Posted
Security operations teams are super busy and it’s not getting any easier. Analysts need to be able to get more done in their day by working smarter, faster, and better. We get it and we hear you! In this release of ThreatConnect 6.5, we have supercharged the ThreatConnect Platform with some exciting updates:
- Threat Intel, Security Analysts, and Incident Responders are going to love the updates we’ve made to our graph and visualizations, making it easier and faster to view and discover connections that exist between indicators.
- For MDR, MSSPs, and enterprises with multi-tenant deployments, we’ve introduced the Super User for Analysts.
- And a few other updates in the Platform like improvements to our API, the metrics library, and enhancements to improve the user interface (UI) and experience (UX).
Explore in Graph
The latest updates to ThreatConnect’s Graph provides you with an improved threat intelligence and investigations experience through better visualization and more context. This allows you to connect indicators and other intelligence faster than ever before. You’ll be able to do even more in Graph as we continue to release new functionality in Explore in Graph in upcoming releases.
With our first release of Graph, you got the ability to pivot within CAL (Collective Analytics Layer) to understand the complex, bi-directional relationships that exist with a particular IOC like WHOIS registrations, DNS details, host data, subdomains, etc.
The updates to Explore in Graph in this release build upon the current capabilities by enabling you to pivot on indicator-to-indicator relationships in ThreatConnect and indicator-to-indicator relationships that exist in CAL. As your investigation continues, you can import new indicators that are discovered or pivot further on Owners within ThreatConnect. Over time, analysts will come to understand the indicator and can then tell a meaningful narrative around it.
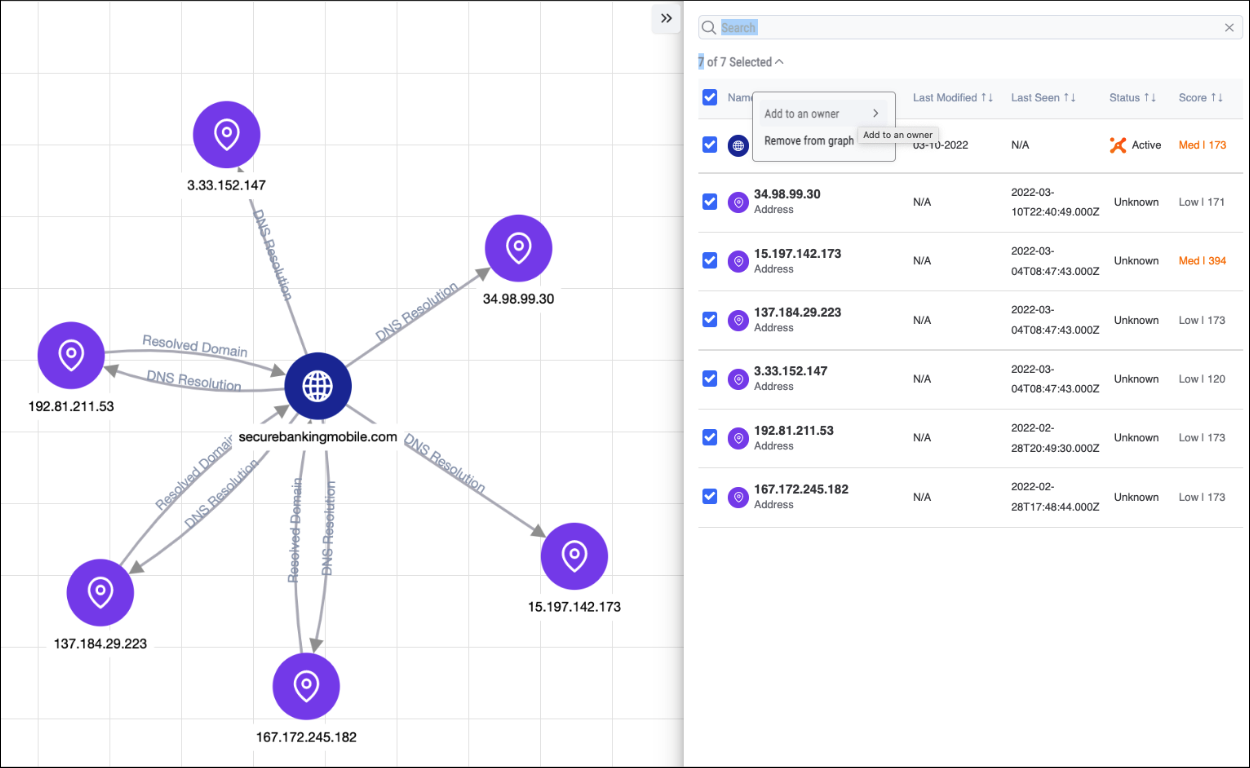
Import Indicators from the Graph
With the updates to Explore in Graph, you can perform investigations faster and easier by:
- Importing indicators that you discover by adding them to existing or new Groups
- Easily seeing relationships between CAL and other IOCs
- Pivoting in multiple Owners on the same Graph to see relationships that exist across Sources, Orgs, and Communities
Super User
Super User is a user within the ThreatConnect Platform with the ability to see across multiple organizations or environments. For multi-tenant users, having a Super User account is critical because it allows them to easily operate across multiple customers without needing to manage multiple accounts, perform multiple logins to the platform, and just make an analyst’s daily activities easier.
Super User allows analysts to have a single pane view for all attacks across their customer base or various environments. This means that they can quickly investigate and confirm whether an indicator or attack is happening with other customers/organizations from a single view and quickly take action.
Super User’s also get added UX and UI improvements. For example: in “My Intel Sources,” analysts can quickly see and view all organizations or just the organizations they are responsible for.
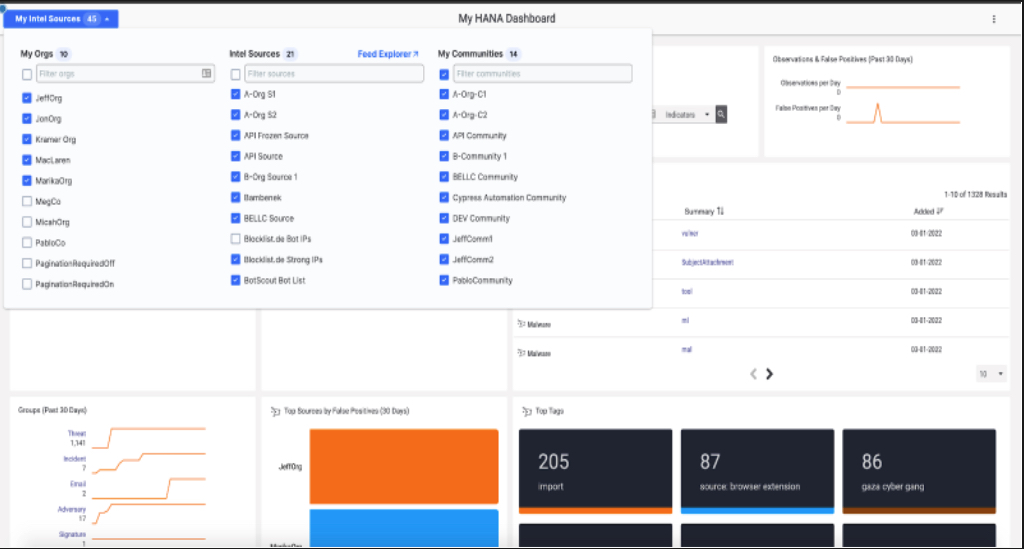
New Super User UI and Dashboard
With Super User, you can reduce complexity and save time by:
- Quickly assessing intelligence and cases across customers, for example: offering a view that enables an effective way to correlate intelligence across organizations, especially in cases where you want to check artifacts seen across organizations.
- Leveraging views across all organizations, sources, and communities
- Sharing Playbook and Workflow Templates across environments
Other Super Cool Updates
We have added some other super cool updates in the 6.5 release to improve the user experience for analysts and leaders.
- Link Intel to Cases with updates to our API
- Workflow Metrics – Analyst Efficiency
- Add last modified date time stamp
- Granular Due Dates
- “Contains” / “Equals” Checkbox on Browse Screen
Automate Linking of Intelligence to Cases
ThreatConnect has improved the automation capabilities in the ThreatConnect Platform to make the lives of threat intel and security operations analysts easier. With this update to the V3 API, users can associate intelligence with cases programmatically. Manually associating intelligence within cases can now be automated, saving more time for analysts.
Workflow Metrics – Analyst Efficiency
Security leaders need access to metrics to measure operations, which is traditionally a manual and time-consuming process. We continue to add more workflow metrics to help leaders identify whether or not current tools, processes, and automations that are set up are scalable to drive operational efficiencies to meet business needs. In the 6.5 release, we have introduced the Analyst Efficiency metric, and the first dashboard card is a leaderboard view of analyst performance for case closure.
With Analysts Efficiency Metrics, SOC leaders can quickly understand their team’s workload and make changes to increase efficiency and prevent burnout. Stay tuned for more Analyst Efficiency Metrics to be added in future releases.
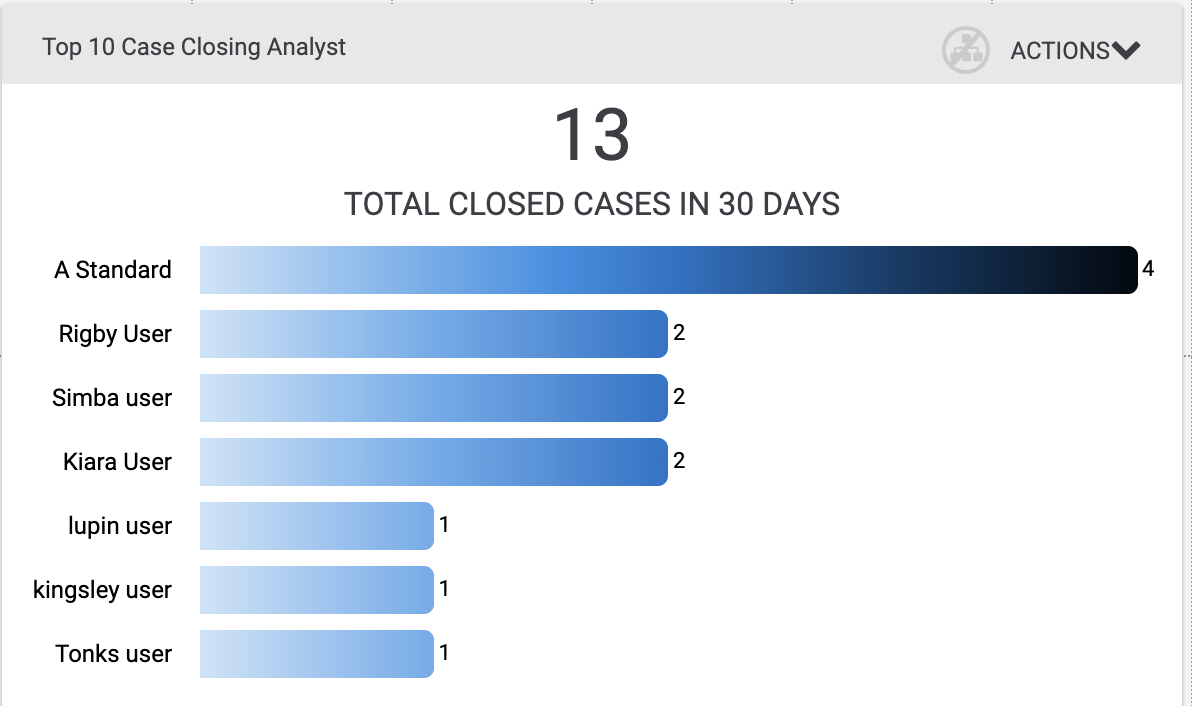
Top 10 Case Closing Analysts Card
Time to upgrade!
Customers should reach out to their Customer Success team for any questions about the 6.5 release and getting upgraded.
For more information on these new capabilities and how ThreatConnect can help your organization super-charge your threat intelligence and security teams, please reach out to sales@threatconnect.com.

