Posted
ThreatConnect® and DomainTools®, have officially partnered to deliver the DomainTools Iris Investigate Playbook App. By combining the data enrichment and domain monitoring power of DomainTools Iris Investigate with the automation capabilities of ThreatConnect Playbooks, you can now prioritize and mitigate threats more efficiently.
DomainTools Iris Investigate Playbook App
We’ve identified several use cases that this integration will enable however, this is just the beginning. We fully expect more use cases and needs to be discovered as our joint customers begin to leverage this Playbook App to its fullest. Here is what you can do with this powerful integration:
- Retrieve Risk Scores, ThreatProfile, Evidence, and Domain Profile intelligence from Iris. These diverse datasets serve as decision factors for scoring domain indicators or taking further actions inside ThreatConnect.
- Auto-pivot to expand threat investigation out to additional levels by quickly discovering potentially malicious infrastructure connected to a domain
- Perform auto-enrichment of domain artifacts that are part of alerts or incidents with Domain intelligence dataset by submitting single or multiple domains at once. The integration provides all of the information from DomainTools Iris as output variables inside of ThreatConnect platform, which can be used for making decisions in automated processes.
- Perform a Reverse Search on one or more search fields, such as IP address, SSL hash, email, or more, and the integration will return Domain Profile information for any domain name with a record that matches the search.
- Build automated processes between analyst work in the Iris UI by monitoring for Search Hash results or matching Tags. Users can begin their investigation in the Iris UI and automatically bring the results into ThreatConnect for further correlation and analysis.
So far, we’ve explained what you can do with this Playbook App, now let’s get into how you do it. To go along with this integration, we built two ready-to-use Playbook templates with plans to release more templates in the future. These following Playbook actions are available:
- Get Single Domain Profile
- Get Multiple Domain Profiles
- Search & Pivot
- Get Search Hash Results
- Parse Domain Profile Results
Available Playbook templates:
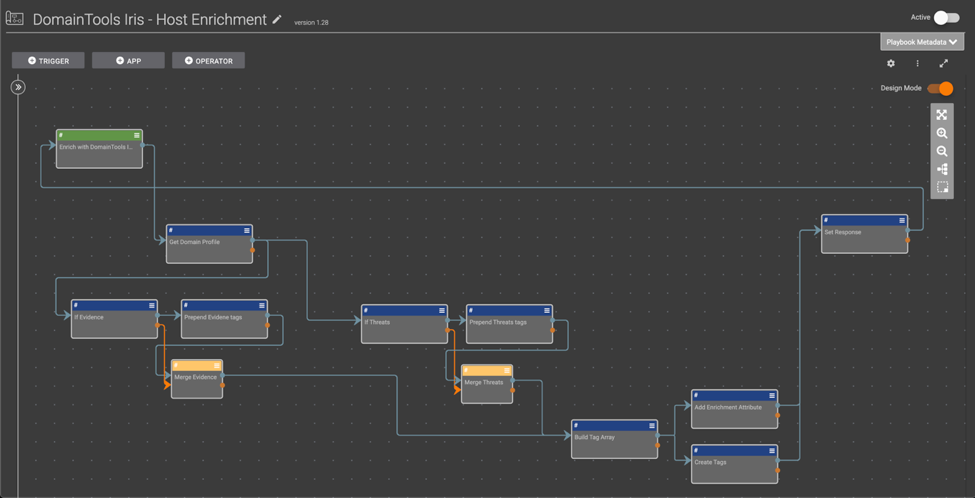
DomainTools Iris – Host Enrichment
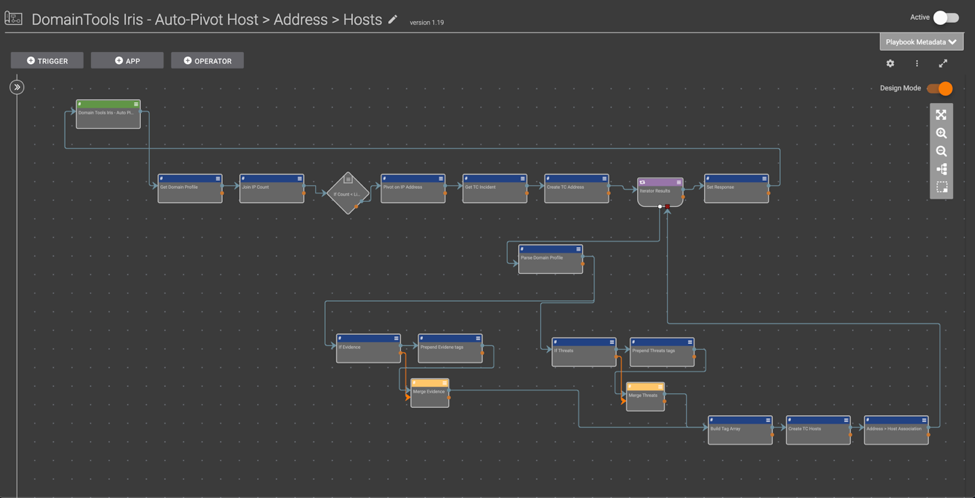
DomainTools Iris – Auto-Pivot Host > Address > Hosts
See an overview of the integration:
So far we’ve explained what you can do, how you can do it, so let’s wrap up with why it’s important. This integration allows researchers and threat hunters to monitor changes in adversary infrastructure and automate investigative and hunting actions. By automating these tasks, you free up human minds for highly-cognitive human tasks.
If you’re a ThreatConnect customer, please reach out to your dedicated Customer Success Team for more information on utilizing the DomainTools Investigate Iris App. If you’re not yet a customer and are interested in ThreatConnect and this integration, contact us at sales@threatconnect.com.