Posted
Event prioritization means organizing your events and picking the most important items to address first. The reason for this is simple and hopefully obvious: you want to identify which event is more important to you to help you determine which task/event you want to commit to first and where immediate attention is required.
How importance is defined is the key. Importance, in this case, has a lot to do with relevancy and the potential impact that an alert can have on a particular organization if corroborated. This could typically be done via a correlated rule triggering, where event ‘a’ and event ‘b’ have met a specific condition and therefore are deemed essential and prioritized. The problem with manual prioritization is that you never have enough time to review every event that comes into the SIEM.
This brings us to the importance of automation.
Automating your SOC and how it relates to event prioritization
The word automation can sound like a complex and challenging task to accomplish, but it doesn’t have to be. Orchestration and automation are simple concepts with several moving parts. An important thing to remember when discussing how a SOAR solution can help with event prioritization is that it doesn’t stop at automation and orchestration. Let’s dig into that. By definition, three characteristics make up SOAR: a Threat Intelligence Platform (TIP), Security Orchestration and Automation (SOA), and Incident Response Management (IRM). ThreatConnect provides all of these components, making intelligence-driven automation and incident response an entirely achievable goal.
When done correctly, this leads to the following outcomes across your organization:
- Bolster staff productivity through reducing workload with automation, orchestration, and templated workflows
- Improve situational awareness and make more confident decisions by leveraging historical data and allowing processes to adapt to changing environments
- Reduce dwell time and time to respond to decrease the overall impact of an incident
So where do you start?
Enriching all correlated event sources with threat intelligence is a great place to start. You will see an instant benefit to prioritizing the triage of those security events as the number of actionable events goes from everything to a much smaller manageable list that can be addressed by your SOC analysts. This is achieved by adding threat intelligence to correlated events and adding the simple rule of “if match with the enriched data source, then escalate to higher severity and magnitude/risk score”. Doing this will decrease the number of potential false positives and increase the impact of the correlated event.
Below is an outline of a sample workflow depicting how automating event prioritization could work in ThreatConnect – beginning with a SIEM event.
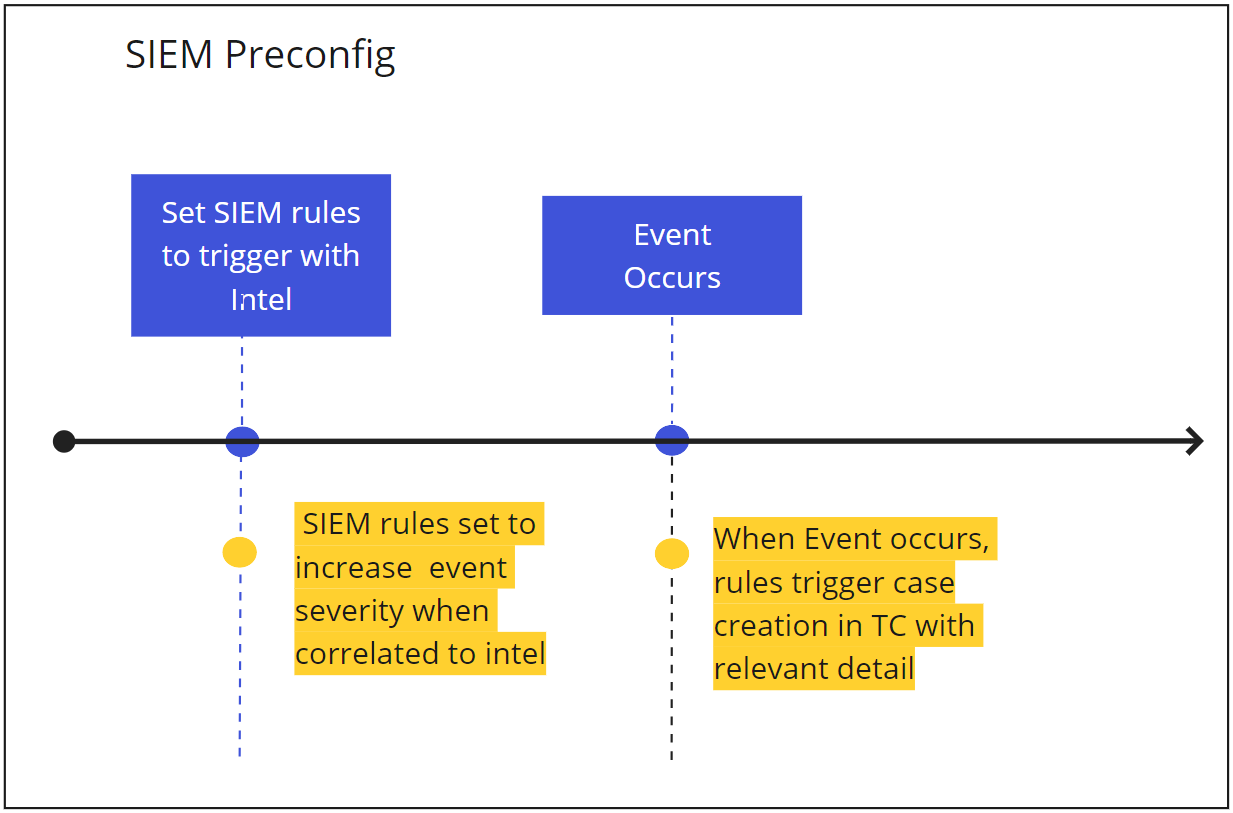
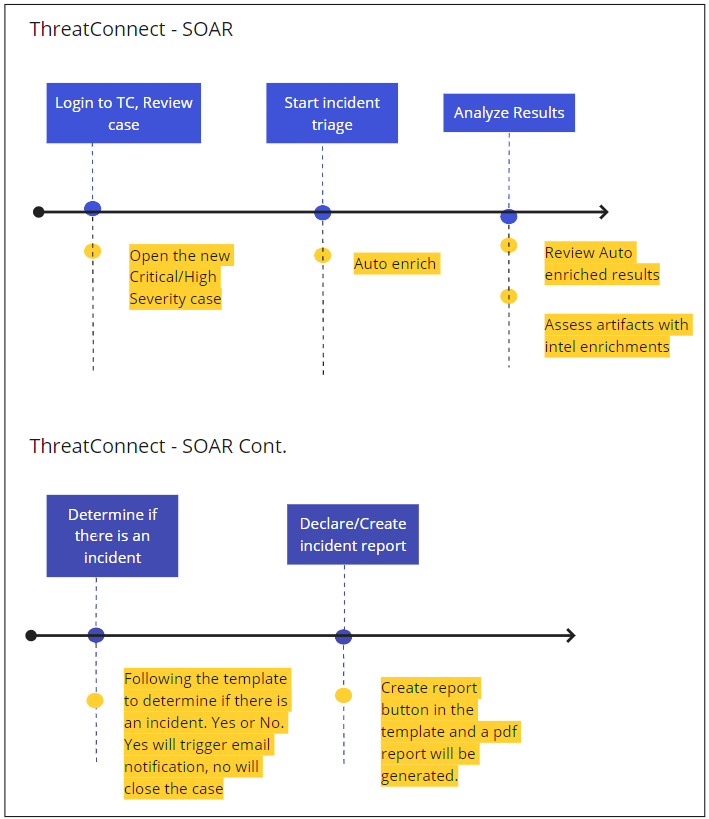
Automated incident and case ingestion
So you have correlated your event, now what? Let’s do something with it! As shown in the image below, ThreatConnect automatically ingests the incident and starts triage of the related alerts or artifacts. Additional 3rd party enrichments (DomainTools, Hyas, VirusTotal, ThreatGrid, Recorded Futures, AbuseIP, etc) can provide additional information at the click of a button.
Previously, when done manually, this would normally require several minutes of analyst time being wasted changing screens, logging in and out of various tools. Not to mention the added level of frustration often experienced during these tedious tasks.
After enriching the incident with the information provided from directory services, 3rd party enrichments, and CAL and ThreatAssess, you can move on to analyzing the results. After making the determination that this is a real incident that needs to be sent to the incident response team or escalated to management (or both!).
By using ThreatConnect’s Workflow templates, ensure that SOC processes are followed down to the letter – automating where possible and allowing for analysts to focus on the areas that require additional attention.
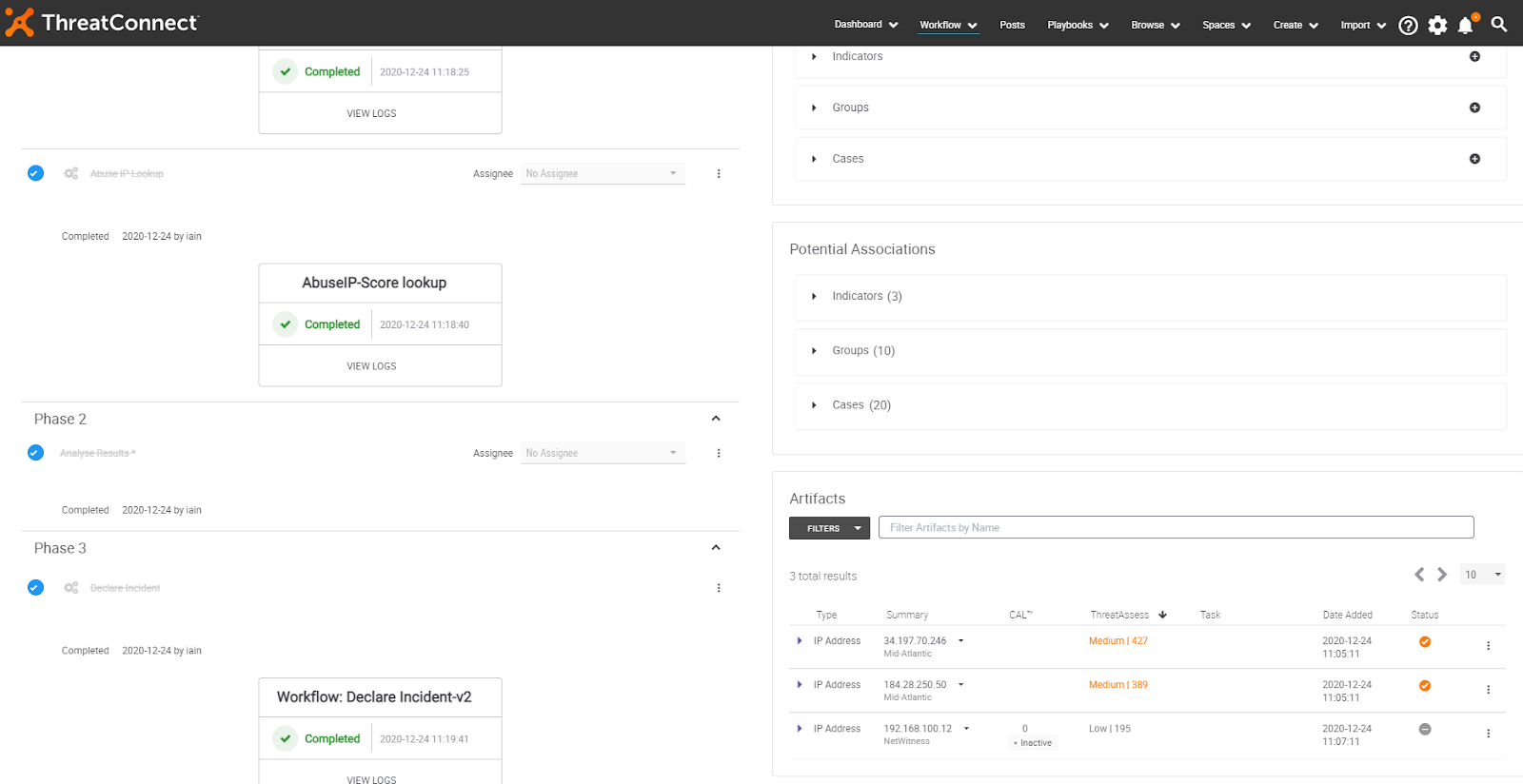
Visualization of threat vectors, observables, and types
Many don’t feel like there is such a thing as a useful Dashboard. I used to be one of them. The problem used to be that it was just a bunch of useless and sometimes static images that nobody really paid attention to. What makes the way we present the information in ThreatConnect different is that the information within the Dashboard is actually useful, updated regularly, and helps you keep track of what’s important to both the analyst and SOC management. Allowing you to gather metrics from executed 3rd party enrichments, cases created, reported false positives, observations (threat intel matches) from your SIEM, EDR, etc.
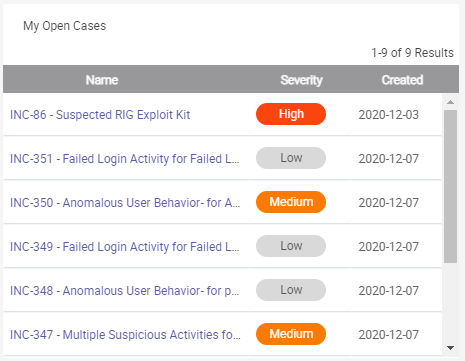
Dashboard cards like the examples below can be used to show useful information like the number of open cases and IOC’s observed related to threat actors.
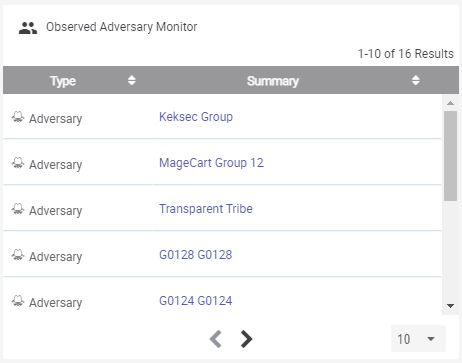
These cards are completely customizable in size and content. The card on the left shows the organization’s current open cases and their severity. While the card on the right shows an observation monitor for active adversaries relative to the organization’s relevant threat landscape.
Conclusion
Security teams across organizations of all shapes and sizes have a to-do list that is forever growing, yet they’re continuing to deal with menial, repetitive tasks. Automating event prioritization enables teams to properly prioritize and lean into a more predictive approach to security.
If you’re interested in seeing in more detail how this could help your organization, contact us at sales@threatconnect.com
