Posted
The 2025 SANS Cyber Threat Intelligence (CTI) Survey reveals a maturing discipline facing persistent challenges: lack of process formalization, difficulty proving ROI, and an urgent need to communicate value to business stakeholders.
This article summarizes the survey’s key findings and explains how ThreatConnect’s Intel Hub Platform – which combines our TI Ops, Risk Quantifier, and Polarity tools – directly addresses them. Each section below outlines a common CTI challenge, what the survey reveals, and how ThreatConnect solves it with specific, actionable features.
From Intelligence to Business Impact: 2025 SANS CTI Survey + How ThreatConnect Helps
- Challenge: CTI Workflows Are Still Largely Ad Hoc
- Challenge: CTI Teams Struggle to Demonstrate ROI and Gain Executive Buy-In
- Challenge: Threat Hunters Lack Seamless Access to Contextual Intelligence
- Challenge: Internal Data Remains Underutilized in CTI
- Challenge: Feedback Loops and Effectiveness Measurement Are Weak
Platform Summary: ThreatConnect as a Cyber Resilience Enabler
Conclusion: Aligning CTI with Business Outcomes
1. Challenge: CTI Workflows Are Still Largely Ad Hoc
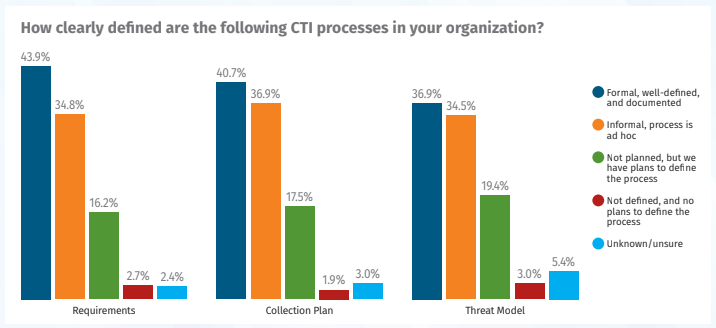
Survey Insight: Most organizations do not have well-defined workflows for CTI processes such as collection planning, threat modeling, or reporting.
Why This Matters: Ad hoc intelligence processes are difficult to scale, audit, or improve. This also makes it harder to prove CTI’s value to stakeholders.
How ThreatConnect Helps:
- Workflows enable repeatable CTI processes across collection, enrichment, analysis, and reporting.
- Workflow-to-Report Automation allows teams to convert structured workflows directly into deliverable reports.
Example: A CTI team monitoring executive phishing can create a workflow that pulls in dark web indicators, enriches them with VirusTotal and ATT&CK data, links them to threat actor profiles, and generates weekly executive protection briefings—automatically.
2. Challenge: CTI Teams Struggle to Demonstrate ROI and Gain Executive Buy-In
Survey Insight: Executive participation in CTI planning has grown (52%), yet many teams still cannot clearly demonstrate business value or secure budget.
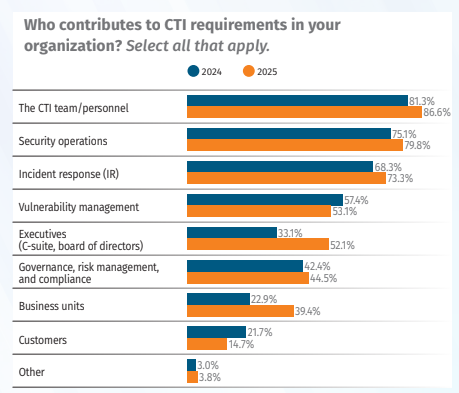
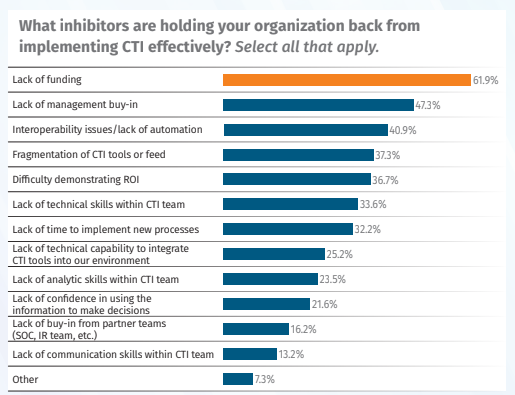
Why This Matters: Without measurable ROI, CTI teams risk being deprioritized in favor of other security initiatives.
How ThreatConnect Helps:
- ThreatConnect’s Intel Hub quantifies the financial risk of specific TTPs using proprietary models mapped to your assets, vulnerabilities, and controls.
- Risk-Based Intel Requirements allow CTI teams to prioritize intelligence collection based on highest potential business impact.
Example: The executive team makes a strategic decision to prioritize a particular malware family. Using ThreatConnect’s Intel Hub, the intel team models it via ATT&CK, and the risk team applies real financial impact to those TTPs (for example, $950k). Threat hunters are given the highest impact TTPs to search for and remediate, with all actions tied back to that $950k risk reduction. This becomes the basis for an evidence-based pitch for strategic initiatives and new resources.
3. Challenge: Threat Hunters Lack Seamless Access to Contextual Intelligence
Survey Insight: Threat hunting is the most common use case for CTI. MITRE ATT&CK is the dominant framework, but it is often siloed from operational workflows.
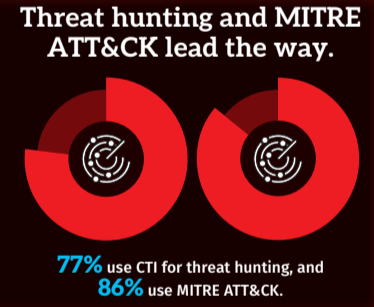
Why This Matters: Swivel-chairing between tools reduces efficiency and increases the risk of missing key threat insights.
How ThreatConnect Helps:
- Polarity Overlay runs directly on top of hunting tools (e.g., EDR, SIEM), scanning the interface for observable data in real time.
- Contextual Overlays automatically link on-screen observables to ATT&CK TTPs, threat actor profiles, and prior cases.
- AI-Powered Summaries provide fast context to support triage and decision-making.
Example: A hunter reviewing a suspicious PowerShell command in CrowdStrike sees Polarity detect and highlight T1059.001. It surfaces FIN7-linked behaviors, related malware families, and prior incidents—all without leaving the current screen.
4. Challenge: Internal Data Remains Underutilized in CTI
Survey Insight: 90% of organizations use external threat intelligence sources, but only 64% incorporate internal sources like incident reports, vulnerability data, or security analytics.
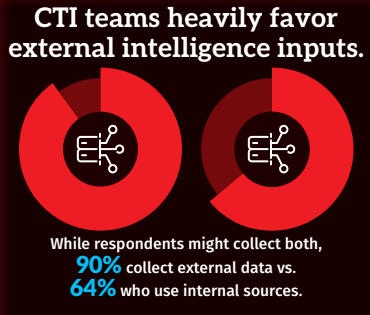
Why This Matters: External data alone can miss key context. Internal signals—such as where vulnerabilities exist, what’s been targeted recently, or how past incidents unfolded—help analysts prioritize what really matters in their environment.
How ThreatConnect Helps:
- The Intel Hub ingests and correlates internal sources such as:
- Past incident reports
- Internal vulnerability scan results
- Threat detection alerts (via SIEM, XDR)
- Endpoint or asset metadata (e.g., criticality tags)
- Correlates this data with external threat feeds and ATT&CK TTPs to deliver more contextual, actionable intelligence.
Example:
Your team sees chatter around a new ransomware campaign exploiting CVE-2024-32001. Rather than treating it as a generic alert, ThreatConnect checks:
- Whether the CVE is present in your internal vuln data
- Which assets are exposed, and whether they’re tagged as high-impact (e.g., payment systems)
- Whether this TTP matches patterns from recent internal IR cases
- Insights into this vulnerability will also be surfaced automatically by anyone performing an investigation using Polarity.
The result: your team prioritizes patching on high-value targets and notifies stakeholders with a high-confidence, business-relevant advisory.
5. Challenge: Feedback Loops and Effectiveness Measurement Are Weak
Survey Insight: Only 55% of CTI teams measure effectiveness; fewer have structured methods for collecting stakeholder feedback.

Why This Matters: Lack of measurement leads to stagnation, reduces perceived value, and undermines long-term resilience.
How ThreatConnect Helps:
- Engagement Tracking lets teams measure how reports are consumed and referenced.
- Feedback Integration via forms and metrics dashboards supports continuous improvement.
- CTI Metrics Framework Support aligns output to models like CTI-CMM.
Example: A CTI team publishes a quarterly landscape report. ThreatConnect tracks readership, records which sections inform new detection logic, and collects direct feedback through a linked form. The team uses this data to prioritize content for the next report.
Platform Summary: ThreatConnect as a Cyber Resilience Enabler
Across all findings, the 2025 SANS CTI Survey points to one overarching need: CTI must evolve from activity to impact. That’s where ThreatConnect’s approach to Threat & Risk-Informed Intelligence makes a difference.
- Intel Hub for correlating threat data with business risk and internal context
- Workflows to formalize and automate the CTI lifecycle
- Polarity Overlay for operationalizing CTI in real-time analyst workflows
- Risk Quantification for ROI modeling and business-aligned prioritization
- Feedback and Measurement Tools for continuous improvement and maturity tracking
Conclusion: Aligning CTI with Business Outcomes
CTI teams are no longer just supporting the SOC—they’re informing business decisions, enabling proactive defense, and contributing directly to cyber resilience. But to do that, intelligence must be:
- Structured
- Contextual
- Quantifiable
- Communicated in business terms
ThreatConnect exists to help you do just that. We’ve built the platform CTI teams need to show value, drive action, and secure the resources that allow them to thrive.
Ready to make your intelligence matter more? Let’s talk!

