DomainTools
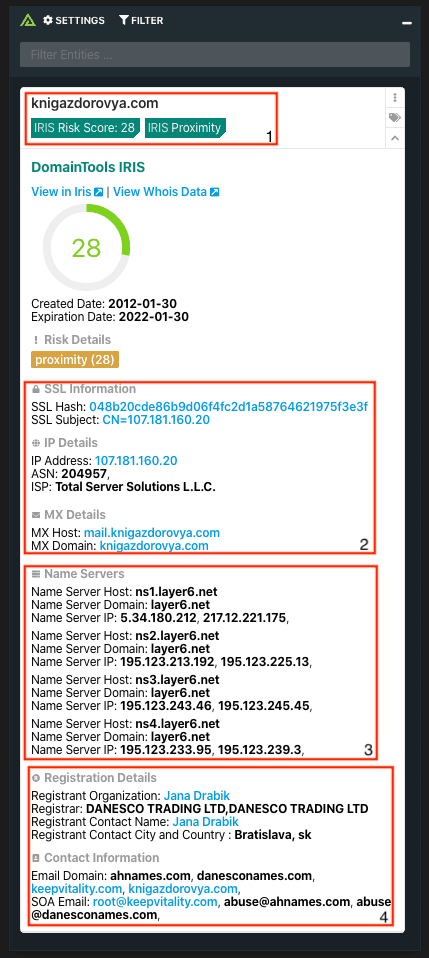
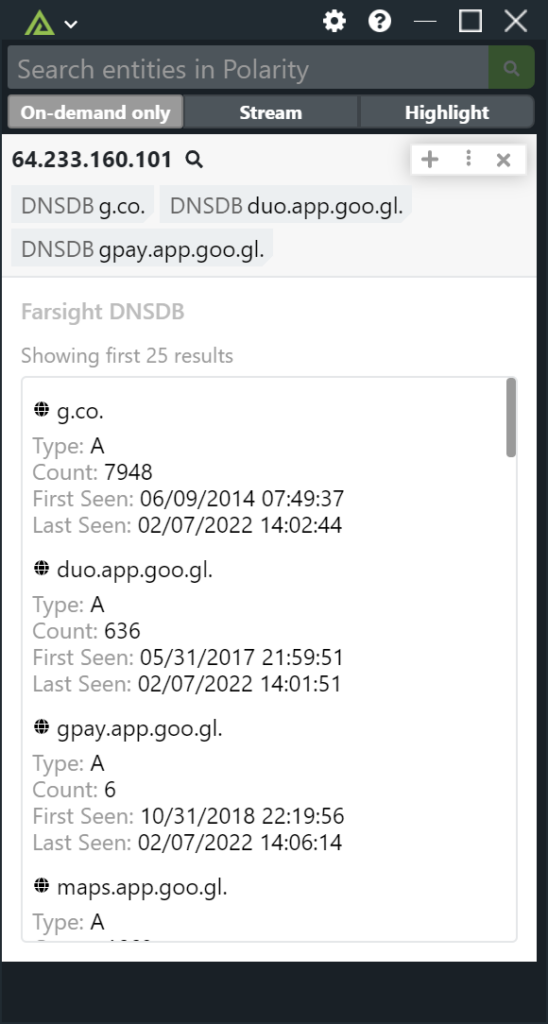
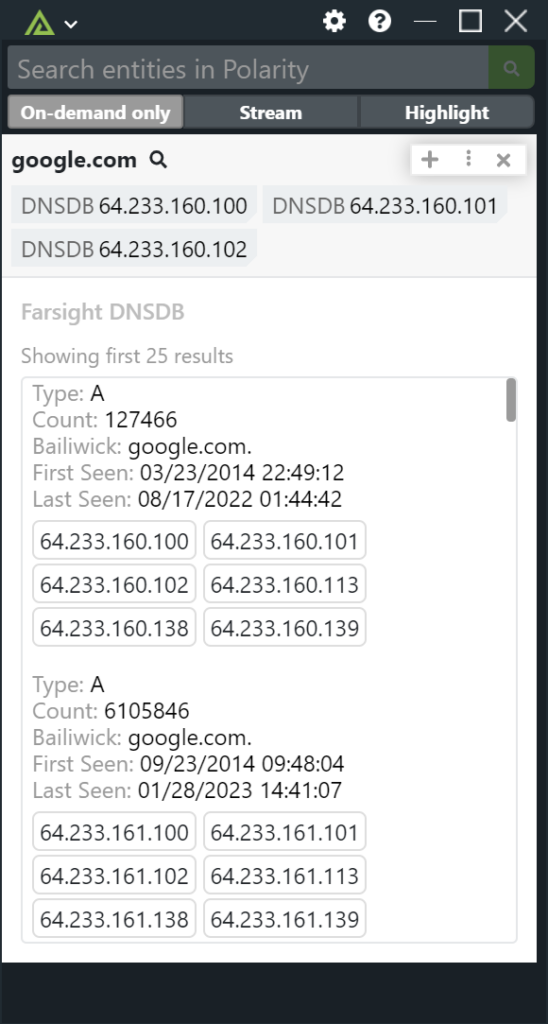
DomainTools offers the most comprehensive searchable database of domain name registration, Whois records and hosting data for online investigations and research. Cyber security analysts, fraud investigators, domain professionals and marketers use DomainTools to investigate cybercrime, protect their assets and monitor online activity. DomainTools has 12 years of history on domain name ownership, Whois records, hosting data, screenshots and other DNS records. That’s why customers say, “Every online investigation starts with DomainTools.” DomainTools customers include many Fortune 1000 companies, leading vendors in the Security and Threat Intelligence community and most crime-fighting government agencies.
Specialties
Integrations
Related Resources
Built By ThreatConnect
Related Resources
Built By Polarity
Downloads
Related Resources
Built By Partner
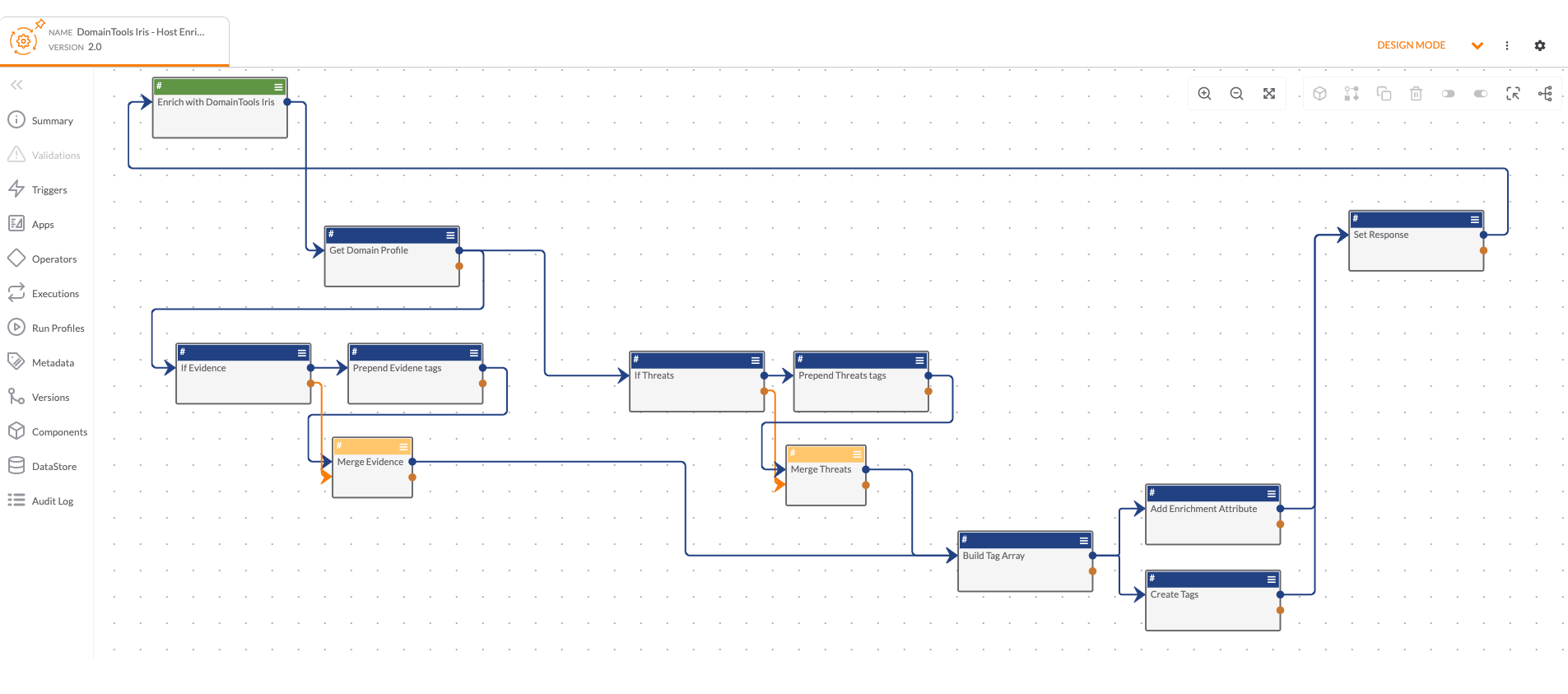
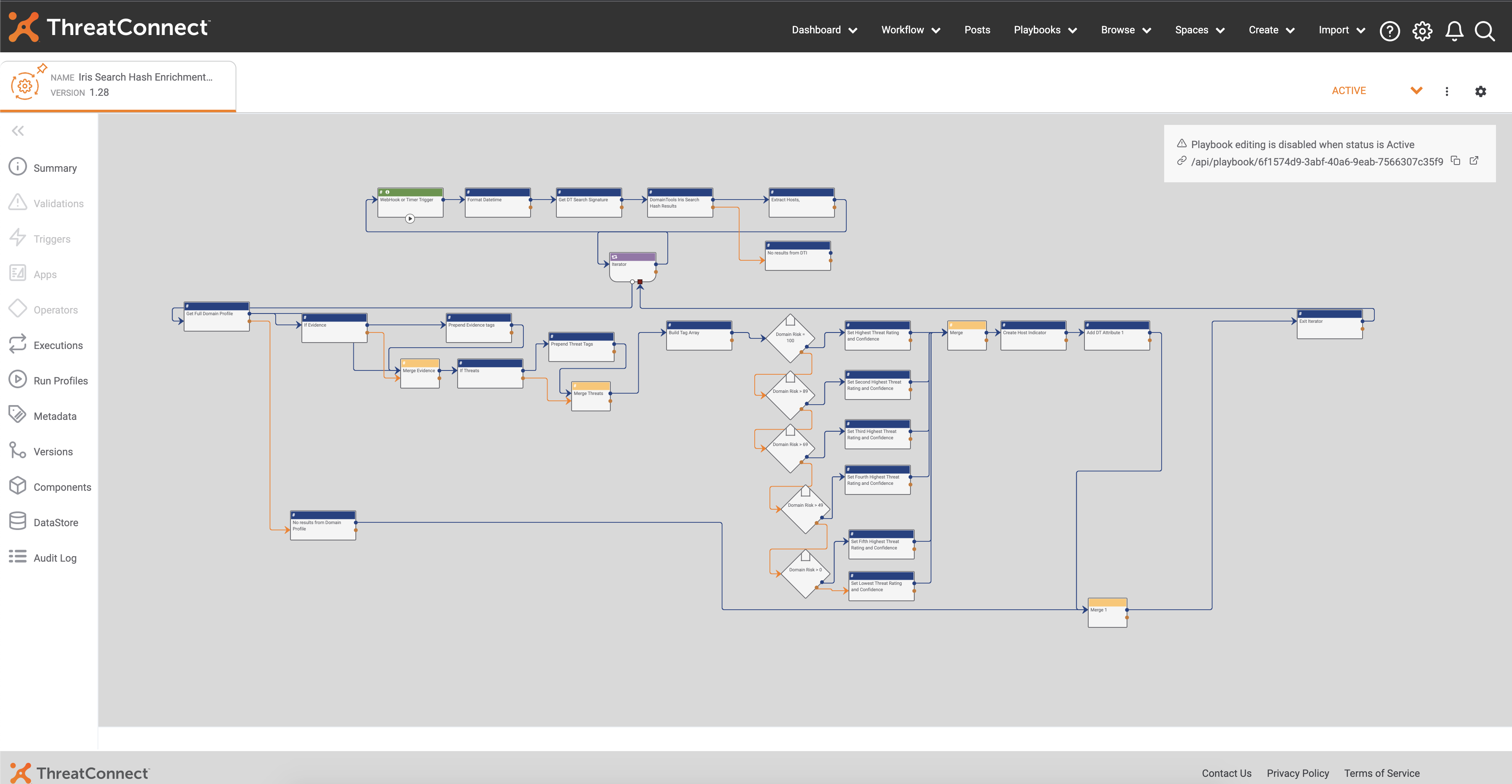
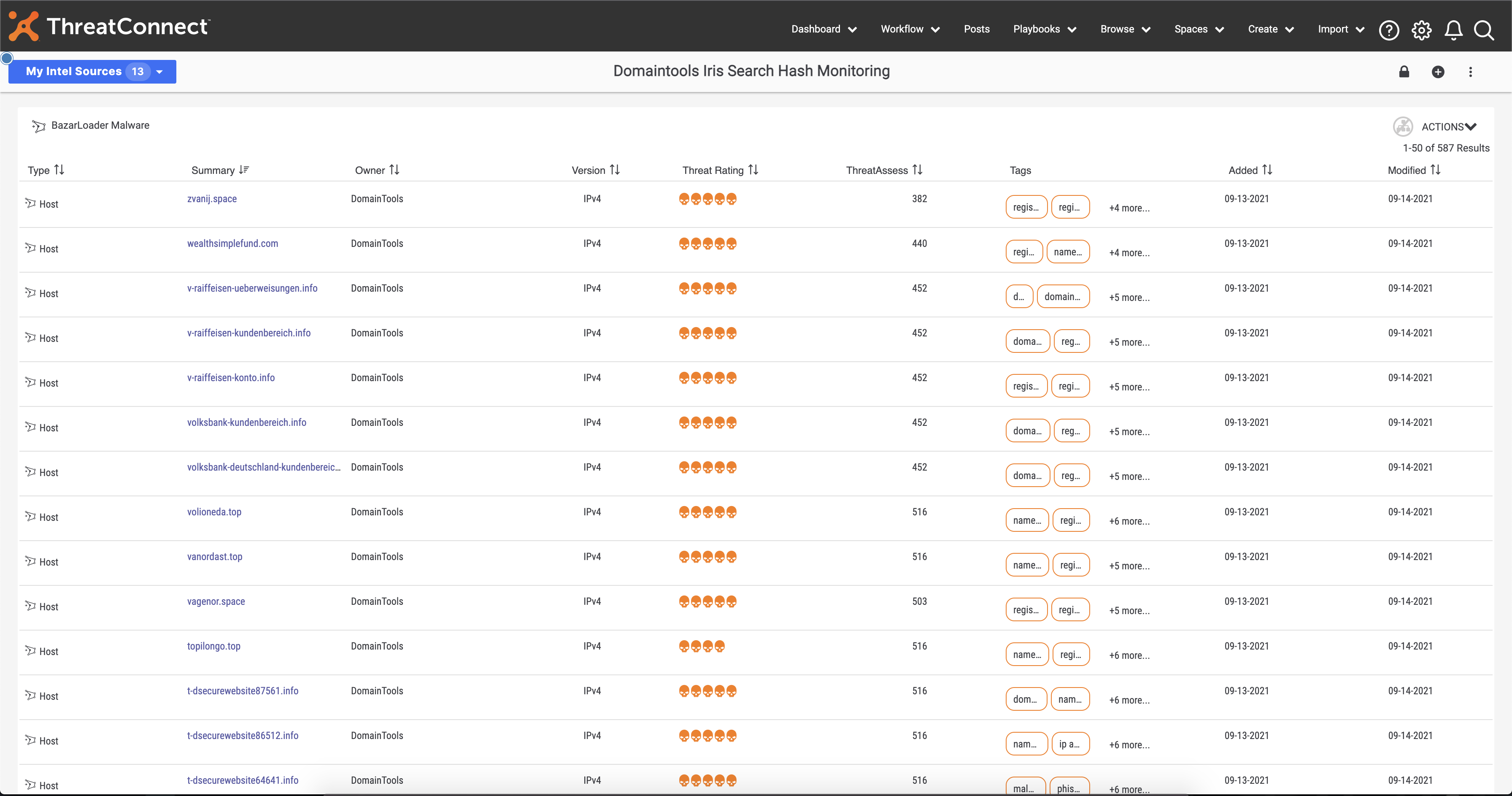
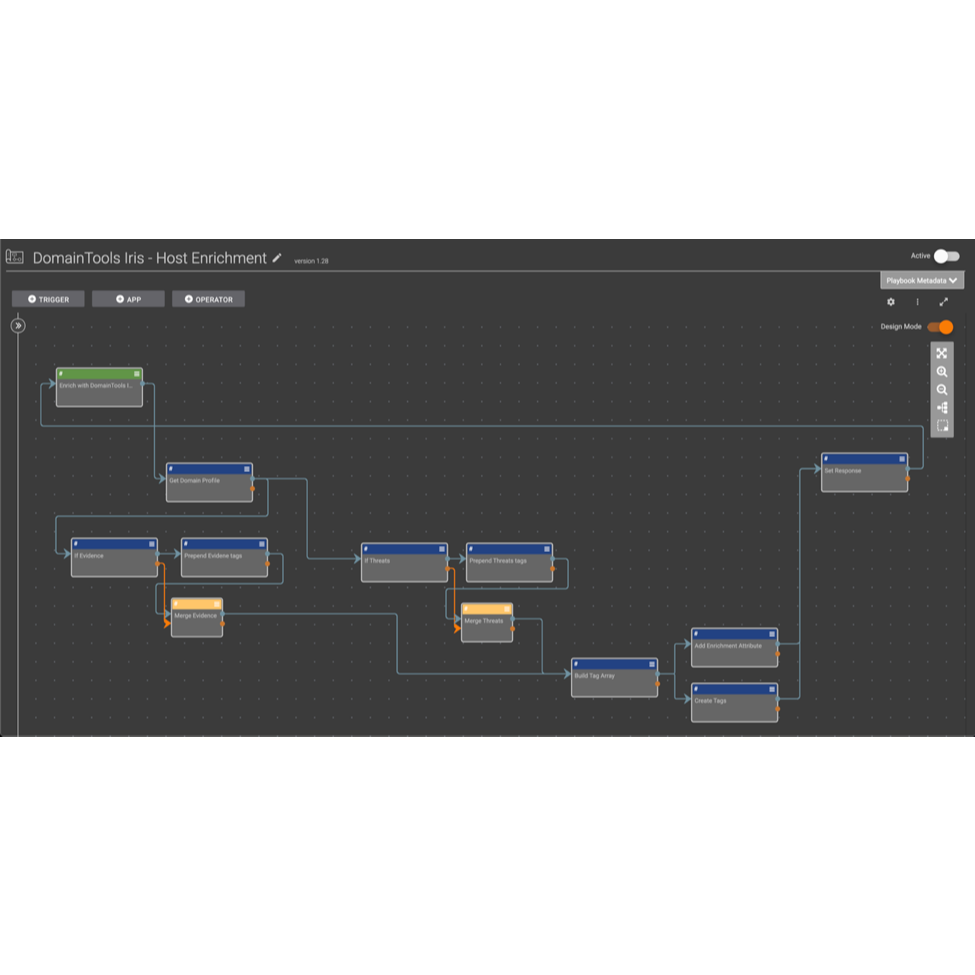
Playbooks
Built By ThreatConnect
Related Resources
Built By ThreatConnect


 Polarity
Polarity