Cyber threats are often characterized by fragmented intel and seemingly disconnected events, making it hard to piece together the big picture. The Diamond Model of Intrusion Analysis (aka the Diamond Model), written by Sergio Caltagirone, Andy Pendergast (co-founder and EVP of Product at ThreatConnect), and Christopher Betz, offers a strategic framework that enables organizations to dissect and analyze cyberattacks in a systematic way. By focusing on key elements of an attack, this framework helps cybersecurity teams understand what happened, predict future threats, and improve defenses.
What Is the Diamond Model of Intrusion Analysis?
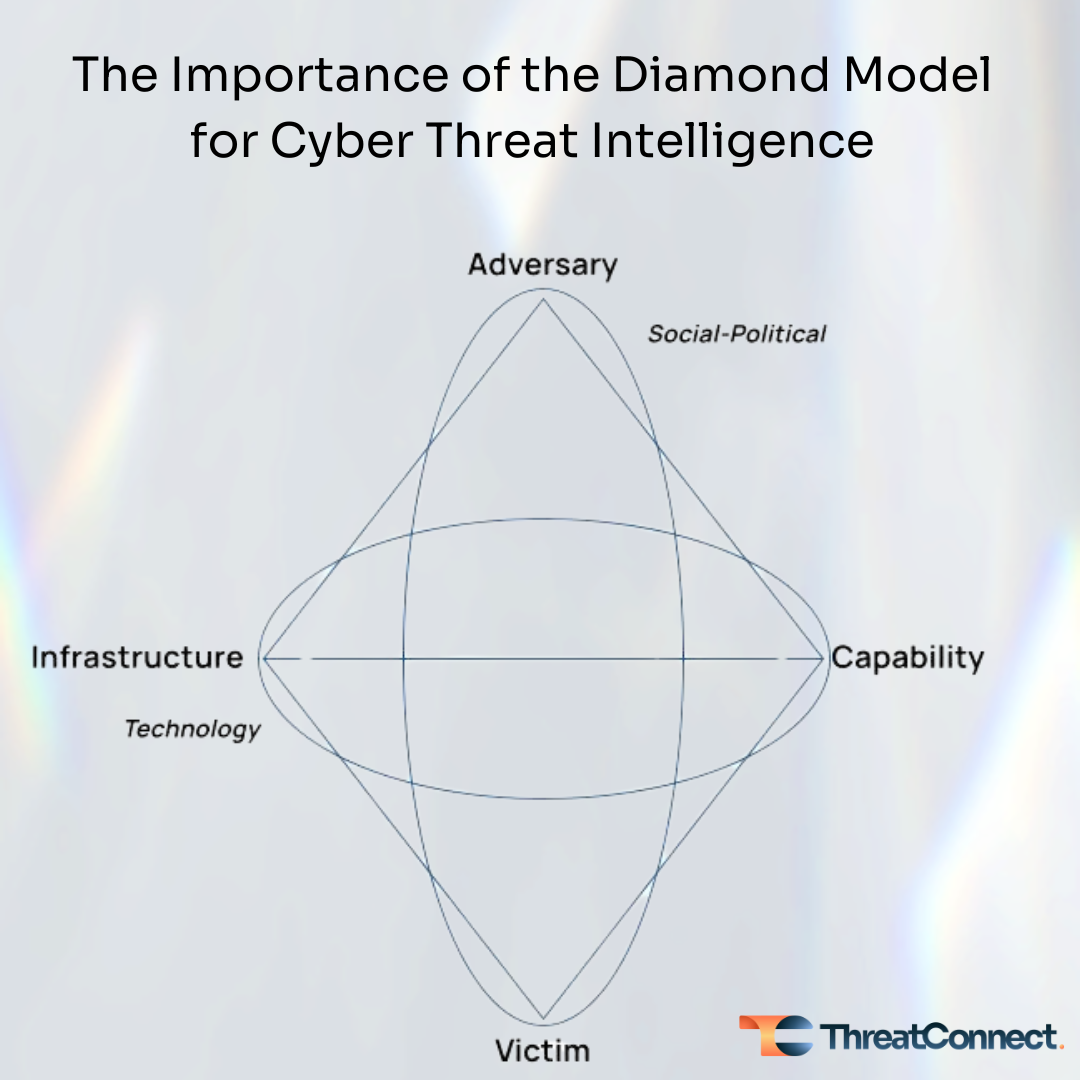
The Diamond Model of intrusion analysis is a methodology that deconstructs cyber intrusions into four core elements, forming the vertices of a diamond shape:
- Adversary: The adversary is the individual, group, or entity responsible for orchestrating the attack. This could be a hacker, cybercriminal, or nation-state actor. The attacker’s capabilities, intentions, and motivations determine the attack.
- Infrastructure: The virtual and physical tools, systems, and networks used by the adversary to execute the attack, such as servers, domains, email accounts, IP addresses, and compromised machines.
- Capability: The methods, techniques, and processes utilized by the adversary to execute the attack. This includes malware, phishing tactics, exploit kits, and custom-developed software.
- Victim: The target of the attack, which could be an organization, network, system, or individual.
The Diamond Model helps security analysts construct a detailed view of an intrusion by analyzing these interconnected components. This holistic approach identifies the immediate threat and uncovers relationships and patterns that may indicate larger campaigns or persistent threat actors.
How the Diamond Model Is Used in Threat Intelligence
Utilizing the Diamond Model cybersecurity approach enables organizations to move beyond reactive measures, allowing for proactive threat hunting and strategic planning based on comprehensive intelligence. This model serves as a foundational tool in threat intelligence for several key reasons:
- Attack mapping: The first step in using the Diamond Model is to break down an attack into four core components — Adversary, Capability, Infrastructure, and Victim. By identifying each of these elements, the model allows for a comprehensive and structured view of the attack.
- Relationship analysis: By connecting the four elements, analysts can visualize and understand the relationships between different attacks, tools, and adversaries.
- Pattern recognition: Identifying commonalities across multiple incidents helps in recognizing threat patterns, tactics, and techniques used by adversaries. These may include repeated use of domains, IP addresses, and similar victim profiles (same industry or region).
- Predictive insights: Understanding the adversary’s capabilities and infrastructure aids in anticipating future attacks and preparing appropriate defenses.
- Enhanced communication: The model establishes a common language for security teams, facilitating better collaboration and information sharing within and between organizations.
ThreatConnect’s Platform and the Diamond Model
At ThreatConnect, we have integrated the principles of the Diamond Model into our Threat Intelligence Platform (TIP), empowering organizations to build a comprehensive view of cyber threats. ThreatConnect leverages the Diamond Model in numerous ways, including:
- Integrated data modeling: Our platform’s architecture is built around the Diamond Model, allowing for seamless categorization and association of threat data according to the four core elements.
- Dynamic associations: Users can explore relationships between adversaries, infrastructure, capabilities, and victims, building a rich network of intelligence.
- Advanced pivoting: Analysts can pivot between related threat elements within the platform, uncovering hidden links and uncovering deeper insights.
- Automated correlations: Our platform utilizes AI and machine learning to automatically correlate new and existing threat data, enhancing the speed and accuracy of analysis.
- Collaborative intelligence: By sharing and correlating data within the Diamond Model framework, organizations can benefit from collective insights and strengthen their defenses against common threats.
Unlock Deeper Insights with ThreatConnect’s Diamond Model Approach
Understanding the full scope of cyber threats is crucial for building a resilient security posture. The Diamond Model equips your organization with a robust methodology to dissect and anticipate cyber-attacks.
Request a demo today to discover how ThreatConnect’s TIP leverages the Diamond Model to provide actionable insights and empower your team.