Posted
ThreatConnect 6.3 introduces major core architecture changes to the TIP side of our platform with the introduction of New Group Objects as well as major changes to the SOAR side with the addition of Workflow Attributes and Workflow Metrics.
In 6.3, we’re giving you new ways to adapt to the Platform. We’re adding Attribute support to Workflow, which means that SOAR customers can track whatever metadata they need to as part of a Case: whether that’s business unit, impact types, geography, internal reference codes, and more! We’re also expanding our TIP data model to support several new Group types to better manage your Threat Library.
Lastly, we are adding valuable Workflow Metrics like Mean Time to Detect (MTTD), Mean Time to Resolve (MTTR), and False Positive Ratio so that you can monitor and maximize your SOC team’s efficacy and make incremental changes to improve your security posture over time.
Ultimately this release is all about furthering ThreatConnect’s goal of allowing our platform to adapt to your processes rather than the other way around.
New Group Objects
Over the years, STIX has become the gold standard when it comes to categorizing Threat Intel. With the addition of new group objects, we better align with STIX taxonomy and will allow you to better map and manage your Threat Library.
New Group Objects include:
- Attack Pattern
- Malware
- Vulnerability
- Tactic
- Tool
- Course of Action
Previously, analysts had a problem when bringing over certain types of intelligence into ThreatConnect. For example, many would want to bring Vulnerability Objects into the platform and would need to use Threat Objects as a ‘catch all’. This was essentially “putting a square peg into a round hole” – things didn’t match up and important threat data and fields were being dropped. The addition of new Group Objects fixes this problem.
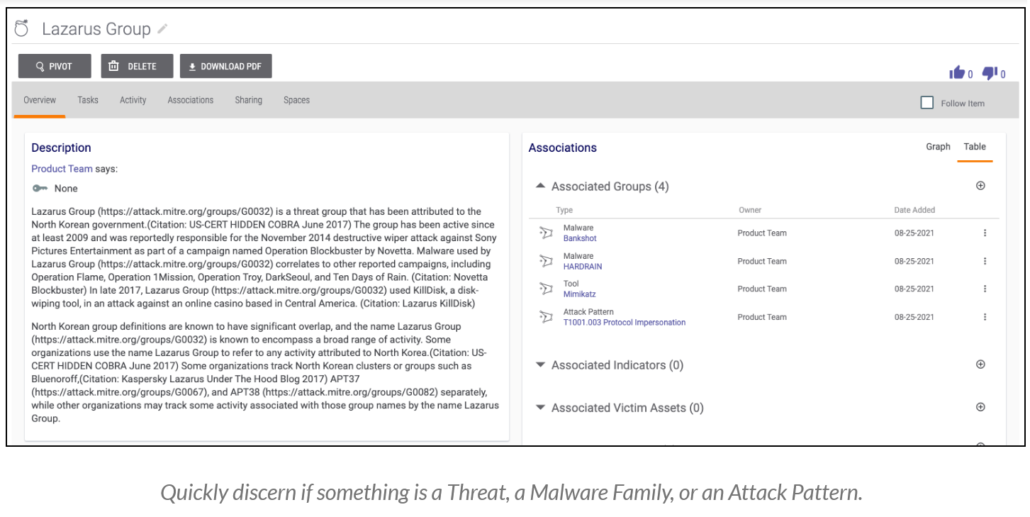
Instead of wondering if a Group is; a Malware family name, a MITRE ATT&CK technique, or Threat Actor Group, you can now quickly see and understand exactly what you’re viewing. The release of these new Groups enables ThreatConnect to map to STIX objects more effectively and lays the groundwork needed to expose more data from the ThreatConnect Collective Analytics Layer (CAL™) in the future.
Ultimately, this helps to ensure that the Threat Library you build with ThreatConnect is approachable, collated, and equipped to help your security teams when they need it most.
Workflow Metrics
Gaining insight into the SOC team is critical for security leaders. They typically have large teams that are dealing with a high volume of cases and escalations. What they need is more granular information about the tools, processes, and people in their environment to define clear and realistic short-term and long-term strategies.
In ThreatConnect 6.3, you can now easily create dashboard cards on three key performance indicators (KPIs):
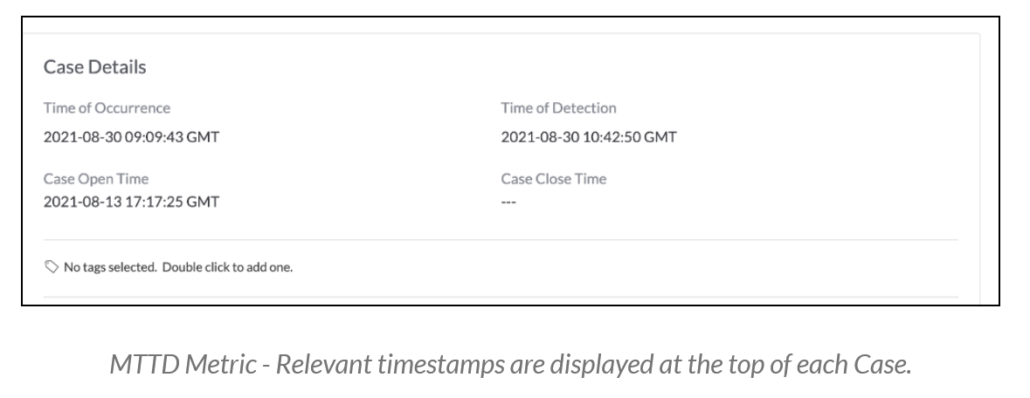
- Mean Time to Detect (MTTD): The average time it takes to discover a security threat or incident.
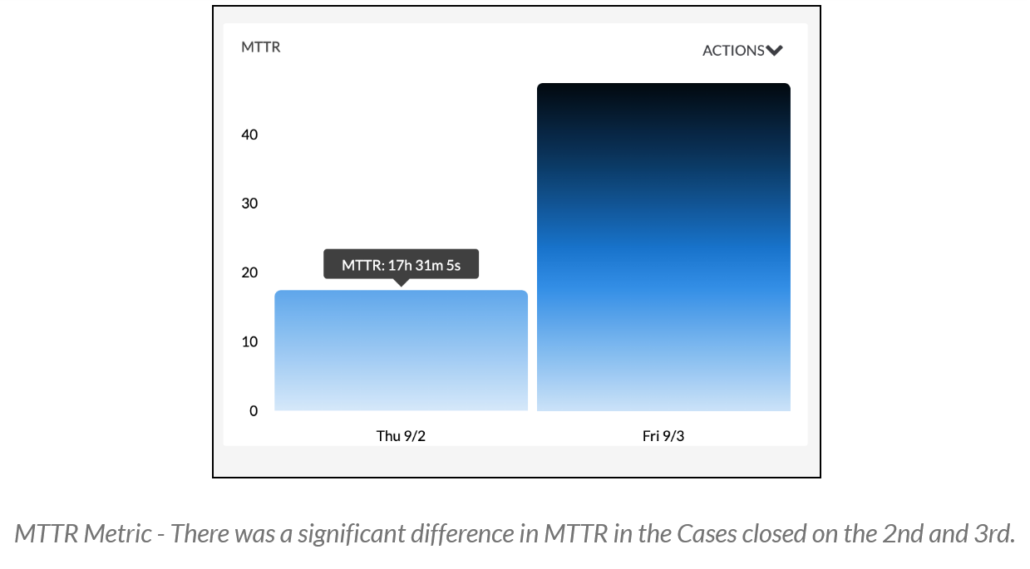
- Mean Time to Respond (MTTR): The average time it takes to control and remediate a threat.
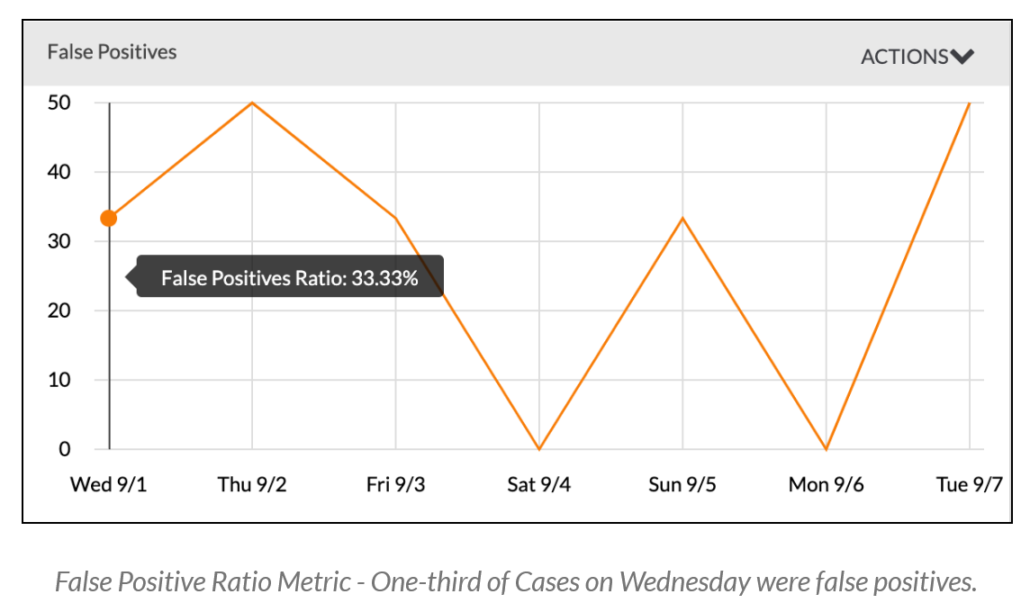
- False Positive Ratio: The percentage of alerts that upon investigation are revealed to be not valid threats.
These metrics will help you see whether current tools, processes, and automations in place are helping the organization to identify and remediate threats faster or not.
Other benefits include:
- By measuring MTTD, you can bring down lurking threats sooner and measure and then improve upon your overall security posture.
- By measuring MTTR, you can maximize staff efficiency and optimize your team’s security tools and processes.
By measuring FP Ratios, you can understand if changes made to the teams, tools, and processes have resulted in a positive impact on the team’s overall accuracy and determine if the changes in this ratio coincide with other changes in the organization (i.e., policy changes, the deployment of additional security tools, hiring and onboarding additional or new analysts, etc).
Workflow Case Attributes
You now can create Attributes for Cases. Attributes have long been part of the TIP side of the platform and now we bring them to the SOAR side. Case Attributes are key data sets that can be added to a Case, and they provide an excellent way to organize and categorize Case metadata. You can add anything of value to a Case, such as relevant research and analysis associated with Cases, the source that triggered an alert, affected network or business units, and recommended courses of action. The sky’s the limit!
Other benefits include:
- Allows team leaders to ensure that the most important elements needed on a Case are captured and allows coordination between teams that have different Case formats.
- Provides your SOC team with more context while working on Cases – this extra context will help them to make fast more informed decisions.
We are excited to see how you leverage these new features! For more information on these capabilities and how ThreatConnect can help your organization, please reach out to our Customer Success Team or email us at sales@threatconnect.com.
