Posted
This is part 1 of a 2 part series.
In a previous article, “SOAR: An Incident Responder’s Best Friend,” we discussed the issues facing Incident Responders today and how Security Orchestration, Automation, and Response (SOAR) can help to reduce alert fatigue while providing faster, more timely responses. In this article we are going to expand on that theme to include all analyst roles because the need for SOAR is the same.
If we consider a typical enterprise to be composed of multiple technologies such as SIEMs, Vulnerability and Malware Analysis solutions as well as ticketing and incident management platforms (just to name a few), using SOAR to tie these together makes sense, but where does the workflow start? An incident responder is typically the last phase of an investigation when the incident is understood, a course of action has been selected and the cleanup begins. So one clear starting point is the initial alert; after all it is the volume and fidelity of the alerts that we are constantly hearing are the problem.
In many cases the alert originates from the SIEM as a Case, Offense, Alert or Incident that requires investigation and escalation depending on the outcome. So let’s start there and use “Alert” to define this group.
ThreatConnect provides a methodology that reduces the risk of high false positives when an intelligence feed is added to a SIEM for correlating tactical intelligence relative to existing information, enriching it for context and sharing the targeted intelligence results, and finally applying the result to the correlation rules used to define an alert. These steps significantly reduce false positives while giving the Analyst and Incident Responders the information they need at the time the event occurs.
Someone has to be first so I am going to use IBM’s QRadar to illustrate this approach.
The ThreatConnect solution includes:
- Analyst-driven indicator lookups from QRadar
- The creation of tactical intelligence Reference Sets
- Enrichment of existing Offenses from ThreatConnect
- Automated update of new and existing Offenses
This process helps facilitate a Priority Intelligence Requirement (PIR) for known intelligence related to an Offense that enables automated or analyst driven decision making.
At this point you may be asking, “But how does this work? I thought I needed a Threat Intelligence Analyst to define a PIR?”
Well, it depends…
Traditionally, operationalizing Threat Intelligence is carried out by the Threat Intelligence Analysts who translate the strategic requirements of the organization into operational intelligence in the form of PIR’s with ThreatConnect’s Threat Intelligence Platform (TIP) capabilities facilitating the collection and translation of information into actionable tactical intelligence. But this process can take time and besides, we are not all fortunate enough to have a dedicated Threat Intelligence team.
“How do I operationalize the strategic requirements of the organization?”
Well it’s actually quite simple. The great news is that you already have the starting point defined – for QRadar it’s your existing Offenses which are already aligned to the security threats facing your organization. As a part of the initial integration, ThreatConnect’s template-driven orchestration will query your QRadar instance for active Offenses, extract relevant information, and hunt for known intelligence using existing collection methodologies and external services that are then added directly to the Offense.
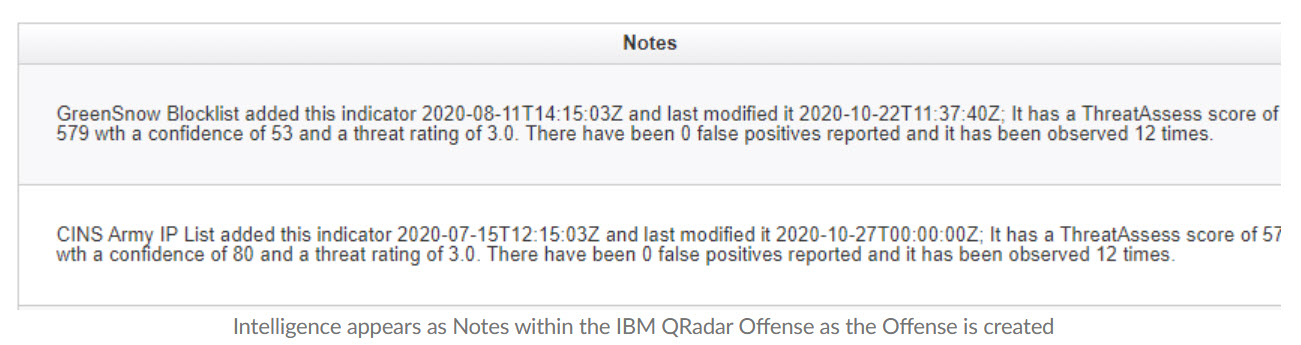
The best part is that you get to define what is relevant and what sources to include or you can simply use them all.
A tagging taxonomy enables Dashboard visualization and reporting within the ThreatConnect Platform and that same taxonomy enables the creation and update of targeted, relevant Intelligence based Reference Sets that, when applied to existing rules, reduce false positives creating a continuous application of targeted, high fidelity Threat Intelligence to existing security controls.
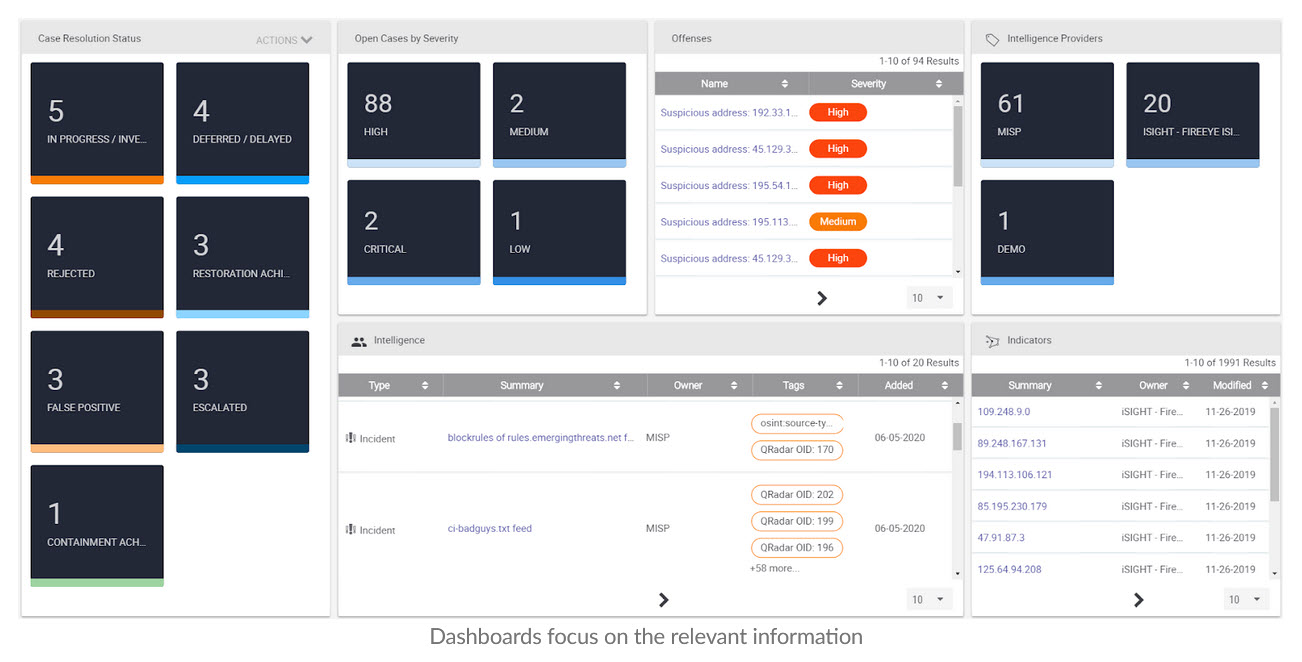
“How is this going to help me move forward?”
Well again that is a part of the solution. In this example, using the QRadar Offense custom actions we can post information as the offense is created to ThreatConnect’s Playbook Orchestration which processes the results and repeats the initial threat hunting exercise, thereby supporting the PIR: “What is known about x” and updating the Offense notes with targeted intelligence. This instantly forms a continuous loop that is truly operationalizing Threat Intelligence.
“That’s great but I don’t have QRadar, so will this still work for me?”
Not to worry, that was just an example and the methodology is the same regardless of the vendor. The model may change slightly based on how the Alerts are defined but the outcome is the same. Intelligence is provided to those that need it when they need it most. It’s a bit like the “Room of Requirement” for all you Harry Potter buffs out there.
Of course this is just the start of an exciting journey. Unification of a Threat Intelligence Platform, Case Management, Orchestration and Automation in one platform means that tasks that would normally require significant initial and ongoing development resources, manual intervention or escalation based on activity or results can now be automated according to your processes, integrating your security technology stack in a way that creates a single source of truth that changes to suit your environment.
