Posted
There are many definitions for Threat hunting from an active cyber defense activity that proactively and iteratively searches through networks to detect and isolate advanced threats that evade existing security solutions to the practice of proactively searching for cyber threats that are lurking undetected in a network.
These are just two of the many definitions widely published but how do you go about implementing them as a working model?
In a previous article, “SOAR: Reactive Threat Hunting” we discussed a traditional methodology using alerts to initiate the Threat Hunting process that identifies relevant indicators and intelligence from existing collections correlating the results with the SIEM as the alert occurs thereby defining Threat based on existing activity which enables the definition of relevant tactical Threat Intelligence that enables the ongoing identification of potentially related activity.
Can we expand that model to answer critical questions such as:
“What do we know about x and how does it affect us today?”
In the ThreatConnect Podcast: Episode 4: Threat Hunting, members of ThreatConnect’s Research team discussed this very topic, providing insights into their methodologies for tactic, infrastructure, capability and human behavior based Threat Hunting using a variety of tools, many of which were external to ThreatConnect itself. Well the good news is that ThreatConnect provides a solution that supports these methodologies using a combination of Orchestration, Workflow and Analyst activities – and demonstrates the power of offering tightly integrated SOAR and TIP capabilities in one platform
Don’t worry if you think this is all sounding complicated – the problem may be, but the solution is not.
I like to think of Threat Hunting as an art form rather than a science requiring the practitioner to feel their way through the information. This is just one of many possible and in this case, simplified methodologies to highlight the process. But it is easy to see that subject matter expertise and a detailed understanding of the environment, how to integrate it with existing systems, and that all important report generation capability is a skill in itself and one that can be time consuming and complex to both learn and execute.
With ThreatConnect the tools to accelerate this process are at your fingertips.
I consider a common analyst driven activity within ThreatConnect when hunting for information to be:
- Search for keywords
- Review results
- Identify infrastructure, capability and tactics
- Search for indicators of compromise in detective controls
- Determine probable activity
- Report results
ThreatConnect’s Search and Browse features enable the identification of information relative to keywords, tags and temporal factors based on existing collections with simple to use options for analyzing the results and their associations but we can do much more because the results are only as good as your collection.
Context aware Investigation Links help an analyst extend their investigation beyond the existing collection, while integrating with perimeter and host defensive technologies as well as SIEM solutions enable the results of the investigation to determine possible activity within our organization.
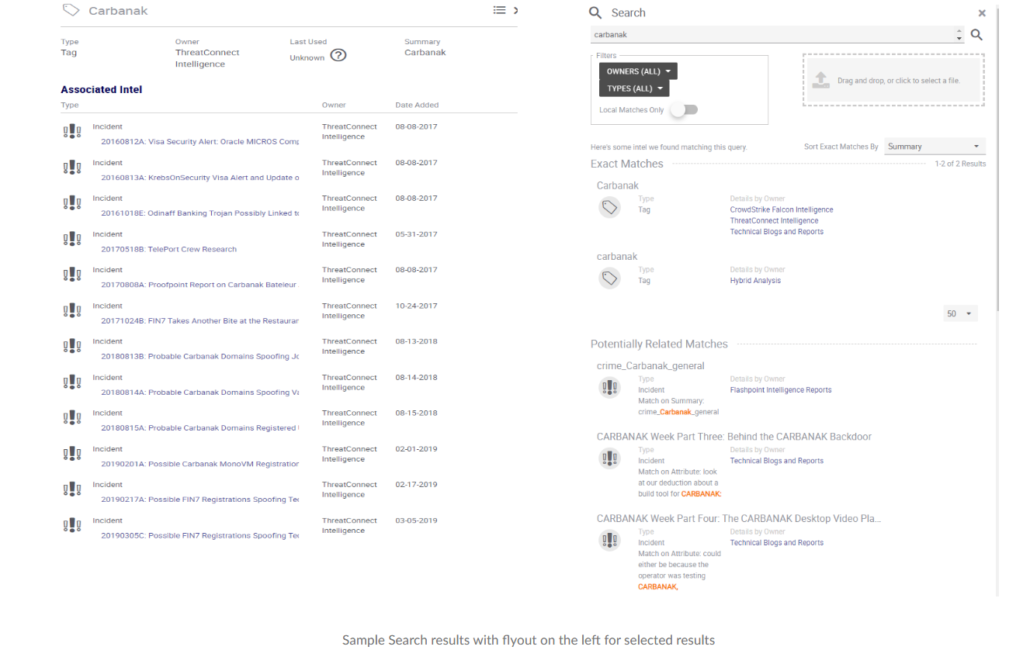
“Hold on, you said this could be automated through Orchestration and Workflow but I’m not seeing it!”
That’s where SOAR enters the picture.
Now that we have the foundation for our model we can apply our automation using both Playbooks and Workflow.
Starting points can vary depending upon the role, the event, or the process teams want to instantiate. Whether manual or automated via a product integration or action, ThreatConnect supports nearly any entry point you can imagine and helps conduct the subsequent activity with build-in workflow and orchestration.
In the following scenario we start the process with a context aware trigger called a “User Action,” which an Analyst can use to manually initiate this process within the platform. But in order to reduce platform interaction to widen the potential user base and reduce the pressure on hard working Threat Intelligence Analysts, users could send their requests to an email address and receive a completed report by using the Mailbox Trigger instead.
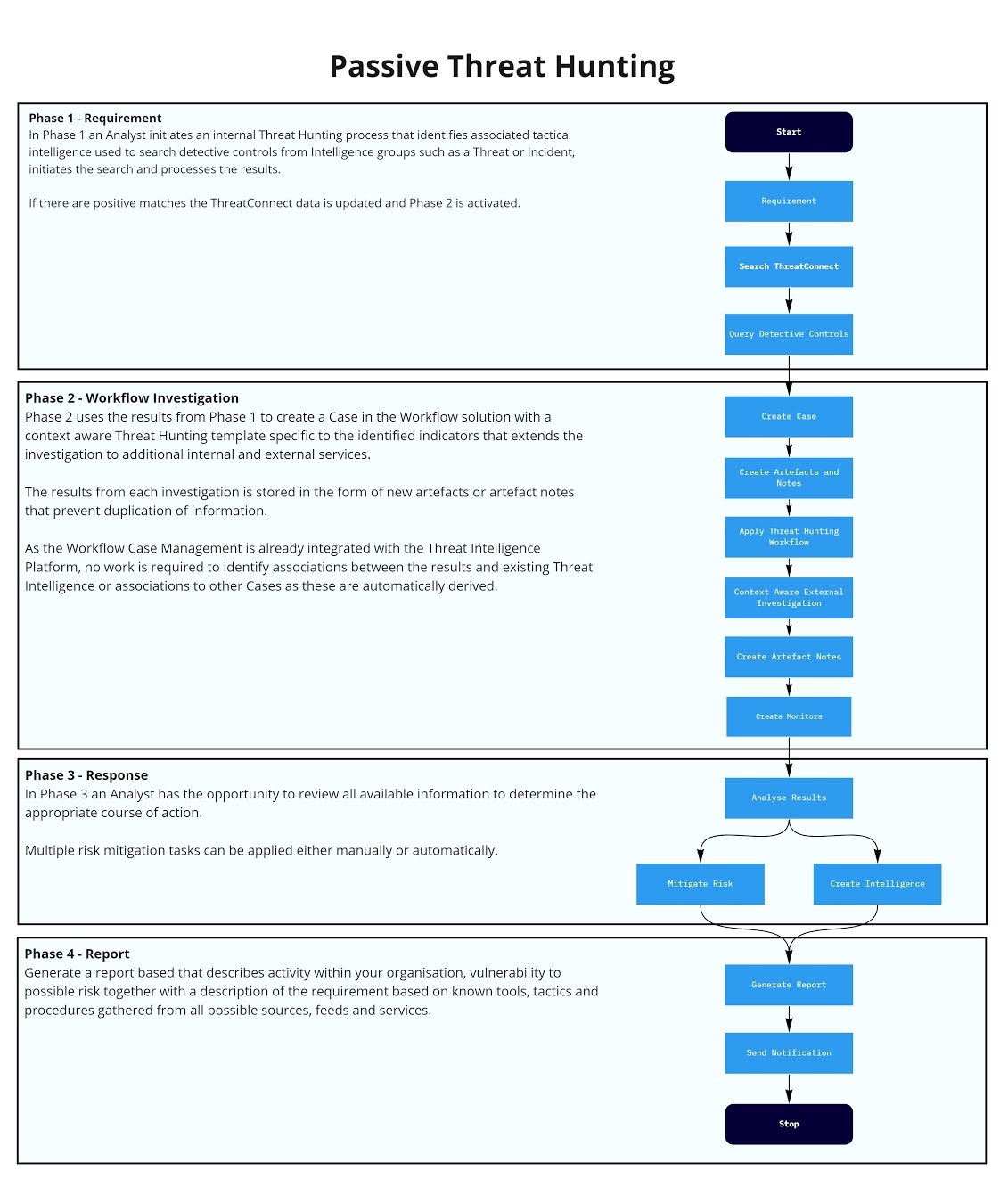
The high level workflow described above demonstrates the capabilities a fully integrated SOAR solution can provide with the modular approach provided by ThreatConnect, enabling the model to be tuned, modified and expanded upon based on the availability of source, feed and enrichment services and according to the users needs.
Orchestration enables the platform to receive the information request and create a Workflow Case applying a defined Workflow Template with minimal or no user interaction that searches for existing intelligence and adds it to the case in the form of artifacts and notes. As the Threat Intelligence Platform and Case Management are on the same system there is no need to do anything to build an association as that is automatic.
The workflow template identifies context aware external investigations to enrich the existing information while applying a common taxonomy to ensure continued monitoring. The aggregated results are used to query existing security controls.
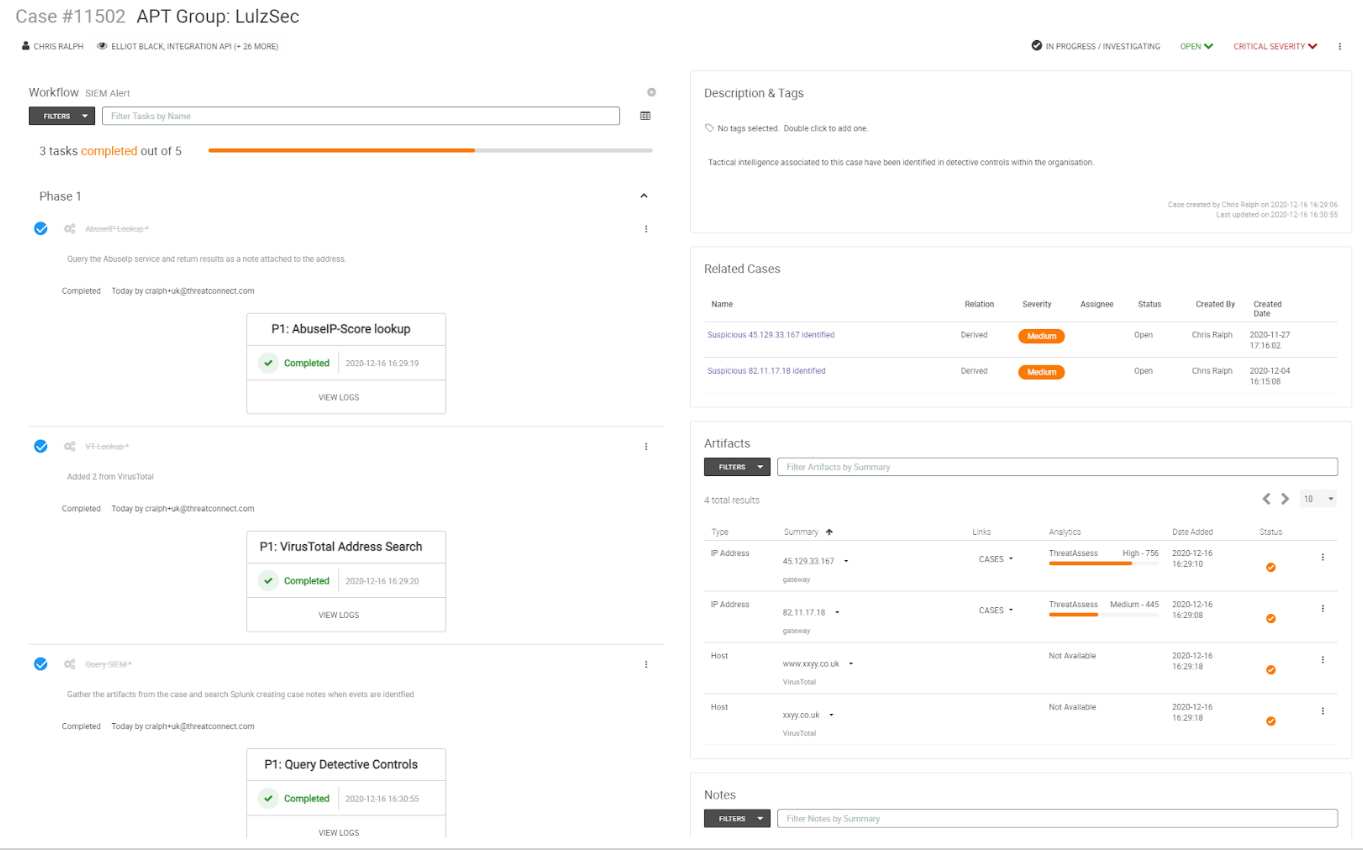
Finally, once the investigation is complete a suitable course of action can be defined, such as declaring an incident, generating a report, requesting additional information or sharing the results with detective controls either as a part of the defined workflow or through artifact enabled workflow orchestration.

