AI & ML-Powered Threat Intel Insights
ThreatConnect CAL™, uses generative AI, natural language processing, and machine learning to strip away complexity and surface the insights you need.
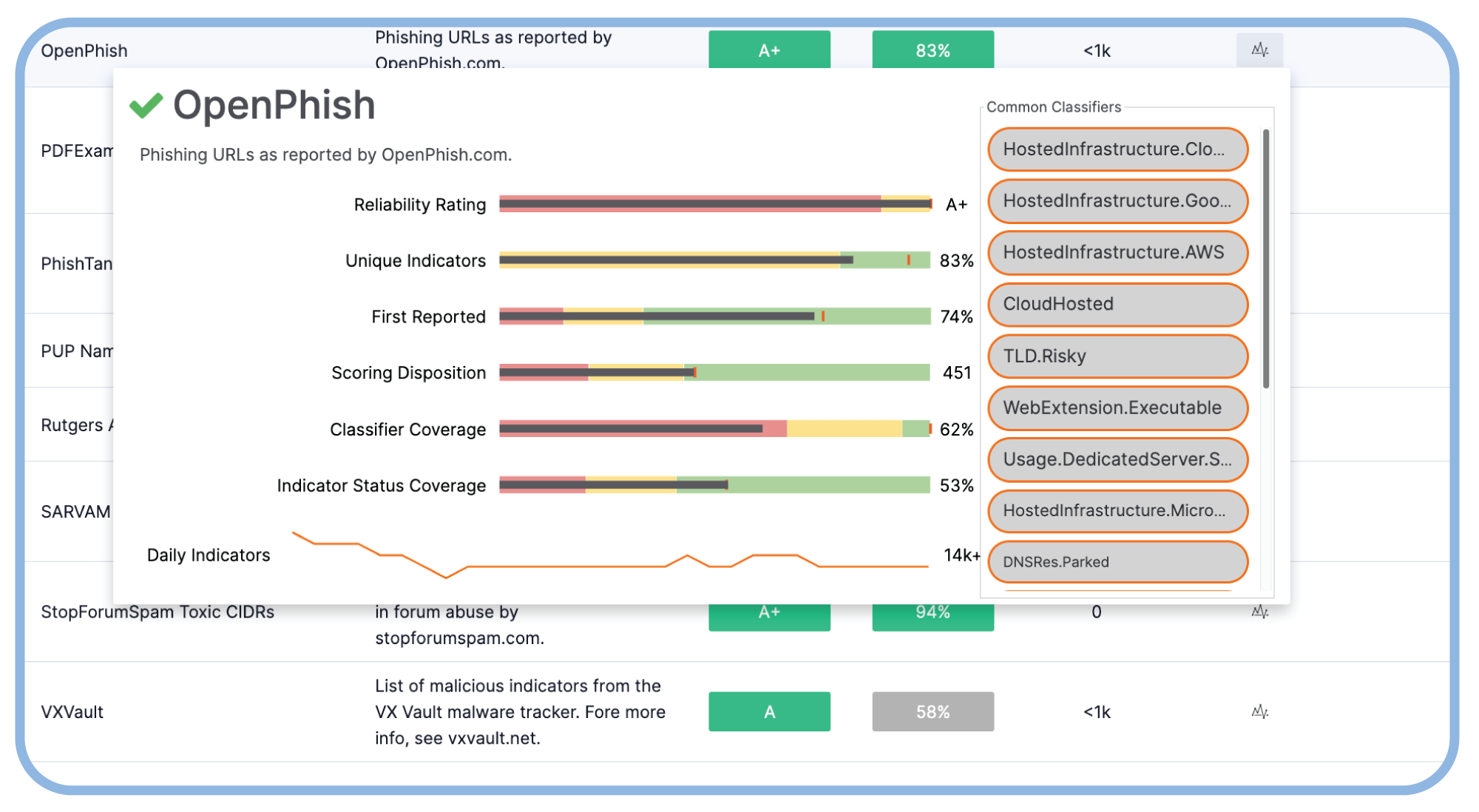
Streamline Open-Source Threat Intel Curation
With insights from more than 60 open-source intelligence (OSINT) sources, including blogs and social media, CAL uses the power of AI to simplify the analyst’s task of reading, analyzing, and memorializing intel from a wide variety of sources.
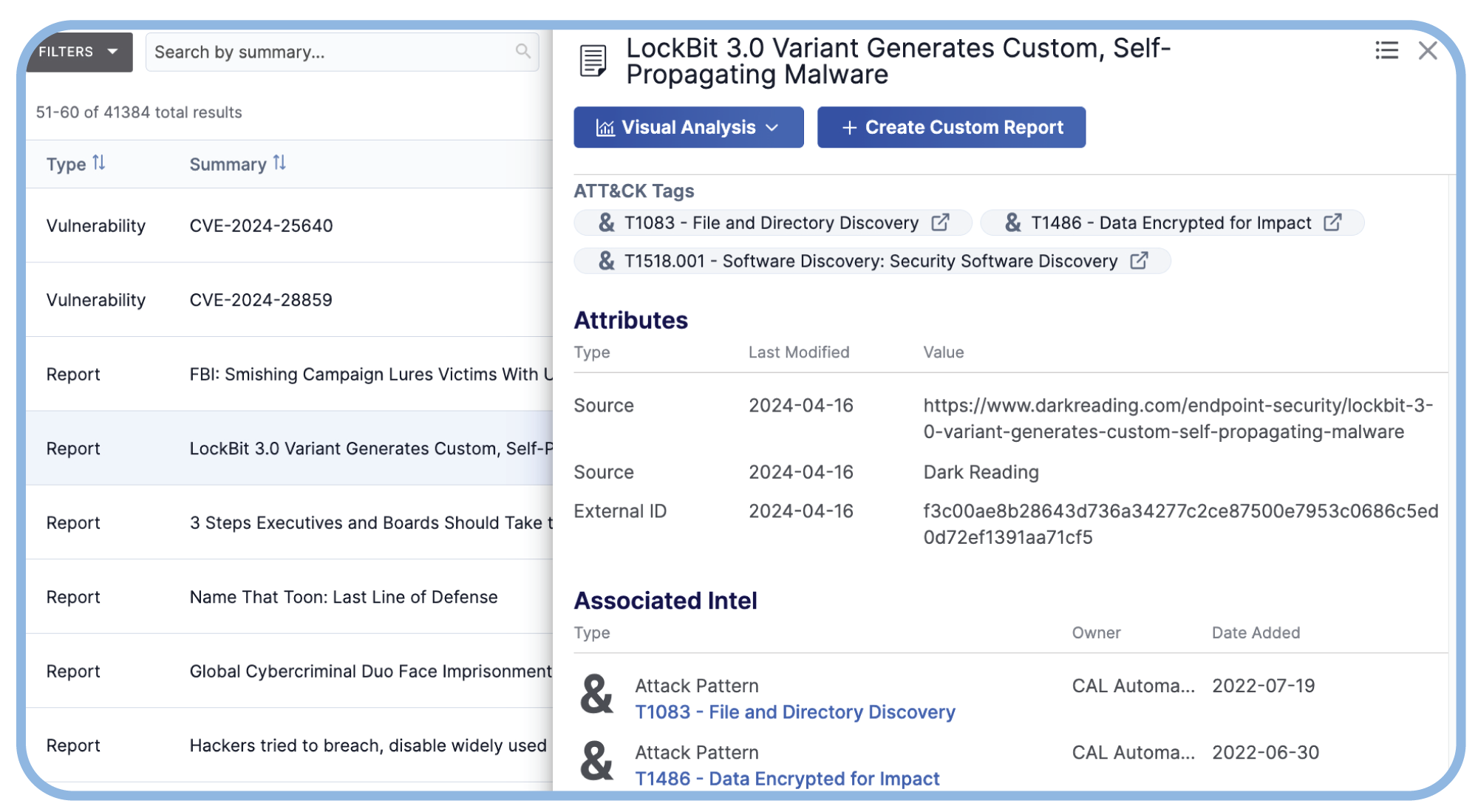
Speed Analysis with AI-Powered Intel Summaries
Get high quality, easy-to-consume AI-generated report summaries in the CAL Automated Threat Library. Users get easy-to-read bullet points and a brief summary, saving time when consuming intel reports.
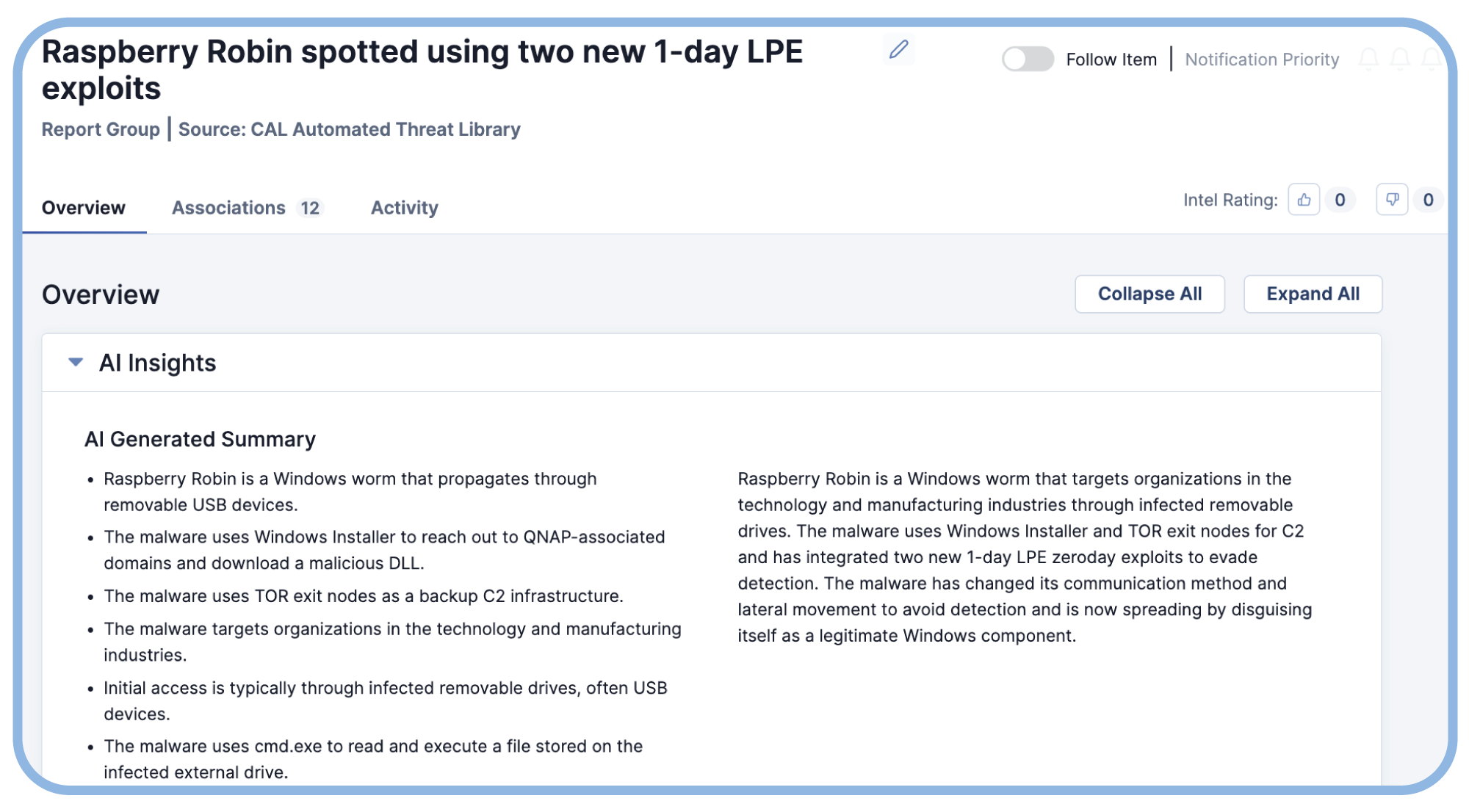
Optimize Your Threat Intel Portfolio
CAL Feed Explorer and Report Cards provide performance-related insights for all your intel feeds in the TI Ops Platform. Optimize your data source portfolio, cut complexity, and save money by eliminating redundant feeds.
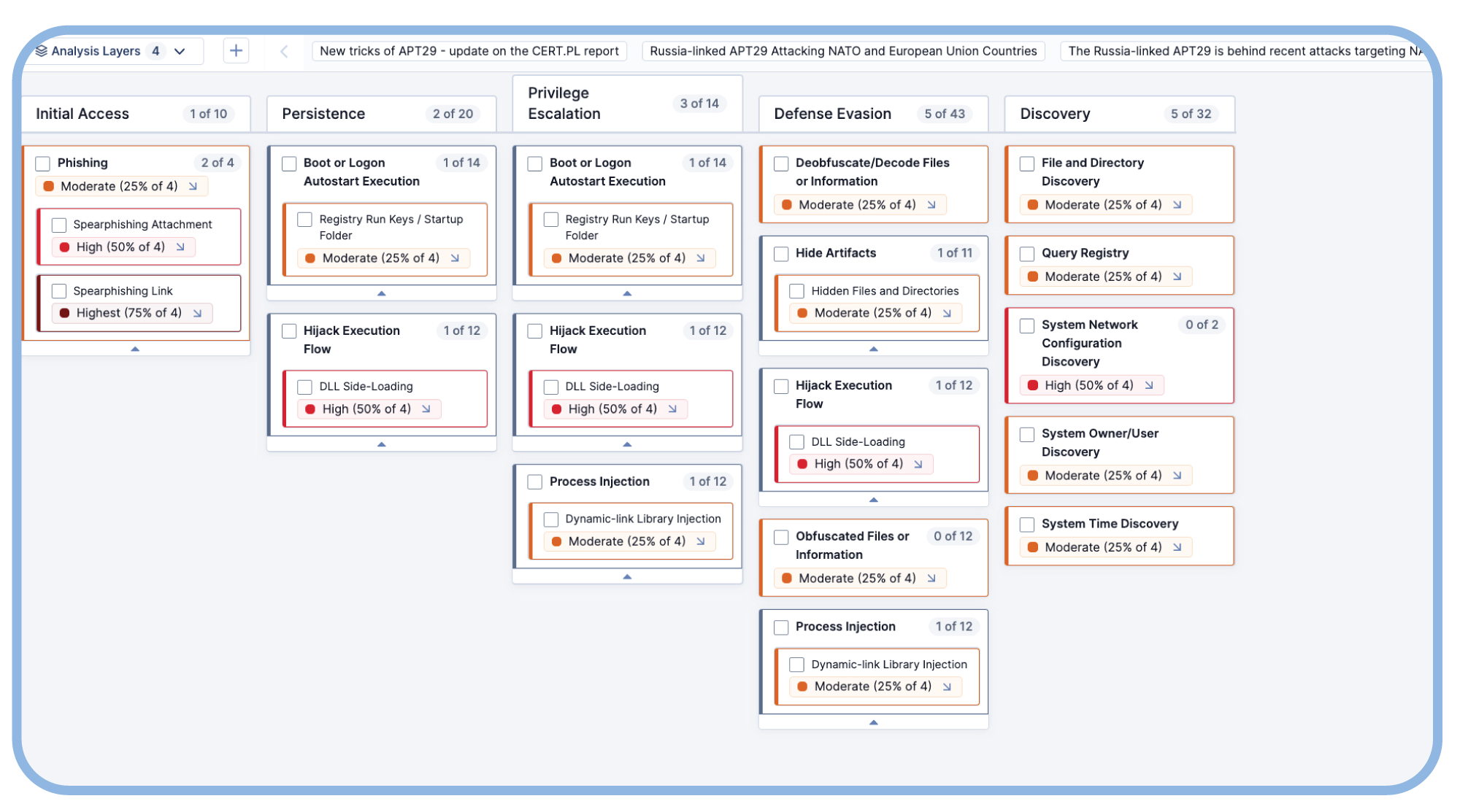
Effortless MITRE ATT&CK Context
CAL’s NLP analyzes the content in blogs, websites, and other text sources, interprets it, identifies, and tags ATT&CK techniques. This streamlines the laborious process of analysis and tagging ATT&CK context.
Access Intel Where You Work with Intel Anywhere
Efficiently gather information from any web-interface, like websites and security tool consoles, with ThreatConnect Intelligence Anywhere. This browser plugin allows you to quickly access existing knowledge about a known indicator or threat, and seamlessly memorialize it to your threat library for future analysis and investigation efforts.
Modern Threat Intel Operations with AI
Dawn of Threat Intelligence Operations White Paper
Download the Dawn of Threat Intelligence Operations white paper to learn how an evolution to TI Ops changes the value proposition of threat intelligence teams.
See how the ThreatConnect TI Ops Platform Leverages GenAI
Read how the CAL Automated Threat Library uses AI Insights to generate summaries of open source intelligence, making analysis faster and easier.
Intelligence Anywhere Puts Critical Information Within Reach
ThreatConnect’s Intelligence Anywhere feature makes the Threat Library in the TI Ops Platform instantly accessible to CTI and security operations analysts within any web-based interface.