link so you can check their work!
1. “Superior Intelligence, Enhanced with Context”
Anomali claims to provide a “comprehensive solution” for intelligence, yet they don’t define what comprehensive means. It’s true that ThreatConnect offers more than 125 OSINT feeds and blogs out of the box, many of which aren’t available in a machine-readable format anywhere else (and we’re adding more all the time!). OSINT is valuable, but context is king in CTI. That’s why we use AI to classify data within OSINT feeds by industry, MITRE ATT&CK techniques, and other relevant factors such as industry and geographic relevance —bringing them closer to the level of premium feeds.
Anomali also claims to “eliminate alert fatigue.” I wish! If a cybersecurity vendor could eliminate alert fatigue, it would revolutionize cybersecurity, and we’d all be able to retire early. Realistic alert fatigue is about volume: the key isn’t eliminating alerts but making sure the right ones get surfaced with the right context.
How ThreatConnect Solves This:
- AI-Powered Context: We don’t rely on third-party data quality itself. We make sure it’s tuned and contextualized for you. ThreatConnect enriches all intelligence sources with both proprietary analytics and real-world attack context so you can filter what’s relevant more easily and make decisions faster.
- Aligned Intelligence: ThreatConnect tailors CTI to your unique intelligence requirements, ensuring only relevant intelligence is surfaced—unlike Anomali’s reliance on third-party feeds with minimal alignment.
- Polarity: Polarity is a brand new way to deliver threat intelligence to wherever it’s needed at the moment of investigation and action. It allows analysts to contextualize whatever they’re looking at and gain insights from both threat intelligence and operational data (e.g. SIEMs) without ever leaving the tool they’re in.
Bottom Line:
Results speak louder than claims, so don’t take our word for it; see this quote from one of our customers:
“We received 200,000,000 SIEM events per month or 50,000,000 per week. With ThreatConnect’s intelligence-driven automation capabilities, those events get narrowed down to 12 incidents per month, or 3-4 per week.”
-Fortune 300 Financial Institution
Relevant and contextualized intelligence helps more than reduce alert fatigue in Detection; it helps the entire CTI function more impactfully to support every other function, too (Response, Hunt, Vuln Management, etc.).
Further, thanks to Polarity, analysts can conduct adaptive threat analysis directly in their workflow, prioritizing threats without additional integrations. Intelligence can be customized to your unique requirements.
(P.S. If anyone knows a way to completely eliminate alert fatigue, let me know—I have my eye on a ski-in/ski-out cabin with a hot tub…)
2. “Advanced AI for Adaptive Threat Analysis”—or Just a Black Box?
Anomali touts their machine-learning engine, Macula, for threat scoring and classification. That’s great, but AI isn’t useful if you can’t check its work. It’s a human optimizer, not a human replacer. A black-box ML model without transparency is a liability, not an asset.
At ThreatConnect, we believe AI should enhance, not replace, human analysis. That’s why:
- We’ve marked over 11 million indicators as safe, backed by clear citations and scoring explanations.
- We provide full visibility into how our AI-derived conclusions are made.
- Just checking the facts here: Anomali says that our analytics are a paid add-on. We don’t believe that critical insights should be paywalled. All of our analytics – AI or otherwise – are included in our base subscription. Also if I’m throwing shade, our integrations are also all included: you want another SIEM integration? You better be ready to pay Anomali extra.
- Polarity’s AI-powered summaries provide instant context for large datasets, streamlining investigations without reliance on opaque AI models. In addition, you can leverage your own compliant-ready AI models without needing to rely on the vendor’s.
Bottom Line: ThreatConnect doesn’t just score threats—we add context that analysts can verify. And we don’t charge extra for analytics or integrations.
“Our incident response time from soup-to-nuts went from 7 hours to 37 minutes, and is still decreasing … ThreatConnect enabled us to quantify ROI and to define business requirements for onboarding technology.”
-Forbes 2000 Hospital & Healthcare System
3. “Streamlined Automation and Integration”—or a Customization Dead End?
Anomali tries to have it both ways: they say ThreatConnect Playbooks are too rigid, yet they also require “too much customization.” Which is it?
Customization is crucial for modern security teams that must adapt to evolving tech stacks. Many of our customers are former Anomali users who hit a wall—they found Anomali couldn’t adapt or scale to their needs.
Here’s how we do it better:
- Fully Customizable Playbooks: ThreatConnect supports automation at scale without the roadblocks of pre-built, inflexible workflows.
- Elastic Workflows: Unlike Anomali, which struggles with scaling automation, our workflows adapt to handle increased intelligence volumes seamlessly.
- World-Class Customer Success Team: Our team includes former practitioners (like CTI analysts and red-teamers) who help customers optimize their security operations. We’re also staffed with security engineers who do this sort of thing for fun (seriously, you should see some of their home labs). They’re here to help make sure even your most bespoke use cases are operationalized quickly.
Bottom Line: We adapt to both your technological and tradecraft needs, helping you mature by sitting alongside you as you deal with those growing pains.
“To reduce the load of our security and IT staff, we introduced over 60 workflow automations with ThreatConnect Playbooks, saving over $1.3 million per year in labor costs.”
-Fortune 2000 Healthcare Organization
4. “Secure Intelligence Sharing”—Our Approach vs. Their “Trusted Circles”
Anomali criticizes ThreatConnect’s approach to intelligence sharing, claiming we are “too open.” But let’s be clear: we do everything they do and more. Our data model allows private, secure community sharing exactly like their Trusted Circles.
However, relying solely on sharing groups usually depends on one or two very well-resourced “sharers” while everyone else simply consumes due to lack of resources or maturity. We solve this problem with a global intelligence network that’s anonymized and automated on an opt-in basis to ensure everyone can benefit from intelligence sharing regardless of resources.
We collect intelligence from billions of network events and investigations, automatically aggregating insights across our platform.
- If you find an indicator, we can show you whether others are investigating it, whether it’s been seen in the wild, or whether it has been debunked as a false positive.
- Unlike Anomali, our intelligence-sharing model doesn’t only depend on manual submissions (although we do support that!), reducing analyst burden while increasing reliability.
- MSSP-Ready: ThreatConnect’s data model is purpose-built to enable MSSPs to control data-sharing granularity, balancing customer privacy with intelligence effectiveness—unlike Anomali’s rigid “Trusted Circles.”
Bottom Line: “Trusted Circles” only work if people contribute. ThreatConnect’s data-sharing model ensures everyone benefits without extra effort. In addition, Trusted Circles were not built specifically to address the needs of MSSPs.
“ThreatConnect It took a 2-5 minute task and turned it into a 2-second task.”
-Fortune 500 Retailer
5. “Advanced Threat Modeling and Analysis”—Marketing Hype vs. Real Tradecraft
Threat modeling is a core CTI skill. Anomali claims to have a more advanced approach, but their writeup focuses on data aggregation—not real tradecraft.
ThreatConnect enables users to operationalize frameworks like MITRE ATT&CK in a structured, repeatable way. This isn’t just about collecting intelligence—it’s about making it actionable.
Additional Differentiators:
- Novel ATT&CK Use Cases: Going beyond traditional threat modeling, we apply ATT&CK to new use cases like security gap analysis and financial risk modeling.
- Modeling Assistance: We robustly map intelligence from structured data provided by partners and parse unstructured data to add labels and context, increasing its discoverability and usability to make it actionable.
- Intel Process Optimization: ThreatConnect’s workflows integrate human decision-making with automated response, reducing manual effort.
- Comprehensive Threat Intelligence: Unlike Anomali, which relies on third-party feeds, ThreatConnect’s CAL™ enhances intelligence with real-world data and performance analytics.
Bottom Line: Anomali talks about advanced modeling, but ThreatConnect does this better and, most importantly, actually helps analysts use it for real needs.
“ThreatConnect provides a comprehensive view of emerging risks and helps us correlate and analyze them to improve the speed of detection and response. It also allows our teams to collaborate more effectively, greatly enhancing our overall security posture and operational efficiency.”
-Global Advertising Agency
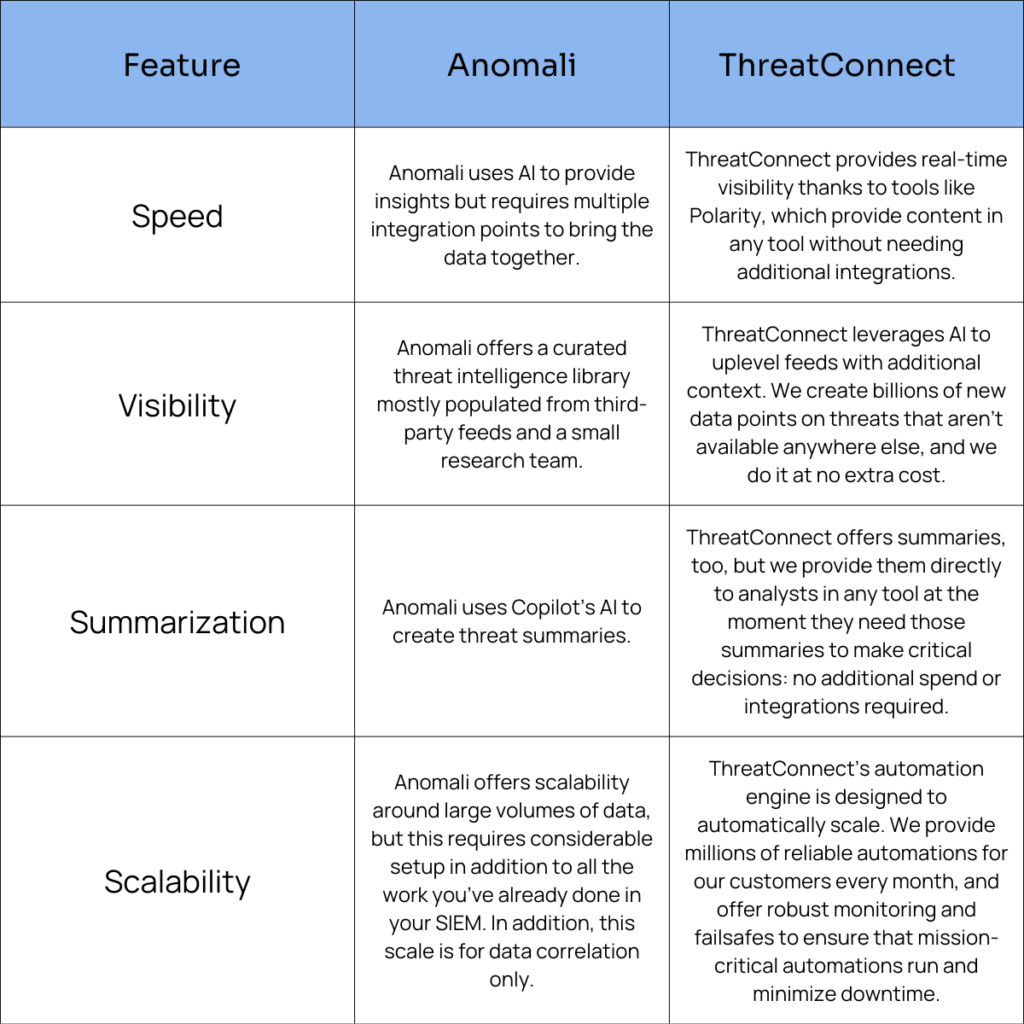
The Real Bottom Line: ThreatConnect is Built for Cyber Defenders for Analysts, Not Marketing Hype
Anomali’s writeup attempts to blur the lines between fact and fiction, but the truth is simple:
- ThreatConnect delivers true intelligence enrichment, not just black-box ML scoring.
- We include all analytics and integrations at no additional cost.
- Our automation scales with your needs, while Anomali customers often hit limitations.
- We make intelligence sharing effortless and anonymous, ensuring insights flow without manual work.
- We help CTI teams apply real-world tradecraft, not just aggregate data.
Want to see the difference for yourself? Schedule a demo today.

